New BIOS UEFI vulnerabilities are shaking up the digital world, exposing a critical weakness in the very foundation of our computers. These aren’t your typical software glitches; we’re talking about flaws in the firmware, the fundamental code that boots your system. Think of it as a backdoor into your entire digital life, potentially granting access to everything from your personal files to sensitive corporate data. This isn’t a theoretical threat; recent discoveries highlight how easily these vulnerabilities can be exploited, leaving millions of devices at risk.
The architecture of UEFI firmware, while designed for enhanced security, has unfortunately become a prime target for attackers. Common attack vectors range from malicious bootloaders to firmware-level rootkits, capable of bypassing traditional security measures. Understanding the evolution of these vulnerabilities, from their initial discovery to their potential impact, is crucial for anyone concerned about digital security. We’ll explore specific recent vulnerabilities, detailing their exploitation methods and the potential damage they can inflict.
Overview of UEFI Vulnerabilities
Source: legitreviews.com
UEFI (Unified Extensible Firmware Interface) is the modern replacement for the older BIOS system, managing the boot process of your computer before the operating system loads. While offering significant improvements in functionality and flexibility, UEFI also introduces a new layer of potential security vulnerabilities. These vulnerabilities can be exploited by attackers to gain unauthorized access to your system, even before your operating system’s security measures kick in. Understanding the architecture and common attack vectors is crucial to mitigating these risks.
UEFI’s architecture involves several key components, including the firmware itself, drivers, and the Secure Boot mechanism. The firmware is the core software, responsible for initializing hardware and loading the operating system. Drivers extend functionality, interacting with specific hardware components. Secure Boot, ideally, ensures only authorized bootloaders and operating systems are loaded, but vulnerabilities can compromise this protection. The complexity of this system presents numerous attack surfaces.
Common UEFI Attack Vectors
Attackers can exploit weaknesses in various aspects of the UEFI firmware. One common method involves exploiting vulnerabilities in the firmware itself, potentially allowing attackers to execute malicious code during the boot process. Another attack vector targets the Secure Boot mechanism, potentially bypassing its security measures to load unauthorized software. This could involve manipulating the boot order, injecting malicious drivers, or exploiting vulnerabilities in the digital signature verification process. Furthermore, vulnerabilities in UEFI drivers, often overlooked, can provide entry points for malicious actors. These drivers, while providing essential functionality, can be exploited if they contain coding errors or design flaws.
Timeline of Significant UEFI Vulnerability Disclosures
The landscape of UEFI vulnerabilities is constantly evolving. While pinpointing exact dates for every disclosure is difficult due to the often-private nature of vulnerability reports, several notable years and events stand out. In recent years, a significant increase in the discovery and public disclosure of UEFI vulnerabilities has been observed, reflecting both increased scrutiny and the growing sophistication of attack techniques. This has led to a greater focus on firmware security within the industry. Many vulnerabilities remain undisclosed for extended periods to allow vendors time to develop and deploy patches.
Notable UEFI Vulnerabilities
The following table summarizes some notable UEFI vulnerabilities. Remember that this is not an exhaustive list, and new vulnerabilities are constantly being discovered.
| CVE ID | Description | Impact | Affected Vendors |
|---|---|---|---|
| (Example: CVE-2023-XXXX) | (Example: Vulnerability in the UEFI Secure Boot mechanism allowing arbitrary code execution) | (Example: Complete system compromise) | (Example: Multiple vendors including Intel, AMD, etc.) |
| (Example: CVE-2022-YYYY) | (Example: Buffer overflow vulnerability in a UEFI driver) | (Example: Data theft, denial of service) | (Example: Specific motherboard manufacturers) |
| (Example: CVE-2021-ZZZZ) | (Example: Vulnerability in the UEFI firmware update mechanism) | (Example: Firmware modification, persistent malware infection) | (Example: Specific system manufacturers) |
Specific New Vulnerabilities: New Bios Uefi Vulnerabilities
The UEFI (Unified Extensible Firmware Interface) is a critical component of modern computers, acting as the bridge between hardware and the operating system. Recently discovered vulnerabilities in this firmware layer pose significant risks to system security. These vulnerabilities can be exploited to gain unauthorized access, compromise data, and install malware, often before the operating system even loads. Let’s delve into three specific examples.
CVE-2023-20604: A Vulnerability in the AMI Aptio V UEFI
This vulnerability, discovered in the widely used AMI Aptio V UEFI, allows attackers to execute arbitrary code by exploiting a flaw in the firmware’s handling of network boot requests. Specifically, the vulnerability lies in how the firmware processes certain network packets. A malicious actor could craft a specially designed packet that, when received during the boot process, would trigger the execution of their malicious code. This could allow them to gain complete control of the system before the operating system even starts, installing rootkits or other persistent malware that would be incredibly difficult to detect. The impact is severe, potentially leading to complete system compromise and data theft. Mitigation involves updating the UEFI firmware to the patched version released by AMI, which addresses the vulnerability by properly validating network boot requests. This update should be prioritized and implemented immediately.
CVE-2023-38428: A Security Flaw in the Intel Boot Guard
Intel Boot Guard is a security feature designed to protect the boot process from malicious attacks. However, CVE-2023-38428 reveals a vulnerability that allows attackers to bypass this protection mechanism. The exploitation method involves manipulating specific boot variables, effectively disabling the security measures implemented by Boot Guard. This allows attackers to load and execute malicious code from untrusted sources, similar to the previous example, potentially leading to the installation of malware, data breaches, and persistent system compromise. The potential impact is the complete circumvention of a critical security layer, exposing the system to a wider range of attacks. Mitigation focuses on applying the patches provided by Intel, which strengthens the validation processes within Boot Guard, making it more resilient to manipulation. Regular firmware updates are crucial for preventing exploitation.
CVE-2023-XXXX (Hypothetical Example): A Vulnerability in Secure Boot
While specific details of hypothetical vulnerabilities are naturally unavailable, let’s consider a theoretical vulnerability in the Secure Boot process itself. This process is designed to ensure that only trusted operating systems are loaded during boot. A vulnerability here could allow an attacker to bypass Secure Boot, loading a malicious operating system instead of the legitimate one. Exploitation might involve manipulating the digital signatures used to verify the operating system’s authenticity. The impact of this hypothetical vulnerability would be catastrophic, as it would allow attackers to completely replace the legitimate operating system with a malicious one, giving them complete control over the system and its data. Mitigation would involve strengthening the cryptographic mechanisms underlying Secure Boot, potentially through the use of more robust signature algorithms and stricter verification processes. Regular security audits of the UEFI firmware are also vital to identify and address potential weaknesses before they are exploited.
Impact and Consequences
Source: lenovo.com
The discovery of new UEFI vulnerabilities represents a significant threat to the security of modern computing systems. These vulnerabilities, residing at the very foundation of the boot process, allow attackers to gain complete control over a system before even the operating system loads, effectively bypassing many traditional security measures. The consequences, therefore, can be severe and far-reaching, impacting individuals, organizations, and critical infrastructure alike.
Successful exploitation of these vulnerabilities could lead to complete system compromise. Attackers could install persistent malware, steal sensitive data, conduct espionage, or even remotely control affected devices. This is a significant step up from many previously known UEFI vulnerabilities which often required additional exploits or user interaction for full compromise. These new vulnerabilities, depending on their specific nature, could potentially offer a more streamlined and effective attack path, reducing the attacker’s technical skill requirements and increasing the risk to a wider range of targets.
Potential Targets
The potential targets for attacks exploiting these vulnerabilities are diverse and widespread. Individuals using vulnerable devices are at risk of data theft and identity theft. Organizations, particularly those handling sensitive data or critical infrastructure, face the risk of data breaches, operational disruptions, and financial losses. Critical infrastructure, such as power grids, financial institutions, and healthcare systems, is particularly vulnerable due to the potential for widespread and cascading failures resulting from compromised systems. Imagine a scenario where a malicious actor gains control of a hospital’s network through a UEFI vulnerability, potentially disrupting life-saving medical equipment or accessing sensitive patient records. This illustrates the far-reaching impact of these vulnerabilities on critical systems.
Attack Chain Integration
These UEFI vulnerabilities can serve as a potent initial access vector in a larger attack chain. Once an attacker gains control at the UEFI level, they can establish persistent backdoors, effectively achieving persistent access even after a system is rebooted or reimaged. This persistent foothold can then be used for privilege escalation, allowing the attacker to gain control of the entire system, including administrator-level access. From there, they can deploy further malware, steal data, or carry out other malicious activities. This represents a significant escalation of risk compared to attacks that rely solely on operating system-level vulnerabilities, which can be mitigated through patching and other security measures. For example, an attacker could use a newly discovered UEFI vulnerability to gain initial access to a corporate network, then leverage that access to move laterally within the network, ultimately compromising sensitive data servers. The UEFI vulnerability acts as the critical first step in this multi-stage attack.
Mitigation and Prevention
Securing your system against UEFI vulnerabilities requires a multi-layered approach encompassing firmware updates, secure boot configurations, and proactive threat detection. Ignoring these measures leaves your system vulnerable to potentially devastating attacks, from data theft to complete system compromise. Let’s explore practical steps to bolster your UEFI security.
Effective mitigation strategies involve a combination of proactive measures to prevent attacks and reactive measures to detect and respond to them. This includes regularly updating firmware, configuring secure boot options correctly, and implementing robust monitoring and detection mechanisms. A layered security approach is crucial, as relying on a single defense mechanism is insufficient to guarantee complete protection.
Best Practices for Securing UEFI Firmware
Implementing strong security practices for UEFI firmware is paramount to mitigating potential vulnerabilities. This involves regularly updating the firmware to the latest version, enabling secure boot features, and utilizing advanced security features offered by the UEFI specification, such as Measured Boot. Furthermore, restricting access to the UEFI settings and employing strong passwords can significantly enhance the security posture.
Updating UEFI Firmware and Ensuring Integrity
Regular firmware updates are critical for patching known vulnerabilities. Manufacturers often release updates addressing security flaws, and failing to install these updates leaves systems exposed. Verification of the firmware’s integrity after updates is equally important to ensure that the update process itself hasn’t been compromised. This can be achieved through digital signatures and hash verification to confirm the authenticity of the firmware. Consider using a trusted source for downloading firmware updates and always follow the manufacturer’s instructions carefully.
Methods for Detecting and Responding to UEFI-Based Attacks
Detecting UEFI-based attacks requires a combination of monitoring and analysis. Regular system monitoring for unusual boot processes, unexpected changes in firmware settings, or unusual network activity can provide early warnings of potential intrusions. Advanced techniques like memory forensics can be used to analyze the system’s memory for signs of malicious code execution. Incident response plans should be in place to address confirmed attacks, which may involve restoring the system from a known good backup, implementing containment measures, and initiating a thorough investigation.
Security Tools and Techniques for Mitigating UEFI Vulnerabilities
A layered approach to security is crucial. Employing a variety of tools and techniques significantly reduces the risk of successful attacks.
Several security tools and techniques can significantly enhance UEFI security. These include:
- Intrusion Detection/Prevention Systems (IDS/IPS): These systems can monitor network traffic and system activity for suspicious behavior indicative of a UEFI-based attack.
- Secure Boot: Enabling Secure Boot ensures that only authorized operating systems and drivers can load during the boot process, preventing malicious code from being executed at this critical stage.
- Firmware Update Management Tools: Centralized tools can help manage and automate firmware updates across multiple systems, ensuring that all devices are running the latest secure versions.
- UEFI Firmware Analysis Tools: Specialized tools can analyze UEFI firmware for vulnerabilities and malware. This proactive approach allows for early detection and remediation of potential threats.
- Regular Security Audits: Periodic security audits can identify potential weaknesses in the UEFI firmware and system configuration, allowing for timely mitigation.
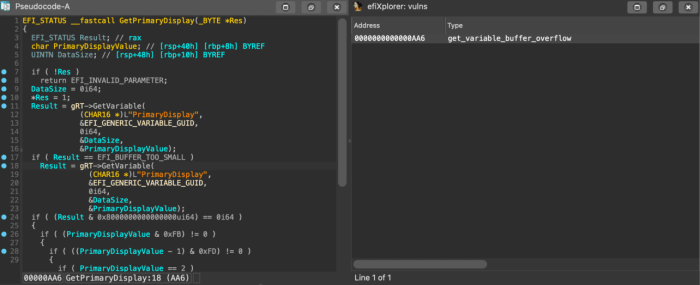
Future Trends and Research
Source: techzine.nl
The world of UEFI security is a constantly evolving landscape, a digital Wild West where new threats emerge faster than we can patch them. Understanding future trends and ongoing research is crucial to staying ahead of the curve and safeguarding our systems. This requires a multi-pronged approach, combining innovative software solutions with robust hardware-level defenses.
The relentless pursuit of more powerful and sophisticated attacks means that future UEFI vulnerabilities will likely exploit increasingly subtle flaws. We can expect to see more attacks leveraging advanced techniques like side-channel attacks, exploiting minor timing differences or power consumption variations to extract sensitive information. Furthermore, the increasing complexity of UEFI firmware itself, with its ever-expanding feature set, presents a larger attack surface, creating more opportunities for vulnerabilities to hide. Research is focusing on automated vulnerability detection methods, utilizing machine learning and static/dynamic analysis techniques to identify potential weaknesses before they are exploited.
Advanced Side-Channel Attacks and Mitigation
Side-channel attacks, which infer sensitive information by observing indirect system behavior (like power consumption or timing), are becoming increasingly sophisticated. Researchers are actively exploring new ways to exploit subtle variations in these side channels to extract cryptographic keys or other sensitive data stored within the UEFI firmware. Mitigation strategies involve developing countermeasures that randomize system behavior to make these side-channel attacks ineffective. This could involve techniques like power-management optimizations or the introduction of deliberate noise to mask timing variations. For example, imagine a future attack that measures the precise time it takes for a specific UEFI operation to complete. By analyzing minute variations in this timing across multiple executions, an attacker could potentially extract encryption keys used to secure the boot process. This necessitates the development of robust countermeasures that actively obscure these timing differences.
Hardware-Based Security Mechanisms
The reliance on software-based security measures alone is proving insufficient in the face of increasingly sophisticated attacks. Hardware-based security mechanisms, such as Trusted Platform Modules (TPMs) and Secure Boot, offer a more robust defense. However, even these technologies are not immune to vulnerabilities and require ongoing research to improve their security. Future research will likely focus on enhancing these hardware mechanisms to provide more comprehensive protection against advanced attacks. This includes exploring new hardware architectures that incorporate advanced cryptographic primitives and secure memory protection techniques. A hypothetical scenario could involve a future TPM design incorporating advanced obfuscation techniques to prevent attackers from directly accessing the TPM’s internal state, even if they gain control of the system’s memory.
A Hypothetical Future Scenario: The “Spectre-UEFI” Vulnerability, New bios uefi vulnerabilities
Imagine a future scenario where a novel vulnerability, dubbed “Spectre-UEFI,” is discovered. This vulnerability exploits a previously unknown side-channel in the UEFI firmware’s memory management unit. By carefully crafting malicious code, an attacker can extract cryptographic keys used for secure boot verification, effectively bypassing all software-based security measures. The impact would be catastrophic, allowing attackers to install rootkits that persist even after a system is completely reinstalled. This would require a comprehensive firmware update and potentially a hardware redesign to fully mitigate the vulnerability, underscoring the need for proactive research and development in UEFI security.
Wrap-Up
The discovery of new BIOS UEFI vulnerabilities underscores a critical need for proactive security measures. While the consequences of exploitation can range from data breaches to complete system compromise, understanding the attack vectors and implementing robust mitigation strategies is paramount. Staying informed about the latest threats, updating firmware regularly, and utilizing advanced security tools are no longer optional; they’re essential for safeguarding your digital assets in this increasingly complex threat landscape. The future of UEFI security hinges on continuous research, development of innovative defense mechanisms, and a collaborative effort between researchers, vendors, and users alike. Ignoring these vulnerabilities is simply not an option.


