Google OAuth vulnerability: It sounds scary, right? But understanding how these vulnerabilities work is crucial for anyone building or using web applications. Think of OAuth as the digital bouncer at the club – it verifies your identity before letting you in (accessing your data). But if the bouncer’s a bit lax, trouble can brew. This deep dive explores the common pitfalls in Google OAuth implementations, showing you how to spot and fix them before they become major headaches.
We’ll dissect the inner workings of Google OAuth 2.0, examining its authorization flow and common use cases. Then, we’ll get into the nitty-gritty of vulnerabilities, from client-side security flaws to insecure server configurations. We’ll also explore real-world examples of exploited vulnerabilities, revealing how attackers have successfully compromised systems and the devastating consequences. Finally, we’ll arm you with mitigation strategies and best practices to build secure and robust applications.
Understanding Google OAuth 2.0
Source: liveenhanced.com
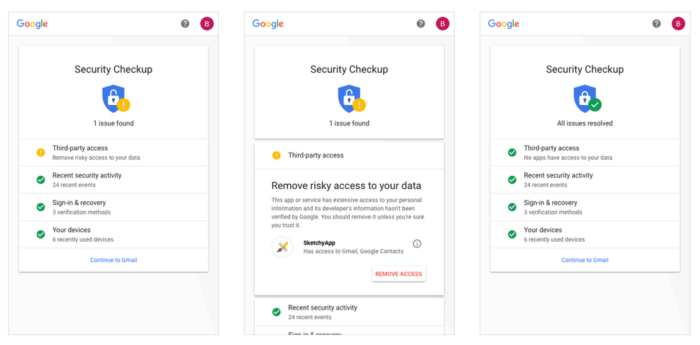
Google OAuth 2.0 is the authentication protocol that lets you access Google services and data without sharing your password directly. Think of it as a secure keycard system for your Google account, granting specific apps access only to the information they need. This system is crucial for securing your data and maintaining privacy in today’s interconnected world.
Core Components of Google OAuth 2.0
The Google OAuth 2.0 framework hinges on several key players. There’s the resource owner (you!), the resource server (like Google Drive or Gmail), the client application (the app wanting your data), and the authorization server (Google’s authentication system). These components interact through a well-defined process to ensure secure access. The authorization server verifies your identity and issues access tokens that the client application uses to access your data on the resource server. This multi-layered approach minimizes security risks.
The Authorization Flow and Grant Types
The authorization flow involves a series of steps where the client application requests access, you grant permission, and an access token is issued. Different grant types cater to various scenarios. The Authorization Code Grant is the most secure, ideal for web applications. It involves a redirect to Google’s authorization server, followed by a token exchange. The Implicit Grant is simpler but less secure, often used for single-page applications. The Refresh Token Grant allows extending the lifespan of access tokens without repeatedly requesting authorization. The Client Credentials Grant is used when the application itself needs access, without user interaction. Each grant type optimizes the balance between security and ease of implementation.
Common Use Cases for Google OAuth 2.0 in Web Applications
Google OAuth 2.0 is widely used in web apps to allow users to log in using their Google accounts, eliminating the need for separate usernames and passwords. This simplifies the user experience and enhances security. Many applications leverage OAuth 2.0 to access user data like profile information, contacts, calendar events, or emails, subject to the user’s permissions. Consider popular apps that allow you to share your Google Calendar or Google Drive files – they almost certainly utilize OAuth 2.0 for secure access.
Examples of OAuth 2.0 Tokens for API Access
Once you’ve granted permission, the client application receives an access token. This token is like a temporary password, allowing the application to make requests to Google APIs on your behalf. For instance, if an app wants to display your Google Calendar events, it uses the access token in the header of its API requests to Google Calendar’s servers. The server verifies the token and, if valid, returns the requested data. This token-based authentication ensures that only authorized requests are processed. This process happens behind the scenes, ensuring a seamless user experience.
Comparison of OAuth 2.0 with Other Authentication Protocols
| Protocol | Security | Complexity | Use Cases |
|---|---|---|---|
| OAuth 2.0 | High (especially with Authorization Code Grant) | Moderate | Web apps, mobile apps, APIs |
| OpenID Connect (OIDC) | High | High | User authentication and authorization |
| Basic Authentication | Low | Low | Simple scenarios, limited security |
| API Keys | Low | Low | Machine-to-machine communication |
Common Vulnerabilities in Google OAuth Implementations: Google Oauth Vulnerability
Source: cybersecuritynews.com
Google OAuth 2.0, while a robust authorization framework, isn’t immune to vulnerabilities. Improper implementation on the developer’s side often opens the door to security breaches, potentially exposing user data and compromising application integrity. Let’s dive into some common pitfalls.
Client-Side Security Vulnerabilities
Client-side vulnerabilities are a significant concern. Malicious actors can exploit weaknesses in a web application’s JavaScript code or manipulate the user’s browser to intercept OAuth tokens or redirect users to phishing sites. This can happen if the application doesn’t properly validate the origin of OAuth callbacks or if sensitive data is exposed through insecure client-side storage. A common example is the lack of HTTPS for all communication involving OAuth flows. Without HTTPS, sensitive data transmitted between the client and the authorization server can be intercepted by attackers using techniques like man-in-the-middle attacks. Another vulnerability is the insecure storage of access tokens in local storage or session storage, which can be accessed by malicious scripts running in the browser.
Risks Associated with Improper Token Management
Mishandling OAuth tokens is a recipe for disaster. Tokens, representing the user’s authorization, must be treated with utmost care. Storing tokens insecurely, failing to refresh them properly, or not revoking them when no longer needed leaves the application vulnerable. Imagine a scenario where an application stores access tokens in plain text within its database – a simple SQL injection attack could expose all user tokens, granting attackers complete access to user accounts. Similarly, failure to implement proper token revocation mechanisms means that even after a user logs out, compromised tokens might still grant access to sensitive resources. Proper token management requires secure storage, timely revocation, and the use of short-lived tokens with refresh tokens for long-lived access.
Dangers of Insecure Authorization Server Configurations
The authorization server itself needs to be bulletproof. Misconfigurations, such as weak passwords or insufficient logging and monitoring, can create significant vulnerabilities. For instance, an authorization server with default credentials or poorly configured access controls could be easily compromised, giving attackers access to all user data and potentially allowing them to impersonate users. Furthermore, a lack of robust rate limiting and input validation mechanisms could lead to denial-of-service attacks or data breaches through injection attacks. Regular security audits and updates are crucial for maintaining a secure authorization server.
Vulnerabilities Arising from Flawed Authorization Code Handling
Improper handling of authorization codes is another critical vulnerability. Authorization codes are temporary, short-lived codes exchanged during the OAuth flow. If not handled securely, they can be intercepted and used to obtain access tokens without the user’s knowledge. A common mistake is to expose authorization codes directly in URLs or to use insecure communication channels when exchanging them for access tokens. Attackers can exploit this to perform various malicious actions, such as gaining unauthorized access to user accounts or manipulating application data. Therefore, it’s crucial to ensure that authorization codes are handled with the same level of security as access tokens. They should never be exposed directly and should always be exchanged using secure HTTPS connections.
Secure Implementation of Google OAuth 2.0 in a Sample Application
A secure implementation involves several key steps. First, use HTTPS for all communication with the Google OAuth 2.0 authorization server and the resource server. Second, store access and refresh tokens securely, ideally using a secure key management system or a dedicated token store with robust encryption and access controls. Third, implement proper token revocation mechanisms, ensuring that tokens are revoked when no longer needed. Fourth, validate the origin of OAuth callbacks to prevent redirection attacks. Fifth, regularly update your application and its dependencies to patch any known security vulnerabilities. Finally, implement robust input validation and sanitization to prevent injection attacks. A simple example could involve using a secure backend service to handle the OAuth flow, ensuring that sensitive data never directly touches the client-side code. The backend would be responsible for managing tokens, making API calls, and securely handling user data. This architectural approach significantly reduces the risk of client-side vulnerabilities.
Mitigation Strategies and Best Practices
Securing your Google OAuth 2.0 implementation isn’t just about ticking boxes; it’s about building a robust, resilient system that protects user data and maintains trust. Ignoring security best practices can lead to serious vulnerabilities, exposing your application and its users to significant risks. Let’s explore the crucial steps you can take to mitigate these risks.
Robust input validation is paramount in preventing injection attacks, a common vulnerability in many OAuth implementations. Failing to properly sanitize user inputs opens the door to SQL injection, cross-site scripting (XSS), and other malicious exploits. By implementing rigorous validation, you create a significant barrier against these attacks.
Input Validation Best Practices
Implementing robust input validation involves several key strategies. First, always validate and sanitize all user inputs before using them in any database queries or dynamic code generation. This includes checking data types, lengths, and formats, ensuring they conform to expected parameters. Second, utilize parameterized queries or prepared statements to prevent SQL injection. These techniques separate data from SQL code, preventing malicious code from being executed. Third, employ output encoding to neutralize potentially harmful characters in data displayed to the user, mitigating XSS attacks. Finally, regularly update your libraries and frameworks to patch known vulnerabilities. Failing to update leaves your application vulnerable to exploits that have already been identified and addressed by security experts. For instance, neglecting to update a vulnerable library could allow an attacker to inject malicious JavaScript code, potentially stealing user credentials or compromising the entire system.
OAuth Token Security, Google oauth vulnerability
Protecting OAuth tokens is critical. Tokens should be treated as highly sensitive data, requiring stringent security measures. Storing tokens insecurely or improperly handling their lifecycle can lead to unauthorized access and data breaches.
- Use HTTPS Everywhere: Always transmit tokens over HTTPS to prevent eavesdropping and interception. HTTPS encrypts the communication channel, ensuring that tokens remain confidential during transit.
- Short-Lived Tokens: Employ short-lived access tokens, refreshing them frequently. This limits the impact of compromised tokens. If a token is compromised, its limited lifespan minimizes the damage.
- Token Revocation: Implement a robust token revocation mechanism. This allows you to invalidate tokens immediately if a security breach occurs, preventing further unauthorized access.
- Secure Storage: Store tokens securely, using encryption and appropriate access controls. Never store tokens in plain text. For example, using encryption at rest and in transit protects tokens from unauthorized access even if a system is compromised.
Secure Communication Channels
Using HTTPS is not merely a best practice; it’s a fundamental requirement for securing any application that handles sensitive data, including OAuth tokens. HTTPS encrypts the communication between the client and the server, protecting the data from interception and modification. This prevents attackers from eavesdropping on the communication and stealing sensitive information, such as OAuth tokens. Consider implementing HTTP Strict Transport Security (HSTS) to enforce HTTPS usage and prevent downgrade attacks. HSTS instructs browsers to only connect to the website over HTTPS, preventing any accidental or malicious redirection to HTTP.
Security Checklist for Google OAuth Developers
Before deploying any application using Google OAuth, carefully review this checklist:
- Input Validation: Have you implemented robust input validation to prevent injection attacks?
- HTTPS: Are all communication channels secured using HTTPS and HSTS?
- Token Security: Are OAuth tokens stored securely, using encryption and appropriate access controls? Are tokens short-lived and revoked promptly when necessary?
- Authorization: Have you implemented proper authorization controls to ensure that users only access resources they are permitted to?
- Error Handling: Does your application handle errors gracefully, preventing the disclosure of sensitive information?
- Regular Updates: Are all libraries and frameworks regularly updated to patch known vulnerabilities?
- Security Audits: Have you conducted regular security audits and penetration testing to identify and address potential vulnerabilities?
Real-World Examples of Exploited Vulnerabilities
Understanding the theoretical vulnerabilities of Google OAuth is crucial, but seeing them in action paints a clearer picture. Let’s delve into some real-world examples of exploited vulnerabilities, highlighting the impact and methods used by attackers. These examples aren’t meant to scare you, but to arm you with knowledge to prevent similar situations.
The following examples illustrate how various vulnerabilities have been exploited in the past, emphasizing the importance of robust security practices. We’ll categorize them by vulnerability type for clarity.
Cross-Site Request Forgery (CSRF) Exploits
CSRF attacks exploit the trust relationship between a user and a website. Attackers trick users into performing unwanted actions on a trusted site. In the context of OAuth, this could involve unknowingly granting access to an attacker’s application.
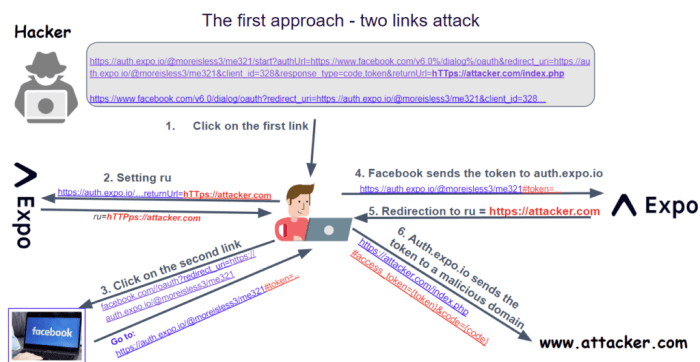
- Example 1: A malicious website might embed a hidden form that initiates an OAuth authorization request to a legitimate service. If a user is logged into that service and visits the malicious site, they might unknowingly grant the attacker access without realizing it. The impact is the attacker gaining unauthorized access to the user’s data on the target service. The exploitation hinges on the user’s already established session with the legitimate service and the lack of CSRF protection on the authorization endpoint.
- Example 2: Imagine a scenario where a compromised website includes a cleverly disguised link. When clicked, this link triggers an OAuth flow, granting access to an attacker-controlled application without explicit user consent. The consequences range from data breaches to account hijacking, depending on the permissions granted. The vulnerability is exploited by leveraging the user’s active session and the lack of appropriate anti-CSRF measures.
Authorization Bypass Vulnerabilities
These vulnerabilities allow attackers to circumvent the intended authorization mechanisms, gaining access to resources they shouldn’t have. This often involves exploiting flaws in the implementation of OAuth itself.
- Example: A flaw in how an application validates OAuth tokens could allow an attacker to forge or manipulate tokens, gaining access to protected resources without proper authorization. The impact could be catastrophic, potentially leading to a complete compromise of the application’s data and functionality. Exploitation often involves reverse-engineering the token validation process to find weaknesses and create fraudulent tokens.
Cross-Site Scripting (XSS) Vulnerabilities in OAuth Flows
XSS vulnerabilities can be injected into OAuth flows, allowing attackers to steal user tokens or redirect users to malicious websites. This often involves injecting malicious JavaScript code into the OAuth authorization process.
- Example: An attacker might inject malicious JavaScript code into an OAuth callback URL. When the user is redirected back to the application after successful authentication, this malicious code executes, stealing the OAuth token and potentially compromising the user’s account. The impact includes data breaches, account hijacking, and potential further attacks leveraging the stolen token. The exploitation relies on the lack of proper input sanitization and output encoding in the OAuth flow.
Advanced Attack Vectors and Defense Mechanisms

Source: lifeboat.com
Beyond the common vulnerabilities, sophisticated attackers employ advanced techniques to exploit weaknesses in Google OAuth implementations. These attacks often leverage social engineering and exploit human error to gain unauthorized access. Understanding these advanced vectors is crucial for implementing robust defense mechanisms.
Advanced attacks go beyond simple credential stuffing or exploiting known vulnerabilities. They often involve a combination of techniques, targeting both technical flaws and human vulnerabilities. This makes them particularly challenging to defend against, requiring a multi-layered approach to security.
Social Engineering in OAuth Attacks
Social engineering plays a significant role in OAuth compromises. Attackers might use deceptive emails or messages, pretending to be legitimate services or individuals, to trick users into revealing their OAuth credentials or granting access to malicious applications. This often involves creating convincing phishing websites that mimic the look and feel of legitimate Google login pages. The attacker might exploit trust and urgency to pressure the victim into quick action, bypassing their usual security protocols. For example, an attacker could send an email claiming to be from Google, stating that the user’s account has been compromised and needs immediate verification through a provided link—a link leading to a fake login page designed to capture OAuth tokens.
Phishing and Credential Stuffing in OAuth Compromises
Phishing remains a potent threat. Attackers create fake login pages designed to steal usernames and passwords, which can then be used to obtain OAuth tokens. Credential stuffing, on the other hand, involves using lists of stolen credentials obtained from previous data breaches to attempt logins to various services, including those using OAuth. Because many users reuse passwords across multiple platforms, a successful credential stuffing attempt on one service can potentially grant access to others, including those utilizing OAuth. The scale of credential stuffing attacks makes them a significant threat, as automated tools can rapidly test thousands of credentials against a target system.
Defense Mechanisms Against Advanced Attacks
A multi-layered approach is necessary to effectively mitigate advanced OAuth attacks. This involves a combination of technical and non-technical measures. Strong password policies, multi-factor authentication (MFA), and regular security awareness training for employees are crucial. Furthermore, implementing robust security protocols such as OAuth 2.0 best practices, regular security audits, and the use of security information and event management (SIEM) systems are essential for detecting and responding to attacks. Regularly updating software and employing web application firewalls (WAFs) can help to mitigate some of the technical vulnerabilities that attackers might exploit.
Illustrative Sophisticated Attack Scenario
Imagine a scenario where an attacker compromises an employee’s email account through a sophisticated phishing campaign. This email account has access to the company’s internal systems through OAuth. The attacker then uses the compromised account to gain access to a privileged application. This application might allow the attacker to read sensitive data, modify settings, or even deploy malware. The attacker’s success relies on a combination of social engineering to gain initial access to the email account and the exploitation of an OAuth-based authentication system to access sensitive internal resources. This highlights the importance of robust security measures, including MFA and regular security awareness training, to prevent such attacks. The attack unfolds in stages: 1. Phishing Email Sent, 2. Credentials Compromised, 3. OAuth Token Obtained, 4. Access to Internal Systems, 5. Data Breach/Malware Deployment. Each stage represents a point of potential failure that can be addressed with appropriate security controls.
Closing Notes
Securing your Google OAuth implementation isn’t just about following best practices; it’s about understanding the attacker’s mindset. By anticipating potential vulnerabilities and implementing robust security measures, you can significantly reduce your risk. Remember, a well-protected system is a proactive system. Stay vigilant, stay informed, and stay secure. The digital world is a wild place; let’s make sure your data stays safe.