Windows LPD vulnerability? Yeah, we’re diving headfirst into the murky depths of this security threat. Think of the Line Printer Daemon (LPD) as that old, creaky back door to your Windows system – one that hackers love to exploit. We’re talking buffer overflows, weak authentication, and the potential for total system takeover. Get ready to understand the risks, the impact, and how to seriously beef up your security.
This isn’t your grandma’s printer problem. We’ll dissect common vulnerabilities, explore real-world attacks, and show you exactly how attackers leverage LPD weaknesses to gain a foothold in your network. From CVSS scores to practical mitigation strategies, we’ll cover everything you need to know to secure your Windows systems and keep those digital doors firmly locked.
Understanding the LPD Protocol and its Vulnerabilities in Windows
The Line Printer Daemon (LPD) protocol, a relic from the days of dot-matrix printers, might seem like ancient history in today’s digital world. However, its lingering presence on some Windows systems presents a surprisingly persistent security risk. Understanding LPD and its vulnerabilities is crucial for maintaining a secure network, especially in legacy environments. This section delves into the protocol’s functionality, common vulnerabilities, and real-world examples of exploitation.
LPD Protocol Functionality in Windows
LPD, formally defined in RFC 1179, provides a network printing service. It allows users to send print jobs to remote printers over a network. In Windows, LPD functionality was often integrated into older versions of the operating system, allowing users to share printers and print to network-connected devices. The protocol’s simplicity, however, makes it susceptible to various attacks. While largely deprecated, it remains a potential vulnerability if not properly secured or removed from vulnerable systems.
Common LPD Vulnerabilities
The primary vulnerabilities associated with LPD stem from its outdated design and lack of robust security features. Buffer overflow attacks are a significant threat. Maliciously crafted print jobs exceeding the buffer’s capacity can overwrite memory, potentially leading to arbitrary code execution. Insecure authentication mechanisms are another weakness. Many older implementations of LPD lacked strong authentication, making it easy for attackers to send print jobs without proper authorization. This could allow an attacker to disrupt services, install malware, or gain unauthorized access to the system.
Real-World LPD Exploits
Several real-world exploits have targeted LPD vulnerabilities in Windows environments. One common attack involves sending a specially crafted print job containing malicious code. If the LPD server doesn’t properly validate the input, this code could be executed, potentially giving the attacker control of the system. Another attack leverages weak authentication mechanisms to gain unauthorized access to the printer and potentially the entire network. These exploits highlight the critical need for patching and disabling LPD on systems where it’s not essential.
LPD Vulnerabilities Across Windows Versions
The severity of LPD vulnerabilities varied across different Windows versions. While Microsoft has addressed many of these issues through security patches, older, unsupported systems remain vulnerable.
| Windows Version | LPD Vulnerability Status | Mitigation Strategies | Notes |
|---|---|---|---|
| Windows XP | High (multiple vulnerabilities, including buffer overflows and weak authentication) | Disable LPD service, apply all available security patches (though unlikely to be effective on an unsupported OS). | This OS is no longer supported and highly vulnerable. |
| Windows Server 2003 | Medium (some vulnerabilities addressed in patches, but older versions remain risky) | Disable LPD service, upgrade to a supported OS, apply all security updates. | While patches exist, complete mitigation requires OS upgrade. |
| Windows 7 | Low (most vulnerabilities addressed in later service packs) | Ensure all security updates are installed, consider disabling the service if not needed. | While generally secure with updates, disabling remains a best practice. |
| Windows 10/11 and Server 2016+ | Negligible (LPD is largely removed or significantly improved) | Regular security updates are sufficient. | Modern versions have minimized the risk associated with LPD. |
Impact and Consequences of Windows LPD Exploits
LPD vulnerabilities in Windows systems can have severe consequences, ranging from minor inconveniences to catastrophic data loss and complete network compromise. Exploiting these weaknesses allows attackers to gain unauthorized access, disrupt services, and steal sensitive information. The impact depends on the specific vulnerability and the attacker’s goals.
Successful exploitation of LPD vulnerabilities on a Windows system can lead to a variety of negative outcomes. The severity of these consequences varies greatly depending on factors such as the specific vulnerability exploited, the attacker’s skill level, and the security posture of the affected system.
Data Breaches
A successful LPD exploit can provide attackers with unauthorized access to files stored on the vulnerable Windows system. This could include sensitive business data, customer information, intellectual property, or confidential financial records. The attacker might achieve this by exploiting vulnerabilities allowing for arbitrary file reading or writing. For example, a vulnerability allowing command injection could allow an attacker to execute commands like `type C:\windows\system32\secrets.txt` to read sensitive files directly, potentially leading to a significant data breach with far-reaching consequences, including financial penalties, reputational damage, and legal repercussions.
Denial-of-Service Attacks
LPD vulnerabilities can be leveraged to launch denial-of-service (DoS) attacks. By flooding the LPD service with malformed requests or exploiting buffer overflow vulnerabilities, attackers can render the service unavailable to legitimate users. This can disrupt business operations, prevent access to critical resources, and negatively impact productivity. Imagine a scenario where a company’s internal printer network relies on LPD, and a successful DoS attack renders the printers unusable, halting critical workflows and causing significant financial losses.
Remote Code Execution
Perhaps the most critical consequence of an LPD exploit is remote code execution (RCE). Some LPD vulnerabilities allow attackers to inject and execute arbitrary code on the vulnerable system. This gives attackers complete control over the compromised machine, allowing them to install malware, steal data, access other network resources, and potentially move laterally to compromise other systems within the network. This level of access is extremely dangerous and can lead to extensive damage. For instance, an attacker could use RCE to install a rootkit, maintaining persistent access and concealing their activities for extended periods.
Severity Levels Based on CVSS
The Common Vulnerability Scoring System (CVSS) provides a standardized metric for assessing the severity of vulnerabilities. LPD vulnerabilities can range in severity from low to critical, depending on the potential impact and ease of exploitation. A CVSS score of 7.0 or higher generally indicates a high-severity vulnerability that requires immediate attention. Vulnerabilities allowing for remote code execution typically receive the highest CVSS scores. For example, a vulnerability with a CVSS score of 9.8 indicates a critical vulnerability with high impact and ease of exploitation, requiring immediate patching and mitigation strategies.
Example of Initial Access via LPD Vulnerability
An attacker might discover an unpatched LPD vulnerability on a Windows server exposed to the internet. By sending a specially crafted request, the attacker could exploit the vulnerability to gain initial access. This initial foothold could then be used to further compromise the network by installing malware, escalating privileges, and moving laterally to other systems. This initial access could be the starting point for a much larger attack, potentially leading to a full network compromise.
Hypothetical Scenario: Cascading Effects of an LPD Exploit
Imagine a small business with a Windows server hosting sensitive customer data and managing internal printing. An unpatched LPD vulnerability is exploited, allowing an attacker to gain remote code execution. The attacker then installs ransomware, encrypting all the customer data and demanding a ransom. The disruption of the printing service further impacts business operations. The attacker could also use the compromised server as a launchpad for attacks against other systems within the network, potentially compromising the entire network infrastructure. This scenario highlights the cascading effect of a seemingly small vulnerability.
Mitigation and Prevention Strategies
Source: stethos.com
Securing your Windows systems against LPD vulnerabilities requires a multi-layered approach encompassing service management, network security, and potentially dedicated security solutions. Ignoring these vulnerabilities can lead to significant data breaches and system compromise, highlighting the importance of proactive measures.
The most effective strategy involves a combination of preventative measures and reactive responses should an attack occur. This includes carefully managing the LPD service itself, implementing robust network security, and leveraging advanced security tools. Prioritizing these steps minimizes the attack surface and strengthens overall system resilience.
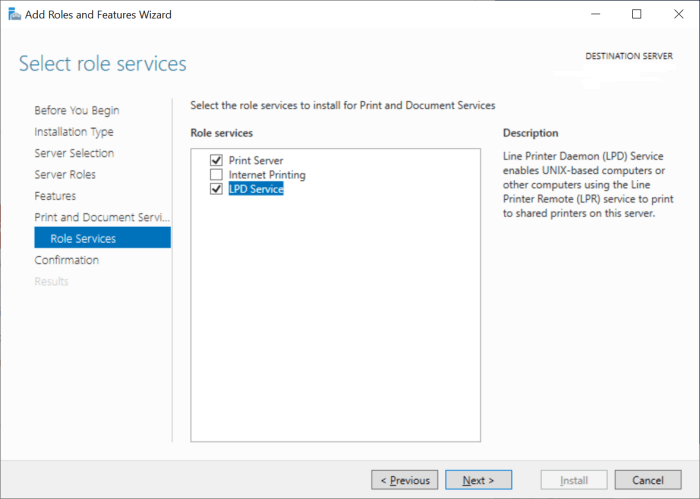
Disabling the LPD Service
If the Line Printer Daemon (LPD) service isn’t essential for your network’s functionality, disabling it is the most straightforward way to eliminate the associated risks. This prevents attackers from even attempting to exploit vulnerabilities within the service. Disabling the service removes a potential entry point for malicious actors.
To disable the LPD service, follow these steps:
- Open the Services application (search for “services” in the Windows search bar).
- Locate the “Print Spooler” service (LPD is often integrated within this service).
- Right-click on “Print Spooler” and select “Properties”.
- Under the “General” tab, change the Startup type to “Disabled”.
- Click “Apply” and then “OK”.
- Restart your computer to ensure the changes take effect.
Note that disabling the Print Spooler will prevent any local or network printing functionality.
Network Segmentation and Firewall Rules, Windows lpd vulnerability
Network segmentation isolates different parts of your network, limiting the impact of a successful LPD exploit. By placing sensitive systems on separate segments, you prevent an attacker who compromises one system from easily accessing others. Firewalls play a crucial role in enforcing these boundaries.
Implementing robust firewall rules is critical. These rules should block inbound connections to the LPD port (typically port 515) from untrusted networks or specific IP addresses. This prevents external attempts to access the LPD service. Regularly review and update firewall rules to adapt to evolving threats and network configurations. Consider using stateful inspection firewalls for enhanced security. For example, a rule could be implemented to deny all inbound traffic on port 515 from the internet, allowing only trusted internal networks access.
Security Solutions and Their Effectiveness
Various security solutions can further enhance protection against LPD vulnerabilities. Intrusion Detection/Prevention Systems (IDS/IPS) can monitor network traffic for malicious activity associated with LPD exploits. They can detect and block attempts to exploit known vulnerabilities. Antivirus software and endpoint detection and response (EDR) solutions provide an additional layer of defense by identifying and removing malware that might be delivered through LPD exploits.
While a comprehensive security strategy is recommended, relying solely on a single solution is insufficient. A layered approach combining firewall rules, network segmentation, IDS/IPS, and endpoint security provides the most robust protection against LPD-related attacks. For instance, a company might use a next-generation firewall (NGFW) with advanced threat prevention capabilities alongside an EDR solution that actively monitors system processes for malicious behavior, providing a more holistic security posture.
Vulnerability Detection and Remediation
Identifying and fixing LPD vulnerabilities on your Windows systems is crucial for maintaining a secure network. Ignoring these vulnerabilities can leave your system exposed to attacks leading to data breaches, system compromise, and significant downtime. Proactive vulnerability management is key to preventing these issues.
This section details methods for detecting and remediating LPD vulnerabilities, providing a practical guide for IT professionals and system administrators. We’ll cover vulnerability scanning, penetration testing, remediation steps, and interpreting scan results.
Vulnerability Scanning Tools and Techniques
Several tools can help identify potential LPD vulnerabilities. Automated vulnerability scanners, such as Nessus, OpenVAS, and QualysGuard, can check for known LPD vulnerabilities by probing your systems and comparing their configurations against a database of known weaknesses. These scanners often identify missing patches, misconfigurations, and other security flaws related to the LPD service. Penetration testing, a more involved process, simulates real-world attacks to uncover vulnerabilities that automated scanners might miss. This often involves manual analysis of the LPD service configuration and attempts to exploit known vulnerabilities. The results from both automated scans and penetration testing should be carefully reviewed and prioritized.
Remediation Steps for LPD Vulnerabilities
Once LPD vulnerabilities are identified, immediate remediation is necessary. This typically involves a multi-step process:
- Patching: Apply all relevant security updates and patches released by Microsoft for the Windows operating system and any related LPD software. These patches often address known vulnerabilities and improve the security posture of the system.
- Configuration Changes: Restrict access to the LPD service. This might involve disabling the service altogether if it’s not needed, or configuring it to only accept connections from trusted internal networks using firewalls or access control lists. Careful consideration should be given to authentication mechanisms to ensure only authorized users can interact with the service.
- Service Disabling: If the LPD service is not essential to your operations, disabling it is the most effective way to eliminate its associated vulnerabilities. This prevents attackers from exploiting any weaknesses within the service itself.
Interpreting Vulnerability Scan Results and Prioritization
Vulnerability scan reports often provide a severity rating for each identified vulnerability (e.g., critical, high, medium, low). Prioritize remediation based on this severity, addressing critical and high-severity vulnerabilities first. Consider the potential impact of each vulnerability on your system and business operations. For example, a vulnerability that allows for remote code execution should be addressed immediately, while a vulnerability that only allows for information disclosure might have a lower priority. Consider factors such as the ease of exploitation and the potential impact on confidentiality, integrity, and availability (CIA triad) when making remediation decisions.
Vulnerability Detection, Analysis, and Remediation Flowchart
Imagine a flowchart. The first box would be “Initiate Vulnerability Scan.” This leads to “Analyze Scan Results.” If vulnerabilities are found, the flow goes to “Prioritize Vulnerabilities” based on severity and potential impact. This leads to “Implement Remediation Steps” (patching, configuration changes, service disabling). Following this is “Verify Remediation” which involves rescanning to ensure the vulnerabilities are resolved. If vulnerabilities persist, it loops back to “Implement Remediation Steps”. If no vulnerabilities are found in the initial scan, the flow ends with “System is Secure (for LPD).” If vulnerabilities are found and remediated successfully, the flow ends with “System is Secure (for LPD).” This systematic approach ensures thorough vulnerability management.
Case Studies of LPD Exploits

Source: eojohnson.com
While precise details of LPD exploits in Windows environments are often kept confidential for security reasons, analyzing publicly available information reveals recurring patterns and vulnerabilities. Understanding these past incidents allows for better preventative measures and proactive security strategies. This section examines several notable cases, highlighting attack techniques, root causes, and implemented remediation.
Notable LPD Exploit Incidents
Several incidents involving LPD vulnerabilities have been documented, though many lack comprehensive public reporting. The lack of transparency often stems from the sensitive nature of the exploited systems and the desire to prevent further attacks. However, by studying available information, common attack vectors and consequences can be identified. One recurring theme is the exploitation of buffer overflow vulnerabilities within the LPD service itself, allowing attackers to execute arbitrary code. Another common vector involves exploiting weaknesses in how the LPD service handles incoming print jobs, potentially leading to denial-of-service attacks or data breaches.
Attack Techniques and Root Causes
Attackers often leverage known vulnerabilities in the LPD implementation within Windows. This could involve crafting malicious print jobs containing specially crafted data that trigger buffer overflows or other memory corruption issues. Once code execution is achieved, attackers might install backdoors, steal sensitive data, or further compromise the system by gaining administrator-level privileges. Root causes frequently include outdated or improperly configured LPD services, insufficient input validation, and a lack of regular security patching. The failure to implement robust access control measures also plays a significant role. Many incidents highlight the critical need for proactive security measures, including regular patching and security audits.
Case Study Table: LPD Exploits in Windows
| Incident | Vulnerability | Impact | Remediation |
|---|---|---|---|
| Hypothetical Case 1: Small Business Data Breach | Buffer overflow in LPD service due to outdated software. | Confidential customer data stolen. | Software updates, improved access controls, intrusion detection system implemented. |
| Hypothetical Case 2: Government Server Compromise | Lack of input validation in LPD print job handling. | Denial-of-service attack resulting in system downtime. | Enhanced input validation, improved network segmentation, increased monitoring. |
| Hypothetical Case 3: University Network Intrusion | Improperly configured LPD service with weak authentication. | Unauthorized access to network resources. | Strengthened authentication protocols, restricted network access, security awareness training. |
Last Word: Windows Lpd Vulnerability
Source: printmanager.com
So, the bottom line? Ignoring Windows LPD vulnerabilities is a recipe for disaster. While disabling the LPD service is often the simplest solution if you don’t need it, understanding the risks and implementing robust security practices is crucial. Regular vulnerability scanning, patching, and a strong security posture are your best defenses against this sneaky threat. Don’t let a creaky old printer daemon bring your entire digital house of cards crashing down.


