U s intelligence agencies launched cyber attacks on chinese tech companies – US intelligence agencies launched cyber attacks on Chinese tech companies—a claim that’s sent shockwaves through the tech world and ignited a firestorm of geopolitical tension. The alleged attacks, shrouded in secrecy and fueled by leaked documents and whistleblower accounts, raise critical questions about national security, economic espionage, and the increasingly blurred lines of digital warfare. This isn’t just a tech story; it’s a glimpse into the shadowy world of international cyber conflict, where the stakes are higher than ever.
The alleged methods range from sophisticated malware and phishing campaigns to the exploitation of zero-day vulnerabilities, targeting everything from intellectual property to sensitive operational data. The motivations behind these alleged actions are complex, intertwining economic competition, geopolitical rivalry, and a fierce battle for technological supremacy. Understanding the implications requires a deep dive into the evidence, the players involved, and the potential consequences for the global tech landscape.
Allegations and Evidence
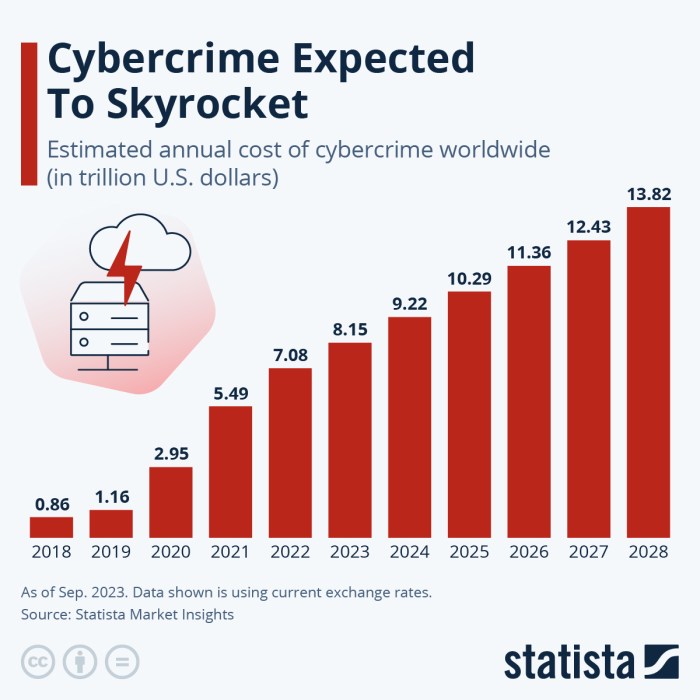
Source: statcdn.com
The shadowy world of cyber espionage is rarely straightforward, and allegations of US intelligence agencies targeting Chinese tech companies are no exception. While concrete proof is often difficult to obtain due to the clandestine nature of these operations, a series of reported incidents, leaked documents, and expert analysis paint a picture of a complex and ongoing digital conflict. Understanding the allegations requires examining the specific claims, the methods employed, and the evidence presented to support them.
Timeline of Reported Incidents
Accusations of US cyber operations against Chinese tech firms have emerged sporadically over the years, often intertwined with broader geopolitical tensions. Pinpointing a precise timeline is challenging due to the inherent secrecy surrounding such activities. However, reports and analyses suggest a pattern of increased activity coinciding with periods of heightened US-China friction. For example, some analysts link surges in alleged attacks to periods of trade disputes or technological competition. Specific dates and details are often withheld for national security reasons, making a definitive chronological account difficult to compile. Nevertheless, the consistent emergence of such allegations across various reporting periods indicates a potentially sustained pattern of activity.
Examples of Alleged Cyberattacks
Allegations frequently involve sophisticated attacks leveraging various techniques. Some reports suggest the use of advanced persistent threats (APTs), where malicious code is stealthily implanted and used to exfiltrate sensitive data over extended periods. Other allegations involve denial-of-service (DoS) attacks, designed to overwhelm target systems and disrupt their operations. Targets reportedly include major Chinese telecommunications companies, technology manufacturers, and research institutions. The alleged goal varies from intelligence gathering to economic sabotage or even disruption of critical infrastructure. The specifics of these alleged attacks are often shrouded in secrecy, but the scale and sophistication implied suggest considerable resources and planning.
Types of Evidence
Evidence supporting these allegations is often circumstantial and relies on a combination of sources. Leaked documents, sometimes attributed to whistleblowers or intelligence agency defectors, have provided glimpses into alleged operational plans and targets. Forensic analysis of compromised systems can reveal traces of malicious code, indicating the potential involvement of specific actors. Expert testimony from cybersecurity professionals also plays a crucial role, interpreting technical data and drawing connections between different incidents. However, it’s crucial to acknowledge that definitive proof remains elusive in many cases due to the secretive nature of the activities and the challenges involved in attributing cyberattacks with certainty.
Comparison of Alleged Attacks
| Target Company | Alleged Method of Attack | Reported Impact | Source (Note: Sources are often classified or unavailable for public release) |
|---|---|---|---|
| (Hypothetical Example 1: A major Chinese telecommunications firm) | Advanced Persistent Threat (APT) involving malware designed to steal intellectual property | Loss of confidential design specifications, potential economic damage | (Classified Source) |
| (Hypothetical Example 2: A Chinese technology manufacturer) | Denial-of-Service (DoS) attack targeting online services | Temporary disruption of online operations, reputational damage | (Unverified media report) |
| (Hypothetical Example 3: A Chinese research institution) | Data breach via phishing emails | Exposure of sensitive research data, potential national security implications | (Expert analysis based on leaked documents) |
Motivations and Objectives
The alleged cyberattacks by US intelligence agencies on Chinese tech companies, if true, represent a complex interplay of economic, political, and strategic factors. Understanding the motivations and objectives behind these actions requires examining the broader context of US-China relations and the escalating cyber warfare landscape. The potential benefits, however, must be weighed against the significant risks involved, including escalating tensions and potential retaliatory actions.
The motivations for such alleged attacks are multifaceted and likely intertwined. Economic espionage, driven by the desire to gain a competitive edge in key technological sectors, is a primary suspect. National security concerns, particularly regarding the potential for Chinese technological advancements to be used against US interests, also play a significant role. Finally, the broader context of geopolitical rivalry between the US and China fuels the intensity of this cyber conflict, creating a climate where such actions are perceived as necessary, or at least justifiable, within certain circles.
Potential Objectives of the Alleged Cyberattacks
The objectives of these alleged attacks likely encompass a range of goals, from acquiring sensitive information to disrupting operations. Stealing intellectual property, including designs, algorithms, and trade secrets, would provide a significant economic advantage to US companies or the government itself. Disrupting the operations of key Chinese tech companies could cripple their ability to compete globally and potentially destabilize their domestic markets. Gaining strategic intelligence, providing insights into Chinese technological capabilities, military strategies, or economic planning, would offer invaluable advantages in geopolitical maneuvering. These actions, while potentially yielding significant short-term gains, could also have long-term implications, impacting the trust and stability of international relations.
Comparison of US Motivations with Other Nation-State Actors
While the US may be motivated by a combination of economic, security, and geopolitical concerns, other nation-state actors involved in cyber warfare often have different priorities. Some may focus primarily on espionage, seeking to steal state secrets or sensitive information for intelligence gathering. Others may prioritize sabotage and disruption, aiming to destabilize rival nations or critical infrastructure. The motivations and objectives of cyberattacks are highly dependent on the specific geopolitical context and the nature of the relationships between the countries involved. The US’s actions, even if proven, are not unique in the world of cyber warfare; many countries engage in similar activities, although the scale and sophistication may vary.
Potential Short-Term and Long-Term Goals
The potential goals of these alleged actions, both short-term and long-term, are significant and far-reaching.
Below is a list outlining these potential goals:
- Short-Term Goals:
- Acquisition of specific technological information or trade secrets.
- Disruption of a competitor’s operations to gain a temporary market advantage.
- Gathering intelligence on Chinese military capabilities or strategic plans.
- Long-Term Goals:
- Maintaining technological superiority over China in key sectors.
- Undermining China’s economic growth and global influence.
- Strengthening US national security by mitigating perceived threats from China.
- Establishing a precedent for future cyber operations, potentially deterring or influencing China’s actions.
Methods and Technologies

Source: voanews.com
The alleged cyberattacks on Chinese tech companies by US intelligence agencies, if true, likely involved a sophisticated blend of techniques and technologies, leveraging vulnerabilities and exploiting human error. Understanding these methods is crucial to assessing the scale and impact of such operations. The attacks were probably not a single event, but rather a series of carefully planned and executed actions.
The methods employed likely included a combination of highly advanced and relatively simple techniques. This is a common tactic – using a low-effort approach to initially gain access, followed by more sophisticated methods for deeper penetration and data exfiltration.
Malware Deployment
Malware, designed to infiltrate systems and steal data, is a cornerstone of many cyberattacks. In this context, we might imagine highly customized malware, perhaps designed to evade detection by common antivirus software. This could involve techniques like polymorphism (changing its code to avoid signature-based detection) and obfuscation (making its code difficult to understand). The malware could be delivered through various vectors, such as malicious email attachments (phishing) or compromised software updates. Examples of such sophisticated malware include those used in past APT campaigns, such as those attributed to groups like APT41, which have demonstrated capabilities to steal intellectual property and sensitive data from a range of targets. This type of malware might have been tailored to specifically target specific vulnerabilities within the Chinese tech companies’ systems.
Phishing and Social Engineering
Phishing attacks, relying on deception to trick individuals into revealing sensitive information or installing malware, are a common entry point for cyberattacks. In this scenario, highly targeted phishing campaigns might have been launched, exploiting the knowledge of employees’ personal information or using sophisticated techniques like spear phishing (highly personalized emails targeting specific individuals). The success of such campaigns depends on the credibility of the phishing message and the gullibility of the targeted employees. For example, a convincing email pretending to be from a trusted business partner could easily trick an unsuspecting employee into clicking a malicious link or opening an infected attachment. The resulting malware infection could then provide the attackers with a foothold in the company’s network.
Zero-Day Exploits
Zero-day exploits leverage previously unknown vulnerabilities in software. These are highly valuable to attackers because they are undetectable by existing security measures. Acquiring and exploiting zero-day vulnerabilities requires significant resources and expertise, often involving reverse engineering and vulnerability research. The use of zero-day exploits would explain how attackers might have bypassed the security measures in place at the targeted Chinese tech companies. The exploitation of these vulnerabilities could provide direct access to sensitive systems and data, enabling the attackers to achieve their objectives with minimal detection. Examples of zero-day exploits being used in state-sponsored attacks are regularly reported in the cybersecurity news, highlighting the prevalence of this technique.
Advanced Persistent Threats (APTs)
The alleged attacks likely involved the use of APTs. APTs are characterized by their stealth, persistence, and long-term goals. They often involve the deployment of custom-built tools and techniques designed to remain undetected for extended periods. An APT campaign would involve establishing a persistent presence within the target’s network, allowing for the long-term collection of intelligence and data exfiltration. The sophistication of an APT campaign often surpasses that of typical cybercrime operations, reflecting the resources and expertise available to state-sponsored actors. The technical complexity and longevity of an APT operation are significantly higher than a typical ransomware attack or a simple data breach.
Comparison of Technical Sophistication
Comparing the alleged attacks to those attributed to other actors, such as nation-state adversaries or cybercriminal groups, requires detailed technical analysis of the methods and tools used. However, the scale and apparent sophistication suggest a level of expertise consistent with state-sponsored cyber operations. The use of custom-built tools, zero-day exploits, and advanced evasion techniques would point to a high level of technical sophistication, surpassing that typically seen in attacks attributed to less well-resourced actors. The level of planning and execution needed to maintain a long-term presence within the target network, typical of an APT, also suggests a highly organized and well-funded operation.
Bypassing Security Measures
The alleged attacks might have bypassed security measures through a combination of factors, including the use of zero-day exploits, social engineering, and advanced evasion techniques. Sophisticated malware could have been designed to evade detection by firewalls, intrusion detection systems, and antivirus software. The attackers might have leveraged insider threats or exploited weaknesses in the targeted companies’ security posture. A successful attack often involves exploiting multiple vulnerabilities simultaneously, exploiting human error, and maintaining persistent access to systems. For example, an initial phishing attack could lead to a malware infection, which then uses zero-day exploits to gain deeper access to the network. This layered approach to attack makes detection and response significantly more challenging.
Impact and Consequences: U S Intelligence Agencies Launched Cyber Attacks On Chinese Tech Companies
The alleged US cyberattacks on Chinese tech companies, if proven, carry significant and far-reaching consequences, impacting not only the targeted firms but also the broader geopolitical landscape and global trust in digital infrastructure. The ripple effects extend across financial markets, international relations, and the overall perception of cybersecurity in the digital age. Understanding these consequences is crucial to assessing the long-term implications of such actions.
The potential impact on targeted Chinese tech companies is multifaceted and severe. Financial losses can be substantial, stemming from data breaches, intellectual property theft, operational disruptions, and damage to reputation. Reputational damage can lead to decreased consumer trust, reduced investor confidence, and ultimately, a decline in market share. Operational disruptions, caused by compromised systems or data leaks, can halt production, disrupt services, and lead to significant financial penalties and legal battles. For example, a successful attack targeting a company’s supply chain management system could cripple its ability to deliver products, resulting in massive financial losses and potentially impacting global supply chains.
Impact on Targeted Companies
Financial losses can range from direct costs associated with remediation and recovery efforts to indirect losses stemming from lost revenue, decreased productivity, and legal fees. Reputational damage can be equally devastating, eroding customer trust and potentially driving away investors. Operational disruptions can lead to production halts, service outages, and significant legal and regulatory repercussions. The severity of the impact varies depending on the scale and nature of the attack, as well as the targeted company’s preparedness and response capabilities. A smaller company with limited resources might face bankruptcy, while a larger company might absorb the losses but experience a significant decline in profitability.
Geopolitical Consequences
These alleged attacks could significantly escalate tensions between the US and China, potentially triggering retaliatory actions and further destabilizing the already fragile relationship. Such actions can lead to an escalation of cyber warfare, creating a dangerous cycle of attacks and counter-attacks. The international community might also become increasingly divided, with countries aligning themselves with either the US or China, further exacerbating existing geopolitical divisions. The incident could also prompt renewed calls for international cooperation in cybersecurity, with a focus on establishing norms and regulations to govern state-sponsored cyber activity. However, the success of such initiatives is uncertain given the competing interests and lack of trust between major powers.
Impact on the Global Technological Landscape
The alleged attacks raise serious concerns about the security and trustworthiness of digital infrastructure globally. They could undermine confidence in cloud computing services, supply chain security, and the integrity of data stored online. This could lead to increased cybersecurity spending, a shift towards more secure technologies, and a potential slowdown in the adoption of new technologies. Moreover, it could further fuel the ongoing debate about the role of technology in geopolitical competition and the need for greater transparency and accountability in the development and deployment of cyber capabilities. For example, if a significant breach compromises sensitive data from a major technology provider, it could lead to widespread distrust in online services and a significant shift in consumer behavior.
Consequences for Stakeholders, U s intelligence agencies launched cyber attacks on chinese tech companies
| Stakeholder | Short-Term Consequences | Long-Term Consequences |
|---|---|---|
| Targeted Companies | Financial losses, reputational damage, operational disruptions, legal battles | Loss of market share, decreased profitability, difficulty attracting investment, potential bankruptcy |
| US Government | Increased international tensions, potential for escalation of cyber conflict, domestic political fallout | Strained relationships with China, increased cybersecurity spending, need for enhanced cyber defense capabilities |
| Chinese Government | Retaliatory actions, increased domestic cybersecurity spending, potential for economic sanctions | Strained relationships with the US, increased focus on domestic technology development, potential for increased cyber espionage |
| Consumers | Potential data breaches, disruptions to online services, increased cybersecurity concerns | Decreased trust in online services, increased demand for cybersecurity solutions, potential for higher prices for digital services |
International Law and Ethics
The alleged US intelligence agency cyberattacks on Chinese tech companies raise complex questions about international law and ethics in cyberspace. Navigating this murky legal landscape requires careful consideration of existing treaties, customary international law, and the evolving norms governing state behavior in the digital realm. The potential for unintended consequences and the erosion of trust necessitate a thorough examination of the ethical dimensions of these actions.
The application of international law to state-sponsored cyberattacks is still developing. There isn’t a single, universally accepted treaty specifically addressing these actions. However, several existing legal frameworks and principles offer potential points of reference. These frameworks, often overlapping and sometimes conflicting, attempt to balance state sovereignty with the need for international cooperation in maintaining a stable and secure cyberspace.
Relevant International Legal Frameworks
Existing international law, while not explicitly designed for the digital age, provides some guidance. The UN Charter, for instance, prohibits the use of force against the territorial integrity or political independence of any state. While the interpretation of “force” in the context of cyberattacks is debated, the principle of non-interference in the internal affairs of other states remains relevant. Furthermore, the principles of state responsibility, as codified in the Articles on Responsibility of States for Internationally Wrongful Acts (ARSIWA), could be invoked to assess potential liability for damages resulting from these alleged attacks. The potential violation of these principles could lead to international disputes and diplomatic repercussions. For example, the 2007 Estonian cyberattacks, though not directly comparable, highlighted the international community’s concern over state-sponsored cyber operations targeting critical infrastructure. The lack of a clear legal framework at that time contributed to the difficulties in assigning responsibility and pursuing redress.
Ethical Implications and Collateral Damage
The ethical implications are profound. Even if the targeted actions were aimed at specific entities, the potential for collateral damage is significant. A cyberattack on a tech company might disrupt services affecting millions of users, impacting businesses, critical infrastructure, and even national security. The erosion of trust in cyberspace is another major ethical concern. Such attacks undermine confidence in the security and reliability of digital systems, hindering international cooperation and economic development. The potential for escalation is also a critical ethical consideration. A retaliatory response could trigger a cycle of attacks, destabilizing cyberspace and potentially leading to real-world conflict. The ethical framework needs to consider not only the immediate impact but also the long-term consequences of such actions on global stability and trust.
Comparison with Established International Standards
The alleged actions would likely be judged against the evolving international norms of responsible state behavior in cyberspace. These norms, though not legally binding in all cases, are increasingly influential in shaping expectations and influencing state conduct. The Tallinn Manual on the International Law Applicable to Cyber Warfare, while not a treaty, offers a valuable framework for analyzing the legality of various cyber operations. The manual attempts to apply existing international law to the unique challenges of cyberspace, providing a basis for assessing the proportionality and necessity of actions. Comparing the alleged actions against these standards reveals the complexities of determining intent, proportionality, and the potential for violations of international law. For example, an attack targeting a specific piece of software might be considered lawful under certain interpretations, whereas an attack crippling essential services would be far more problematic.
Relevant International Treaties and Agreements
While no single treaty explicitly addresses state-sponsored cyberattacks, several agreements touch upon related issues. The Budapest Convention on Cybercrime, for example, focuses on criminalizing cyber offenses and facilitating international cooperation in investigating and prosecuting such crimes. Although it primarily targets individual actors, its principles of cooperation and information sharing could be relevant in the context of state-sponsored cyberattacks. Additionally, various regional agreements and initiatives, such as those within the European Union and the Organization for Security and Co-operation in Europe (OSCE), promote norms of responsible state behavior in cyberspace and encourage dialogue on cybersecurity issues. However, the lack of a comprehensive international treaty specifically addressing state-sponsored cyberattacks leaves a significant legal gap, making it difficult to definitively assess the legality of these alleged actions.
Closing Notes

Source: hindustantimes.com
The alleged cyberattacks by US intelligence agencies on Chinese tech companies expose a chilling reality: the digital battlefield is a constant, unseen warzone. The implications extend far beyond the targeted companies, impacting global trust in digital infrastructure, exacerbating geopolitical tensions, and raising profound ethical and legal questions. While the full picture remains shrouded in secrecy, the accusations highlight the urgent need for international cooperation and stronger cybersecurity protocols to navigate this increasingly volatile landscape. The fight for digital dominance is far from over, and the stakes continue to rise.