IBM Cognos Analytics vulnerability: Sounds scary, right? But understanding the risks is the first step to securing your business data. […]
Software Testing
Apache HugeGraph Server Vulnerability A Deep Dive
Apache HugeGraph server vulnerability: The phrase alone sends shivers down the spines of database admins. This isn’t your grandpappy’s database; […]
US Intelligence Agencies Cyberattacked Chinese Tech Firms
U s intelligence agencies launched cyber attacks on chinese tech companies – US intelligence agencies launched cyber attacks on Chinese […]
Netwalker Ransomware Operator Sentenced
Netwalker ransomware operator sentenced – the headline screams it, and the implications reverberate across the digital world. This isn’t just […]
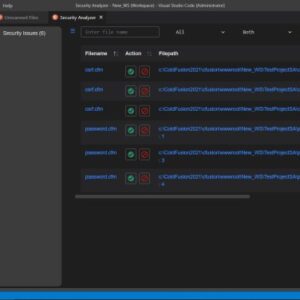
Adobe ColdFusion Vulnerability A Deep Dive
Adobe ColdFusion vulnerability: It’s a phrase that sends shivers down the spines of developers everywhere. For years, ColdFusion has powered […]
G Door Bypass Cracking Microsoft 365 Security
G door bypass microsoft 365 security – G Door Bypass: Microsoft 365 security, that seemingly impenetrable fortress, suddenly looks vulnerable. […]
Sharp Routers Vulnerabilities A Deep Dive
Sharp routers vulnerabilities? Yeah, we’re diving headfirst into the scary world of insecure home networks. Think your internet connection is […]