Notepad input validation flaw? Sounds boring, right? Wrong. This seemingly innocuous text editor holds a surprisingly dark secret: it’s a potential gateway for hackers if not properly secured. Think of it as a digital backdoor, wide open for anyone to exploit. We’re diving deep into the vulnerabilities lurking within your simple notepad, exploring how seemingly harmless text can unleash a cascade of security nightmares.
From SQL injection attacks that could steal your data to buffer overflows that crash your entire system, the risks are real and far-reaching. We’ll break down the different types of vulnerabilities, show you how they’re exploited, and most importantly, how to protect yourself. Get ready to uncover the hidden dangers lurking in your everyday notepad.
Types of Notepad Input Validation Flaws
Source: snaporbital.com
Notepad, while seemingly simple, can surprisingly harbor security vulnerabilities if input validation is neglected. These vulnerabilities arise from the application’s failure to properly check and sanitize user-provided data before processing it. This oversight opens the door to various attacks, compromising system integrity and potentially exposing sensitive information. Let’s delve into the specifics.
Injection Vulnerabilities
While Notepad doesn’t directly interact with databases or web servers, the concept of injection vulnerabilities still applies. Imagine a scenario where a malicious user crafts a specially formatted text file containing commands that, when opened by Notepad, are interpreted as system commands instead of plain text. This could potentially lead to the execution of arbitrary code. While SQL injection and classic command injection are less relevant in a pure Notepad context, Cross-Site Scripting (XSS) is a possibility if the notepad file is later incorporated into a web application. For instance, if a user imports a malicious notepad file into a web application that doesn’t properly sanitize its inputs, the malicious script in the notepad file might execute within the web application’s context.
Buffer Overflow Vulnerabilities
Buffer overflow vulnerabilities occur when a program attempts to write data beyond the allocated memory buffer. In a Notepad context, this might happen if a user inputs an extremely long string of text. If Notepad doesn’t properly handle the length of the input string, it could overwrite adjacent memory regions, leading to unexpected behavior, crashes, or even arbitrary code execution. This is particularly relevant for older or less robust Notepad implementations. The consequences can range from application crashes to complete system compromise, depending on the extent of the memory corruption.
Lack of Input Sanitization, Notepad input validation flaw
The absence of input sanitization in Notepad means that any character a user inputs is accepted without any filtering or checking. This can lead to various issues. For example, if a user inputs special characters that are interpreted as control characters, they could potentially cause unexpected behavior or crashes within Notepad. Additionally, if Notepad later interacts with other systems or applications, unsanitized input could be a vector for attacks on those systems.
Examples of Vulnerable Notepad Inputs
| Vulnerable Input | Type of Flaw | Potential Consequences | Mitigation Strategies |
|---|---|---|---|
|
XSS (Cross-Site Scripting) | Malicious script execution in the web application. | Proper input sanitization in the web application handling the file. |
| A text file containing millions of characters. | Buffer Overflow | Notepad crash, system instability, or potential arbitrary code execution (depending on the system and Notepad version). | Input length validation and appropriate error handling. |
| A file containing control characters (e.g., null bytes) | Lack of Input Sanitization | Unexpected behavior, application crashes, or data corruption. | Input filtering to remove or escape potentially harmful characters. |
cmd /c calc.exe (if interpreted as a command) |
Command Injection (highly context-dependent) | Execution of arbitrary commands on the system. | Strict separation between data and code; avoid interpreting user input as commands. |
Exploiting Notepad Input Validation Flaws

Source: githubusercontent.com
Notepad, despite its seemingly simple nature, can become a vector for attacks if input validation is weak. Failing to properly sanitize user input allows attackers to exploit vulnerabilities, leading to potentially serious consequences ranging from system crashes to data breaches. This section explores various ways attackers can leverage these flaws.
Malicious Input Examples
A simple notepad application lacking robust input validation is vulnerable to various malicious inputs. For instance, an excessively long string could trigger a buffer overflow, causing the application to crash or execute arbitrary code. Another example involves injecting special characters like `` to exploit a cross-site scripting (XSS) vulnerability. Similarly, input containing operating system commands, if not properly filtered, could lead to command injection attacks. The severity depends on the application’s architecture and the operating system.
Exploiting a Buffer Overflow Vulnerability
Let’s imagine a simplified notepad application with a buffer of 100 characters. An attacker could craft a string significantly longer than 100 characters. This would overflow the buffer, overwriting adjacent memory locations. If the overwritten memory contains crucial program instructions, the application could crash. In a more sophisticated scenario, the attacker might carefully craft the input to overwrite the return address on the stack, redirecting execution to malicious code injected within the long string. This injected code could, for example, grant the attacker administrative privileges. The step-by-step process would involve: 1) Identifying the vulnerable application; 2) Crafting a long string exceeding the buffer size, possibly including shellcode; 3) Inputting the string into the application; 4) Observing the application’s behavior (crash or unexpected execution). The success of this attack depends on factors such as memory layout and system architecture.
Cross-OS Vulnerability Exploitation Differences
Exploiting vulnerabilities in notepad-like applications varies across operating systems. Windows, macOS, and Linux differ in their memory management, security mechanisms, and how they handle user input. On Windows, exploiting a buffer overflow might lead to a crash or the execution of arbitrary code, potentially resulting in privilege escalation. macOS and Linux, with their more robust security features, may offer more resistance. However, vulnerabilities can still exist. The success of an attack depends on factors like the specific application’s code, the operating system’s security settings, and the attacker’s skill. For instance, a buffer overflow on Linux might lead to a segmentation fault, whereas on Windows, it might allow arbitrary code execution due to differences in memory protection.
Cross-Site Scripting (XSS) Scenario
Imagine a notepad-like application with a feature allowing users to share notes online. If the application doesn’t sanitize user input before displaying it, an attacker could inject malicious JavaScript code. For example, an attacker might create a note containing ``. When a victim views this note, the malicious script executes in their browser, stealing their cookies which often contain sensitive session data. This data could then be used for identity theft or unauthorized access to the victim’s accounts. This scenario highlights the importance of proper input sanitization to prevent XSS attacks.
Potential Attack Vectors
Several attack vectors target notepad applications with weak input validation:
Buffer Overflow: Overwriting memory buffers with excessively long input, potentially leading to crashes or code execution.
Command Injection: Injecting operating system commands into the input, allowing the attacker to execute arbitrary commands on the system.
Cross-Site Scripting (XSS): Injecting malicious JavaScript code, allowing the attacker to steal user data or perform other malicious actions.
Denial of Service (DoS): Flooding the application with malicious input, causing it to crash or become unresponsive.
SQL Injection (if applicable): Injecting malicious SQL code if the application interacts with a database. This is less likely in a simple notepad but possible if the application has database integration.
Mitigating Notepad Input Validation Flaws
Notepad, despite its simplicity, isn’t immune to security vulnerabilities stemming from inadequate input validation. Failing to properly sanitize user input can expose the application to various attacks, from simple crashes to more serious exploits. Fortunately, implementing robust validation and sanitization techniques can significantly reduce these risks. This section explores practical methods to fortify notepad applications against input-related vulnerabilities.
Input Validation Techniques
Effective input validation is the first line of defense. This involves rigorously checking user-supplied data against predefined rules and formats before it’s processed by the application. This prevents unexpected or malicious data from causing problems. Key techniques include:
- Length Restrictions: Limiting the number of characters allowed prevents buffer overflows. For instance, a notepad application might limit each line to a maximum of 255 characters.
- Data Type Validation: Ensuring that input conforms to the expected data type (e.g., integer, string, date) prevents type-related errors and potential exploits. For example, rejecting non-numeric input when expecting a line number.
- Character Whitelisting: Allowing only specific characters (e.g., alphanumeric characters, punctuation) prevents injection attacks. This approach is more secure than blacklisting, which can be easily bypassed.
- Regular Expression Validation: Using regular expressions allows for complex pattern matching, ensuring input adheres to specific formats (e.g., email addresses, phone numbers). This provides a fine-grained level of control over input.
- Input Encoding: Encoding input using a standard like UTF-8 prevents encoding-related vulnerabilities and ensures consistent data handling across different systems.
Input Sanitization Methods
Sanitization complements validation by transforming potentially harmful input into a safe form. This involves removing or escaping characters that could be interpreted as commands or malicious code. For example:
- HTML Encoding: Converting special characters like `<`, `>`, and `&` into their HTML entity equivalents prevents cross-site scripting (XSS) attacks.
- SQL Escaping: Escaping special characters in SQL queries prevents SQL injection attacks. This involves replacing special characters with their escaped counterparts (e.g., single quotes are often escaped with a backslash).
- URL Encoding: Encoding URL parameters prevents URL manipulation attacks. This ensures that special characters in URLs are properly handled.
Secure Coding Practices to Prevent Buffer Overflows
Buffer overflows occur when a program attempts to write data beyond the allocated memory buffer. This can lead to program crashes or allow attackers to execute arbitrary code. Key practices to prevent buffer overflows include:
- Bounds Checking: Always check the size of the input before writing it to a buffer. Ensure that the input does not exceed the buffer’s capacity.
- Safe String Functions: Use string functions that automatically handle buffer size limitations (e.g., `strncpy` in C instead of `strcpy`).
- Input Size Validation: Validate the size of the input before processing it. Reject input that exceeds predefined size limits.
Examples of Robust Input Validation Functions
Implementing robust input validation requires careful consideration of the programming language and context. Here are examples of input validation functions in Python, C++, and Java:
- Python:
def validate_input(input_string, max_length=255):
if len(input_string) > max_length:
raise ValueError("Input string exceeds maximum length.")
sanitized_string = input_string.replace('<', '<').replace('>', '>') #Basic HTML sanitization
return sanitized_string
- C++:
#include
#includestd::string validate_input(const std::string& input_string, size_t max_length)
if (input_string.length() > max_length)
throw std::runtime_error("Input string exceeds maximum length.");std::string sanitized_string = input_string;
std::replace(sanitized_string.begin(), sanitized_string.end(), '<', '<'); std::replace(sanitized_string.begin(), sanitized_string.end(), '>', '>');
return sanitized_string; - Java:
public static String validateInput(String inputString, int maxLength)
if (inputString.length() > maxLength)
throw new IllegalArgumentException("Input string exceeds maximum length.");String sanitizedString = inputString.replace("<", "<").replace(">", ">");
return sanitizedString;
Parameterized Queries to Prevent SQL Injection
If a notepad application interacts with a database, parameterized queries are crucial for preventing SQL injection. Instead of directly embedding user input into SQL queries, parameterized queries treat user input as parameters, separating data from the query structure. This prevents attackers from injecting malicious SQL code. Most database libraries provide mechanisms for using parameterized queries. The specific syntax will vary depending on the database system and the programming language being used. For instance, in many systems, the query might look something like this:
SELECT * FROM notes WHERE user_id = ? AND note_text LIKE ?;
where the `?` placeholders are replaced with the user ID and note text, respectively, preventing the direct insertion of malicious code into the SQL statement.
Secure Design Principles for Notepad Applications: Notepad Input Validation Flaw
Building a seemingly simple application like Notepad requires careful consideration of security best practices. Ignoring these can lead to vulnerabilities that expose users to significant risks. A secure-by-design approach is crucial, focusing on preventing vulnerabilities rather than patching them later. This involves implementing robust security measures from the very beginning of the development process.
Least Privilege in Notepad Applications
The principle of least privilege dictates that a program should only have the minimum necessary permissions to perform its intended function. In the context of Notepad, this means restricting its access to system resources. For example, Notepad should not have write access to system directories or the ability to execute arbitrary code. Implementing this principle minimizes the potential damage caused by a security breach. If a malicious actor were to compromise a Notepad application with restricted privileges, the impact would be far less severe than if it had broader access. This approach dramatically reduces the attack surface.
Input Validation as a Layered Security Approach
Input validation acts as a crucial first line of defense against various attacks. It involves rigorously checking all user inputs – text, file paths, etc. – to ensure they conform to expected formats and values. This prevents malicious code injection, buffer overflows, and other common vulnerabilities. However, relying solely on input validation is insufficient. A layered security approach is essential, combining input validation with other techniques such as output encoding (to prevent cross-site scripting) and access control mechanisms to create a robust defense. Each layer adds another obstacle for attackers, making exploitation considerably harder. For instance, even if an attacker bypasses input validation, further layers will likely stop their malicious actions.
Security Considerations for File Handling and Data Persistence
Notepad applications often handle files, requiring careful consideration of security implications. Secure file handling involves verifying file paths to prevent directory traversal attacks, where an attacker manipulates file paths to access unauthorized files. Furthermore, data persistence, or how data is stored, should be secure. If Notepad stores user data, it should be encrypted both at rest and in transit to protect sensitive information from unauthorized access. Implementing proper access controls is vital, preventing unauthorized modification or deletion of files. Consideration should also be given to the secure handling of temporary files created by the application, ensuring their proper deletion after use.
Comparing Input Validation Approaches
Several approaches exist for input validation, each with trade-offs between effectiveness and performance. Whitelisting, which allows only explicitly permitted inputs, is highly effective but can be more complex to implement. Blacklisting, which blocks known harmful inputs, is simpler but susceptible to bypass if new attack vectors emerge. Regular expressions offer a flexible approach but require careful crafting to avoid vulnerabilities. The optimal approach depends on the specific requirements of the Notepad application and the risk tolerance. A robust strategy might combine multiple methods for a layered defense. For example, a whitelist could be used for critical inputs, while a blacklist could handle less critical ones.
Secure Coding Practices Checklist for Notepad Developers
Before releasing any Notepad application, developers should thoroughly review their code against a comprehensive checklist. This checklist should include:
- Perform rigorous input validation on all user inputs.
- Implement the principle of least privilege, restricting access to system resources.
- Use parameterized queries or prepared statements to prevent SQL injection if interacting with databases.
- Securely handle file paths to prevent directory traversal attacks.
- Encrypt sensitive data both at rest and in transit.
- Implement robust error handling to prevent information leakage.
- Regularly update dependencies and libraries to patch known vulnerabilities.
- Conduct thorough code reviews and security testing before release.
- Follow secure coding guidelines and best practices.
Case Studies of Notepad Vulnerabilities
Notepad, despite its seemingly simple nature, can become a vector for security vulnerabilities if not carefully designed and implemented. While publicly documented cases of widespread notepad-specific exploits are rare due to the application’s limited functionality, the principles of input validation flaws remain relevant. Let’s explore a hypothetical scenario to illustrate the potential risks.
Hypothetical Security Incident: Malicious File Execution via Notepad
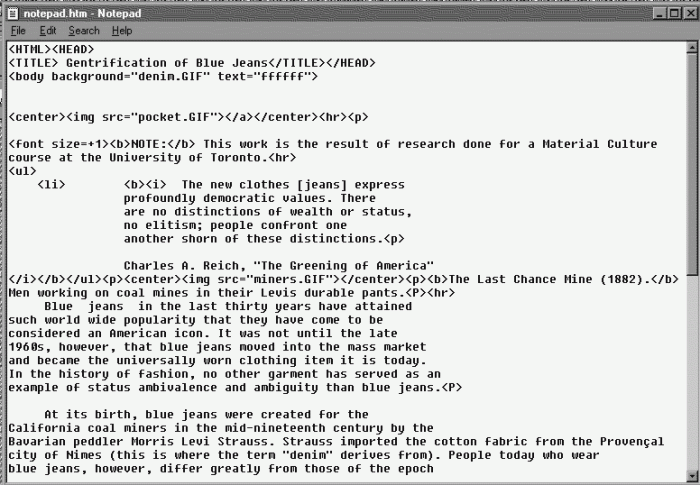
Imagine a scenario where a company uses a custom-built notepad application integrated into their internal system for taking notes on sensitive projects. This application, lacking robust input validation, allows users to open and save files with arbitrary file extensions. A malicious actor gains access to the network and crafts a specially designed file—appearing as a harmless “.txt” file—but actually containing malicious code disguised as plain text. This file, when opened within the custom notepad application, executes the embedded code due to the lack of proper file type validation and sanitization.
The vulnerability lies in the application’s failure to verify the actual content of the opened file. It merely checks the file extension, which is easily spoofed. The malicious code could range from simple data exfiltration to more sophisticated actions like installing malware or gaining unauthorized system access.
The impact on the system could be severe, potentially leading to data breaches, system compromise, and disruption of business operations. For users, the impact might include loss of sensitive information, exposure to malware, and compromised personal data. The damage extends beyond immediate financial losses; it includes reputational harm and the cost of remediation and recovery.
Remediation and Prevention
To remediate this vulnerability, the company immediately implemented several crucial changes. First, the custom notepad application underwent a complete security audit and code review to identify all potential input validation weaknesses. Second, the application was updated to perform rigorous file type validation, not only checking the file extension but also analyzing the file’s content using robust methods to detect malicious code. Third, the application was enhanced to restrict file saving to approved extensions and locations, minimizing the risk of malicious files being created or saved within the system. Finally, comprehensive employee training was conducted to educate users about the risks of opening unknown files and the importance of practicing safe computing habits. These combined measures significantly reduced the risk of future incidents.
Wrap-Up
Source: albany.edu
So, your trusty notepad – that seemingly harmless application – is actually a potential security minefield if left unchecked. Understanding the various input validation flaws, from simple injection attacks to complex buffer overflows, is crucial for safeguarding your data and system integrity. By implementing the mitigation strategies discussed, you can significantly reduce your risk and enjoy the convenience of your notepad without the constant worry of lurking threats. Remember, a little vigilance goes a long way in the world of cybersecurity.