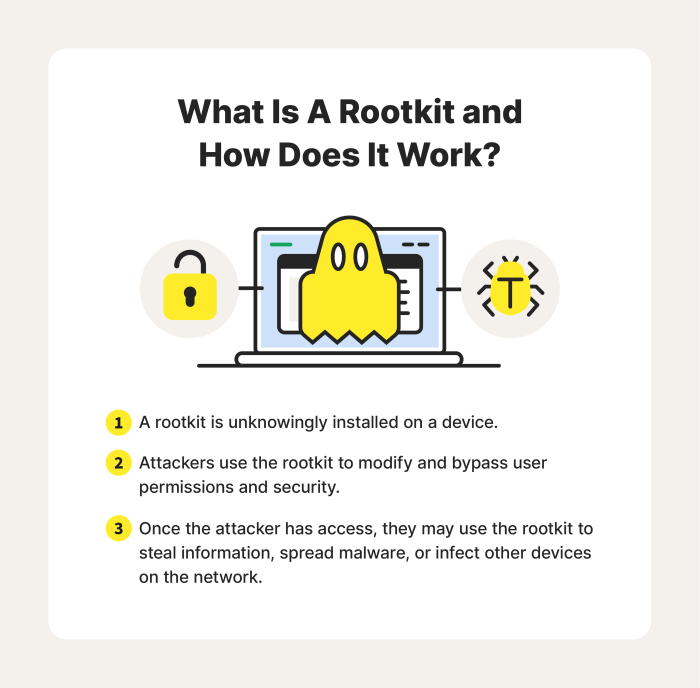
Rootkit Malware Controls Linux Systems Remotely
Rootkit malware controls Linux systems remotely – a chilling reality for anyone managing sensitive data. Imagine a silent intruder, burrowing deep into your server’s core, silently siphoning information and controlling your system from afar. This isn’t some sci-fi thriller; it’s a very real threat, leveraging vulnerabilities in the operating system to establish a persistent backdoor. … Read more