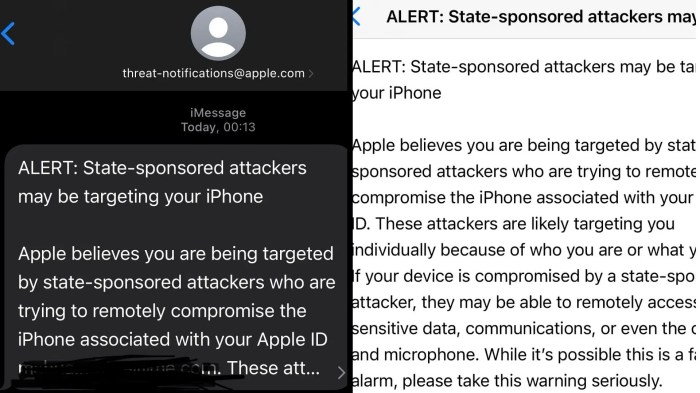
133k Vulnerable FortiOS FortiProxy A Deep Dive
133k vulnerable FortiOS FortiProxy devices? Whoa. That’s a seriously scary number. This massive vulnerability exposes a critical weakness in network security, leaving countless organizations exposed to potential data breaches, crippling service disruptions, and hefty financial losses. We’re diving deep into the nitty-gritty of this cybersecurity nightmare, exploring the vulnerabilities, exploitation methods, and crucial mitigation strategies … Read more