Pentagon Vulnerability Report: It sounds like a top-secret thriller, right? And it kind of is. This report dives deep into the hidden weaknesses within the US Department of Defense’s systems – from software glitches to physical security lapses. We’re talking about vulnerabilities that could potentially unravel national security, leaving the Pentagon exposed to cyberattacks and other threats. This isn’t just about lines of code; it’s about the real-world impact of these flaws and the constant battle to stay one step ahead of those who would exploit them.
We’ll explore the evolution of vulnerability reporting, the various types of threats faced, and the Pentagon’s complex response mechanisms. We’ll also look at the human element – the whistleblowers, the investigators, and the engineers working tirelessly to patch these holes before they’re exploited. Get ready for a peek behind the curtain of national security, where the stakes are higher than ever.
Pentagon Vulnerability Report
The Pentagon’s vulnerability reporting system, while seemingly impenetrable, has undergone a fascinating evolution over the past two decades. From a relatively opaque and reactive approach to a more proactive and (at least in theory) transparent system, the journey reflects broader changes in cybersecurity understanding and the increasing sophistication of threats. This evolution hasn’t been a smooth, linear progression; it’s been punctuated by significant events and policy shifts that have reshaped how vulnerabilities are identified, reported, and addressed.
Pentagon Vulnerability Reporting: A Historical Overview
The early 2000s saw a largely decentralized approach to vulnerability reporting within the Department of Defense (DoD). Many individual agencies and branches maintained their own systems, leading to inconsistencies and potential gaps in overall security. Reporting was often reactive, triggered by incidents rather than proactive vulnerability assessments. Communication between different parts of the DoD was not streamlined, hindering effective response. This fragmented landscape was ill-equipped to handle the growing complexity of cyber threats.
Key Events Shaping Vulnerability Reporting, Pentagon vulnerability report
Several key events significantly impacted the evolution of Pentagon vulnerability reporting. The rise of sophisticated cyberattacks, such as the 2007 Estonia cyberattacks and the 2008 Georgia cyberwar, highlighted the urgent need for improved cybersecurity practices and coordinated vulnerability reporting. The 2010 Stuxnet worm, a sophisticated piece of malware targeting Iranian nuclear facilities, further underscored the threat landscape and the importance of robust vulnerability management. These incidents, along with several high-profile data breaches affecting government agencies, served as catalysts for reform. Subsequent legislation and policy changes mandated increased transparency and improved information sharing, leading to a more centralized and structured reporting system. The establishment of the Cybersecurity and Infrastructure Security Agency (CISA) also played a pivotal role in improving national cybersecurity coordination and vulnerability response.
Comparison of Past and Present Reporting Mechanisms
Historically, vulnerability reporting within the Pentagon relied heavily on internal channels and a limited number of external partnerships. The process was often slow, bureaucratic, and lacked the transparency needed for effective threat response. Today, the Pentagon utilizes a more sophisticated and integrated approach. This includes dedicated vulnerability disclosure programs, improved communication channels with external security researchers (often through bug bounty programs), and a greater emphasis on proactive vulnerability assessments and penetration testing. While complete transparency remains a challenge due to national security concerns, the shift towards greater collaboration and information sharing marks a significant improvement.
Timeline of Major Changes and Milestones
Understanding the evolution requires a chronological overview:
| Year | Event/Milestone | Impact on Reporting |
|---|---|---|
| 2003-2007 | Decentralized reporting, reactive approach | Inconsistent reporting, slow response times |
| 2007-2010 | Significant cyberattacks (Estonia, Georgia), Stuxnet | Increased awareness of vulnerability, calls for improved security |
| 2010-2015 | Increased focus on cybersecurity, legislative changes | Development of more centralized reporting systems, improved information sharing |
| 2015-Present | Establishment of CISA, increased use of bug bounty programs | Greater collaboration with external security researchers, more proactive approach |
Types of Vulnerabilities Reported
The Pentagon’s vulnerability reports encompass a wide range of security weaknesses, impacting various aspects of its operational infrastructure. Understanding these vulnerabilities is crucial for effective mitigation and the overall security posture of the Department of Defense. This section categorizes these vulnerabilities, providing examples and illustrating their potential impact.
Software Vulnerabilities
Software vulnerabilities are flaws in the design, implementation, or operation of software that can be exploited by attackers. These flaws can range from simple coding errors to complex design weaknesses. Exploiting these vulnerabilities can lead to data breaches, system crashes, and unauthorized access.
| Category | Example | Potential Impact | Severity Level |
|---|---|---|---|
| Software Bugs | Buffer overflow vulnerability in a critical defense system | System crash, data corruption, unauthorized code execution | Critical |
| Outdated Software | Using an unpatched version of a widely used operating system | Exposure to known exploits, data breaches, denial-of-service attacks | High |
| Improper Input Validation | A web application failing to sanitize user inputs, leading to SQL injection | Data breaches, unauthorized access to sensitive information, system compromise | High |
Hardware Vulnerabilities
Hardware vulnerabilities relate to weaknesses in the physical components of systems. These vulnerabilities can range from easily exploitable physical access points to sophisticated hardware Trojans embedded during manufacturing. Exploiting these vulnerabilities can result in data theft, system malfunction, and physical damage.
| Category | Example | Potential Impact | Severity Level |
|---|---|---|---|
| Physical Access | Lack of physical security controls allowing unauthorized access to servers | Data theft, equipment damage, unauthorized system access | High |
| Hardware Trojans | Malicious hardware components intentionally embedded within a system | Data exfiltration, system compromise, espionage | Critical |
| Hardware Failure | Failure of a critical component leading to system outage | Disruption of operations, loss of data, financial losses | Medium to High (depending on the criticality of the component) |
Network Vulnerabilities
Network vulnerabilities expose weaknesses in the communication infrastructure. These vulnerabilities can arise from insecure network configurations, outdated network equipment, or the use of weak encryption protocols. Exploiting these vulnerabilities can lead to denial-of-service attacks, data interception, and unauthorized network access.
| Category | Example | Potential Impact | Severity Level |
|---|---|---|---|
| Unsecured Wi-Fi Networks | Lack of encryption on a wireless network | Data interception, unauthorized network access | High |
| Weak Passwords | Use of easily guessable passwords on network devices | Unauthorized access to network resources | Medium |
| Denial-of-Service Attacks | Overwhelming a network with traffic, rendering it inaccessible | Disruption of services, loss of productivity | High |
Physical Security Vulnerabilities
Physical security vulnerabilities relate to weaknesses in the physical protection of assets. This includes vulnerabilities in building security, access control, and perimeter protection. Exploiting these vulnerabilities can lead to theft of equipment, data breaches, and physical harm to personnel.
| Category | Example | Potential Impact | Severity Level |
|---|---|---|---|
| Insufficient Access Control | Lack of proper access control measures at sensitive facilities | Unauthorized access to sensitive areas and equipment | High |
| Weak Perimeter Security | Inadequate fencing or surveillance around critical infrastructure | Physical intrusion, theft of equipment, sabotage | High |
| Lack of Surveillance | Absence of CCTV cameras or other surveillance systems | Increased risk of theft, vandalism, and unauthorized access | Medium |
Sources and Methods of Vulnerability Discovery
Uncovering weaknesses in the Pentagon’s vast digital infrastructure is a complex, multi-faceted undertaking, relying on a range of sources and employing diverse methodologies. The accuracy and timeliness of vulnerability discovery directly impacts the Pentagon’s ability to maintain its cybersecurity posture and protect sensitive information. This section delves into the various approaches used, weighing their strengths and weaknesses.
Internal Audits and Assessments
Regular internal audits and security assessments are crucial for proactive vulnerability identification. These involve systematic reviews of systems, networks, and applications within the Pentagon’s control. Teams of internal security experts use established methodologies like vulnerability scanning, penetration testing (though often limited in scope compared to external efforts), and code reviews to pinpoint weaknesses.
- Pros: Provides continuous monitoring, allows for early detection, and fosters a culture of security awareness within the organization. Internal teams possess intimate knowledge of the systems.
- Cons: Can be limited by internal biases, may miss vulnerabilities due to familiarity with systems, and resource constraints can restrict the scope and frequency of audits.
External Penetration Testing
Unlike internal audits, external penetration testing simulates real-world attacks from the perspective of a malicious actor. Specialized security firms or government agencies conduct these tests, attempting to breach the Pentagon’s defenses using a variety of techniques. This approach provides a more objective and comprehensive evaluation of vulnerabilities.
- Pros: Offers a realistic assessment of security posture, identifies vulnerabilities that internal teams might miss, and provides valuable insights into attacker methodologies.
- Cons: Can be expensive and time-consuming, requires careful planning and coordination, and might reveal sensitive information if not properly managed.
Whistleblower Reports
While less structured, whistleblower reports can be a critical source of vulnerability information. Individuals with inside knowledge of security flaws may choose to report them, potentially uncovering vulnerabilities that other methods might miss. Effective whistleblower protection programs are crucial for encouraging such disclosures.
- Pros: Can reveal vulnerabilities missed by automated tools or internal reviews, often provides detailed context and exploit information.
- Cons: Reports may lack technical detail or be unreliable, requires thorough investigation and verification, and relies on the willingness of individuals to come forward.
Vulnerability Scanning and Automated Tools
Automated vulnerability scanners are widely used to identify known vulnerabilities by comparing system configurations against publicly available databases of known weaknesses (like the National Vulnerability Database). These tools can rapidly scan large networks, identifying potential issues quickly.
- Pros: Efficient and cost-effective for initial vulnerability identification, covers a broad range of systems and applications.
- Cons: Produces a high volume of false positives, may miss zero-day vulnerabilities (newly discovered flaws), and requires expert interpretation of results.
Effectiveness Comparison
The effectiveness of each method varies depending on the specific context. External penetration testing generally provides a more comprehensive assessment than internal audits, but it is more costly. Whistleblower reports can be invaluable, but they require careful vetting. Automated tools are efficient for initial screening but require human expertise for accurate interpretation. A combined approach, leveraging the strengths of multiple methods, is often the most effective strategy. For instance, a vulnerability discovered through automated scanning might be further investigated via manual penetration testing to verify its exploitability and impact.
Impact and Remediation of Vulnerabilities: Pentagon Vulnerability Report
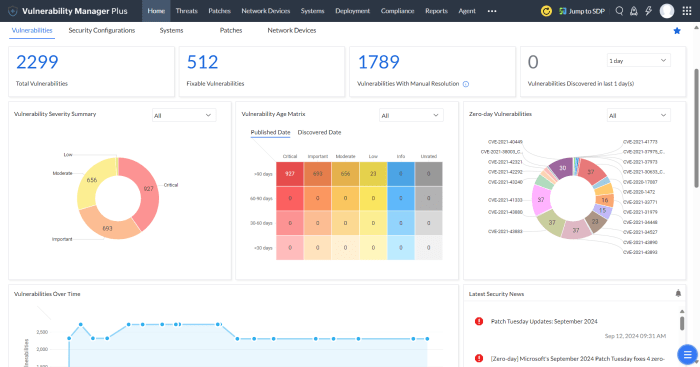
Source: manageengine.com
The Pentagon’s vulnerability to cyberattacks carries significant consequences, ranging from data breaches and operational disruptions to national security threats. Understanding the impact of these vulnerabilities and the processes used to remediate them is crucial for maintaining the integrity and security of the nation’s defense systems. Failure to address vulnerabilities promptly can lead to catastrophic outcomes, highlighting the need for robust remediation strategies.
Unpatched vulnerabilities can have far-reaching consequences. For instance, a successful cyberattack could compromise sensitive military plans, intelligence data, or even weapon systems. The real-world impact is not merely theoretical; leaked classified documents, compromised communication networks, and disrupted operations are all potential outcomes of unaddressed vulnerabilities. Imagine a scenario where a sophisticated adversary gains access to a critical defense system controlling drone deployments. The potential for devastating consequences is clear. The cost of such an attack, including financial losses, reputational damage, and potential loss of life, is immeasurable.
Remediation Processes and Procedures
Remediating reported vulnerabilities involves a multi-stage process. First, the vulnerability is verified and assessed to determine its severity and potential impact. This involves analyzing the nature of the vulnerability, the systems affected, and the potential consequences of exploitation. Next, a remediation plan is developed, which may involve patching software, implementing security controls, or upgrading hardware. This plan is then implemented, often in a phased approach to minimize disruption to ongoing operations. Finally, the effectiveness of the remediation is validated through testing and monitoring to ensure the vulnerability has been successfully addressed. This rigorous approach ensures that the Pentagon’s systems remain resilient against cyber threats.
Resources and Expertise Required for Effective Remediation
Effective remediation requires significant resources and expertise. This includes skilled cybersecurity professionals with specialized knowledge in vulnerability analysis, penetration testing, and incident response. Furthermore, access to advanced tools and technologies, such as vulnerability scanners, intrusion detection systems, and security information and event management (SIEM) platforms, is essential. The Pentagon relies on a network of internal and external experts, including government agencies, private sector companies, and academic institutions, to ensure that it has the resources needed to effectively address vulnerabilities. The investment in these resources is a critical component of maintaining a strong cybersecurity posture.
Consequences of Delayed or Ineffective Remediation
Delayed or ineffective remediation can have severe consequences, potentially leading to a significant security breach. Consider a hypothetical scenario: a vulnerability in a Pentagon system controlling nuclear launch codes remains unpatched for an extended period. A sophisticated state-sponsored actor exploits this vulnerability, gaining unauthorized access to the system and potentially altering launch codes. The ramifications of such a scenario are catastrophic, potentially triggering a global crisis. This illustrates the critical importance of timely and effective remediation in preventing devastating consequences. The cost of inaction far outweighs the cost of proactive security measures.
Pentagon’s Response to Vulnerability Reports

Source: wired.com
The Pentagon’s response to vulnerability reports is a complex, multi-layered process designed to ensure the security of its vast network of systems and data. This involves a coordinated effort across various departments and agencies, prioritizing threats based on severity and potential impact. Efficiency and speed are paramount to mitigate risks effectively.
The process begins with the initial report itself, which is then channeled through established channels to the appropriate teams. These teams assess the vulnerability, determine its severity, and then develop and implement a remediation strategy. This involves a continuous feedback loop to ensure effective mitigation and ongoing system security. The entire process is governed by strict protocols to maintain confidentiality and accountability.
Internal Processes for Handling and Prioritizing Vulnerability Reports
The Pentagon utilizes a tiered system for handling vulnerability reports, prioritizing those with the most immediate and significant potential impact. Reports are categorized based on factors like the criticality of the affected system, the ease of exploitation, and the potential consequences of a successful attack. A scoring system, often incorporating CVSS (Common Vulnerability Scoring System) metrics, guides this prioritization. Higher-scoring vulnerabilities receive immediate attention and resources, while lower-scoring vulnerabilities are addressed according to a predetermined schedule. This ensures that the most critical threats are addressed first, minimizing the overall risk to national security. The process also includes regular reviews and adjustments to the prioritization scheme to adapt to evolving threat landscapes.
Key Stakeholders Involved in the Response Process
Several key stakeholders are involved in the Pentagon’s response to vulnerability reports. This includes specialized cybersecurity teams within each branch of the military, the Defense Information Systems Agency (DISA), the National Security Agency (NSA), and external cybersecurity firms contracted for specific expertise. Each stakeholder plays a unique role, contributing their specialized knowledge and resources to the overall response. For instance, DISA might focus on network-level vulnerabilities, while the NSA might handle intelligence gathering related to potential exploits. Internal and external communication is crucial for coordinated action. Regular meetings and briefings are held to keep stakeholders informed and ensure a unified response.
Communication Protocols Used to Inform Relevant Parties
Communication protocols are critical to the Pentagon’s vulnerability response process. Secure channels are used to relay information, often employing encrypted systems to protect sensitive data. The communication process begins with the initial report, which may be submitted through various channels, including internal reporting systems, external bug bounty programs, or intelligence agencies. The information is then disseminated through a structured chain of command, ensuring that all relevant parties are informed promptly and accurately. This includes regular updates on the status of the vulnerability, the remediation efforts, and any ongoing monitoring activities. A formal communication log is maintained to document all actions and decisions taken. This structured approach ensures transparency and accountability throughout the process.
Flowchart Illustrating the Pentagon’s Response to a Vulnerability Report
[Imagine a flowchart here. The flowchart would begin with “Vulnerability Report Received,” branching into “Assessment and Prioritization” (including severity scoring), then “Remediation Planning,” followed by “Implementation and Testing,” and finally “Monitoring and Ongoing Security.” Each step would have associated details, such as the specific teams involved and the communication protocols used. The flowchart would visually represent the sequential and iterative nature of the Pentagon’s response process, highlighting the feedback loops and decision points involved.]
External Factors Influencing Vulnerability Reporting
The Pentagon’s vulnerability reporting process isn’t conducted in a vacuum. A complex interplay of external forces – evolving cyber threats, regulatory landscapes, technological advancements, and comparative practices – significantly shapes its effectiveness and efficiency. Understanding these influences is crucial for assessing the overall security posture of the Department of Defense.
The landscape of cyber threats is in constant flux, demanding a dynamic approach to vulnerability reporting. New attack vectors emerge regularly, necessitating continuous adaptation in identification, assessment, and remediation strategies. For instance, the rise of sophisticated AI-driven attacks necessitates more advanced vulnerability detection methods and quicker response times, impacting the prioritization and handling of reported vulnerabilities. This necessitates a continuous cycle of improvement and adaptation within the Pentagon’s reporting framework.
Evolving Cyber Threats and Vulnerability Reporting Practices
The increasing sophistication and frequency of cyberattacks directly influence the Pentagon’s vulnerability reporting practices. The shift from simple malware to advanced persistent threats (APTs) and nation-state-sponsored attacks requires a more proactive and intelligence-driven approach to vulnerability management. This means a shift from reactive patching to predictive analysis and proactive threat hunting, impacting how vulnerabilities are identified, prioritized, and addressed. The Pentagon’s reporting systems must be agile enough to adapt to these emerging threats, incorporating new threat intelligence and analysis techniques into its processes. The time sensitivity of addressing critical vulnerabilities has also increased dramatically, pushing for faster response times and more streamlined reporting procedures.
External Regulations and Standards Influencing Reporting
Several external regulations and standards significantly influence the Pentagon’s vulnerability reporting processes. Compliance with laws like the Federal Information Security Management Act (FISMA) and the Cybersecurity and Infrastructure Security Agency (CISA) guidelines mandates specific reporting procedures and security controls. Furthermore, adherence to industry best practices and standards like NIST Cybersecurity Framework further shapes the reporting mechanisms and the overall security posture. These regulations often dictate the level of detail required in vulnerability reports, the reporting timelines, and the types of vulnerabilities that must be reported. Non-compliance can lead to significant penalties and reputational damage.
Technological Advancements and Vulnerability Management
Technological advancements are continuously reshaping vulnerability discovery and remediation. The advent of automated vulnerability scanning tools, penetration testing techniques, and threat intelligence platforms has drastically improved the speed and efficiency of identifying vulnerabilities. However, this also presents challenges; the sheer volume of vulnerabilities detected requires advanced prioritization and triage systems to effectively manage and remediate them. Furthermore, the development of new technologies, like cloud computing and Internet of Things (IoT) devices, introduces new attack surfaces and requires adapting vulnerability reporting practices to encompass these emerging threats. The Pentagon must invest in and adopt these advanced technologies to maintain a robust security posture.
Comparison of Vulnerability Reporting Practices
The Pentagon’s vulnerability reporting practices can be compared to those of other government agencies and private sector organizations. While specifics vary based on the organization’s size, mission, and regulatory environment, common themes include the use of vulnerability scanning tools, penetration testing, and vulnerability databases. However, the Pentagon’s reporting process is likely more stringent due to the high-stakes nature of its operations and the sensitive nature of the data it handles. Private sector organizations may have more flexible reporting processes, but often face similar challenges in balancing security with operational efficiency. Government agencies, like the Pentagon, generally prioritize security and compliance more heavily, leading to more formal and structured reporting procedures. This comparison helps identify best practices and areas for improvement within the Pentagon’s framework.
Illustrative Example: A Hypothetical Vulnerability
Let’s imagine a scenario involving a hypothetical vulnerability within the Pentagon’s highly secure network. This example will highlight the potential impact of even seemingly minor weaknesses and the process of addressing them. We’ll focus on a vulnerability related to access control, a common yet critical area of concern in any large organization, especially one handling sensitive national security information.
Our hypothetical vulnerability centers around a misconfiguration in a newly implemented authentication system for access to a specific database containing classified intelligence reports. This database, let’s call it “Project Nightingale,” houses highly sensitive information about ongoing covert operations. The misconfiguration allows unauthorized users with specific network privileges, but lacking the proper security clearance, to bypass the multi-factor authentication process under certain circumstances.
Vulnerability Exploitation
The vulnerability arises from a flaw in the system’s logic regarding the handling of user roles and permissions. Specifically, if a user attempts to access the database using a specific outdated application alongside their standard credentials, the authentication system fails to properly verify their clearance level before granting access. This outdated application, still present on some legacy systems, is incorrectly flagged as requiring only standard login credentials instead of the mandatory multi-factor authentication needed for access to Project Nightingale. An attacker aware of this flaw could leverage an account with network access but lacking the necessary security clearance, combined with the outdated application, to gain unauthorized access.
Potential Consequences
Successful exploitation of this vulnerability could have severe consequences. Unauthorized access to Project Nightingale could expose sensitive information, potentially compromising ongoing operations, endangering personnel involved in covert activities, and severely damaging national security. The leaked information could be used by foreign adversaries to disrupt operations, gain intelligence advantages, or even launch targeted attacks. The reputational damage to the Pentagon and the erosion of public trust would also be significant. This kind of breach could have far-reaching and long-lasting implications, similar to the damage caused by past leaks of classified information, which have impacted national security and international relations. For instance, the WikiLeaks disclosures highlighted the potential damage caused by a large-scale breach of classified documents.
Vulnerability Identification, Reporting, and Remediation
The hypothetical vulnerability might be initially identified during routine security audits or penetration testing. Security analysts reviewing system logs might notice unusual access patterns or authentication failures that indicate a potential bypass. Alternatively, a white-hat hacker participating in a bug bounty program might discover and report the vulnerability. Once identified, the vulnerability would be meticulously documented, including detailed steps to reproduce the exploit. This report would be submitted through established channels, potentially including a formal vulnerability disclosure process, and would be prioritized based on its potential impact. Remediation would involve patching the authentication system to correctly enforce multi-factor authentication for all users accessing Project Nightingale, regardless of the application used. This might also involve decommissioning the outdated application to eliminate the possibility of exploitation. Following the remediation, rigorous testing would be conducted to ensure the vulnerability is completely resolved and that no similar weaknesses remain.
Last Word
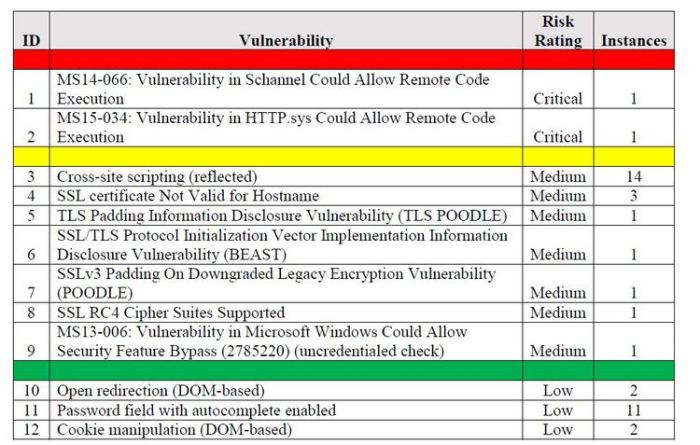
Source: alpinesecurity.com
The Pentagon Vulnerability Report isn’t just a document; it’s a snapshot of a continuous, high-stakes game of cat and mouse. As cyber threats evolve and technology advances, the challenge of securing such a vast and complex system remains a monumental task. The report highlights the critical importance of proactive measures, robust security protocols, and the constant vigilance required to protect national security in the digital age. The fight for digital dominance is ongoing, and the stakes couldn’t be higher.