32 million Windows 10 devices at risk? Whoa. That’s a seriously huge chunk of the digital world potentially vulnerable. We’re talking major security flaws, leaving users wide open to data breaches, financial heists, and all sorts of digital mayhem. Think ransomware, identity theft – the whole shebang. This isn’t just some techie scare tactic; this is a real threat impacting millions.
This deep dive explores the vulnerabilities, the potential impact on unsuspecting users, and, most importantly, what you can do to protect yourself. We’ll break down the risks, examine real-world examples of similar attacks, and arm you with the knowledge and strategies to safeguard your digital life. Get ready to level up your Windows security game.
Vulnerability Assessment
Thirty-two million Windows 10 devices facing security risks is a significant figure, highlighting the persistent need for robust security practices. This vulnerability assessment delves into the potential weaknesses affecting these systems and the likely attack vectors employed by malicious actors. Understanding these vulnerabilities is crucial for implementing effective mitigation strategies.
The potential vulnerabilities affecting these 32 million Windows 10 devices are multifaceted, stemming from both outdated software and exploitable weaknesses in the operating system itself. These vulnerabilities can range from easily patched software flaws to more complex, zero-day exploits. The widespread nature of the issue underscores the importance of proactive security measures and regular updates.
Attack Vectors
Attackers exploit these vulnerabilities through various methods, often leveraging social engineering tactics to gain initial access. Phishing emails containing malicious attachments or links are a common entry point. Exploiting unpatched software vulnerabilities, such as those in web browsers or other applications, is another popular technique. Once initial access is gained, attackers may leverage lateral movement techniques to compromise other systems within the network. Remote Desktop Protocol (RDP) vulnerabilities, if left unpatched, represent a significant risk.
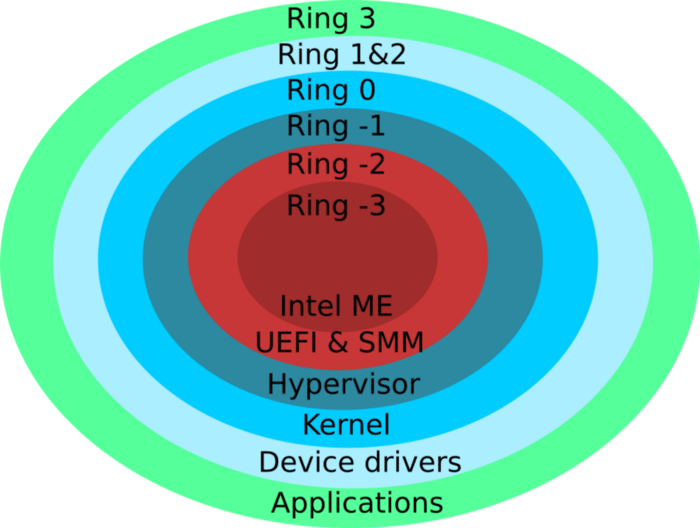
Critical Vulnerabilities
The following table categorizes some of the most critical vulnerabilities affecting Windows 10 devices, detailing their severity and potential impact. Note that this is not an exhaustive list, and the specific vulnerabilities affecting the 32 million devices may vary.
| Vulnerability Name | Severity | Description | Potential Impact |
|---|---|---|---|
| Unpatched Kernel Exploits | Critical | Exploits targeting vulnerabilities in the Windows kernel, the core of the operating system. | Complete system compromise, data theft, malware installation. |
| Outdated Antivirus Software | High | Using outdated or ineffective antivirus software leaves systems vulnerable to malware. | Malware infections, data breaches, ransomware attacks. |
| Weak Passwords | High | Using easily guessable passwords provides attackers with easy access. | Account takeover, data theft, unauthorized access. |
| Unpatched Browser Vulnerabilities | Medium to High | Outdated web browsers with known vulnerabilities can be exploited via malicious websites. | Malware downloads, phishing attacks, data theft. The severity depends on the specific browser and vulnerability. |
| RDP Exposure | High | Exposing Remote Desktop Protocol (RDP) without proper security measures allows remote access. | Complete system compromise, data theft, ransomware attacks. |
Impact Analysis
Thirty-two million Windows 10 devices vulnerable to a single exploit represent a significant threat landscape. A successful attack could have far-reaching and devastating consequences for individuals, businesses, and even critical infrastructure. The potential for widespread damage underscores the urgency of addressing this vulnerability.
The consequences of a successful attack on this scale are multifaceted and potentially catastrophic. The sheer number of affected devices amplifies the potential impact, creating a domino effect across various sectors. We’re not just talking about individual inconvenience; we’re talking about potential systemic failure.
Data Breaches and Information Theft, 32 million windows 10 devices at risk
A successful exploit could lead to widespread data breaches, exposing sensitive personal information, financial records, intellectual property, and confidential business data. The scale of the breach would depend on the specific nature of the vulnerability and the attacker’s objectives. Stolen data could be used for identity theft, financial fraud, corporate espionage, or even blackmail. The cost of remediation, including legal fees, regulatory fines, and reputational damage, could be astronomical.
Financial Losses
The financial implications of such an attack are substantial. Businesses could face significant losses due to data breaches, service disruptions, and the costs associated with remediation and recovery. Individuals could suffer financial losses from identity theft and fraud. The overall economic impact could be felt across multiple sectors, potentially affecting market confidence and economic stability. Considering the number of affected devices, even a relatively small financial loss per device could translate to billions of dollars in overall damage.
Service Disruptions and Operational Downtime
A successful attack could cripple essential services, leading to widespread operational downtime. Hospitals, financial institutions, and government agencies rely heavily on computer systems, and a large-scale attack could disrupt their operations, potentially leading to critical failures with severe consequences. The disruption of essential services could have cascading effects, impacting various aspects of daily life and the economy. Imagine widespread power outages or banking system failures – the consequences would be far-reaching and deeply disruptive.
Real-World Examples of Similar Vulnerabilities and Outcomes
The potential impact of this vulnerability can be understood by examining similar incidents in the past. These examples highlight the severity of the consequences and the importance of proactive security measures.
- The NotPetya ransomware attack in 2017, which exploited a vulnerability in Ukrainian accounting software, spread globally, causing billions of dollars in damages and disrupting businesses worldwide. The attack highlighted the interconnectedness of global systems and the potential for a single vulnerability to cause widespread chaos.
- The SolarWinds supply chain attack in 2020 compromised thousands of organizations through a compromised software update. This attack demonstrated the potential for sophisticated attackers to leverage vulnerabilities in widely used software to gain access to a large number of systems. The long-term damage and cost of detection and remediation were significant.
- The WannaCry ransomware attack in 2017 exploited a vulnerability in older versions of Windows, encrypting files and demanding ransom payments. Millions of computers were affected, causing significant disruption and financial losses. This demonstrated the potential for widespread damage when vulnerabilities in widely used software are not patched promptly.
Affected User Demographics
Source: co.uk
Thirty-two million Windows 10 devices at risk represents a significant chunk of the global user base. Understanding the demographics of these affected users is crucial for targeted mitigation strategies and effective communication of the vulnerability. Pinpointing the most vulnerable groups allows for a more efficient and impactful response.
The likely demographic profile of affected users is broad, spanning various age groups, geographic locations, and occupations. However, certain segments are likely to be disproportionately affected due to factors like digital literacy and security awareness. This uneven distribution necessitates a tailored approach to remediation and prevention.
Geographic Distribution and Age
The global reach of Windows 10 means affected users are likely spread across numerous countries. However, regions with lower levels of digital literacy or weaker cybersecurity infrastructure may experience a higher concentration of vulnerable devices. Similarly, older users, who may be less tech-savvy and less likely to update their software regularly, could be more at risk. Consider, for instance, a retiree in a rural area of a developing nation, less likely to be aware of the vulnerability and less equipped to update their system. Conversely, tech-savvy younger users in urban areas of developed nations, while still vulnerable, may be more proactive in patching their systems.
Occupational Groups and Digital Literacy
The vulnerability’s impact varies significantly across different occupational groups. Individuals working in sectors with less stringent security protocols or those lacking regular security training might be more susceptible. Imagine a small business owner relying on an outdated Windows 10 system for their accounting – their lack of dedicated IT support makes them a prime target. In contrast, large corporations with dedicated IT departments are likely to have implemented security measures and regular updates, mitigating the risk to a greater extent. The correlation between digital literacy and security awareness is evident here: higher digital literacy often translates to better security practices.
Hypothetical Affected User Profile
A typical affected user could be a middle-aged individual, residing in a suburban area with limited technical expertise. They might use their Windows 10 device primarily for personal tasks like email, social media, and online banking. This individual might not be fully aware of the importance of regular software updates and might delay or neglect them due to a lack of understanding or perceived inconvenience. This profile highlights the potential for significant personal data breaches and financial losses. The risk exposure for this individual is high, particularly considering the potential for malware infection and identity theft.
Mitigation Strategies
Source: futurecdn.net
Thirty-two million Windows 10 devices facing vulnerabilities? That’s a serious situation. The good news is that proactive mitigation strategies can significantly reduce the risk. This section Artikels a comprehensive plan to secure your Windows 10 machine, empowering you to take control of your digital safety. We’ll break down actionable steps and compare different security solutions to help you choose the best fit for your needs.
This section details a multi-pronged approach to mitigating the risks associated with the identified Windows 10 vulnerabilities. It focuses on both immediate actions users can take and longer-term strategies for enhanced security. The goal is to provide a clear and actionable plan to protect your data and privacy.
Immediate Actions for Enhanced Security
Acting quickly is crucial. These steps provide an immediate boost to your system’s security, reducing your vulnerability to attack.
- Update Windows: Ensure your Windows 10 operating system is fully updated. Microsoft regularly releases security patches addressing known vulnerabilities. Check for updates manually or enable automatic updates in your system settings. This is arguably the single most important step.
- Install Latest Antivirus Software: A robust antivirus program provides real-time protection against malware and other threats. Ensure your antivirus software is up-to-date and actively scanning your system. Consider features like behavioral monitoring and firewall protection.
- Enable Windows Defender Firewall: Windows Defender Firewall acts as a barrier, preventing unauthorized access to your system. Verify that it is enabled and configured to block incoming connections unless explicitly allowed. This basic step provides a fundamental layer of protection.
- Strong Passwords and Multi-Factor Authentication (MFA): Use strong, unique passwords for all your accounts, and enable MFA wherever possible. MFA adds an extra layer of security, requiring a second form of verification (like a code from your phone) in addition to your password.
- Regularly Back Up Your Data: In the event of a security breach or system failure, having regular backups of your important data is essential. Use a cloud-based backup service or an external hard drive to ensure data recovery is possible.
Comparative Analysis of Security Solutions
Several security solutions can bolster your defenses against these vulnerabilities. Understanding their strengths and weaknesses is crucial in making an informed choice.
| Security Solution | Strengths | Weaknesses |
|---|---|---|
| Antivirus Software (e.g., Norton, McAfee, Bitdefender) | Real-time protection against malware, virus scanning, firewall capabilities. | Can be resource-intensive, may require subscription fees, potential for false positives. |
| Endpoint Detection and Response (EDR) Solutions (e.g., CrowdStrike, SentinelOne) | Advanced threat detection, incident response capabilities, proactive threat hunting. | Often more expensive than antivirus software, requires specialized expertise for management. |
| Firewall Software (e.g., Windows Defender Firewall, third-party firewalls) | Controls network traffic, prevents unauthorized access. | Can be complex to configure, may block legitimate traffic if not properly configured. |
| Virtual Private Network (VPN) | Encrypts internet traffic, protects your data on public Wi-Fi networks. | Can slow down internet speeds, requires a subscription for most services. |
Long-Term Security Strategies
Proactive measures beyond immediate fixes are crucial for sustained protection.
- Security Awareness Training: Educate yourself and your users about common phishing scams, malware threats, and social engineering tactics. Regular training significantly reduces the likelihood of successful attacks.
- Regular Security Audits and Penetration Testing: Periodically assess your system’s security posture through audits and penetration testing to identify and address potential vulnerabilities before attackers can exploit them. This proactive approach is crucial for large organizations.
- Implement a Patch Management System: Establish a robust system for patching vulnerabilities promptly. This involves automating the update process and testing patches before deployment to minimize disruption.
- Principle of Least Privilege: Grant users only the necessary permissions to perform their tasks. This limits the impact of a compromised account.
Software Updates and Patching
Regular software updates and patching are the unsung heroes of cybersecurity. They’re the digital armor that protects your system from the bad guys lurking in the shadows, ready to exploit vulnerabilities and wreak havoc. For 32 million Windows 10 devices facing potential threats, this isn’t just a suggestion; it’s a critical necessity. Ignoring updates leaves your systems exposed, making them easy targets for malware and other cyberattacks.
The importance of keeping your software patched can’t be overstated. These updates often contain crucial security fixes that plug holes in your system’s defenses, preventing malicious actors from gaining unauthorized access to your data or causing system failures. Think of it like this: every update is a new layer of security, strengthening your digital fortress against attacks. Regular patching significantly reduces the risk of falling victim to the very vulnerabilities we’re discussing.
Windows 10 Update Process
Checking for and installing updates on Windows 10 is generally straightforward. First, click the Start button, then the gear icon (Settings). Navigate to “Update & Security,” and then select “Windows Update.” Click “Check for updates,” and Windows will scan for any available updates. Once found, you can choose to install them immediately or schedule them for a later time. Windows 10 often installs updates automatically in the background, but checking manually ensures you’re always up-to-date. Remember to restart your computer after installing updates to ensure all changes take effect.
Challenges of Patching Large-Scale Deployments
Managing updates across 32 million Windows 10 devices presents significant logistical challenges. Ensuring every single device receives and installs the necessary patches in a timely manner requires robust infrastructure, careful planning, and sophisticated management tools. Consider the sheer scale: different devices might have varying configurations, network connectivity issues could delay updates, and some users might disable automatic updates altogether. This complexity necessitates a multi-faceted approach, including automated deployment systems, rigorous testing procedures, and effective communication strategies to ensure smooth and timely patching across the entire fleet. Furthermore, the need to minimize disruption to users during the update process is crucial, as downtime can impact productivity and create user frustration. The potential for incompatibility between updates and existing software also adds to the challenge, necessitating thorough testing before widespread deployment.
Security Awareness Training
Source: bleepstatic.com
Thirty-two million Windows 10 devices at risk demand immediate and effective security awareness training. This isn’t just about patching software; it’s about empowering users to be the first line of defense against increasingly sophisticated cyber threats. A well-designed training program can significantly reduce the likelihood of successful attacks, protecting both individual users and the overall system.
This section Artikels a concise security awareness training program designed to equip users with the knowledge and skills to identify and avoid common threats. We’ll cover best practices for securing devices and illustrate how social engineering tactics exploit vulnerabilities, helping users recognize and resist manipulation.
Security Awareness Training Program Overview
The training program will be delivered via a short, engaging online module, supplemented by easily digestible infographics and readily available resources. The module will focus on practical, actionable steps users can take to improve their security posture. The emphasis will be on clear, concise information presented in a non-technical manner, ensuring accessibility for all users. The program will include interactive elements such as quizzes and scenarios to reinforce learning and assess comprehension. Regular refresher courses will be scheduled to ensure ongoing awareness of emerging threats and best practices.
Best Practices for Protecting Devices
Understanding the basics of online security is crucial for mitigating risks. The following table summarizes essential best practices users should adopt:
| Best Practice | Explanation |
|---|---|
| Strong Passwords | Use unique, complex passwords for each online account. Avoid using easily guessable information like birthdays or pet names. Consider using a password manager to generate and securely store strong passwords. |
| Software Updates | Install all operating system and software updates promptly. These updates often include critical security patches that protect against known vulnerabilities. |
| Phishing Awareness | Be wary of suspicious emails, messages, or websites. Look for grammatical errors, unusual requests, or links that don’t match the sender’s domain. Never click on links or download attachments from unknown sources. |
| Antivirus Software | Install and maintain reputable antivirus software on your device. Regularly scan your system for malware and keep the software updated. |
| Two-Factor Authentication (2FA) | Enable 2FA whenever possible. This adds an extra layer of security by requiring a second form of authentication, such as a code sent to your phone, in addition to your password. |
| Secure Wi-Fi Networks | Avoid using public Wi-Fi networks for sensitive activities like online banking or shopping. If you must use public Wi-Fi, consider using a VPN to encrypt your connection. |
Social Engineering Techniques and Exploitation
Social engineering manipulates individuals into divulging confidential information or performing actions that compromise security. Attackers might use deceptive emails (phishing) pretending to be legitimate organizations, requesting login credentials or personal data under the guise of urgent matters or technical support. Another common tactic involves creating a sense of urgency or fear to pressure victims into acting quickly without thinking critically. For example, an attacker might claim that the user’s account has been compromised and prompt them to click a malicious link to “restore” their account. These attacks prey on human psychology, exploiting trust and fear to gain access to systems and data. Training will focus on identifying these tactics and promoting critical thinking before responding to suspicious communications.
Illustrative Scenario: 32 Million Windows 10 Devices At Risk
Imagine Sarah, a freelance graphic designer working from home. Her aging Windows 10 machine, one of the 32 million vulnerable devices, hasn’t received security updates in months. She relies on this computer for everything – client communication, design software, and personal banking. This lack of updates leaves her system exposed to a critical vulnerability.
The attack begins subtly. Sarah clicks a seemingly innocuous link in a phishing email disguised as an invoice from a regular client. This link doesn’t download a malicious file directly; instead, it exploits the known vulnerability in her outdated Windows 10 system. The exploit leverages a zero-day vulnerability – meaning it’s unknown to Microsoft and thus hasn’t been patched. This vulnerability allows an attacker remote code execution, giving them complete control over Sarah’s computer without her knowledge.
Attack Progression and Techniques
The attacker gains initial access through the exploited vulnerability, silently installing a remote access trojan (RAT). This RAT acts as a backdoor, allowing the attacker persistent access to Sarah’s system. They then proceed to install keyloggers to capture her passwords and banking details. Further, they deploy a screen-scraping tool to capture sensitive information displayed on her screen, such as her online banking session. The attacker’s actions are covert; Sarah remains completely unaware of the compromise.
Impact of the Attack
The consequences for Sarah are severe. The attacker gains access to her client communication, potentially stealing sensitive design files and confidential client information. More critically, they access her banking details, leading to financial loss. The breach of her personal and professional data also exposes her to identity theft and reputational damage. The incident causes significant stress and financial hardship, requiring her to spend time and money to recover from the attack and secure her data.
Attacker Motivations and Goals
The attacker’s motivation is likely financial gain. Stealing banking details is a direct route to financial profit. Additionally, stealing client data and design files could be sold on the dark web, providing further revenue. The attacker might also have additional malicious goals, such as using Sarah’s computer as part of a larger botnet for distributed denial-of-service (DDoS) attacks or for further exploitation of other targets. The lack of security updates on Sarah’s machine made her an easy target, demonstrating the critical importance of timely patching and security awareness.
Summary
The vulnerability affecting 32 million Windows 10 devices is a serious wake-up call. While the sheer number is alarming, the good news is that proactive steps can significantly reduce your risk. Staying updated with patches, practicing good online hygiene, and being aware of potential threats are crucial. Don’t wait for disaster to strike – take control of your digital security today. Your peace of mind (and your data) will thank you.