Network intrusion detection systems in SOCs: They’re the unsung heroes silently guarding your digital fortress. These systems are the vigilant sentinels, constantly monitoring network traffic for suspicious activity, acting as the first line of defense against cyber threats. From signature-based systems that look for known attack patterns to anomaly-based systems that hunt for the unusual, NIDS are crucial for any modern SOC. But how do they fit into the bigger picture? How effective are they really? Let’s dive in.
This deep dive explores the world of Network Intrusion Detection Systems (NIDS) within Security Operations Centers (SOCs). We’ll cover everything from integrating NIDS alerts into your incident response workflow to leveraging threat intelligence for better detection and response. We’ll also tackle the challenges, like dealing with false positives and keeping your NIDS systems up-to-date. Get ready to become a NIDS expert!
Network Intrusion Detection Systems (NIDS) in Security Operations Centers (SOCs)
Network Intrusion Detection Systems (NIDS) are the unsung heroes of the SOC, silently monitoring network traffic for malicious activity. They act as the first line of defense, providing crucial early warnings that allow security analysts to react swiftly to threats before they can cause significant damage. Think of them as the ever-vigilant guards patrolling the digital perimeter, constantly scanning for suspicious behavior.
NIDS play a vital role in a SOC environment by providing real-time visibility into network traffic, identifying potential security breaches, and assisting in incident response. They help SOC teams proactively hunt for threats, rather than simply reacting to alerts. This proactive approach significantly reduces the impact of successful attacks and minimizes downtime. Essentially, they’re the eyes and ears of your network security.
Types of NIDS
NIDS employ different methods to detect intrusions. Understanding these methods is key to selecting the right NIDS for your specific needs and effectively interpreting its alerts.
- Signature-based NIDS: These systems work by comparing network traffic against a database of known attack signatures (patterns of malicious activity). If a match is found, an alert is triggered. Think of it like a fingerprint database for cyberattacks. This approach is effective against known threats but struggles with novel or zero-day attacks.
- Anomaly-based NIDS: Instead of relying on known signatures, anomaly-based NIDS establish a baseline of normal network behavior. Any deviation from this baseline triggers an alert. This is like learning the normal heartbeat of your network and flagging anything unusual. While effective against unknown threats, they can generate false positives if the baseline isn’t properly configured or if network behavior naturally changes.
- Hybrid NIDS: Combining the strengths of both signature-based and anomaly-based approaches, hybrid NIDS offer a comprehensive solution. They leverage the speed and accuracy of signature-based detection for known threats while also identifying anomalies that might indicate new or evolving attacks. This approach provides a balanced strategy for threat detection.
Common NIDS Deployment Scenarios
The optimal deployment strategy for a NIDS depends on the specific security needs and infrastructure of the organization. However, some common scenarios illustrate their practical application.
- Perimeter Security: Deploying NIDS at the network perimeter allows for the monitoring of all incoming and outgoing traffic, providing a crucial first line of defense against external threats. This is akin to setting up security checkpoints at the border of your network.
- Internal Network Monitoring: NIDS can also be deployed within the internal network to monitor traffic between internal systems and detect insider threats or lateral movement by attackers who have already breached the perimeter. This is like having internal security patrols within your network.
- Cloud Environments: With the rise of cloud computing, NIDS are increasingly deployed in cloud environments to monitor traffic within virtual networks and protect cloud-based resources. This mirrors the need for security in physical and virtual spaces.
- Specific Segment Monitoring: Organizations may deploy NIDS to monitor specific network segments, such as those containing sensitive data or critical infrastructure, providing targeted protection for high-value assets. This is like focusing security efforts on high-risk areas within a building.
NIDS Integration within the SOC Workflow
Integrating Network Intrusion Detection Systems (NIDS) effectively into your Security Operations Center (SOC) is crucial for a robust security posture. A well-integrated NIDS doesn’t just passively report alerts; it actively contributes to a streamlined incident response process, enhancing the overall effectiveness of your SOC. This involves careful planning, proper configuration, and a deep understanding of how NIDS data fits within your existing security ecosystem.
NIDS alerts are the raw material for incident response. They represent potential threats that need investigation and, if confirmed, remediation. However, simply receiving alerts isn’t enough. The key lies in effectively processing and contextualizing these alerts within the broader SOC workflow, which includes correlation with other security data sources and efficient escalation procedures.
NIDS Alert Integration into the SOC Incident Response Process
The integration of NIDS alerts into the SOC’s incident response process follows a structured approach, ensuring that potential security incidents are addressed efficiently and effectively. The process typically begins with the NIDS generating an alert based on predefined rules or anomaly detection. This alert is then ingested into the SOC’s Security Information and Event Management (SIEM) system, where it’s enriched with contextual information from other security tools. This enriched alert is then prioritized based on its severity and potential impact, and finally, assigned to a security analyst for investigation and remediation. The analyst uses various tools and techniques to verify the alert, determine the root cause, and implement necessary security controls to prevent further compromise. This entire process should be documented and regularly reviewed to ensure continuous improvement.
Best Practices for Correlating NIDS Alerts with Other Security Data Sources
Effective correlation of NIDS alerts with data from other sources is vital for accurate threat assessment and incident response. For example, correlating a NIDS alert indicating suspicious network activity with logs from firewalls, endpoint detection and response (EDR) systems, and user activity monitoring can provide a much clearer picture of the potential threat. This comprehensive view allows security analysts to determine whether the alert is a true positive, a false positive, or part of a larger, more complex attack. Best practices include establishing clear data integration pathways between different security tools, using a SIEM to centralize and correlate security data, and developing robust correlation rules based on known attack patterns and threat intelligence.
Workflow Diagram: NIDS Integration within a SOC
The following table illustrates a simplified workflow for NIDS integration within a SOC. This is a sample, and specific steps and tools will vary based on the organization’s specific security infrastructure and processes.
| Step | Action | System/Tool | Output |
|---|---|---|---|
| 1 | NIDS detects suspicious network activity. | NIDS | Alert generated. |
| 2 | Alert is ingested into the SIEM. | SIEM | Enriched alert with contextual data. |
| 3 | Alert is prioritized based on severity and impact. | SIEM/SOAR | Prioritized alert. |
| 4 | Alert is assigned to a security analyst. | Ticketing system/SOAR | Analyst assigned to the case. |
| 5 | Analyst investigates the alert, correlating it with other security data. | Various security tools (EDR, Firewall logs, etc.) | Incident report. |
| 6 | Analyst determines root cause and implements remediation. | Various security tools | Remediated incident. |
| 7 | Incident is documented and reviewed. | Incident management system | Updated incident report and process improvement suggestions. |
Analyzing NIDS Alerts and Identifying Threats: Network Intrusion Detection Systems In Soc
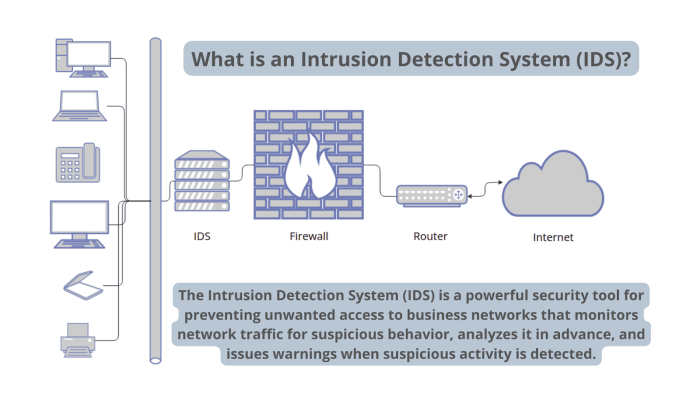
Source: com.au
Sifting through the deluge of alerts generated by a Network Intrusion Detection System (NIDS) is a crucial, yet often overwhelming, task for any SOC team. Effective analysis hinges on a structured approach that prioritizes alerts, identifies false positives, and leverages the data for proactive threat hunting. This process is vital for minimizing response times and maximizing the effectiveness of incident response efforts.
The sheer volume of alerts generated by NIDS can quickly become unmanageable. Prioritization and triage are essential for focusing resources on the most critical threats. A well-defined system ensures that security analysts don’t get bogged down in less important events.
Prioritizing and Triaging NIDS Alerts, Network intrusion detection systems in soc
Effective prioritization relies on several factors. Severity scoring, based on the potential impact of the detected event, is paramount. A critical alert indicating a potential data breach should take precedence over a low-severity alert suggesting suspicious network traffic. Contextual information, such as the source IP address, destination IP address, and the type of attack detected, helps to further refine the prioritization process. Alerts originating from internal sources, for example, might require more immediate attention than those originating from external sources, unless they are clearly malicious. Finally, integrating NIDS alerts with other security tools, such as SIEM (Security Information and Event Management) systems, provides a broader context and enables more informed decisions. This allows for correlation with other security events, helping analysts understand the bigger picture and prioritize accordingly. For instance, a suspicious login attempt flagged by a NIDS could be cross-referenced with authentication logs to confirm the legitimacy of the user.
Common False Positives and Mitigation Strategies
NIDS, while powerful, are not perfect. False positives—alerts that indicate a potential threat but are ultimately benign—are a common occurrence. These can be caused by various factors, including legitimate network activity that mimics malicious behavior, misconfigured NIDS rules, or simply noisy network environments. Common sources of false positives include legitimate port scans during network maintenance, automated system updates that trigger intrusion signatures, and even unusual network traffic patterns from applications using unconventional protocols.
Reducing false positives requires a multi-pronged approach. Regularly reviewing and refining NIDS rules is crucial. This includes adjusting thresholds, removing outdated signatures, and adding exceptions for known legitimate activities. Implementing proper network segmentation can also significantly reduce the number of false positives by isolating sensitive systems and reducing the overall network traffic that the NIDS needs to analyze. Finally, employing machine learning techniques within the NIDS can help to identify and filter out patterns consistent with benign activity, thereby improving the accuracy of alerts. For example, a machine learning model trained on historical network data can learn to differentiate between legitimate network scans and malicious scans based on factors such as scan frequency and target selection.
Threat Hunting with NIDS Data
Threat hunting involves proactively searching for malicious activity within the network, rather than simply reacting to alerts. NIDS data provides a rich source of information for this purpose. One approach involves using NIDS logs to identify unusual network activity, such as connections to known malicious IP addresses or unusual patterns in network traffic. Another technique involves using the NIDS data to reconstruct attack chains by correlating multiple events. This might involve combining information from different NIDS sensors to trace the path of an attacker across the network. Finally, advanced analytics, such as anomaly detection, can be applied to the NIDS data to identify deviations from established baselines and pinpoint potentially malicious activity that might not trigger traditional signature-based alerts. For example, a sudden spike in traffic to a specific server could indicate a denial-of-service attack even if it doesn’t match any known attack signatures.
NIDS and Threat Intelligence
Network Intrusion Detection Systems (NIDS) are powerful tools, but their effectiveness can be significantly boosted by integrating them with threat intelligence. Threat intelligence provides context and prioritization to the alerts generated by NIDS, transforming raw data into actionable insights. This synergy allows security teams to respond more efficiently and effectively to real threats, minimizing false positives and maximizing resource allocation.
Threat intelligence feeds enhance NIDS effectiveness by providing preemptive knowledge of known malicious actors, techniques, and indicators of compromise (IOCs). By correlating NIDS alerts with threat intelligence data, security analysts can quickly identify and prioritize truly dangerous events, separating the wheat from the chaff in the flood of alerts a busy SOC faces daily. This allows for faster response times and reduces the overall workload associated with analyzing potentially thousands of alerts.
Leveraging NIDS Data for Threat Intelligence Development
NIDS data itself is a valuable source of threat intelligence. By analyzing patterns and trends in NIDS alerts, organizations can develop their own proprietary threat intelligence. For example, observing a sudden surge in connections from a specific IP address to a critical server, coupled with unusual port usage, could indicate a targeted attack. This information can be used to update internal threat intelligence databases, enabling proactive defense against future similar attacks. Furthermore, the analysis of malware signatures observed in network traffic can provide crucial information about emerging threats, potentially before they are widely known. This proactive approach allows for quicker patching and mitigation strategies, preventing widespread damage.
Potential Threat Indicators Identifiable by NIDS
The following list highlights some potential threat indicators that can be effectively identified using NIDS:
- Known malicious IP addresses: NIDS can detect connections originating from IP addresses known to be associated with malicious activities, such as botnets or command-and-control servers. This information can be cross-referenced with threat intelligence feeds to verify the threat level.
- Port scanning activity: Detecting systematic scans of open ports on network devices can indicate reconnaissance activities preceding an attack. This early warning allows for proactive security measures to be implemented.
- Unusual network traffic patterns: Significant deviations from normal network behavior, such as a sudden increase in traffic volume or unusual data transfer patterns, can indicate malicious activity. For instance, a large volume of outbound traffic to an unknown server could suggest data exfiltration.
- Exploit attempts: NIDS can detect attempts to exploit known vulnerabilities, such as buffer overflows or SQL injection attempts. Identifying these attempts allows for immediate patching and mitigation.
- Malware signatures: NIDS can detect the presence of malware signatures within network traffic, providing immediate alerts about potentially compromised systems. This can help contain the spread of malware before significant damage is done.
- Suspicious login attempts: Failed login attempts from unusual locations or using incorrect credentials can indicate brute-force attacks or compromised accounts. This can trigger alerts and lead to account lockouts or password resets.
NIDS Configuration and Management
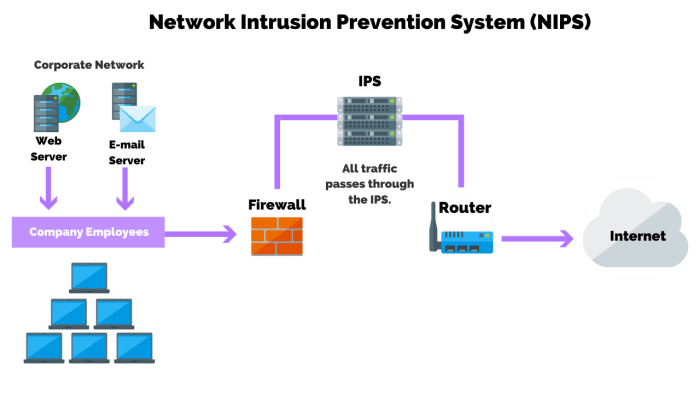
Source: purplesec.us
Effective NIDS configuration and management are crucial for maximizing their threat detection capabilities within a SOC. Poorly configured systems can generate excessive false positives, overwhelming analysts and hindering the detection of genuine threats. Conversely, well-managed NIDS provide a robust first line of defense, significantly improving the overall security posture.
Proper configuration and ongoing maintenance are not merely technical tasks; they’re vital components of a comprehensive security strategy. Ignoring these aspects can render even the most advanced NIDS ineffective, leaving your organization vulnerable to sophisticated attacks.
NIDS Sensor Tuning for Optimal Performance and Accuracy
Optimizing NIDS sensors involves a delicate balance between sensitivity and noise reduction. Overly sensitive settings generate numerous false positives, while overly restrictive settings can miss legitimate threats. The key is to fine-tune the sensors to your specific network environment and security requirements. This involves adjusting parameters like signature thresholds, anomaly detection levels, and the types of traffic monitored. For example, a financial institution might prioritize the detection of specific financial transaction anomalies, while a gaming company might focus on detecting DDoS attacks. Careful consideration of the network traffic patterns, including expected volumes and types of communication, is crucial for effective tuning. Regular performance monitoring and analysis of alert data help identify areas requiring adjustments.
The Importance of Regular NIDS Updates and Maintenance
Regular updates and maintenance are paramount to ensuring the continued effectiveness of your NIDS. NIDS vendors regularly release updates that address vulnerabilities, improve detection capabilities, and enhance performance. These updates often include new signatures for emerging threats, allowing the system to identify and respond to the latest attack vectors. Neglecting these updates leaves your organization exposed to known vulnerabilities that attackers can exploit. Maintenance includes tasks such as checking log files for errors, ensuring sufficient disk space, and verifying the integrity of the system’s configuration. Proactive maintenance minimizes downtime and maximizes the lifespan of the NIDS. Failing to implement regular updates and maintenance significantly reduces the effectiveness of the NIDS, making it a weaker security component. Consider a scenario where a critical vulnerability in the NIDS itself is exploited, potentially disabling its ability to detect threats.
Essential Tasks for NIDS Administration
A comprehensive checklist for NIDS administration should include several key tasks performed on a regular basis. These tasks ensure the system remains operational, effective, and secure.
- Regular Software Updates: Implement a schedule for applying vendor-provided updates and patches to address known vulnerabilities and enhance detection capabilities. This includes both the NIDS software itself and any associated components.
- Signature Updates: Regularly update the NIDS signature database to incorporate the latest threat intelligence. Outdated signatures significantly reduce the system’s ability to detect emerging threats.
- Log Management: Establish a robust log management system to collect, store, and analyze NIDS logs. Regularly review these logs to identify trends, anomalies, and potential security breaches.
- Performance Monitoring: Continuously monitor the NIDS performance, including CPU usage, memory consumption, and network bandwidth. Identify and address any performance bottlenecks to ensure optimal operation.
- Alert Management: Implement a process for managing and responding to NIDS alerts. This includes prioritizing alerts, investigating potential threats, and taking appropriate actions to mitigate risks.
- Capacity Planning: Regularly assess the NIDS capacity to ensure it can handle increasing network traffic and data volumes. Plan for future capacity needs to avoid performance degradation.
- Security Audits: Conduct regular security audits to identify any vulnerabilities in the NIDS configuration or operation. Address any identified vulnerabilities promptly.
Emerging Trends in NIDS for SOCs
The landscape of network security is constantly evolving, driven by the increasing sophistication of cyber threats and the rapid adoption of new technologies. Network Intrusion Detection Systems (NIDS), a cornerstone of Security Operations Centers (SOCs), are adapting to these changes, incorporating advanced capabilities to stay ahead of the curve. This section explores some of the most significant emerging trends shaping the future of NIDS in SOC environments.
The integration of cutting-edge technologies like cloud computing, virtualization, machine learning, and artificial intelligence is fundamentally transforming how NIDS are deployed and utilized, enhancing their effectiveness in detecting and responding to increasingly complex cyberattacks.
Cloud Computing and Virtualization’s Impact on NIDS Deployment
The shift towards cloud-based infrastructure and virtualization presents both challenges and opportunities for NIDS deployment. Traditional NIDS, often deployed as physical appliances, struggle to scale effectively with the dynamic nature of cloud environments. However, virtualized and cloud-native NIDS solutions offer enhanced scalability, flexibility, and cost-effectiveness. These solutions can be easily deployed and managed across multiple virtual machines or cloud instances, adapting to fluctuating network traffic demands. For example, a company migrating to a multi-cloud strategy can leverage cloud-native NIDS to monitor traffic across different cloud providers, ensuring consistent security coverage without the complexities of managing separate physical appliances. This seamless integration helps maintain comprehensive visibility and control, irrespective of the underlying infrastructure.
Machine Learning and Artificial Intelligence in Enhancing NIDS Capabilities
Machine learning (ML) and artificial intelligence (AI) are revolutionizing NIDS capabilities. Traditional signature-based NIDS rely on predefined patterns to identify known threats. ML-powered NIDS, however, can analyze vast amounts of network traffic data to identify anomalies and patterns indicative of malicious activity, even without pre-defined signatures. This allows for the detection of zero-day exploits and advanced persistent threats (APTs) that traditional methods often miss. AI algorithms can further enhance this by automatically prioritizing alerts based on severity and likelihood, reducing alert fatigue and improving the efficiency of SOC analysts. For instance, an AI-powered NIDS might identify a subtle pattern of unusual data exfiltration attempts that would be missed by a purely signature-based system, leading to earlier detection and mitigation of a potential breach.
NIDS in Detecting and Responding to Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) are sophisticated, long-term attacks often conducted by state-sponsored actors or highly organized criminal groups. Their stealthy nature makes detection challenging for traditional security tools. However, NIDS, augmented with ML and AI, play a crucial role in identifying and responding to APTs. By analyzing network traffic for unusual patterns, such as lateral movement within a network, data exfiltration to unusual destinations, or the use of command-and-control (C&C) servers, NIDS can provide early warning signs of an APT campaign. Furthermore, integrating NIDS with other security tools, such as Security Information and Event Management (SIEM) systems and threat intelligence platforms, allows for a more comprehensive understanding of the threat landscape and facilitates a coordinated response. For example, the detection of unusual DNS queries to a known C&C server, combined with threat intelligence indicating malicious activity associated with that server, can provide strong evidence of an ongoing APT attack, enabling timely intervention.
Case Studies
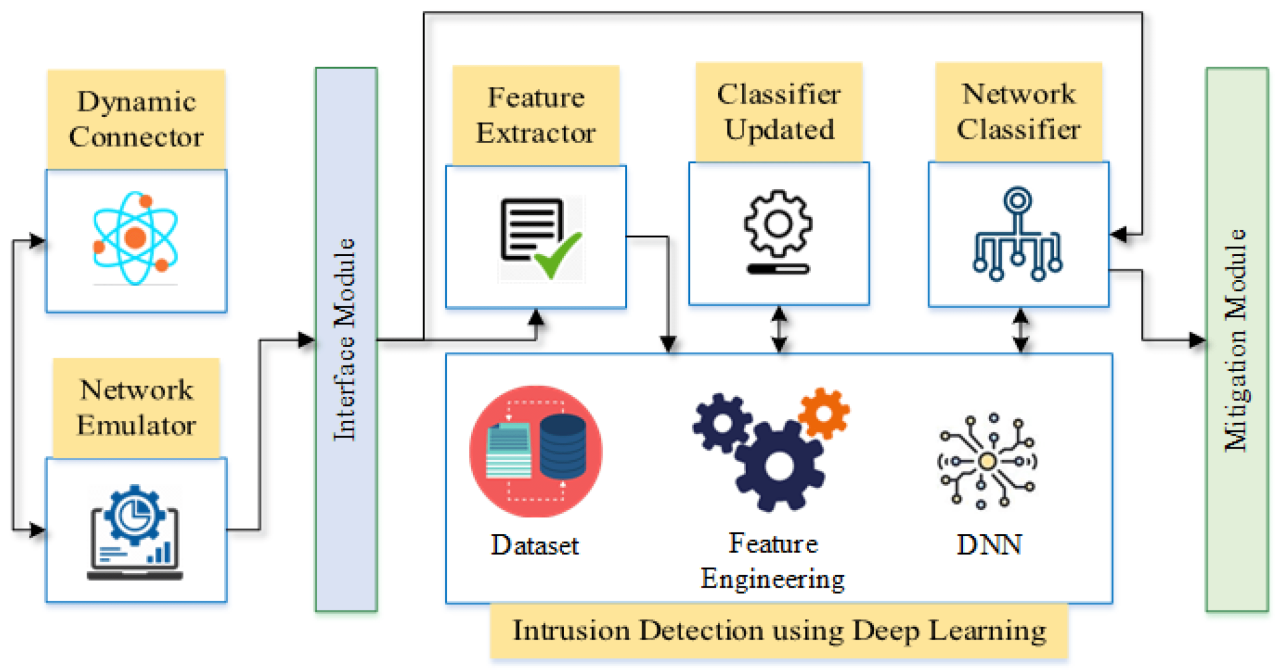
Source: mdpi-res.com
Real-world examples offer the best illustration of a Network Intrusion Detection System’s (NIDS) capabilities and limitations. Let’s dive into two distinct scenarios: one highlighting a successful NIDS-driven threat response, and another showcasing the challenges of false positives. These case studies provide valuable insights into the practical application of NIDS within a Security Operations Center (SOC).
Successful NIDS-Driven Threat Response: A Distributed Denial of Service (DDoS) Attack
A large e-commerce company experienced a sudden surge in network traffic, significantly impacting website availability. Their NIDS, a robust system monitoring various network segments, immediately detected an anomalous increase in SYN packets originating from multiple IP addresses across different geographic locations – a classic signature of a DDoS attack. The NIDS generated alerts specifying the source IP addresses, the volume of malicious traffic, and the targeted services. These alerts triggered automated responses, including traffic mitigation through a web application firewall (WAF) and routing the malicious traffic to a sinkhole. Simultaneously, the SOC team was notified, allowing them to investigate the attack further, identify the attack vector (a botnet), and implement additional security measures to prevent future attacks. The incident was resolved within an hour, minimizing service disruption and financial losses.
The rapid detection and response to the DDoS attack, enabled by the NIDS, minimized business impact and showcased the system’s effectiveness in mitigating large-scale threats.
NIDS False Positive: A Misinterpreted Port Scan
During routine monitoring, the NIDS flagged numerous alerts indicating potential port scanning activity from a specific IP address. The alerts triggered automated notifications to the SOC team, leading to an immediate investigation. However, upon closer examination of the network logs and the source IP address, the SOC team discovered that the activity originated from a legitimate security audit conducted by an external penetration testing firm. The firm had not properly communicated their testing schedule, leading to the NIDS misinterpreting the scans as malicious activity. The SOC team subsequently updated their NIDS rules to exclude the known IP address of the penetration testing firm and implemented a better communication protocol with external security vendors.
This case study highlights the importance of thorough investigation and proper configuration of NIDS rules to minimize false positives and prevent unnecessary alerts from overwhelming the SOC team. Effective communication with external security partners is also crucial.
Summary
In the ever-evolving landscape of cybersecurity, Network Intrusion Detection Systems remain a critical component of any robust SOC. Understanding their intricacies, from deployment and integration to alert analysis and threat intelligence integration, is paramount. While challenges exist, like managing false positives and adapting to new threats, the benefits of a well-configured and actively managed NIDS far outweigh the drawbacks. By embracing the power of NIDS and integrating them effectively within your SOC, you can significantly strengthen your organization’s security posture and stay ahead of the curve in the ongoing battle against cyber threats. Remember, it’s not just about detecting intrusions; it’s about responding effectively and learning from each encounter.


