New iot botnet launching large scale ddos attacks – New IoT botnet launching large-scale DDoS attacks—sounds like the plot of a tech thriller, right? Except this isn’t fiction. We’re diving deep into the murky world of interconnected devices, exploring how a newly emerged botnet is weaponizing them for massive distributed denial-of-service attacks. Get ready to uncover the architecture of this digital menace, the vulnerable devices it targets, and the chillingly effective methods it uses to cripple online services.
From understanding the attack vectors used to infect unsuspecting smart devices to dissecting the sophisticated evasion techniques employed by the botnet, we’ll unravel the layers of this cyber threat. We’ll also examine the devastating consequences of successful attacks, including financial losses, reputational damage, and the potential disruption of critical infrastructure. This isn’t just about numbers; it’s about the real-world impact on individuals, businesses, and even national security.
The Nature of the Botnet: New Iot Botnet Launching Large Scale Ddos Attacks
The rise of sophisticated IoT botnets capable of launching devastating DDoS attacks presents a significant cybersecurity challenge. These networks leverage the inherent vulnerabilities of numerous interconnected devices to create a powerful, distributed force capable of overwhelming online services. Understanding their architecture and attack mechanisms is crucial for effective mitigation strategies.
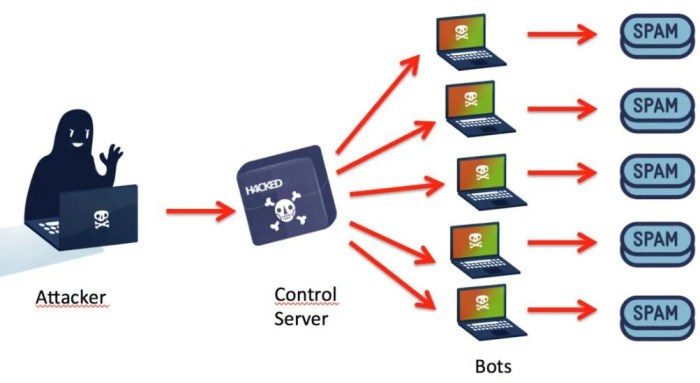
The architecture of a modern IoT botnet typically involves a command-and-control (C&C) server, numerous compromised IoT devices (the botnet’s “bots”), and a communication infrastructure to coordinate their actions. The C&C server directs the bots, assigning targets and attack instructions. This communication can utilize various protocols, often obfuscated to evade detection. The bots themselves are typically low-powered devices, making them easy targets and difficult to track individually. The sheer scale of the botnet, however, creates a formidable threat.
IoT Device Vulnerabilities, New iot botnet launching large scale ddos attacks
Several types of IoT devices are particularly vulnerable to compromise and recruitment into botnets. These devices often lack robust security features, such as strong authentication mechanisms and regular software updates. Examples include security cameras, smart TVs, routers, and other devices with default or easily guessable passwords. The simplicity of these devices, coupled with their widespread deployment, makes them ideal targets for attackers seeking to build a large-scale botnet. Their often-limited processing power also makes them difficult to secure effectively. The lack of regular updates means security vulnerabilities may remain unpatched for extended periods, allowing attackers easy access.
Command-and-Control Mechanisms
Botnets employ various command-and-control (C&C) mechanisms to maintain control over their constituent devices. These methods range from simple, centralized architectures where all bots communicate directly with a single C&C server, to more complex, decentralized models employing peer-to-peer (P2P) communication or bot herders. Centralized C&C offers simplicity but is vulnerable to takedowns; P2P networks offer greater resilience but are more complex to manage. The choice of C&C mechanism depends on the attacker’s resources and goals. For instance, a botnet using a Domain Generation Algorithm (DGA) to dynamically generate C&C server addresses makes it significantly harder to track and disrupt. The use of encryption further complicates the task of monitoring botnet activity and identifying the attacker.
Attack Vectors
The following table Artikels potential attack vectors used to infect IoT devices and incorporate them into botnets. The vulnerabilities exploited often stem from default or weak credentials, outdated firmware, and known security flaws.
| Attack Vector | Description | Vulnerable Devices | Mitigation |
|---|---|---|---|
| Brute-force attacks | Attempting numerous password combinations to gain access. | Devices with weak or default passwords. | Strong, unique passwords; multi-factor authentication. |
| Exploiting known vulnerabilities | Leveraging publicly known software flaws to gain unauthorized access. | Devices with outdated firmware or unpatched vulnerabilities. | Regular software updates; security patching. |
| Phishing | Tricking users into installing malware or revealing credentials. | All connected devices. | User education; robust email filtering. |
| Man-in-the-middle attacks | Intercepting communication between devices and servers to steal credentials or inject malware. | Devices using unsecured Wi-Fi networks. | Secure Wi-Fi networks; VPNs. |
Attack Methodology and Tactics
This newly launched IoT botnet leverages a multi-pronged approach to maximize its DDoS capabilities, relying on a combination of established and evolving techniques to overwhelm target systems and evade detection. The scale and sophistication of the operation suggest a well-resourced and organized threat actor.
The botnet’s attack methodology centers on saturating target servers with massive volumes of traffic, rendering them unavailable to legitimate users. This is achieved through a variety of techniques, each designed to exploit specific vulnerabilities and circumvent security measures.
DDoS Attack Vectors
The botnet likely employs a diverse range of DDoS attack vectors, exploiting the vulnerabilities inherent in many IoT devices. These include, but are not limited to, UDP floods, which overwhelm servers with unsolicited UDP packets; HTTP floods, which exhaust server resources by sending numerous HTTP requests; and SYN floods, which target the TCP handshake process to cripple network connectivity. The botnet’s operators likely select the most effective attack vector based on the target’s infrastructure and security posture. For example, a target known to be vulnerable to specific HTTP requests might be subjected to a tailored HTTP flood attack. Conversely, a target with robust HTTP defenses might be attacked using UDP floods, leveraging the simpler nature of UDP packets to bypass certain filters.
Evasion Techniques
To avoid detection and mitigation, the botnet likely employs several sophisticated evasion techniques. These include distributed attack vectors originating from numerous compromised IoT devices across diverse geographical locations, making tracing the source difficult. Furthermore, the botnet likely utilizes techniques such as packet fragmentation and spoofing to mask the origin of the attack traffic and overwhelm intrusion detection systems (IDS) and firewalls. The use of low-and-slow attacks, which gradually increase the attack traffic over time, helps to avoid immediate detection by exceeding the target’s capacity for sustained traffic volume. Additionally, the botnet might use encrypted communication channels to conceal its command-and-control infrastructure.
Attack Lifecycle
The attack lifecycle begins with the initial compromise of vulnerable IoT devices. This is often achieved through exploiting known vulnerabilities in firmware or default credentials. Once compromised, these devices are enrolled into the botnet and await instructions from the command-and-control (C&C) server. The C&C server then orchestrates the DDoS attack, assigning targets and attack vectors to individual bots based on their capabilities and the target’s vulnerabilities. The attack itself involves a coordinated flood of traffic towards the target, aiming to exhaust its resources and render it unresponsive. Finally, the botnet operators monitor the attack’s effectiveness and adjust their strategy as needed. The Mirai botnet, for instance, used similar tactics, compromising millions of IoT devices and launching massive DDoS attacks against various targets.
Attack Flowchart
A simplified representation of the attack lifecycle could be illustrated as follows:
[Imagine a flowchart here. The flowchart would visually depict the stages: 1. Initial Compromise (Vulnerable IoT Device); 2. Botnet Enrollment (C&C Communication); 3. Target Selection (C&C Server assigns targets); 4. DDoS Attack (Coordinated Traffic Flood); 5. Monitoring and Adjustment (C&C Server monitors and adjusts attack strategy). Arrows would connect these stages, showing the flow of the attack.] This visual representation clarifies the sequential nature of the attack, from the initial infection to the final stage of monitoring and adaptation. The Mirai botnet’s attack lifecycle closely resembles this model, demonstrating the effectiveness of this approach in launching large-scale DDoS attacks.
Impact and Consequences
Source: cdn-website.com
The launch of a large-scale IoT botnet capable of devastating DDoS attacks presents a significant threat to the global digital landscape. The potential consequences extend far beyond simple website outages, impacting critical infrastructure, financial stability, and public trust. The sheer scale of such an attack magnifies the risks exponentially, creating cascading failures and widespread disruption.
The potential targets are numerous and varied, representing a significant risk to modern society’s interconnectedness. The attack’s impact will ripple through various sectors, causing widespread disruption and significant financial losses.
Potential Targets of DDoS Attacks
This botnet’s potential targets encompass a broad spectrum of vital systems. Critical infrastructure, such as power grids, water treatment facilities, and transportation networks, are particularly vulnerable. A successful attack could cripple essential services, leading to widespread power outages, water shortages, or transportation gridlock. Financial institutions, including banks and payment processors, are also prime targets. A successful attack could disrupt financial transactions, leading to significant financial losses and potentially triggering wider economic instability. Furthermore, online services, including e-commerce platforms, social media networks, and gaming servers, would face significant service disruptions, affecting millions of users and causing considerable reputational damage to the affected companies. Think of the 2016 Dyn DDoS attack, which took down major websites like Twitter, Netflix, and Spotify – a smaller scale example of what this botnet could achieve.
Impact on Targeted Entities
The impacts on targeted entities are multifaceted and severe. Financial losses can be astronomical, resulting from lost revenue, business interruption, and the costs of remediation and recovery. Reputational damage is inevitable, eroding public trust and potentially driving customers away. Service disruptions can lead to lost productivity, compromised data security, and a general sense of instability. For example, a successful attack on a major bank could lead to days of service disruption, costing millions in lost transactions and damaging the bank’s reputation. The resulting loss of confidence could trigger a bank run, with far-reaching consequences.
Cascading Effects on Interconnected Systems
The interconnected nature of modern systems means that a successful attack on one entity can trigger a cascade of failures across multiple sectors. For instance, a DDoS attack on a power grid could lead to widespread outages, affecting hospitals, communication networks, and financial institutions, all reliant on a stable power supply. Similarly, a disruption to financial systems could have a domino effect on businesses and individuals, leading to economic instability and social unrest. The 2010 Stuxnet worm, though not strictly a DDoS attack, demonstrated how a sophisticated cyberattack targeting a single industrial system (Iran’s nuclear enrichment program) could have far-reaching geopolitical consequences.
Legal and Regulatory Consequences for Perpetrators
The legal and regulatory consequences for the perpetrators of such a large-scale attack are severe and multifaceted. Depending on the jurisdiction and the specific targets, perpetrators could face charges ranging from computer fraud and abuse to terrorism, espionage, and sabotage. Significant fines, lengthy prison sentences, and international cooperation to apprehend and prosecute the individuals or groups responsible are highly probable. The penalties reflect the gravity of the crime and the potential for widespread harm. International treaties and agreements, such as the Budapest Convention on Cybercrime, provide a framework for cross-border cooperation in investigating and prosecuting cybercrimes of this magnitude.
Mitigation and Defense Strategies

Source: whatismyipaddress.com
The recent surge in IoT botnet-driven DDoS attacks necessitates a proactive and multi-layered approach to security. Ignoring the vulnerabilities inherent in poorly secured IoT devices is no longer an option; the consequences are too severe. Effective mitigation requires a combination of robust device security, advanced detection systems, and strategically implemented DDoS mitigation techniques.
IoT device security forms the first line of defense. Weak security practices leave devices vulnerable to compromise, transforming them into unwitting participants in large-scale attacks. A comprehensive strategy must address several key areas.
Strong IoT Device Security Measures
Implementing strong security measures on IoT devices is paramount to preventing their exploitation in botnets. This involves several crucial steps. First, regularly updating firmware is essential to patch known vulnerabilities. Outdated firmware often contains exploitable weaknesses that attackers can easily leverage. Second, using strong, unique passwords for each device prevents attackers from gaining unauthorized access through brute-force attacks or credential stuffing. Third, network segmentation isolates IoT devices from critical systems, limiting the damage caused by a compromised device. If one device is compromised, the impact is contained rather than cascading through the entire network. Consider creating separate VLANs for IoT devices, separating them from business-critical systems and servers.
Detecting and Responding to Botnet Activity
Detecting botnet activity within an IoT network requires a multi-faceted approach leveraging network monitoring tools and security information and event management (SIEM) systems. These systems can analyze network traffic for suspicious patterns indicative of botnet command-and-control (C&C) communications, such as unusual amounts of data flowing to specific IP addresses or unusual communication patterns. Anomaly detection algorithms can identify deviations from normal network behavior, flagging potential botnet activity. Real-time monitoring is critical; the sooner an infection is detected, the faster mitigation efforts can begin. This includes analyzing logs from routers, firewalls, and intrusion detection systems for suspicious activities. Rapid response is key; infected devices should be isolated or removed from the network immediately to prevent further damage.
DDoS Mitigation Techniques
Several techniques exist for mitigating DDoS attacks, each with its strengths and weaknesses. Rate limiting restricts the number of requests from a single IP address or network, preventing a flood of traffic from overwhelming a server. Blackholing involves dropping all traffic from a known malicious IP address, effectively blocking the attacker. Scrubbing centers filter malicious traffic before it reaches the target server, offering a more sophisticated and scalable solution for large-scale attacks. Choosing the right technique depends on the scale and nature of the attack and the resources available. For example, a small-scale attack might be effectively mitigated with rate limiting, while a large-scale attack may require the use of a scrubbing center. A layered approach, combining multiple techniques, is often the most effective strategy.
Network Security Tools and Practices
Implementing robust network security tools and practices significantly improves resilience against DDoS attacks. Intrusion detection and prevention systems (IDPS) can monitor network traffic for malicious activity and automatically block or mitigate attacks. Firewalls filter traffic based on predefined rules, preventing unauthorized access and limiting the impact of attacks. Regular security audits and penetration testing identify vulnerabilities and weaknesses, allowing for proactive mitigation. Furthermore, employing a distributed denial-of-service (DDoS) protection service from a reputable provider offers an additional layer of defense, often providing advanced mitigation capabilities and expertise. This is especially crucial for organizations facing frequent or large-scale attacks. Investing in these tools and practices is a cost-effective way to reduce the risk and impact of DDoS attacks.
Attribution and Forensics
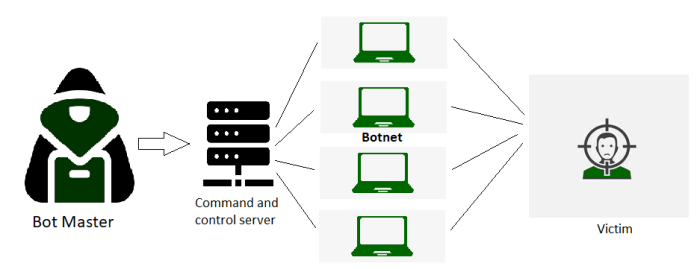
Source: geeksforgeeks.org
Pinpointing the source of a massive DDoS attack orchestrated by a sophisticated botnet is like finding a needle in a digital haystack – incredibly challenging, yet crucial for accountability and future prevention. The sheer scale of these attacks, often involving millions of compromised devices scattered across the globe, obscures the true perpetrators, creating a complex forensic puzzle. The anonymity offered by the internet, coupled with the use of advanced techniques to mask origins, makes attribution a difficult but essential task.
The challenges involved in tracing the origin of a large-scale DDoS attack stem from the decentralized and distributed nature of botnets. Attackers leverage numerous compromised devices (bots), making it difficult to identify the command-and-control (C&C) servers orchestrating the attacks. Furthermore, the use of proxies, VPNs, and other anonymization techniques further complicates the process of tracing the attack back to its origin. Finally, the ephemeral nature of botnet infrastructure, with C&C servers frequently changing IP addresses and locations, makes real-time tracking exceptionally difficult.
Digital Forensic Evidence in DDoS Attribution
Investigating a large-scale DDoS attack requires a multi-faceted approach to digital forensics. Investigators must gather and analyze various types of digital evidence to build a comprehensive picture of the attack and potentially identify the perpetrators. This includes network traffic analysis, examining logs from compromised devices and network infrastructure, malware analysis to understand the botnet’s structure and functionality, and investigation of financial transactions related to the botnet’s operation. Analyzing the attack’s characteristics, such as the attack vector, the type of DDoS attack used, and the specific targets, can also provide valuable clues.
Indicators of Compromise (IOCs) Associated with Botnet Activity
Identifying specific indicators of compromise is crucial in the investigation and mitigation of botnet-based DDoS attacks. These IOCs can help security professionals to identify compromised systems, track the spread of the malware, and ultimately attribute the attack to a specific actor or group.
A comprehensive list of potential IOCs includes:
- Suspicious network traffic patterns, such as unusual volumes of traffic originating from a specific IP address range or exhibiting characteristics consistent with DDoS attacks (e.g., SYN floods, UDP floods).
- Compromised systems exhibiting unusual activity, such as unexpected outbound connections or changes in system configurations.
- Malware signatures detected on compromised systems, indicating the presence of botnet malware.
- Domain names and IP addresses associated with command-and-control (C&C) servers used to manage the botnet.
- Financial transactions linked to the purchase or rental of botnet services or the payment of attackers.
- Specific malware variants used in the botnet, often identifiable through unique code signatures or behavioral patterns.
- Communication patterns between compromised systems and C&C servers, including specific protocols and port numbers used.
International Collaboration in Cyberattack Investigations
Effectively combating large-scale DDoS attacks necessitates robust international collaboration. These attacks often transcend national borders, requiring cooperation between law enforcement agencies, intelligence services, and cybersecurity companies across multiple jurisdictions. Sharing information about IOCs, malware samples, and investigative findings is essential for identifying and disrupting botnet operations and holding perpetrators accountable. The complexity and global reach of these attacks demand a coordinated international response, leveraging the expertise and resources of multiple countries. Examples of successful international collaborations in cybercrime investigations, though not necessarily specifically focused on DDoS, demonstrate the potential for effective action when nations work together. The sharing of intelligence and resources is critical to achieving success.
Ending Remarks
The emergence of this new IoT botnet capable of launching large-scale DDoS attacks highlights a critical vulnerability in our increasingly interconnected world. While the threat is significant, understanding the mechanics of these attacks—from infection vectors to mitigation strategies—is crucial. By proactively strengthening IoT device security and implementing robust DDoS mitigation techniques, we can collectively build a more resilient digital landscape and minimize the devastating consequences of these cyberattacks. The fight against this digital menace is ongoing, and awareness is our first line of defense.


