Sysbumps. The word itself sounds like a tiny, disruptive tremor shaking your perfectly optimized system. But what exactly *are* sysbumps? Are they a sudden surge in server load, a sneaky software glitch, or a rogue network packet causing havoc? This deep dive explores the multifaceted world of sysbumps, uncovering their origins, impact, and how to effectively mitigate these often-overlooked system hiccups.
From hardware malfunctions to software bugs and network congestion, we’ll dissect the various causes of sysbumps, examining their severity and the ripple effects they can have on your system’s performance and data integrity. We’ll equip you with practical strategies for prevention, detection, and resolution, turning you into a sysbump-busting pro.
Understanding “Sysbumps” in Context

Source: webflow.com
The term “sysbump,” while not a formally recognized technical term, likely refers to unexpected, disruptive events within a system. It suggests a sudden, albeit potentially minor, disruption to the normal operation of a computer system, network, or application. Think of it as a small, localized earthquake in the digital world – jarring, but hopefully not catastrophic. The impact and severity of a sysbump can vary wildly depending on the context.
Sysbumps can manifest differently across various technological domains. The specific meaning and implications will depend heavily on the system in question and the nature of the disruption.
Sysbumps in System Administration
In the realm of system administration, a sysbump might refer to a brief service interruption, a temporary resource bottleneck, or a minor configuration error that quickly resolves itself. For example, a sudden spike in network traffic might briefly overload a server, causing slow response times for a few minutes before things stabilize. Another example could be a momentary database connection failure, resulting in a few failed transactions before the connection is re-established. These are transient events, often self-correcting, but still noteworthy enough to be logged and potentially investigated to prevent recurrence. The impact might range from barely noticeable to a slight inconvenience for users, depending on the affected service and the duration of the disruption.
Sysbumps in Software Development
Within software development, a sysbump could describe a minor bug or glitch that causes a temporary malfunction in an application. Imagine a web application briefly displaying an incorrect value or failing to load a specific image. These issues might be related to transient network conditions, race conditions within the application’s code, or even a temporary overload on the application server. Unlike major software failures, sysbumps in this context are usually quickly resolved and don’t necessitate a full system restart or major code overhaul. The user experience is minimally affected, often with only a slight hiccup in functionality.
Sysbumps in Networking
In networking, a sysbump might represent a fleeting connectivity issue, a momentary packet loss, or a brief network outage affecting a small portion of the network. A scenario could involve a temporary disruption in a specific network segment due to a temporary hardware failure or a brief network congestion. This could manifest as intermittent connectivity problems for a small number of users or devices. The impact is localized and usually short-lived, requiring minimal intervention. It is often automatically resolved as the underlying issue resolves itself.
Hypothetical Sysbump Scenario
Let’s imagine a web hosting provider experiencing a sudden surge in traffic to a particular website. This causes a temporary overload on the web server handling that site. The server doesn’t crash, but response times increase significantly for a few minutes, resulting in slow page loading for users. Error messages might briefly appear for some users, but the service quickly returns to normal as the traffic surge subsides. This event would qualify as a sysbump: a temporary, localized disruption that didn’t lead to a complete system failure but still caused a noticeable impact on user experience. Monitoring tools would likely record this event, providing valuable data for capacity planning and system optimization.
Types and Causes of Sysbumps
Sysbumps, those frustrating hiccups in your system’s smooth operation, can stem from a variety of sources. Understanding the root causes is key to effective troubleshooting and prevention. We’ll break down the common culprits, categorizing them by their origin and impact.
Sysbumps manifest in different ways, ranging from minor inconveniences to complete system crashes. Their severity depends heavily on the underlying cause and the criticality of the affected system component. A minor software glitch might cause a temporary freeze, while a failing hard drive could lead to data loss and extended downtime. Effective diagnosis involves a systematic approach, starting with the most likely causes and working through potential solutions.
Hardware-Related Sysbumps
Hardware failures are a significant source of sysbumps. These can range from failing components like hard drives and RAM to overheating processors or faulty power supplies. A failing hard drive, for example, might manifest as slow performance, data corruption, or complete system failure. Overheating, often due to inadequate cooling, can lead to system instability and unexpected shutdowns. Diagnosing hardware issues often involves running diagnostic tools, checking system logs for error messages, and potentially replacing faulty components. Visual inspection for physical damage (like loose connections or burnt components) can also be helpful.
Software-Related Sysbumps
Software glitches, bugs, and conflicts are another major contributor to sysbumps. Outdated drivers, incompatible applications, or corrupted system files can all disrupt normal system operation. A classic example is a software conflict where two programs are vying for the same system resource, leading to instability or crashes. Diagnosing software problems usually involves checking for updates, running system file checkers, and potentially reinstalling problematic applications. Careful attention to system logs and error messages can pinpoint the source of the software-related sysbump.
Network-Related Sysbumps
Network issues can also trigger sysbumps, particularly in systems that rely on network connectivity. These problems can range from temporary network outages to persistent connectivity issues caused by faulty network hardware or misconfigurations. A slow internet connection, for example, can impact the performance of applications that rely on online resources. Diagnosing network-related sysbumps typically involves checking network cables, verifying network settings, and running network diagnostic tools to identify connectivity problems or network congestion. In some cases, contacting your internet service provider may be necessary to resolve underlying network infrastructure issues.
Comparing Sysbump Severity and Impact, Sysbumps
The impact of a sysbump can vary dramatically depending on the affected system and the nature of the problem. A minor software glitch might only cause a brief interruption, while a hardware failure could lead to significant data loss and extended downtime. For instance, a momentary freeze caused by a software bug is a relatively minor sysbump, easily resolved with a simple restart. Conversely, a failing hard drive could result in irreversible data loss, requiring extensive data recovery efforts and potentially costly hardware replacement. The criticality of the affected system also plays a role; a sysbump on a personal computer might be an inconvenience, but the same issue on a server supporting a critical business application could have far-reaching consequences.
Impact and Mitigation Strategies
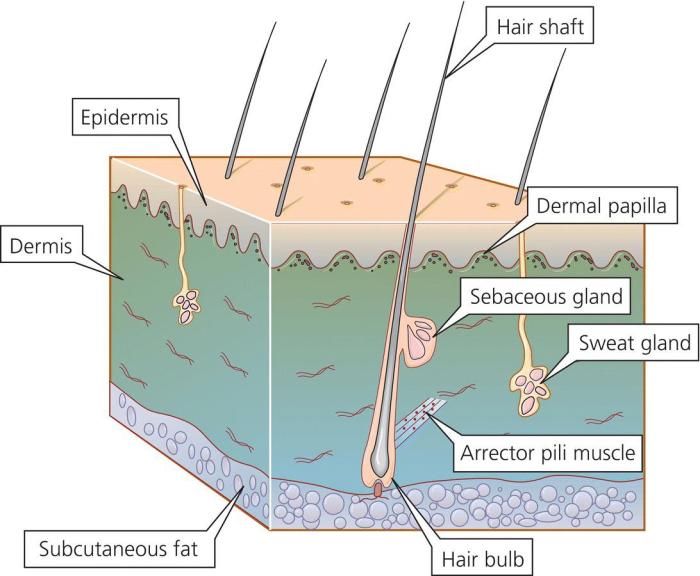
Source: perlego.com
Unresolved sysbumps, those pesky system hiccups, can have far-reaching consequences, impacting everything from user experience to the integrity of your precious data. Ignoring them is akin to ignoring a persistent cough – it might seem minor at first, but it can escalate into something much more serious.
System performance takes a direct hit when sysbumps are left unaddressed. Think slow loading times, application crashes, and general system instability. This not only frustrates users but can also lead to lost productivity and revenue, especially in business settings. Imagine an e-commerce site struggling with slow loading times during a peak shopping period – lost sales are a direct consequence. Furthermore, data integrity is jeopardized. Corrupted files, lost information, and inconsistent data records are all potential outcomes. The repercussions can range from minor inconveniences to catastrophic data loss, depending on the severity and nature of the sysbump.
Sysbump Mitigation Process
The following flowchart illustrates a systematic approach to resolving sysbumps:
“`
[Start] –> Identify the Sysbump (Symptoms, affected systems) –> Diagnose the Root Cause (Logs, monitoring tools) –> Implement Solution (Configuration changes, software updates, hardware replacement) –> Test and Verify (System stability, data integrity) –> Document Resolution (Root cause, solution, preventative measures) –> [End]
“`
This flowchart represents a typical mitigation process. The specific steps and their order might vary depending on the complexity and nature of the sysbump. For example, a simple configuration error might require fewer steps than a hardware failure. The key is a systematic approach to ensure thorough diagnosis and effective resolution.
Best Practices for Sysbump Prevention
Proactive measures are crucial in preventing future sysbumps. By implementing these best practices, you can significantly reduce the likelihood of system disruptions and maintain a stable and reliable system.
| Practice | Description | Implementation | Benefits |
|---|---|---|---|
| Regular System Monitoring | Continuous observation of system performance metrics (CPU usage, memory consumption, disk I/O, network traffic). | Utilize system monitoring tools (e.g., Nagios, Zabbix, Prometheus) to set alerts for critical thresholds. | Early detection of potential issues, proactive intervention before major problems arise. |
| Automated Backups | Regular and automated creation of system backups, including both data and system configurations. | Implement backup software (e.g., rsync, Bacula) with scheduled backups to a separate storage location. | Data protection against data loss from various causes (hardware failure, software errors, cyberattacks). Faster recovery time. |
| Software Updates and Patching | Regular application of security patches and updates to operating systems, applications, and firmware. | Establish a patching schedule and utilize automated update mechanisms where available. | Reduced vulnerability to security exploits and improved system stability. |
| Capacity Planning | Proactive assessment of future resource needs (CPU, memory, storage, network bandwidth) based on projected growth. | Analyze historical data and project future requirements to avoid resource bottlenecks. | Prevention of performance degradation due to resource exhaustion, ensures system scalability. |
Monitoring and Prevention
Preventing sysbumps isn’t about reacting to problems; it’s about anticipating them. A proactive approach, combining smart monitoring with regular maintenance, significantly reduces downtime and keeps your systems humming. This involves understanding your system’s vulnerabilities and establishing a robust early warning system.
Proactive monitoring involves implementing a system that continuously observes key performance indicators (KPIs) and system behaviors, identifying anomalies that might precede a full-blown sysbump. This allows for intervention before a minor issue escalates into a major outage. Think of it as a preventative health check for your digital infrastructure.
System Monitoring Design for Sysbump Precursors
A robust monitoring system requires a multi-layered approach. This includes hardware monitoring (CPU usage, memory, disk space), software monitoring (application performance, database activity, network traffic), and log analysis. Crucially, you need to define thresholds for each metric. For example, if CPU usage consistently exceeds 90% for extended periods, it’s a warning sign. Similarly, a sudden spike in error logs from a specific application might indicate an impending failure. Effective monitoring tools can visualize these metrics in real-time, providing immediate alerts when thresholds are breached. Implementing automated alerts, such as email or SMS notifications, ensures timely responses to potential issues. Consider using centralized monitoring systems that aggregate data from various sources for a holistic view of your system’s health. This allows for faster identification of potential sysbumps and more efficient troubleshooting.
The Role of Logging and System Alerts in Sysbump Detection
Detailed logging is the backbone of effective sysbump prevention. Comprehensive logs record all significant system events, providing a historical record that can be analyzed to identify patterns and potential problems. These logs should include information such as timestamps, error messages, user activity, and resource utilization. System alerts, triggered by pre-defined thresholds or specific events, act as immediate warnings, alerting administrators to potential issues. These alerts should be prioritized based on severity, ensuring that critical issues are addressed promptly. For example, a critical alert might indicate a complete system failure, while a warning might indicate a gradual decline in performance. Effective log management involves regular review, analysis, and archiving. Analyzing log data can reveal hidden patterns and trends that might indicate vulnerabilities or potential issues before they escalate into a sysbump. Investing in log management tools that can automatically analyze logs and generate reports can significantly improve the efficiency of this process.
Preventative Maintenance to Reduce Sysbump Frequency
Preventative maintenance is a crucial component of a comprehensive sysbump prevention strategy. This involves regularly performing tasks such as software updates, security patching, hardware checks, and database optimization. Regular software updates address known vulnerabilities and bugs, reducing the risk of system failures. Security patching protects against malicious attacks that can trigger sysbumps. Hardware checks ensure that components are functioning correctly and identify potential issues before they lead to failures. Database optimization improves performance and prevents bottlenecks that can lead to system instability. A well-defined maintenance schedule ensures that these tasks are performed consistently and efficiently. The schedule should be tailored to the specific needs of your system, taking into account factors such as the criticality of the system and the frequency of updates. Documentation of maintenance activities is crucial for tracking progress and identifying potential areas for improvement.
Case Studies and Examples
Understanding sysbumps requires looking beyond theoretical definitions. Real-world scenarios, both hypothetical and loosely based on actual events (without revealing sensitive information), help illustrate the impact and complexities of these system disruptions. Let’s delve into some examples to solidify our understanding.
Hypothetical Sysbump Incident: The Case of the Misconfigured Load Balancer
Imagine a mid-sized e-commerce company experiencing a sudden surge in website traffic due to a highly successful marketing campaign. Their load balancer, responsible for distributing traffic across multiple servers, was misconfigured. Instead of evenly distributing the load, it directed almost all traffic to a single server, causing that server to overload and crash. The effect was immediate: the website became unresponsive, leading to lost sales, frustrated customers, and reputational damage. The resolution involved quickly identifying the misconfiguration, rerouting traffic to the remaining healthy servers, and implementing more robust monitoring and failover mechanisms. The incident highlighted the critical need for rigorous testing and redundancy in system architecture.
Fictional Case Study: Global Bank Faces Major Sysbump
GlobalBank, a large multinational financial institution, experienced a severe sysbump due to a cascading failure triggered by a seemingly minor software update. The update, intended to improve security, inadvertently introduced a bug that caused a critical database system to become unstable. This instability led to a ripple effect, impacting various internal systems, including customer account access, payment processing, and internal communication channels. The resulting outage lasted for several hours, causing significant financial losses due to interrupted transactions and reputational damage due to widespread service disruption. The investigation revealed insufficient testing of the software update and a lack of robust rollback mechanisms. The resolution involved a complete system restoration from backups, a thorough review of their update procedures, and significant investments in disaster recovery planning.
Real-World Analogous Scenarios
Several real-world situations, while not explicitly labeled as “sysbumps,” exhibit similar characteristics. For example, a large-scale power outage affecting a data center can lead to widespread service disruptions, mirroring the effects of a severe sysbump. Similarly, a denial-of-service (DoS) attack, overwhelming a system with traffic, can cause a similar level of disruption. Finally, a major software bug in a widely used application, like a critical operating system component, could trigger cascading failures across numerous interconnected systems, mimicking a complex sysbump event. These scenarios underscore the interconnected nature of modern systems and the potential for widespread impact from seemingly isolated incidents.
Illustrative Examples (Visual)
Visual aids can significantly enhance our understanding of complex technical issues like sysbumps. By representing abstract concepts graphically, we can better grasp the sequence of events, pinpoint vulnerabilities, and ultimately develop more effective mitigation strategies. Let’s explore two illustrative examples.
Progression of a Sysbump Event
Imagine a flowchart illustrating a typical sysbump. The flowchart begins with a “Trigger Event” box, perhaps a sudden surge in network traffic or a faulty database query. Arrows lead from this box to subsequent boxes representing the cascading effects: “Resource Exhaustion” (memory, CPU, etc.), then “Performance Degradation” (slow response times, increased latency), followed by “Service Disruption” (application crashes, website downtime). Finally, an arrow leads to a “Resolution” box, depicting the actions taken to restore normalcy – perhaps restarting a service, deploying a patch, or scaling resources. The color-coding could further enhance the visualization. For instance, the “Trigger Event” and “Service Disruption” boxes could be highlighted in red, while “Resolution” is in green. The arrows themselves could indicate the flow of time and the severity of the impact. Thicker, darker arrows could represent more significant consequences. This visual representation would clearly show the domino effect of a sysbump, highlighting the importance of rapid response and proactive mitigation.
Vulnerable System Components
A second illustration could depict a system architecture diagram. This diagram would showcase the various components of a system – servers, databases, network devices, applications, and their interconnections. Potential points of failure, vulnerable to sysbumps, are highlighted. For example, a database server could be marked with a red flag indicating its susceptibility to overload during peak traffic. A network switch could be similarly marked, representing a single point of failure that could cripple the entire system if it malfunctions. The applications relying on these components could be visually linked, demonstrating the ripple effect of a failure in one area. Different colors could represent different layers of the system (e.g., network infrastructure in blue, application layer in orange, database layer in purple). This diagram allows for a clear identification of potential weak points, enabling proactive mitigation strategies to be focused on these critical areas. A legend explaining the color-coding and the significance of each marked component would complete the visualization, making it easily understandable.
Concluding Remarks
Source: githubassets.com
Navigating the unpredictable landscape of sysbumps requires a proactive and multi-pronged approach. By understanding their root causes, implementing robust monitoring systems, and embracing preventative maintenance, you can significantly reduce their frequency and impact. Remember, a stitch in time saves nine – or in this case, prevents a major system meltdown. Stay vigilant, stay informed, and keep your systems running smoothly!