Researchers detailed the ghostwriter APT infrastructure, unveiling a sophisticated cyberattack operation. This deep dive into the group’s methods, targets, and infrastructure reveals a chillingly effective campaign. We’ll dissect their attack vectors, explore their objectives, and examine the indicators of compromise (IOCs) that expose their activities. Get ready to unravel the mysteries behind this shadowy operation and understand the real-world implications.
From the intricate components of their infrastructure to the specific techniques used for initial compromise and lateral movement, we’ll leave no stone unturned. We’ll also analyze the potential impact on targeted organizations and explore practical mitigation strategies to protect against future attacks. This isn’t just another tech story; it’s a gripping tale of espionage and cyber warfare.
Understanding the “Ghostwriter APT Infrastructure”
Source: googleusercontent.com
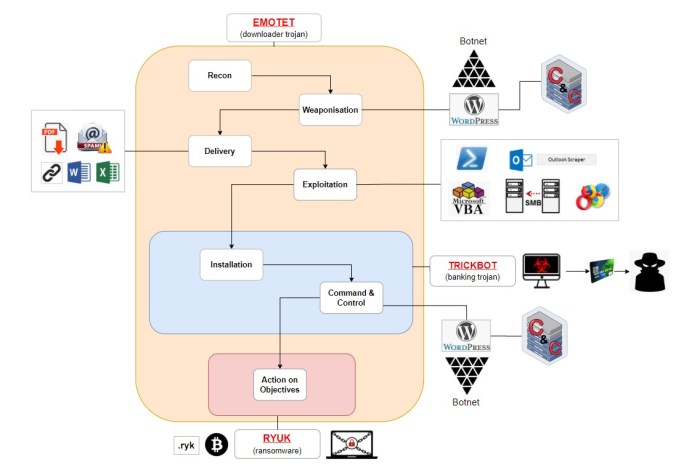
The Ghostwriter APT infrastructure, as detailed by researchers, represents a sophisticated and persistent threat actor. Its modular design and use of various techniques make it a challenging adversary to detect and neutralize. Understanding its components and functionalities is crucial for developing effective countermeasures. This analysis will delve into the infrastructure’s architecture, comparing it to known APT group structures and highlighting potential vulnerabilities.
Ghostwriter Infrastructure Components and Functionalities
The Ghostwriter infrastructure is characterized by a layered architecture, employing various tools and techniques for maintaining persistence, exfiltrating data, and controlling compromised systems. Key components include command-and-control (C2) servers, custom malware, and various techniques for evading detection. The C2 servers act as the central hub, coordinating operations and delivering commands to the compromised systems. Custom malware, tailored to specific targets, performs the actual data exfiltration and system control. The use of various evasion techniques, such as using legitimate software for malicious purposes, obfuscation, and anti-analysis measures, makes detection challenging.
Comparison with Known APT Infrastructure Architectures
The Ghostwriter infrastructure shares similarities with other known APT groups, such as using a multi-stage attack process and employing custom malware for specific targets. However, the precise techniques and tools used by Ghostwriter differ, indicating unique operational procedures and potentially a different origin or affiliation compared to other known groups. For example, while many APTs rely heavily on specific exploits, Ghostwriter might leverage a broader range of techniques, making attribution more difficult. Some similarities might include the use of legitimate software for malicious purposes (living off the land) and the use of encryption to protect communications. However, the specific implementations and the overall architecture might differ significantly.
Key Components, Functions, and Vulnerabilities of the Ghostwriter Infrastructure
| Component | Function | Vulnerability | Mitigation |
|---|---|---|---|
| Command-and-Control (C2) Servers | Centralized communication and control of compromised systems; delivery of commands and malware updates. | Compromise of C2 servers can disrupt operations and provide insights into the attacker’s activities. Detection of C2 traffic through network monitoring. | Employing robust security measures on C2 servers, including intrusion detection systems and regular security audits. Using encryption and obfuscation techniques to make C2 traffic harder to detect. |
| Custom Malware | Data exfiltration, system control, and persistence on compromised systems. | Vulnerabilities in the malware’s code can be exploited for analysis and potentially for disruption of its operation. Reverse engineering of the malware to identify vulnerabilities. | Regular updates and patching of systems. Employing sandboxing and other techniques to analyze the malware in a controlled environment. Using code signing and other techniques to increase trust and reduce the likelihood of infection. |
| Evasion Techniques | Obfuscation, anti-analysis, and use of legitimate software for malicious purposes. | Sophisticated evasion techniques can make detection difficult, but they may still leave traces that can be identified through advanced analysis. Over-reliance on a specific evasion technique, leaving it vulnerable to discovery. | Employing advanced threat detection techniques, including behavioral analysis and machine learning. Regular security awareness training for personnel. |
| Data Exfiltration Channels | Methods used to transfer stolen data from compromised systems to the attacker’s infrastructure. | Compromise of exfiltration channels can disrupt operations and provide insights into the attacker’s activities. Detection of unusual network traffic patterns. | Monitoring network traffic for suspicious activity. Implementing data loss prevention (DLP) measures. Using encryption to protect data in transit. |
Attack Vectors and Techniques Employed

Source: studylib.net
Ghostwriter, a sophisticated advanced persistent threat (APT) group, utilizes a multi-faceted approach to compromise its targets. Their operations are characterized by a blend of established techniques and custom-developed tools, demonstrating a high level of technical expertise and operational security. Understanding their attack vectors and techniques is crucial for effective defense.
The group’s success hinges on its ability to blend into the background, leveraging existing vulnerabilities and exploiting human error. Their methods are not flashy; instead, they rely on stealth and persistence, making detection and attribution challenging. This focus on subtlety underscores the need for robust security practices and proactive threat hunting.
Initial Compromise Vectors
Ghostwriter’s initial compromise often leverages spear-phishing campaigns. These campaigns typically involve highly targeted emails containing malicious attachments or links designed to exploit known vulnerabilities in commonly used software. The emails are meticulously crafted to appear legitimate, often mimicking communication from trusted sources or incorporating information specific to the target organization. This personalization significantly increases the likelihood of a successful attack. Beyond spear-phishing, the group has also been known to exploit zero-day vulnerabilities and software supply chain compromises for initial access. The exploitation of these vulnerabilities often leads to the deployment of custom malware tailored to specific targets.
Lateral Movement Techniques
Once initial access is gained, Ghostwriter employs a range of techniques for lateral movement within the compromised network. This involves exploiting system vulnerabilities, leveraging compromised credentials, and utilizing legitimate administrative tools to gain access to higher-privilege accounts and sensitive data. Pass-the-hash techniques, where stolen credentials are used to access other systems, are frequently employed. The group also demonstrates proficiency in using tools such as PowerShell for command and control, allowing them to maintain a low profile and evade detection. Their lateral movement is carefully planned and executed, aiming to remain undetected while accessing critical systems and data.
Persistence Mechanisms
Maintaining persistence within the compromised environment is critical for Ghostwriter’s long-term objectives. They achieve this through various methods, including the installation of backdoors, the modification of system configurations, and the use of scheduled tasks. These techniques allow them to maintain access to the compromised systems even after reboots or security updates. The group frequently uses custom malware and scripts to ensure persistence, often embedding these within legitimate system processes to evade detection. This persistent presence allows them to conduct espionage, data exfiltration, and other malicious activities over extended periods.
Stages of a Typical Ghostwriter Attack Lifecycle
The following points Artikel the typical stages of a Ghostwriter attack:
- Initial Access: Spear-phishing, zero-day exploits, or supply chain attacks.
- Reconnaissance: Mapping the network infrastructure and identifying high-value targets.
- Lateral Movement: Moving between systems to gain broader access and privileges.
- Privilege Escalation: Gaining elevated access to critical systems and data.
- Data Exfiltration: Stealing sensitive information, often using covert channels.
- Persistence: Establishing mechanisms to maintain long-term access to the compromised systems.
- Command and Control (C2): Maintaining communication with the attacker’s infrastructure.
Targets and Objectives of the Ghostwriter Group

Source: githubassets.com
The Ghostwriter APT group, known for its sophisticated cyber espionage operations, has targeted a range of entities, revealing a clear pattern in its selection of victims and its overall objectives. Understanding these targets and objectives is crucial for building effective defenses against future attacks and for attributing responsibility for past incidents. The group’s operational methodology, while advanced, often leaves behind digital breadcrumbs that allow researchers to piece together a clearer picture of its motives and targets.
The primary targets of Ghostwriter operations appear to be government institutions and organizations within Central and Eastern Europe, particularly those involved in politics, diplomacy, and defense. This focus suggests a strategic intent beyond simple data theft, pointing towards a campaign of influence operations and information gathering for geopolitical advantage. The objectives are less about financial gain and more about achieving strategic political goals. This contrasts with some other APT groups which are primarily focused on intellectual property theft or financial fraud.
Target Types and Objectives
The following table summarizes the identified targets and the likely objectives of the Ghostwriter group, drawing on findings from multiple cybersecurity research reports. It’s important to note that attribution in the cyber world is complex, and these findings represent the current consensus within the security community. Further investigation and analysis may reveal additional targets and objectives in the future.
| Target Type | Objective |
|---|---|
| Government Ministries (e.g., Foreign Affairs, Defense) | Intelligence gathering, influence operations, compromising sensitive policy documents. This allows the group to understand the political landscape, predict future actions, and potentially influence decision-making. |
| Political Parties and Think Tanks | Gathering intelligence on political strategies, identifying key influencers, and potentially spreading disinformation or propaganda to sway public opinion. |
| Media Outlets and Journalists | Compromising journalistic sources, spreading disinformation, and influencing public narratives. This could include planting false stories or discrediting legitimate news sources. |
| Non-Governmental Organizations (NGOs) | Understanding the activities and influence of NGOs, potentially to identify and target those perceived as threats or obstacles to the group’s goals. |
Comparison with Other APT Groups
While Ghostwriter shares some characteristics with other APT groups, its focus on Central and Eastern European targets and its emphasis on influence operations distinguishes it from many others. Groups like APT28 (Fancy Bear) and APT30 (Stone Panda) also engage in espionage, but their targets and objectives often differ. APT28, for example, has a broader geographical scope and a greater focus on military intelligence, whereas Ghostwriter’s actions seem more targeted towards influencing political processes. The difference highlights the varied motivations and goals behind different state-sponsored cyber operations. The specificity of Ghostwriter’s targets suggests a highly focused campaign with clear political objectives, rather than a broader, more opportunistic approach seen in some other groups.
Attribution and Indicators of Compromise (IOCs): Researchers Detailed The Ghostwriter Apt Infrastructure
Pinpointing the perpetrators behind sophisticated cyberattacks like those attributed to the Ghostwriter group requires meticulous analysis of various digital fingerprints left behind. Researchers employ a multi-faceted approach, combining technical indicators with geopolitical context and operational patterns to build a compelling case for attribution. This process isn’t about absolute certainty, but rather constructing a high-confidence assessment based on the weight of evidence.
Attributing malicious infrastructure to a specific group, like Ghostwriter, relies on a convergence of evidence. This includes analyzing the techniques, tactics, and procedures (TTPs) employed in the attacks, identifying overlaps with previously known campaigns, and examining the infrastructure’s characteristics such as command-and-control (C2) servers, malware code, and data exfiltration methods. The unique blend of these factors helps researchers build a strong case for attribution.
Evidence for Ghostwriter Attribution
The attribution of the Ghostwriter APT infrastructure is supported by a combination of factors. Researchers have observed consistent use of specific malware families, overlapping infrastructure components across multiple campaigns, and similar operational techniques. For example, the use of specific code obfuscation methods, unique command-and-control server configurations, and the targeting of similar victim organizations all contribute to the overall attribution assessment. Furthermore, analysis of the language used in phishing emails and the geographical location of compromised systems can provide further corroborating evidence. The combination of these technical and contextual indicators strengthens the overall attribution.
Indicators of Compromise (IOCs) Associated with Ghostwriter
The following indicators of compromise are associated with the Ghostwriter APT infrastructure. Detecting these IOCs is crucial for effective prevention and mitigation strategies.
- Specific malware hashes: Researchers have identified specific SHA-256 hashes associated with malware used by Ghostwriter. These hashes can be used to detect infected systems and prevent further propagation.
- Command and Control (C2) server IP addresses and domains: Identifying and blocking known C2 servers prevents communication with the attacker’s infrastructure.
- Suspicious email addresses and domains: Ghostwriter often uses spear-phishing emails to deliver malware. Monitoring for emails originating from or containing links to known malicious domains is critical.
- Unusual network traffic patterns: Ghostwriter’s activities might involve unusual data exfiltration patterns or communication with uncommon ports. Network monitoring tools can detect these anomalies.
- Specific file paths and registry keys: Malware often modifies specific file paths and registry keys. Monitoring for these changes can indicate a compromise.
Method for Detecting and Preventing Future Attacks
Leveraging the identified IOCs, a multi-layered defense strategy is essential. This involves implementing robust security information and event management (SIEM) systems capable of correlating security alerts across various sources. Regular vulnerability scanning and patching are critical to eliminate known vulnerabilities exploited by Ghostwriter. Furthermore, security awareness training for employees is crucial to mitigate phishing attacks. Employing advanced threat protection solutions that can analyze file behavior and network traffic in real-time is also highly effective. Finally, proactive threat hunting based on known Ghostwriter TTPs can identify potential intrusions before they escalate.
Utilizing IOCs in Threat Intelligence Platforms
Threat intelligence platforms (TIPs) play a vital role in leveraging IOCs effectively. By integrating the IOCs into TIPs, organizations can proactively monitor their networks for malicious activity. TIPs can automatically correlate observed IOCs with threat intelligence feeds, providing context and prioritizing alerts based on the severity and likelihood of an attack. This allows security teams to focus on high-priority threats and respond quickly to incidents. Furthermore, TIPs can help organizations track the evolution of Ghostwriter’s tactics and adapt their security measures accordingly. This continuous monitoring and adaptation are essential for maintaining a strong defense against advanced persistent threats.
Impact and Mitigation Strategies
The Ghostwriter APT infrastructure, with its sophisticated techniques and persistent operations, poses a significant threat to targeted organizations. The potential impact extends far beyond simple data breaches; it can cripple operations, damage reputations, and result in substantial financial losses. Understanding the potential consequences and implementing robust mitigation strategies is crucial for effective cybersecurity.
The impact of a successful Ghostwriter attack can be devastating. Data exfiltration, for example, can lead to intellectual property theft, compromising trade secrets and giving competitors a significant advantage. Disruption of operations through malware deployment can halt production, disrupt services, and severely impact revenue streams. Furthermore, the reputational damage from a publicized attack can be long-lasting, eroding customer trust and impacting investor confidence. The financial costs associated with recovery, including legal fees, regulatory fines, and remediation efforts, can be astronomical. For example, a successful attack against a pharmaceutical company could result in the theft of drug formulas, leading to millions, if not billions, of dollars in lost revenue and potential legal battles.
Potential Impacts on Targeted Organizations
A successful Ghostwriter operation can have far-reaching consequences for targeted organizations. These include, but are not limited to: Data breaches exposing sensitive information such as intellectual property, customer data, and financial records; Disruption of critical operations through malware deployment and denial-of-service attacks; Reputational damage leading to loss of customer trust and investor confidence; Significant financial losses due to remediation efforts, legal fees, and regulatory fines; Legal and regulatory repercussions due to non-compliance with data protection regulations; Long-term operational disruption and decreased productivity. The specific impact will vary depending on the organization’s size, industry, and the nature of the compromised data and systems.
Mitigation Strategies and Security Measures, Researchers detailed the ghostwriter apt infrastructure
Preventing successful exploitation of Ghostwriter-like attacks requires a multi-layered approach to cybersecurity. This includes proactive measures to identify and prevent intrusions, as well as reactive measures to contain and remediate any damage. A robust security posture is essential, combining technical controls with employee training and awareness programs.
Mitigation Strategies, Effectiveness, and Implementation Costs
| Strategy | Effectiveness | Cost |
|---|---|---|
| Regular Security Audits and Penetration Testing | High – Proactive identification of vulnerabilities | Medium – Varies based on scope and frequency |
| Endpoint Detection and Response (EDR) Solutions | High – Real-time threat detection and response | High – Requires software licenses and skilled personnel |
| Security Information and Event Management (SIEM) Systems | High – Centralized log management and threat detection | High – Requires software licenses, hardware, and skilled personnel |
| Employee Security Awareness Training | Medium – Reduces human error, a common attack vector | Low – Primarily involves training materials and time |
| Multi-Factor Authentication (MFA) | High – Adds an extra layer of security to user accounts | Low – Relatively inexpensive to implement |
| Network Segmentation | High – Limits the impact of a breach by isolating sensitive systems | Medium – Requires network infrastructure changes |
| Regular Software Updates and Patching | High – Addresses known vulnerabilities | Low – Requires minimal cost beyond time investment |
| Data Loss Prevention (DLP) Solutions | High – Prevents sensitive data from leaving the network | High – Requires software licenses and integration with existing systems |
| Threat Intelligence Platforms | Medium – Provides early warning of potential threats | Medium to High – Depends on the platform and level of service |
| Incident Response Plan | High – Ensures a coordinated response to a security incident | Low to Medium – Primarily involves planning and documentation |
Final Thoughts
The detailed examination of the Ghostwriter APT infrastructure paints a clear picture of a highly organized and capable threat actor. Understanding their tactics, targets, and the IOCs associated with their operations is crucial for effective cybersecurity defenses. By implementing the mitigation strategies Artikeld, organizations can significantly reduce their vulnerability to similar attacks. The fight against sophisticated cyber threats is ongoing, and staying informed is the first line of defense. This investigation serves as a stark reminder of the ever-evolving landscape of cyber warfare and the importance of proactive security measures.


