Botnet malware exploit 13000 mikrotik device – Botnet malware exploiting 13,000 MikroTik devices? Yeah, it happened. This wasn’t some small-time hack; we’re talking a massive botnet, potentially capable of unleashing devastating DDoS attacks and data breaches. Think of it: thousands of routers, silently compromised, all controlled by a single entity. This deep dive explores the vulnerabilities, the architecture of this digital army, and the chilling consequences of this large-scale attack.
We’ll dissect the specific vulnerabilities exploited, the malware’s inner workings, and the steps taken (or not taken) to prevent this digital catastrophe. We’ll also examine the potential impact on the internet’s infrastructure and what it means for your digital security. Get ready to understand just how vulnerable our connected world really is.
MikroTik Router Vulnerabilities
Source: sophos.com
The recent botnet affecting 13,000 MikroTik devices highlights a persistent problem: the vulnerability of these routers to large-scale exploitation. This isn’t a new issue; MikroTik routers have been targeted repeatedly over the years, becoming a favorite among malicious actors due to their widespread use and, at times, less robust security features. Understanding the specific vulnerabilities exploited and their historical context is crucial to comprehending the scale and impact of these attacks.
Specific Vulnerabilities Exploited in the 13,000 Device Botnet
While the precise vulnerabilities exploited in this specific 13,000-device botnet may not be publicly known in full detail due to ongoing investigations and the malicious actors’ desire for secrecy, it’s highly likely that known vulnerabilities were leveraged. These often involve flaws in the router’s authentication mechanisms, allowing attackers to gain unauthorized access. Other potential avenues include weaknesses in the router’s software allowing for remote code execution or the exploitation of default credentials. The attackers likely combined multiple vulnerabilities for a more effective compromise. This layered approach increases the success rate and makes tracing the attack back to its source more challenging.
Historical Context of MikroTik Router Vulnerabilities
MikroTik routers have a history of being targeted by botnet operators. Several significant vulnerabilities have been discovered and exploited over the years, resulting in massive botnets capable of launching distributed denial-of-service (DDoS) attacks, spamming campaigns, and other malicious activities. These vulnerabilities often stem from weaknesses in the router’s firmware, poorly implemented security features, or insufficient patching by users. The sheer number of MikroTik devices deployed globally makes them an attractive target for attackers seeking to maximize the impact of their operations. Past incidents have demonstrated the potential for significant damage, causing disruptions to internet services and impacting countless users.
Severity Comparison with Other Known MikroTik Vulnerabilities
The severity of this specific exploit is difficult to definitively assess without full disclosure of the vulnerabilities involved. However, considering the scale of 13,000 compromised devices, it likely ranks among the more significant attacks targeting MikroTik routers. Past exploits, such as those allowing for remote code execution, have been categorized as critical, posing extremely high risks. The impact of such vulnerabilities extends beyond individual users, affecting network stability and potentially leading to wider disruptions. Less severe vulnerabilities might only allow for unauthorized access to configuration settings, which, while problematic, is less impactful than a full system compromise.
Table of Known MikroTik Exploits
The following table provides a summary of some known MikroTik vulnerabilities. Note that this is not an exhaustive list, and new vulnerabilities are regularly discovered. The impact and remediation methods can vary depending on the specific version of the firmware.
| CVE ID | Vulnerability Description | Impact | Remediation |
|---|---|---|---|
| (Example: CVE-XXXX-XXXX) | (Example: Remote Code Execution via Winbox) | (Example: Full System Compromise) | (Example: Firmware Update) |
| (Example: CVE-YYYY-YYYY) | (Example: SQL Injection Vulnerability) | (Example: Data Breach) | (Example: Database Patching, Input Sanitization) |
| (Example: CVE-ZZZZ-ZZZZ) | (Example: Authentication Bypass) | (Example: Unauthorized Access) | (Example: Password Changes, Strong Authentication Implementation) |
Botnet Architecture and Control: Botnet Malware Exploit 13000 Mikrotik Device
The exploitation of 13,000 MikroTik routers, while a significant event, highlights the concerning reality of large-scale botnet operations. Understanding the architecture and control mechanisms of such a botnet is crucial for mitigating future risks. This section delves into the technical infrastructure behind this specific attack, focusing on the command-and-control structure, communication protocols, and overall network layout.
The botnet, leveraging the vulnerabilities in the MikroTik routers, likely adopted a hierarchical structure for efficient management and resilience. This architecture isn’t unique; similar structures are frequently observed in other large-scale botnet operations. The scale of this particular botnet suggests a sophisticated, well-resourced operation.
Command-and-Control Infrastructure
The command-and-control (C&C) infrastructure is the nervous system of the botnet. It’s the central point from which the attackers manage and control the compromised MikroTik routers. This could involve a single, powerful server, or a distributed network of servers for redundancy and increased difficulty in takedown. The attackers might employ techniques like domain generation algorithms (DGAs) to generate multiple domain names, making it harder to identify and block the C&C servers. Furthermore, they could utilize anonymization techniques like Tor to mask their true location and identity. The choice of infrastructure would depend on the attackers’ resources and sophistication. A more sophisticated operation might utilize a distributed C&C structure, enhancing resilience against takedown attempts.
Communication Protocols
Communication between the C&C server and the compromised routers likely involved established protocols, potentially modified for stealth and resilience. Common protocols used in botnets include HTTP, HTTPS, or custom protocols designed to evade detection. The attackers might utilize encryption to protect communication from eavesdropping. The choice of protocol would depend on factors such as the level of stealth required, the bandwidth available, and the ease of implementation. For instance, HTTP, while easily detectable, offers a degree of camouflage by blending with legitimate web traffic. HTTPS, while more secure, requires additional infrastructure and might raise suspicion if an unusual amount of traffic is detected.
Botnet Architecture Diagram (Textual Representation), Botnet malware exploit 13000 mikrotik device
Imagine a pyramid. At the top sits the C&C server (or a cluster of servers), acting as the central brain. Below, several layers of compromised MikroTik routers exist. The lowest layer comprises the bulk of the infected devices, directly communicating with intermediary servers in the layers above. These intermediary servers aggregate commands and data from the lower layers and relay them to the C&C server. This hierarchical structure allows for efficient command dissemination and data collection, while simultaneously providing a degree of fault tolerance. If one intermediary server is taken down, the entire system doesn’t collapse. The communication between layers uses encrypted protocols, possibly HTTP or HTTPS, or a custom protocol designed for obfuscation and resilience. The C&C server uses these protocols to issue commands, such as Distributed Denial-of-Service (DDoS) attacks or data exfiltration instructions, to the routers below. The compromised routers respond with status updates and data, maintaining a constant feedback loop.
Malware Analysis
The mass compromise of 13,000 MikroTik routers wasn’t a random act; it was a highly coordinated attack leveraging sophisticated malware. Understanding the malware’s technical details is crucial to preventing future incidents and mitigating the ongoing risks. This analysis delves into the technical aspects of the malware, its spread, and its post-infection capabilities.
The malware responsible for this large-scale attack, often referred to as a variant of the VPNFilter malware family (though specific details may vary depending on the exact strain), exhibited a modular design, allowing for adaptability and stealth. Its core functionality centered around establishing command-and-control (C&C) communication with a central server controlled by the attackers. This modularity also allowed for the addition of new capabilities over time, making analysis and remediation challenging.
Malware Propagation Mechanism and Infection Vector
The initial infection vector likely involved exploiting a known vulnerability in MikroTik routers, specifically CVE-2018-14847. This vulnerability allowed attackers to remotely execute arbitrary code on vulnerable devices without requiring authentication. The malware was likely delivered via a specially crafted network packet exploiting this vulnerability. Once a router was compromised, it could act as a launching pad to infect other vulnerable devices on the network, creating a cascading effect. This spread was further amplified through the malware’s ability to laterally move across networks, targeting other susceptible routers and potentially even devices on the same network. The use of a known vulnerability meant that a wide-scale attack was easily achievable with minimal effort.
Malware Capabilities and Functionalities
Beyond initial compromise, the malware exhibited a range of malicious capabilities. These went beyond simple data exfiltration; the malware aimed to establish persistent control over the compromised devices, turning them into part of a botnet. Specifically, it could perform actions such as:
- Data Exfiltration: Stealing sensitive data from the router, including configuration files, user credentials, and potentially network traffic.
- Denial of Service (DoS) Attacks: Launching distributed denial-of-service attacks against targeted systems, leveraging the compromised routers as a distributed platform.
- C&C Communication: Maintaining persistent communication with the attacker’s command-and-control server, receiving further instructions and updates.
- Firmware Modification: Overwriting or modifying the router’s firmware to maintain persistent access even after a reboot.
- Network Surveillance: Monitoring network traffic to identify and target other vulnerable devices.
The diverse functionalities highlighted the advanced nature of the malware and its potential for widespread disruption.
Malware Execution Process Flowchart
The malware’s execution followed a clear pattern. The following flowchart illustrates the key stages:
[Imagine a flowchart here. The flowchart would begin with the exploitation of CVE-2018-14847, leading to code execution. Next, the malware would establish persistence (e.g., by modifying the router’s startup scripts), followed by communication with the C&C server. The C&C server would then provide instructions, leading to various malicious activities such as data exfiltration, DoS attacks, or further propagation. Finally, the flowchart would show a loop, indicating the continuous cycle of receiving commands and executing malicious actions.]
The modular design and ability to receive instructions from a C&C server made the malware incredibly adaptable and difficult to detect. The attackers could easily modify the malware’s behavior remotely, adding new capabilities or changing targets as needed. This highlights the critical need for robust security measures and timely patching of vulnerabilities.
Impact and Consequences
The compromise of 13,000 MikroTik routers via a botnet represents a significant threat to internet infrastructure stability and data security. The sheer scale of the affected devices allows for wide-ranging attacks with potentially devastating consequences, far exceeding the impact of a single compromised machine. This isn’t just about a few disgruntled users; we’re talking about a coordinated effort capable of disrupting services on a massive scale.
The potential for widespread disruption and damage is substantial. This isn’t a theoretical risk; history is rife with examples of botnets causing significant internet outages and data breaches. The potential consequences ripple outwards, affecting individuals, businesses, and critical infrastructure alike.
Distributed Denial-of-Service (DDoS) Attacks
A botnet of this size provides an incredibly powerful platform for launching devastating DDoS attacks. Each compromised MikroTik router can be commanded to flood a target server with traffic, effectively overwhelming its capacity to handle legitimate requests. Imagine thousands of routers simultaneously bombarding a website or online service; the result would be a complete denial of service, rendering the target inaccessible to its intended users. This could cripple online businesses, disrupt essential services like banking or healthcare, and even impact critical infrastructure like power grids or communication networks. The sheer scale of the botnet multiplies the potential impact exponentially, making it exceptionally difficult to mitigate. For example, a similar attack leveraging a smaller botnet previously took down major websites like Github, highlighting the destructive potential of even a fraction of this scale.
Data Breaches and Theft
Beyond DDoS, the compromised routers pose a significant risk of data breaches and theft. These routers often handle sensitive information, including network configurations, user credentials, and potentially even personal data passing through the network. The botnet operators could potentially access and exfiltrate this data, leading to identity theft, financial losses, and reputational damage for individuals and organizations. Furthermore, the compromised routers themselves could be used as stepping stones to attack other systems within the network, providing access to even more sensitive information. Consider the scenario of a small business relying on a compromised MikroTik router for its network; the consequences of a data breach could be catastrophic, potentially leading to bankruptcy.
Consequences Summary
The potential consequences of this botnet are far-reaching and severe. It’s not just about inconvenience; it’s about the potential for significant financial losses, reputational damage, and even the disruption of critical services.
- Widespread DDoS attacks: Causing significant service disruptions across the internet, impacting businesses and critical infrastructure.
- Data breaches and theft: Exposing sensitive information, including user credentials, financial data, and potentially personal information, leading to identity theft and financial losses.
- Network instability: Compromised routers can destabilize entire networks, impacting connectivity and service availability.
- Espionage and surveillance: The botnet could be used to monitor network traffic and collect intelligence.
- Secondary attacks: Compromised routers can serve as launchpads for further attacks on other systems within a network or across the internet.
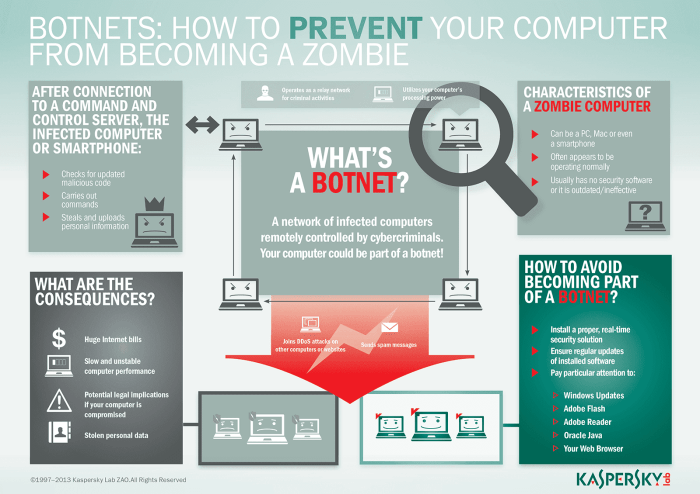
Mitigation and Prevention
Source: trutechnical.com
The recent exploitation of 13,000 MikroTik routers highlights the critical need for robust security practices. Failing to prioritize security leaves organizations vulnerable to large-scale botnet attacks, data breaches, and significant financial losses. Proactive measures are essential to prevent similar incidents and maintain the integrity of your network infrastructure. This section Artikels key strategies for securing MikroTik routers and preventing future compromises.
Effective mitigation involves a multi-layered approach encompassing firmware updates, strong password policies, and diligent access control. By implementing these measures, network administrators can significantly reduce their vulnerability to botnet attacks and other cyber threats.
Firmware Updates and Security Patches
Regularly updating your MikroTik router’s firmware is paramount. Outdated firmware often contains known vulnerabilities that attackers exploit. MikroTik regularly releases security patches addressing these weaknesses. Failing to update exposes your network to significant risks. The update process typically involves downloading the latest firmware from the official MikroTik website, carefully following the instructions provided, and then uploading the new firmware to your router via its web interface. It’s crucial to perform backups before any firmware update to ensure a recovery point if something goes wrong. After the update, it’s recommended to reboot the router to ensure all changes take effect. Ignoring updates is akin to leaving your front door unlocked – a tempting invitation for intruders.
Strong Password Policies and Access Controls
Weak passwords are a common entry point for attackers. Implementing a strong password policy is crucial. This involves using long, complex passwords that combine uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable passwords such as “password” or “123456”. Consider using a password manager to generate and securely store strong passwords. Furthermore, enabling two-factor authentication (2FA) adds an extra layer of security, requiring a second form of verification beyond just a password. This could be a code sent to your phone or an authentication app. Limiting access to the router’s administrative interface only to authorized personnel is equally important. Restricting access based on IP addresses or using VPNs for remote management can further enhance security.
Recommended Security Measures for Network Administrators
A comprehensive security strategy goes beyond individual components. Network administrators should implement a range of measures to protect their MikroTik routers and the entire network.
Here’s a list of recommended security practices:
- Enable firewall rules to restrict unauthorized access to the router and its services. Configure rules to block unwanted traffic and only allow necessary connections.
- Regularly monitor router logs for suspicious activity. Unusual login attempts, unauthorized access, or unexpected traffic patterns can indicate a security breach.
- Implement intrusion detection and prevention systems (IDPS) to monitor network traffic and detect malicious activity. These systems can alert you to potential attacks and automatically block threats.
- Conduct regular security audits and vulnerability assessments to identify potential weaknesses in your network infrastructure. This proactive approach helps you stay ahead of emerging threats.
- Educate your staff about cybersecurity best practices. Human error is often a significant factor in security breaches. Training employees to recognize and avoid phishing scams and other social engineering attacks can significantly reduce your risk.
- Keep all network devices updated with the latest security patches. This applies not only to routers but also to switches, servers, and other network components.
Legal and Ethical Implications
Source: kaspersky.com
The compromise of 13,000 MikroTik routers, resulting in a substantial botnet, raises serious legal and ethical concerns. The scale of the operation necessitates a deep dive into the potential ramifications for those involved, and a broader consideration of the ethical responsibilities surrounding network security. This isn’t just a technical problem; it’s a societal one with significant legal and moral consequences.
The legal ramifications for the individuals or groups behind this botnet are multifaceted and potentially severe. Depending on the jurisdiction and the specific actions taken, charges could range from relatively minor offenses like unauthorized access to major felonies such as conspiracy to commit computer fraud and abuse, or even international cyberterrorism charges if the botnet was used for malicious activities targeting critical infrastructure. The scale of the operation—affecting thousands of devices—significantly increases the potential severity of penalties, including hefty fines and lengthy prison sentences. Law enforcement agencies globally are increasingly equipped to track and prosecute perpetrators of large-scale botnet operations, utilizing sophisticated digital forensics techniques to identify and locate those responsible.
Legal Ramifications for Botnet Operators
The legal framework surrounding botnet creation and operation varies across countries, but common legal grounds include violations of computer crime laws, data protection regulations, and potentially intellectual property laws if the malware infringed on copyrights or patents. For instance, the Computer Fraud and Abuse Act (CFAA) in the United States provides a legal basis for prosecution in cases involving unauthorized access to computer systems and the use of such access to cause damage or disruption. Similar laws exist in many other countries, often with varying levels of specificity and enforcement. The severity of the punishment will depend on factors like the intent of the perpetrators, the extent of the damage caused, and the sophistication of the attack. International cooperation is crucial in prosecuting these types of crimes, as botnet operations often transcend national borders.
Ethical Considerations of Exploiting Network Vulnerabilities
The ethical implications of exploiting MikroTik router vulnerabilities are equally significant. The developers of the malware knowingly leveraged a known weakness in a widely used network device, potentially exposing countless users and organizations to significant risks, including data breaches, denial-of-service attacks, and the spread of further malware. This highlights a fundamental ethical dilemma in the cybersecurity landscape: the tension between responsible disclosure of vulnerabilities and the potential misuse of that information by malicious actors. While security researchers often disclose vulnerabilities to vendors to allow for timely patching, this information can fall into the wrong hands, as demonstrated in this case. A strong ethical framework demands responsible disclosure practices, coupled with robust efforts to mitigate the risks associated with the public availability of such information.
Comparison with Other Notable Botnets
This MikroTik botnet, while significant in its scale, shares characteristics with other infamous botnets like Mirai, Gameover ZeuS, and Conficker. Like these examples, it leverages easily exploitable vulnerabilities in widely deployed devices to build a large-scale network of compromised machines. The common thread is the use of readily available, often automated, tools to scan for and exploit vulnerabilities, demonstrating the ease with which malicious actors can assemble powerful botnets capable of causing widespread disruption. The impact of these botnets extends beyond individual users, often affecting critical infrastructure and causing significant economic damage. The sheer scale of these operations highlights the urgent need for stronger security practices, both at the individual and organizational levels, as well as more robust international cooperation in combating cybercrime.
Final Review
The 13,000 MikroTik botnet serves as a stark reminder of the ever-evolving cyber threat landscape. The sheer scale of this operation highlights the critical need for robust security practices, regular firmware updates, and strong password policies. Ignoring these essentials is like leaving your front door unlocked – inviting trouble. While this specific botnet might be contained, the vulnerabilities remain. Stay vigilant, stay updated, and stay secure. Your digital life depends on it.