UEFI Secure Boot bypass vulnerability: Sounds like something straight out of a cyberpunk thriller, right? It’s actually a serious security flaw that lets hackers sidestep crucial system protections. Think of it as the digital equivalent of picking the lock on your front door before even reaching for your keys. This vulnerability exploits weaknesses in the UEFI (Unified Extensible Firmware Interface), the software that starts your computer before the operating system loads. We’ll unpack how this works, the sneaky ways attackers exploit it, and what you can do to stay safe.
This isn’t just some theoretical threat; real-world examples show how easily malicious code can be injected, leading to everything from data theft to full system compromise. We’ll explore various attack vectors, from software-based tricks to hardware-level exploits, and dissect the consequences of a successful bypass. We’ll also cover practical steps to mitigate these risks, including firmware updates and best practices for developers and system administrators.
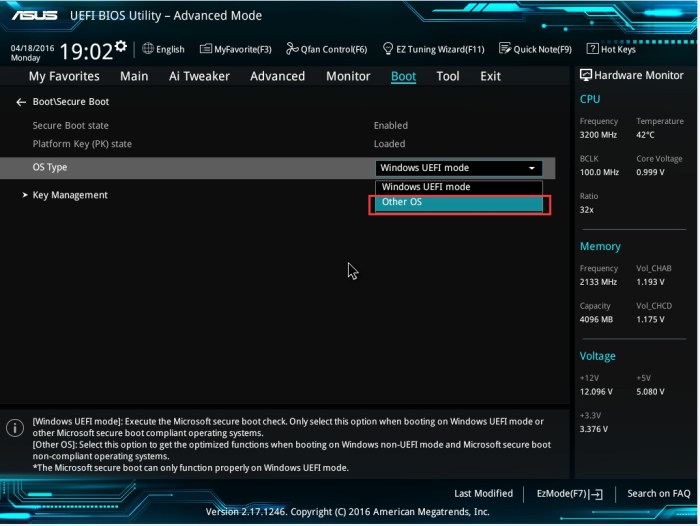
UEFI Secure Boot Mechanisms
Source: pugetsystems.com
UEFI Secure Boot is a critical security feature designed to protect systems from malicious bootloaders and rootkits. It ensures that only authorized software, digitally signed by trusted parties, can load during the boot process. This significantly reduces the attack surface for malware targeting the most vulnerable stage of a computer’s lifecycle – startup. Understanding its mechanisms is key to appreciating its effectiveness and limitations.
UEFI Secure Boot Components and Verification Process
The core of UEFI Secure Boot lies in its chain of trust. This chain starts with the firmware itself and extends to the operating system loader and finally, the operating system. During the boot process, each component verifies the digital signature of the next component in the chain before allowing execution. This process begins with the firmware verifying its own integrity, then checking the signature of the Secure Boot variables, which contain information about authorized bootloaders. The bootloader then verifies the signature of the operating system kernel, and finally, the OS kernel verifies the integrity of its own components. Any mismatch in signatures triggers a boot failure, preventing unauthorized software from loading. The entire process is cryptographically secured, making it difficult for attackers to tamper with the boot sequence without detection.
Secure Boot Implementations Across Platforms
While the core principles of Secure Boot remain consistent, its implementation varies slightly across different operating systems. Windows, for instance, utilizes its own certificate store and signing process for drivers and bootloaders. Linux distributions typically rely on a more flexible approach, allowing users to configure which keys are trusted. macOS, like Windows, has a more integrated and controlled Secure Boot implementation, focusing on Apple-signed software. These differences reflect the varying security models and user control philosophies of each operating system. While the basic concept of chain-of-trust remains, the specifics of key management and enforcement differ.
Secure Boot Process Flowchart
Imagine a flowchart depicting the Secure Boot process. It would begin with the UEFI firmware initializing and performing self-verification. This is followed by a check of the Secure Boot variables, ensuring their integrity and authenticity. Next, the flowchart would illustrate the selection and verification of the boot loader, checking its digital signature against the trusted keys stored in the firmware. The verified bootloader then loads the operating system kernel, whose signature is subsequently verified. Finally, the operating system kernel initializes, completing the secure boot process. Any failure at any verification point results in a halt, preventing the loading of untrusted software. This visual representation clearly demonstrates the layered security provided by Secure Boot.
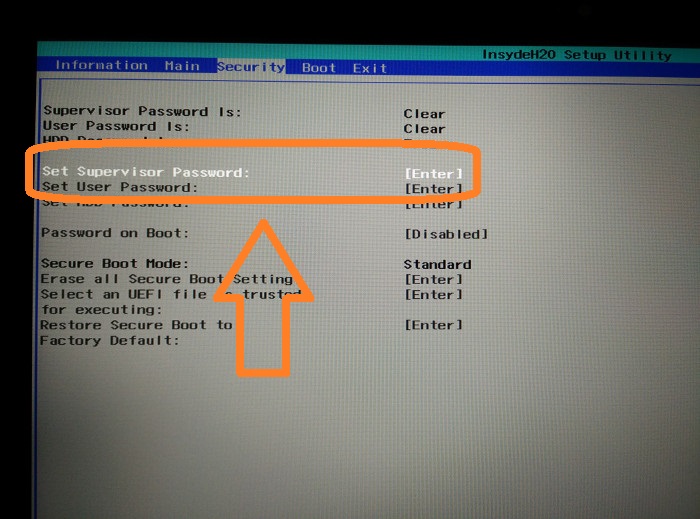
UEFI Secure Boot Bypass Vulnerabilities
Secure Boot, while designed to enhance system security, isn’t impenetrable. Clever attackers have found ways to circumvent its protections, exploiting vulnerabilities in the system’s design and implementation. These bypass methods can be broadly categorized as software-based and hardware-based, each with its own unique characteristics and impact. Understanding these vulnerabilities is crucial for bolstering your system’s defenses.
Software-based attacks leverage weaknesses in the software components of the UEFI firmware itself or in the chain of trust established during the boot process. These attacks often involve manipulating bootloaders, drivers, or other software components to gain unauthorized access. Hardware-based attacks, on the other hand, directly target the hardware components of the system, often requiring physical access. This makes them more difficult to detect and mitigate.
Software-Based UEFI Secure Boot Bypass Vulnerabilities
Software-based vulnerabilities exploit weaknesses in the UEFI firmware’s code or its interaction with other software. These attacks often involve modifying existing components or introducing malicious ones to subvert the Secure Boot process. For example, a vulnerability might exist in a specific driver that allows an attacker to load a malicious kernel, effectively bypassing the Secure Boot restrictions. The impact of these vulnerabilities can range from unauthorized access to complete system compromise, depending on the sophistication of the attack.
Hardware-Based UEFI Secure Boot Bypass Vulnerabilities
Hardware-based bypasses are significantly more challenging to detect and mitigate. They often involve physically modifying the system’s hardware, such as manipulating the firmware directly on the system’s chip or replacing components with compromised versions. This requires advanced technical skills and physical access to the target system. One example might involve modifying the firmware chip to disable Secure Boot entirely or to load a malicious bootloader that bypasses security checks. The impact is often complete system compromise, potentially leading to data theft or persistent malware infections. The high level of access needed usually implies targeted attacks against high-value assets.
Comparison of Software and Hardware-Based Bypass Methods
The following table summarizes the key differences between software and hardware-based UEFI Secure Boot bypass methods:
| Vulnerability Type | Exploitation Method | Impact | Mitigation |
|---|---|---|---|
| Software-based | Exploiting vulnerabilities in UEFI firmware code, drivers, or bootloaders; modifying existing components or introducing malicious ones. | Unauthorized access, system compromise, data theft, malware infection. | Regular firmware updates, secure coding practices, input validation, and robust security audits. |
| Hardware-based | Direct manipulation of firmware chip, replacement of compromised components, potentially involving advanced hardware modifications. | Complete system compromise, potentially leading to data theft, persistent malware infections, and complete control over the system. | Physical security measures, tamper-evident seals, and secure hardware design. |
Exploitation Techniques and Methods
Source: itsfoss.com
UEFI Secure Boot, while designed to enhance system security, isn’t impenetrable. Several clever techniques allow attackers to circumvent its protective measures, leading to unauthorized code execution and potential system compromise. Understanding these methods is crucial for developing robust defenses.
The core principle behind most UEFI Secure Boot bypasses involves manipulating the boot process to load malicious code disguised as legitimate firmware or drivers. This manipulation can occur at various stages, from directly modifying the boot environment variables to exploiting vulnerabilities within the UEFI firmware itself. The methods often require advanced technical knowledge and tools, but the potential impact justifies a deep dive into the techniques used.
Modifying the Boot Environment Variables
Attackers can exploit vulnerabilities in the UEFI firmware to modify boot environment variables, specifically the Secure Boot Database (db). This database contains the public keys of authorized bootloaders and drivers. By replacing or adding malicious entries to this database, an attacker can trick the system into loading and executing unauthorized code. This might involve leveraging a vulnerability allowing direct modification of the db, or a vulnerability in the signature verification process itself that allows a forged signature to be accepted. For instance, an attacker might use a previously unknown vulnerability to inject a malicious bootloader signed with a compromised or self-generated certificate into the db. Once the compromised entry is in place, the next boot cycle would load the attacker’s code.
Exploiting Firmware Vulnerabilities
Many UEFI firmware implementations contain vulnerabilities that can be exploited to gain control of the system before Secure Boot’s protections are fully enforced. These vulnerabilities often stem from improper input validation, buffer overflows, or other coding errors within the firmware itself. Exploiting such a vulnerability could allow an attacker to execute arbitrary code with system privileges, effectively bypassing Secure Boot. Consider a scenario where a vulnerability in a specific UEFI driver allows an attacker to overwrite critical memory regions, injecting malicious code that will execute before Secure Boot verification completes. This malicious code could then modify boot order, disable Secure Boot entirely, or load a rootkit.
Using a Rogue Bootloader
A more direct approach involves replacing the legitimate UEFI bootloader with a malicious one. This rogue bootloader would be designed to bypass Secure Boot checks and then load the attacker’s payload. This could involve replacing the bootloader’s signature with a forged one, leveraging a known vulnerability in the bootloader’s signature verification process, or exploiting a vulnerability to execute arbitrary code within the bootloader itself. Imagine a scenario where a vulnerability allows the attacker to replace the default bootloader with their malicious version. This malicious bootloader could then load a custom operating system or other malware, completely circumventing Secure Boot. The malicious bootloader might even contain features to re-enable itself after a system update or reinstall, ensuring persistence of the attack.
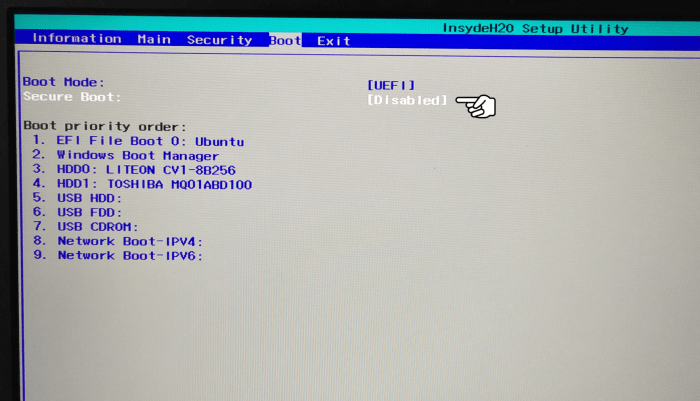
Mitigation Strategies and Best Practices: Uefi Secure Boot Bypass Vulnerability
Source: lecrabeinfo.net
Preventing UEFI Secure Boot bypass attacks requires a multi-layered approach encompassing firmware updates, secure hardware, and robust development practices. Ignoring these measures leaves systems vulnerable to sophisticated attacks that can compromise the entire system integrity, potentially leading to data breaches or complete system takeover. Let’s delve into the specifics of safeguarding your systems.
Effective mitigation hinges on a combination of proactive measures and responsive strategies. Regular updates are crucial, but equally important are secure coding practices and the careful selection of hardware components. A holistic approach, addressing both software and hardware vulnerabilities, is essential for robust security.
Firmware Updates
Regular firmware updates are paramount in patching known vulnerabilities and strengthening the overall security posture of the system. These updates often include critical security fixes that address newly discovered exploits or weaknesses in the UEFI implementation. Manufacturers regularly release updates to address security flaws, and neglecting these updates significantly increases the risk of successful attacks. For example, a 2021 update from a major motherboard manufacturer patched a vulnerability that allowed attackers to bypass Secure Boot by modifying specific firmware components. Failing to apply this update left systems vulnerable to this specific exploit. A consistent and automated update process is crucial for minimizing this risk.
Secure Boot Mechanisms Enhancement, Uefi secure boot bypass vulnerability
Beyond simply updating firmware, strengthening the core Secure Boot mechanisms themselves offers another layer of defense. This could involve implementing stricter validation checks on bootloaders and operating system kernels, ensuring that only authorized and digitally signed components are allowed to load. Advanced features like platform integrity measurements (PIM) can further enhance security by verifying the integrity of critical system components at each boot cycle. Hardware-based root-of-trust (RoT) solutions, often incorporated into newer chipsets, provide an additional layer of protection by ensuring the authenticity and integrity of the initial boot process. These hardware-based mechanisms offer a more robust defense against attacks that target the firmware itself.
Hardware-Based Security Solutions
Hardware-based security solutions offer a significant advantage in mitigating UEFI Secure Boot bypass vulnerabilities. These solutions often integrate directly into the system’s hardware, providing a more tamper-resistant environment. Trusted Platform Modules (TPMs) are a prime example. A TPM is a dedicated cryptographic processor that securely stores cryptographic keys and performs cryptographic operations. This can be leveraged to ensure the integrity of the boot process, making it significantly harder for attackers to bypass Secure Boot. Additionally, some newer processors incorporate advanced security features directly into their architecture, further enhancing the protection offered. The use of such hardware components is a significant step towards a more secure boot process.
Best Practices for Developers and System Administrators
Implementing secure coding practices and following best practices is crucial in minimizing vulnerabilities. Neglecting these can lead to exploitable weaknesses in the system.
Here are some key best practices:
- Regular Security Audits: Conduct regular security audits of the UEFI firmware and the entire boot process to identify and address potential vulnerabilities.
- Secure Development Lifecycle (SDL): Implement a robust SDL that includes secure coding practices, regular testing, and vulnerability assessments.
- Code Signing: Employ code signing techniques to ensure the authenticity and integrity of all boot components.
- Input Validation: Rigorously validate all user inputs to prevent buffer overflows and other common vulnerabilities.
- Memory Protection: Implement strong memory protection mechanisms to prevent unauthorized memory access.
- Least Privilege: Run processes with the least privileges necessary to perform their functions.
- Firmware Update Management: Establish a robust firmware update management system to ensure timely updates are applied.
- Threat Intelligence: Stay informed about the latest UEFI vulnerabilities and exploit techniques.
Impact and Consequences of a Successful Bypass
A successful UEFI Secure Boot bypass represents a significant security breach, potentially leading to catastrophic consequences for both individual users and organizations. The compromised system becomes vulnerable to a wide range of attacks, effectively erasing the fundamental trust upon which the entire operating system’s security relies. This allows attackers to gain complete control, installing persistent malware and manipulating system processes undetected.
The ramifications extend far beyond simple data loss. A compromised system becomes a potential launchpad for further attacks, potentially affecting an entire network. The attacker’s ability to manipulate the boot process grants them a level of access that is virtually undetectable by traditional security measures.
Rootkit Installation and Persistent Malware Presence
A successful UEFI Secure Boot bypass opens the door for rootkit installation. Rootkits are insidious pieces of malware designed to hide their presence and maintain persistent access to the system. Installed at the lowest level of the system, they can manipulate the boot process itself, ensuring their survival even after a system reinstall. This means that even a complete wipe and reinstall of the operating system may not remove the rootkit, as it operates below the OS level. This persistence allows attackers to maintain long-term control, steal data undetected, and potentially deploy further malicious activities without detection. Imagine a scenario where a financial institution’s server is compromised in this manner – the resulting damage could be immense and far-reaching.
Data Integrity, Confidentiality, and System Availability
The consequences of a UEFI Secure Boot bypass directly impact the CIA triad: Confidentiality, Integrity, and Availability. Data confidentiality is compromised as attackers gain complete access to sensitive information. Data integrity is similarly threatened, as attackers can manipulate files and system settings, leading to inaccurate or corrupted data. System availability is also at risk, as attackers can render the system unusable through denial-of-service attacks or by installing ransomware. Consider a hospital’s patient records – a breach resulting from a UEFI Secure Boot bypass could expose sensitive medical information and disrupt critical hospital operations.
Challenges in Detection and Remediation
Detecting a successful UEFI Secure Boot bypass is incredibly difficult. Since the attack occurs at the very foundation of the system’s security, traditional antivirus and endpoint detection systems often fail to identify the intrusion. The attacker’s ability to manipulate the boot process allows them to bypass these security measures. Remediation is equally challenging. Simply reinstalling the operating system is often insufficient, as the rootkit may reside in the UEFI firmware itself. This often requires specialized tools and expertise, and may even involve replacing or reflashing the system’s firmware. The lack of readily available and effective detection methods coupled with the complexity of remediation makes a successful bypass a particularly serious threat.
Case Studies of Real-World Exploits
Real-world exploits of UEFI Secure Boot vulnerabilities highlight the critical need for robust security measures. These attacks demonstrate how sophisticated adversaries can circumvent seemingly impenetrable security mechanisms, potentially leading to significant data breaches and system compromises. Analyzing these cases allows us to understand the techniques employed and develop more effective mitigation strategies.
Analysis of the LoJax UEFI Rootkit
The LoJax campaign, discovered in 2017, represented a significant leap in the sophistication of UEFI-based attacks. This malware, attributed to a sophisticated nation-state actor, leveraged a previously unknown vulnerability to implant a persistent rootkit directly within the UEFI firmware of targeted systems. The rootkit, capable of surviving operating system reinstallation and even hardware replacement, enabled long-term, undetected access to compromised machines. The attackers exploited a vulnerability allowing them to overwrite a portion of the firmware’s code with malicious instructions. This resulted in complete system compromise, enabling persistent data exfiltration and other malicious activities. The impact was severe, affecting numerous high-value targets and highlighting the potential for widespread damage from such attacks.
Examination of the “BootHole” Vulnerability (CVE-2020-1048)
The BootHole vulnerability (CVE-2020-1048) affected a significant number of Intel systems. This vulnerability resided within the Intel Boot Guard component, a security feature designed to protect the integrity of the boot process. Exploitation of BootHole allowed attackers to modify the boot process without requiring administrator privileges. The attack involved manipulating specific data structures within the UEFI firmware to execute malicious code during the boot sequence. The impact was far-reaching, as the vulnerability could be exploited remotely and allowed attackers to gain complete control over affected systems. The relatively simple exploitation method further amplified the threat, allowing even less sophisticated attackers to leverage the vulnerability.
| Vulnerability | Exploit Method | Affected Systems | Outcome |
|---|---|---|---|
| LoJax UEFI Rootkit | Overwriting firmware code via an unknown vulnerability. | Various systems, likely targeted high-value machines. | Persistent system compromise, data exfiltration, and long-term access. |
| BootHole (CVE-2020-1048) | Manipulating data structures within Intel Boot Guard to execute malicious code. | Intel systems with vulnerable Boot Guard implementations. | Complete system compromise, potential for remote exploitation and widespread damage. |
Final Conclusion
So, the next time you boot up your computer, remember the silent battle raging beneath the surface. The UEFI Secure Boot bypass vulnerability is a constant reminder of the ever-evolving arms race between security professionals and those who seek to exploit weaknesses. Understanding these vulnerabilities, implementing strong mitigation strategies, and staying informed about the latest threats are crucial to maintaining a secure digital environment. The fight for digital security is far from over, and staying vigilant is our best defense.


