OWASP NHI Top 10 – ever heard of it? It’s the cybersecurity bible for web developers, outlining the most critical risks facing web applications. From sneaky injection attacks to the perils of insecure designs, understanding these top 10 vulnerabilities is crucial for building robust and safe online experiences. This isn’t just about ticking boxes; it’s about protecting your users and your business from potential disasters.
This guide dives deep into each of the OWASP NHI Top 10 vulnerabilities, providing real-world examples, mitigation strategies, and practical advice. We’ll explore the evolution of these threats, examining how they’ve changed over time and the devastating impact they’ve had on countless websites. Get ready to level up your web app security game.
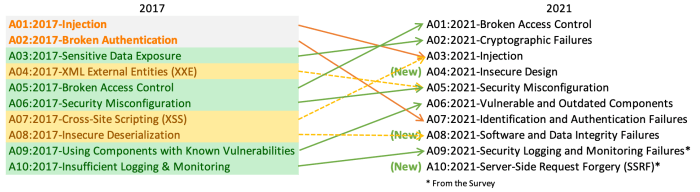
Introduction to OWASP NHI Top 10
The OWASP (Open Web Application Security Project) NHI (NoSQL Injection) Top 10 is a crucial resource for developers and security professionals aiming to build secure web applications. It highlights the most critical risks associated with NoSQL database vulnerabilities, providing a prioritized list to guide remediation efforts. Understanding and addressing these vulnerabilities is paramount in preventing data breaches, unauthorized access, and significant financial losses. This list, while focused on NoSQL, indirectly touches upon broader database security concerns, offering valuable lessons applicable beyond this specific technology.
The significance of the OWASP NHI Top 10 lies in its ability to provide a concise yet comprehensive overview of the most prevalent and dangerous NoSQL injection vulnerabilities. By focusing on these specific threats, developers can prioritize their security efforts, allocating resources effectively to mitigate the most impactful risks. Regularly updating security practices based on the OWASP NHI Top 10 ensures that applications remain resilient against evolving attack vectors. The list acts as a benchmark, allowing organizations to assess their security posture and identify areas needing improvement.
Evolution of the OWASP NHI Top 10
The OWASP NHI Top 10 has evolved over time, reflecting the changing landscape of NoSQL database technologies and attack techniques. Early versions primarily focused on basic injection flaws, such as improper input sanitization. Later versions have incorporated more sophisticated attacks, including those exploiting advanced features like map-reduce functions and improperly configured access controls. Each iteration reflects the lessons learned from real-world incidents and the development of new attack methodologies. For example, initial versions might have focused solely on preventing direct SQL-like injections, whereas later versions incorporated issues around improper authorization checks and data manipulation through NoSQL query languages. This continuous evolution ensures the list remains relevant and addresses current threats effectively. The evolution demonstrates a commitment to staying current with the latest vulnerabilities and attack techniques.
Historical Impact of NoSQL Injection Vulnerabilities
The impact of NoSQL injection vulnerabilities has been significant, resulting in numerous high-profile data breaches and financial losses. Several real-world examples illustrate the consequences of neglecting NoSQL database security. For instance, a poorly secured e-commerce platform vulnerable to NoSQL injection could expose sensitive customer data like credit card information and addresses, leading to identity theft and financial fraud. Similarly, a compromised healthcare application could result in the exposure of patient medical records, violating privacy regulations and potentially causing reputational damage. These incidents highlight the critical need for robust security measures and the importance of following best practices Artikeld in resources like the OWASP NHI Top 10. The cumulative cost of these breaches, including legal fees, remediation efforts, and reputational damage, underscores the economic imperative of prioritizing NoSQL database security. The consistent appearance of NoSQL injection vulnerabilities in reported data breaches emphasizes the ongoing relevance and importance of understanding and mitigating these risks.
Broken Access Control
Broken access control, in the simplest terms, is when an application doesn’t properly restrict access to its resources. Think of it like a poorly secured building: anyone can wander in and out, accessing areas they shouldn’t. This vulnerability allows attackers to bypass intended security measures and gain unauthorized access to sensitive data or functionalities, leading to data breaches, account takeovers, and even system compromise. It’s a serious threat that can have far-reaching consequences.
This vulnerability manifests in various ways, often subtle and easily overlooked during development. Understanding the different types is crucial for effective mitigation.
Types of Broken Access Control Vulnerabilities
Broken access control vulnerabilities come in many flavors. They aren’t always obvious, and often stem from flaws in how an application manages user permissions and authorization. Here are some key categories:
- Insufficient Authorization Checks: The application doesn’t properly verify if a user has the necessary permissions before granting access to a resource. For example, a user might be able to access another user’s profile or edit data they shouldn’t be able to modify.
- Broken Authentication and Session Management: Weaknesses in how the application handles authentication and sessions can allow attackers to hijack sessions or impersonate other users. This could involve vulnerabilities like session hijacking or cross-site request forgery (CSRF).
- Improper Input Validation: If an application doesn’t properly validate user inputs, attackers might be able to manipulate parameters to gain access to restricted resources. For example, changing a user ID in a URL to access another user’s data.
- Unprotected APIs: Web APIs that lack proper authentication and authorization mechanisms are vulnerable to attacks. Attackers can potentially access sensitive data or perform unauthorized actions through these APIs.
- Vertical Privilege Escalation: This occurs when a user with lower privileges is able to elevate their access level to a higher one, often by exploiting flaws in the application’s access control logic.
- Horizontal Privilege Escalation: This allows an attacker to access resources belonging to other users with the same privilege level.
Real-World Examples of Broken Access Control Exploits
Numerous real-world examples highlight the devastating consequences of broken access control. One example involves a social media platform where attackers exploited a flaw in the access control system to access and modify user profiles, including private messages and personal information. Another case involved a banking application where a vulnerability allowed attackers to transfer funds from one account to another without proper authorization. These breaches not only compromised user data but also severely damaged the reputation and trust of the affected organizations. Imagine a scenario where an attacker gains access to an e-commerce site’s admin panel due to a lack of proper access control, allowing them to modify product prices, steal customer data, or even shut down the entire website.
Mitigation Strategies for Broken Access Control Vulnerabilities
Preventing broken access control requires a multi-layered approach that encompasses secure coding practices, robust authentication mechanisms, and regular security assessments.
- Principle of Least Privilege: Grant users only the minimum necessary access rights to perform their tasks.
- Input Validation and Sanitization: Always validate and sanitize all user inputs to prevent attackers from manipulating parameters to gain unauthorized access.
- Secure Authentication and Session Management: Implement strong authentication mechanisms, including multi-factor authentication, and secure session management techniques to prevent session hijacking.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify and address vulnerabilities in the application’s access control system.
- Secure API Design: Design and implement APIs with robust authentication and authorization mechanisms, including proper input validation and rate limiting.
- Role-Based Access Control (RBAC): Implement RBAC to manage user permissions based on their roles within the organization.
- Attribute-Based Access Control (ABAC): Consider using ABAC for more fine-grained control, especially in complex systems.
Comparison of Access Control Mechanisms
| Mechanism | Description | Advantages | Disadvantages |
|---|---|---|---|
| RBAC | Access based on roles and permissions assigned to those roles. | Simple to implement and manage, well-understood. | Can become complex with many roles and permissions. Less granular control than ABAC. |
| ABAC | Access based on attributes of users, resources, and environment. | Highly granular control, adaptable to changing environments. | More complex to implement and manage than RBAC. |
| MAC (Mandatory Access Control) | Access based on security labels assigned to users and resources. | Strong security, often used in high-security environments. | Can be rigid and difficult to manage. |
| DAC (Discretionary Access Control) | Access controlled by the owner of the resource. | Flexible, simple to implement. | Less secure, relies on the owner to manage access correctly. |
Cryptographic Failures
Cryptography is the bedrock of secure web applications, protecting sensitive data like passwords, credit card information, and user communications. However, improperly implemented or outdated cryptographic techniques can leave your application vulnerable to attacks, leading to data breaches and significant reputational damage. Understanding common cryptographic failures is crucial for building robust and secure web applications.
The implications of using weak or outdated cryptographic algorithms are severe. Weak algorithms can be easily cracked using readily available tools and techniques, allowing attackers to decrypt sensitive data or forge digital signatures. Outdated algorithms, even if once strong, may have known vulnerabilities discovered since their deployment. This exposes your application to attacks that could have been prevented by using modern, well-vetted cryptographic methods. The cost of a data breach, including legal fees, remediation efforts, and loss of customer trust, far outweighs the investment in strong cryptography.
Weak or Outdated Encryption Algorithms
Using weak or outdated encryption algorithms like DES or MD5 is a major security risk. DES, with its relatively short key length, is easily broken with modern computing power. MD5, while still used for some purposes like checksum verification, is demonstrably vulnerable to collision attacks, meaning attackers can create different inputs that produce the same MD5 hash. This can be exploited to forge digital signatures or manipulate data without detection. Modern standards like AES (Advanced Encryption Standard) with sufficiently long key lengths and SHA-256 (Secure Hash Algorithm 256-bit) or SHA-3 are far more secure and should be preferred. Choosing the appropriate algorithm depends on the sensitivity of the data and the security requirements of the application. The longer the key length, the more computationally expensive it is to crack, providing stronger security.
Improper Key Management
Secure key management is paramount. Compromised keys render even the strongest encryption useless. This involves securely generating, storing, and rotating keys. Keys should be generated using cryptographically secure random number generators (CSPRNGs), never hardcoded into the application. They should be stored using secure methods like hardware security modules (HSMs) or encrypted at rest with strong encryption. Regular key rotation ensures that even if a key is compromised, the damage is limited to a specific timeframe. Failure to properly manage keys dramatically increases the risk of a successful attack. Imagine a scenario where an attacker gains access to a database containing unencrypted API keys. The consequences could be catastrophic.
Insufficient Randomness
Cryptographic operations often rely on random number generators. If these generators are predictable or biased, it weakens the security of the entire system. Using a weak random number generator can lead to predictable keys, making it easier for attackers to decrypt data. This highlights the importance of using CSPRNGs, which produce statistically random numbers that are difficult to predict. A real-world example would be a poorly implemented lottery system where the random number generator is flawed, leading to predictable winning numbers and undermining fairness. In the context of cryptography, a similar flaw could allow attackers to predict encryption keys.
Failure to Validate Input
Failing to properly validate user inputs can lead to vulnerabilities like cryptographic padding oracles. These oracles allow attackers to extract information about the encrypted data, even without knowing the key, by observing the behavior of the application in response to different inputs. Robust input validation, including sanitization and length restrictions, is crucial to prevent such attacks. For example, if a web application accepts user-supplied data as part of an encryption process without validating its length or format, it might be susceptible to a padding oracle attack.
Lack of Proper Authentication and Authorization
Cryptographic mechanisms are often used in conjunction with authentication and authorization processes. However, if these processes are flawed, it can negate the security provided by the cryptography. For example, using weak passwords or failing to properly implement access control can allow attackers to bypass cryptographic protections and gain unauthorized access to sensitive data. This emphasizes the importance of a holistic security approach that considers all aspects of security, not just cryptography alone.
Injection
Injection flaws happen when an attacker can sneak malicious code into your application’s input. This code then gets executed by the application, giving the attacker unauthorized access or control. Think of it like slipping a hidden message into a letter – the recipient (your application) unknowingly executes the hidden instructions. The consequences can range from data breaches to complete system takeover.
Several types of injection attacks exist, each exploiting different vulnerabilities within applications. Understanding these variations is crucial for building robust defenses.
SQL Injection
SQL injection targets database interactions. Attackers craft malicious SQL code within input fields, altering the intended database query. For example, if a login form asks for a username and password, an attacker might input ' OR '1'='1 as the username. This would bypass authentication because the injected SQL statement SELECT * FROM users WHERE username = '' OR '1'='1' always evaluates to true. The attacker gains access without knowing the correct credentials. This kind of attack can lead to data exfiltration, modification, or deletion.
Cross-Site Scripting (XSS)
Cross-site scripting (XSS) attacks involve injecting malicious scripts into websites viewed by other users. These scripts run in the victim’s browser, allowing the attacker to steal cookies, session tokens, or other sensitive information. Imagine a forum where users can post comments. An attacker could inject a script into a comment that, when viewed by other users, steals their session cookies, granting the attacker access to their accounts. There are reflected XSS, stored XSS, and DOM based XSS, each with subtle but significant differences in how the attack is carried out.
Command Injection
Command injection allows attackers to execute arbitrary operating system commands on the server. This typically occurs when user-supplied data is directly used to construct commands without proper sanitization. For instance, if a web application allows users to specify a file path, an attacker might input ; rm -rf / as the path. This would execute a command to delete all files on the server, causing catastrophic data loss.
Secure Coding Practices to Prevent Injection Attacks
Preventing injection attacks requires a multi-layered approach, focusing on secure coding practices and input validation. Here’s a list of key strategies:
Implementing these practices is vital for building secure applications that can withstand injection attempts.
- Parameterize Queries: Use parameterized queries or prepared statements instead of directly embedding user input into SQL queries. This prevents the attacker’s input from being interpreted as SQL code.
- Input Validation and Sanitization: Strictly validate and sanitize all user inputs before using them in any application logic. This includes checking data types, lengths, and formats, and removing or escaping potentially harmful characters.
- Output Encoding: Encode data appropriately before displaying it to the user. This prevents XSS attacks by rendering potentially harmful script tags harmless.
- Least Privilege Principle: Grant applications only the necessary permissions to access resources. This limits the damage an attacker can do even if they successfully inject code.
- Regular Security Audits and Penetration Testing: Regularly audit your code and conduct penetration testing to identify and address vulnerabilities before attackers find them.
- Use a Web Application Firewall (WAF): A WAF can help filter malicious traffic and prevent injection attacks from reaching your application.
- Keep Software Updated: Regularly update your application and its dependencies to patch known vulnerabilities.
Insecure Design
Source: securitymagazine.com
Insecure design isn’t about a single coding error; it’s a fundamental flaw baked into the application’s architecture. It’s the blueprint that allows vulnerabilities to flourish, no matter how well-written the individual code snippets might be. Think of it as building a house with unlocked doors and windows – even the strongest locks on the inside won’t help. Addressing insecure design requires a shift in mindset, from patching vulnerabilities to preventing them from ever existing.
Insecure design manifests in various ways, from poorly implemented authentication mechanisms to insufficient input validation and lack of consideration for data protection. The consequences can be catastrophic, ranging from data breaches and financial losses to reputational damage and regulatory penalties. A secure design, on the other hand, proactively mitigates risks, leading to more robust and resilient applications. This requires a comprehensive approach that considers security from the very beginning of the development process, not as an afterthought.
Insufficient Input Validation
Insufficient input validation leaves applications vulnerable to a wide array of attacks, including injection flaws (already discussed), cross-site scripting (XSS), and buffer overflows. Failing to properly sanitize and validate user inputs allows attackers to manipulate the application’s behavior, potentially leading to unauthorized access, data modification, or denial-of-service attacks. For example, an application that doesn’t validate the length of a username field could be susceptible to buffer overflow attacks, where an attacker submits an excessively long string, causing the application to crash or expose sensitive information. Robust input validation involves checking data types, lengths, formats, and ranges, and escaping or encoding special characters before using the data in database queries or displaying it to users.
Improper Session Management
Session management is crucial for maintaining the security of user interactions. Weak session management practices, such as using predictable session IDs or failing to implement proper session timeouts, can allow attackers to hijack user sessions and gain unauthorized access to sensitive data. For instance, if an application uses easily guessable session IDs, an attacker could potentially guess a valid session ID and impersonate a legitimate user. Secure session management involves using strong, unpredictable session IDs, implementing appropriate session timeouts, and using HTTPS to protect session data in transit. Regularly rotating session keys is another important practice.
Lack of Authentication and Authorization
A web application should always correctly identify and authorize users. Insufficient authentication mechanisms, such as using weak passwords or relying on easily guessable credentials, can leave applications vulnerable to brute-force attacks and unauthorized access. Similarly, inadequate authorization controls can allow users to access resources they shouldn’t have access to. For example, an application that doesn’t properly restrict access to administrative functions could allow unauthorized users to modify system settings or access sensitive data. Implementing strong authentication and authorization mechanisms, including multi-factor authentication and role-based access control, is essential for protecting applications from unauthorized access.
Hardcoded Credentials
Hardcoding sensitive information, such as database credentials or API keys, directly into the application code is a major security risk. If an attacker gains access to the application code, they will also gain access to these credentials, potentially compromising the entire system. Instead of hardcoding credentials, applications should use secure configuration management techniques, such as storing credentials in encrypted configuration files or using environment variables. This ensures that credentials are not exposed in the application code itself. A best practice is to use dedicated secrets management tools to handle these sensitive pieces of information.
Insufficient Logging and Monitoring
Insufficient logging and monitoring can hinder the ability to detect and respond to security incidents. Without adequate logging, it can be difficult to identify the source of attacks, track attacker activity, or determine the extent of the damage. Real-time monitoring is crucial to detect and respond to attacks as they happen. Effective logging and monitoring involves capturing detailed information about user activity, system events, and security-related incidents. This information should be stored securely and analyzed regularly to identify potential threats. Using a Security Information and Event Management (SIEM) system can greatly enhance the effectiveness of logging and monitoring.
Security Misconfiguration

Source: com.np
Security misconfiguration is a pervasive problem, often stemming from a lack of understanding of default settings, incomplete implementation of security controls, or insufficient attention to detail during system setup and maintenance. It’s a top vulnerability because it provides attackers with readily exploitable entry points into systems and applications, often bypassing more sophisticated defenses. Leaving default credentials unchanged, exposing unnecessary services, and failing to properly configure access controls are all prime examples of this critical oversight.
Leaving default configurations unchanged is like leaving your front door unlocked – it’s an open invitation for trouble. Many applications and services come with default usernames and passwords, or overly permissive settings. Failing to change these before deploying the system creates a significant security risk, easily exploited by attackers using readily available tools and techniques. Similarly, exposing unnecessary services, such as debugging tools or administrative interfaces, provides attackers with additional avenues for compromise. These services, if left enabled and accessible from the internet, become direct entry points into your system.
Default Credentials and Unpatched Software
Default credentials, often found in web applications, databases, and network devices, provide attackers with immediate access without needing to crack passwords. For instance, a web server left with its default administrator password allows anyone to gain full control. Similarly, neglecting to patch known vulnerabilities allows attackers to exploit known weaknesses, often using publicly available exploit code. The consequences can range from data breaches to complete system compromise. Regular patching and the immediate change of default credentials are crucial preventative measures.
Improperly Configured Access Controls
Improperly configured access controls allow unauthorized users or processes to access sensitive data or functionalities. This can range from granting excessive privileges to specific user accounts to failing to properly restrict access to sensitive files or directories. For example, a misconfigured web application might allow anonymous users to access administrative functionalities, leading to complete system takeover. Another example involves databases where default access controls are not modified, allowing potentially anyone to read or even modify sensitive data.
Unnecessary Services and Exposed Information
Leaving unnecessary services running increases the attack surface of a system. Examples include remote administration tools, debugging interfaces, and outdated software. Each running service represents a potential point of entry for attackers. Similarly, exposing sensitive information, such as configuration files, database credentials, or internal network maps, can provide attackers with valuable intelligence to plan and execute more sophisticated attacks. Properly securing these assets requires careful consideration of what services are needed and strict access controls to sensitive information.
Importance of Regular Security Audits and Patching
Regular security audits and patching are critical for mitigating the risks associated with security misconfiguration. Security audits involve systematic checks to identify vulnerabilities and misconfigurations. This process can be manual or automated, employing vulnerability scanners and penetration testing tools. Patching involves updating software and systems with the latest security updates to address known vulnerabilities. A proactive approach to security auditing and patching is essential to maintain a secure system and prevent costly breaches. Ignoring these practices is akin to ignoring regular car maintenance—eventually, a significant problem will arise.
Vulnerable and Outdated Components
Using outdated software is like driving a car with bald tires – it might seem to work fine for a while, but the risk of a catastrophic failure is significantly higher. Outdated components, including libraries, frameworks, and even operating systems, represent a massive security vulnerability. These components often contain known security flaws that attackers actively exploit. Regular updates patch these vulnerabilities, minimizing the attack surface and improving the overall security posture of your application.
Outdated components introduce several risks. Exploitable vulnerabilities are the most immediate concern. These vulnerabilities can range from simple denial-of-service attacks to complete system compromises, leading to data breaches, financial losses, and reputational damage. Furthermore, outdated components may lack support for modern security protocols, leaving your application susceptible to attacks that exploit weaknesses in older technologies. Finally, maintaining compatibility with outdated components can become a significant burden, hindering development and increasing the complexity of your system.
Component Update Strategies
Managing component updates effectively requires a structured approach. A robust strategy ensures that updates are applied promptly without disrupting the application’s functionality. This involves several key steps. First, establish a clear update policy that Artikels the frequency of updates and the process for evaluating and deploying them. This policy should be documented and communicated to all developers. Second, utilize automated dependency management tools to track component versions and identify updates. These tools can automate the update process, reducing the manual effort required. Third, establish a thorough testing procedure to verify that updates don’t introduce new bugs or vulnerabilities. This can include unit testing, integration testing, and security testing. Finally, implement a rollback plan in case an update causes unexpected issues. This plan should allow for a quick and easy reversion to the previous stable version of the component.
Identification and Authentication Failures
In the digital realm, where sensitive data and critical systems reside, robust identification and authentication are the cornerstones of security. Failing to properly secure these processes leaves your systems vulnerable to a wide array of attacks, from simple account takeovers to full-blown data breaches. Think of it like this: your digital front door needs a strong lock and a reliable key system, not a flimsy latch and a spare key hidden under the welcome mat.
Proper identification and authentication mechanisms verify a user’s identity and ensure only authorized individuals can access specific resources. This is more than just a username and password; it’s about implementing a multi-layered defense that minimizes the risk of unauthorized access and maintains data integrity. A weak authentication system can be the weakest link in your overall security posture, creating a pathway for attackers to exploit and compromise your entire system.
Common Vulnerabilities in Authentication and Session Management
Weak or easily guessable passwords, coupled with insufficient password policies, remain a prevalent vulnerability. Users often reuse passwords across multiple platforms, creating a domino effect where a compromise on one site grants access to others. Furthermore, many systems fail to implement proper session management, leaving sessions open for extended periods or lacking mechanisms to detect and mitigate session hijacking attempts. This can allow attackers to steal or manipulate session tokens, gaining unauthorized access to a user’s account and associated data. Another common flaw is the lack of multi-factor authentication (MFA), which adds an extra layer of security beyond just a password.
Designing a Secure Authentication System with Multi-Factor Authentication
A secure authentication system should incorporate multiple layers of defense. Starting with strong password policies that enforce complexity, length, and regular changes is crucial. Password managers can assist users in creating and managing complex passwords securely. Beyond passwords, implementing multi-factor authentication (MFA) significantly enhances security. MFA typically involves combining something the user knows (password), something the user has (phone, security key), and something the user is (biometric data). For example, a user might need to enter a password, then verify a code sent to their registered mobile phone via SMS or a dedicated authentication app. This layered approach makes it exponentially more difficult for attackers to gain unauthorized access, even if they manage to compromise one factor. Regular security audits and penetration testing are essential to identify and address vulnerabilities in the authentication system before they can be exploited. Consider using strong password hashing algorithms (like bcrypt or Argon2) to protect against brute-force attacks, and always ensure your authentication system is kept up-to-date with the latest security patches.
Software and Data Integrity Failures
Software and data integrity failures represent a significant threat in today’s interconnected world. They occur when data is modified unexpectedly, either maliciously or accidentally, leading to inconsistencies and potentially severe security breaches. This compromises the trustworthiness of applications and the reliability of the information they process, impacting everything from financial transactions to critical infrastructure management. Understanding these vulnerabilities is crucial for building robust and secure systems.
Data integrity failures can lead to security breaches in several ways. Compromised data can be used to manipulate system behavior, grant unauthorized access, or even execute malicious code. For instance, an attacker might alter a database record containing a user’s authorization level, granting themselves elevated privileges. Similarly, modification of financial transaction data could result in fraudulent activities. The consequences can range from minor inconveniences to catastrophic losses depending on the context and the sensitivity of the compromised data.
Input Validation and Data Sanitization
Input validation and data sanitization are critical defenses against software and data integrity failures. Input validation ensures that data received from external sources conforms to predefined rules and expectations. This prevents unexpected or malicious data from entering the system. Data sanitization, on the other hand, involves cleaning or transforming data to remove potentially harmful elements before it’s stored or processed. This might include removing special characters, encoding HTML entities, or escaping SQL queries. These processes significantly reduce the risk of injection attacks and other integrity-related vulnerabilities.
Examples of Vulnerabilities
One common example is a SQL injection vulnerability where an attacker manipulates input fields to inject malicious SQL code into a database query. This can allow the attacker to read, modify, or delete data without authorization. Imagine a website with a search functionality that doesn’t properly sanitize user input. An attacker could craft a search query that includes SQL code, for example, `’ OR ‘1’=’1`, which would return all records in the database. Another example is a buffer overflow, where an application attempts to write more data to a buffer than it can hold. This can overwrite adjacent memory locations, leading to unexpected behavior or even crashes, potentially creating an opportunity for code injection. Finally, a failure to properly validate file uploads could allow attackers to upload malicious scripts disguised as legitimate files, leading to server compromise.
Server-Side Request Forgery (SSRF)
Server-Side Request Forgery (SSRF) is a web security vulnerability that allows an attacker to induce the server-side application to make HTTP requests to a URL controlled by the attacker. This seemingly innocuous capability can have devastating consequences, granting attackers access to internal systems, sensitive data, and even the ability to perform actions on behalf of the server. Essentially, the attacker leverages the server’s trust and network privileges to perform actions it wouldn’t otherwise be able to.
SSRF vulnerabilities arise from the server’s trust in user-supplied data when constructing outbound HTTP requests. Imagine a scenario where a website allows users to input a URL to fetch and display an image. If the application doesn’t properly validate or sanitize this user input, an attacker could potentially craft a URL pointing to an internal server, revealing sensitive information or even allowing for further exploitation. The impact of a successful SSRF attack can range from data breaches and internal network reconnaissance to complete server compromise.
Attack Vectors and Exploitation Techniques
Several common attack vectors exist for exploiting SSRF vulnerabilities. One frequent method involves manipulating parameters within a web application that process URLs. For instance, an application might allow users to specify a URL for an image or a file to be downloaded. If this input is not properly validated, an attacker can replace the legitimate URL with a malicious one targeting internal systems. Another vector is through the use of features like URL shortening services, where the application might not fully resolve the shortened URL, allowing an attacker to redirect the server to a hidden internal resource.
Attackers leverage these vulnerabilities to access internal resources, such as intranet sites, internal APIs, or cloud storage accounts. They can also use SSRF to conduct port scanning on the internal network, identifying open ports and services. A particularly dangerous technique is to use SSRF to access metadata servers, potentially revealing sensitive information about the application’s infrastructure. More sophisticated attacks could even involve using SSRF to exploit vulnerabilities in internal services, leading to a complete compromise of the server or the entire network.
Preventing SSRF Vulnerabilities
Preventing SSRF requires a multi-layered approach focused on robust input validation and restricted access to network resources. The most crucial step is to meticulously validate and sanitize all user-supplied data used to construct HTTP requests. This involves ensuring that URLs are properly formatted, checking for malicious schemes (like `file://` or `ftp://`), and restricting access to specific hostnames or IP addresses.
Another critical preventative measure is to leverage allowlists instead of blocklists when defining acceptable targets for HTTP requests. Allowlisting explicitly defines the permitted URLs or IP addresses, preventing requests to any other destinations. This is significantly more secure than attempting to block all potentially malicious URLs, which is inherently difficult and prone to errors. Furthermore, limiting the server’s network privileges can mitigate the impact of a successful SSRF attack, preventing access to sensitive resources even if an attacker manages to craft a malicious request. Regular security audits and penetration testing are essential to identify and address potential SSRF vulnerabilities before they can be exploited.
Final Thoughts

Source: cyberhoot.com
So, there you have it – a whirlwind tour of the OWASP NHI Top 10. While the list might seem daunting, remember that proactive security measures are key. By understanding these vulnerabilities and implementing the appropriate safeguards, you can significantly reduce your risk profile. Don’t just build; build securely. The future of your web app, and your users’ data, depends on it. Stay vigilant, stay updated, and stay secure.