National Cyber Incident Response Plan: Forget Hollywood hacking – this is the real deal. We’re talking about the intricate strategies and procedures nations employ to combat cyberattacks, from identifying threats to restoring systems and learning from the fallout. It’s a high-stakes game of digital defense, and understanding the plan is crucial for anyone concerned about online security, from governments to everyday users.
This plan isn’t just some dusty document gathering virtual cobwebs; it’s a dynamic, ever-evolving blueprint for navigating the complex landscape of cyber warfare and everyday digital threats. It covers everything from detecting and containing breaches to recovering lost data and fostering international cooperation. Think of it as the ultimate playbook for keeping nations safe in the digital age.
Definition and Scope of a National Cyber Incident Response Plan
A National Cyber Incident Response Plan (NCIRP) is essentially a nation’s playbook for dealing with large-scale cyberattacks and digital disruptions. It Artikels the strategies, procedures, and responsibilities for identifying, containing, eradicating, and recovering from significant cyber incidents that threaten national security, critical infrastructure, or the digital well-being of its citizens. Think of it as a comprehensive emergency plan, but specifically for the digital realm. Its effectiveness hinges on clear communication, coordinated action, and a well-defined chain of command.
A robust NCIRP possesses several core components. These include a clearly defined incident classification system to prioritize responses, pre-established communication protocols to ensure timely information sharing among stakeholders, a detailed incident handling process with clear roles and responsibilities, a robust system for identifying and analyzing threats, and a comprehensive recovery plan to restore normalcy after an incident. The plan also needs to address legal and ethical considerations, data privacy concerns, and public communication strategies during and after a cyber incident. Regular testing and updates are crucial to maintain its effectiveness in the ever-evolving cyber landscape.
Types of Cyber Incidents Covered
A national plan must be broad enough to encompass a wide range of cyber threats. This includes large-scale distributed denial-of-service (DDoS) attacks that cripple essential online services, sophisticated malware campaigns targeting critical infrastructure like power grids or financial institutions, data breaches exposing sensitive personal or national security information, advanced persistent threats (APTs) involving state-sponsored actors, supply chain attacks compromising software or hardware, and ransomware attacks demanding payment to unlock critical systems. The plan should also account for less dramatic but equally disruptive incidents, such as phishing campaigns targeting government employees or widespread misinformation campaigns designed to undermine public trust.
Key Stakeholders Involved
Effective implementation of a NCIRP requires collaboration across multiple sectors and agencies. Key stakeholders typically include government agencies responsible for cybersecurity (like a national cybersecurity agency), law enforcement agencies for investigating cybercrimes, critical infrastructure operators (such as power companies, banks, and telecommunications providers), the private sector (including technology companies and cybersecurity firms), and international partners for coordinating responses to transnational cyber threats. Academic institutions and cybersecurity experts often play a crucial advisory role, providing technical expertise and research insights. Effective communication and information sharing between these stakeholders are vital for a coordinated and efficient response.
Comparative Analysis of National Cyber Incident Response Plans
The approach to NCIRPs varies significantly across nations, reflecting differing geopolitical priorities, technological capabilities, and legal frameworks.
| Country | Focus | Key Agencies Involved | Key Strengths/Weaknesses |
|---|---|---|---|
| United States | Multi-agency coordination, public-private partnerships, emphasis on critical infrastructure protection. | CISA, FBI, DHS, NSA | Strong public-private partnerships, extensive resources; complexity can lead to coordination challenges. |
| United Kingdom | Strong emphasis on national security, proactive threat intelligence, close collaboration with industry. | NCSC (National Cyber Security Centre) | Centralized approach facilitates coordination; reliance on industry collaboration may leave smaller businesses vulnerable. |
| Israel | Focus on proactive defense, robust national cybersecurity infrastructure, close ties between military and civilian sectors. | Multiple agencies, including military and intelligence services. | Strong national defense capabilities; potentially less emphasis on public-private partnerships. |
Incident Detection and Reporting Mechanisms
A robust national cyber incident response plan hinges on the ability to swiftly detect and report cyberattacks. Early warning systems and efficient reporting mechanisms are crucial for minimizing damage and ensuring a coordinated national response. This section details the key components of a national-level incident detection and reporting framework.
Early warning systems rely on a multi-layered approach, combining technological solutions with human intelligence. These systems must be capable of detecting a wide range of threats, from sophisticated, targeted attacks to large-scale distributed denial-of-service (DDoS) events. Real-time monitoring of network traffic, analysis of security logs, and the use of threat intelligence feeds are essential components of effective early warning.
National-Level Cyber Incident Detection Methods
Effective national-level cyber incident detection leverages a combination of technologies and strategies. This includes the deployment of intrusion detection systems (IDS) and intrusion prevention systems (IPS) across critical infrastructure networks. These systems continuously monitor network traffic for suspicious activity, generating alerts that can be analyzed by security analysts. Furthermore, security information and event management (SIEM) systems aggregate and correlate security logs from various sources, providing a comprehensive view of security events across the national landscape. Finally, threat intelligence sharing platforms allow for the rapid dissemination of information about emerging threats and vulnerabilities, enabling proactive defense measures. The efficacy of these methods relies on continuous monitoring, timely updates, and skilled personnel to interpret the data.
Best Practices for National Cyber Incident Reporting
A streamlined and efficient reporting process is paramount. This requires clearly defined roles and responsibilities, established communication channels, and standardized reporting procedures. The reporting system should be accessible, user-friendly, and ensure confidentiality and data protection. A crucial element is the establishment of a centralized national cyber incident response team (CIRT) or equivalent body responsible for coordinating incident response efforts. This team would act as the primary point of contact for incident reporting, ensuring a unified response across various sectors. Furthermore, regular training and exercises are necessary to ensure that all stakeholders are familiar with reporting procedures and their roles in the response process.
Hypothetical Incident Reporting Workflow
Let’s consider a hypothetical scenario: a large-scale DDoS attack targeting a national banking system. The workflow would proceed as follows:
1. Detection: Network monitoring tools detect an unusually high volume of traffic targeting the banking system’s infrastructure. IDS/IPS systems flag the anomalous activity.
2. Initial Assessment: Security analysts assess the nature and severity of the attack, confirming it as a DDoS event.
3. Reporting: The incident is reported to the designated national CIRT via a secure communication channel (e.g., dedicated hotline or encrypted email). The report includes details of the attack, affected systems, and initial impact assessment.
4. Escalation: The CIRT assesses the national impact of the incident and determines the necessary response level. This may involve coordination with other government agencies, law enforcement, and private sector partners.
5. Investigation: A joint investigation is launched to determine the source of the attack and the extent of the damage.
6. Containment: Measures are implemented to mitigate the impact of the attack and prevent further damage.
7. Recovery: Systems are restored to normal operation, and lessons learned are documented for future improvements.
8. Post-Incident Analysis: A comprehensive post-incident analysis is conducted to identify vulnerabilities, improve security measures, and refine incident response procedures.
Importance of Timely and Accurate Incident Reporting
Timely and accurate incident reporting is critical for minimizing the damage caused by cyberattacks. Delays in reporting can allow attackers to escalate their actions, causing greater financial and reputational damage. Inaccurate reporting can lead to ineffective response efforts, wasting valuable time and resources. Consider the 2017 NotPetya ransomware attack, which spread globally, causing billions of dollars in damages. Faster reporting and coordination could have potentially mitigated some of the widespread impact. Accurate information is essential for effective resource allocation and coordination among various stakeholders, ensuring a swift and effective response.
Containment and Eradication Strategies
National-level cyber incidents demand swift and decisive action. Containment and eradication are critical phases, aiming to limit the damage and completely remove malicious actors and their effects from affected systems. Success hinges on a well-defined strategy, leveraging a range of techniques and a clear understanding of the threat landscape.
Effective containment and eradication strategies are built on a foundation of thorough incident investigation and analysis. Understanding the nature of the attack, the affected systems, and the attacker’s tactics is paramount before initiating any response. This allows for a targeted approach, maximizing efficiency and minimizing disruption. A reactive, blanket approach can often be more harmful than the initial breach.
Common Containment and Eradication Techniques
Several key techniques are commonly employed to contain and eradicate cyber threats at the national level. These range from isolating infected systems through network segmentation to deploying advanced malware removal tools and forensic analysis to identify and remove persistent threats. The choice of technique depends heavily on the specific nature of the incident and the criticality of the affected systems. For example, a ransomware attack on a critical infrastructure system would require a different approach than a phishing campaign targeting individual users. Techniques such as network segmentation, disconnecting infected systems, patching vulnerabilities, and employing endpoint detection and response (EDR) solutions are often deployed in conjunction. The use of specialized tools and techniques for malware analysis and removal is crucial in achieving complete eradication.
Comparison of System and Data Isolation Approaches
Isolating compromised systems and data is crucial to preventing further damage. Several approaches exist, each with its strengths and weaknesses. Disconnecting the infected system from the network is a straightforward, immediate action, but may not fully prevent data exfiltration if the attacker has already established persistence. More sophisticated techniques include virtual machine snapshots, allowing for rollback to a clean state before the attack, or using network segmentation to isolate the affected area from the rest of the network. The choice depends on the specific context, considering factors such as the criticality of the system, the nature of the threat, and the resources available. In some cases, a combination of approaches may be necessary for complete isolation. For example, a critical server might be isolated from the network and then a snapshot of the virtual machine hosting it is taken as a secondary measure.
Step-by-Step Procedure for Isolating an Infected Network Segment
The process of isolating an infected network segment is a critical step in containing a cyber incident. A swift and organized approach is essential to minimize the impact. The following steps Artikel a typical procedure:
- Identify the affected network segment: This involves analyzing network traffic, security logs, and intrusion detection system alerts to pinpoint the compromised area.
- Assess the criticality of the segment: Determine the impact of isolating the segment on critical services and operations.
- Develop an isolation plan: Artikel the specific steps required to isolate the segment, including disabling network connections, routing changes, and firewall rules.
- Implement the isolation plan: Execute the plan, ensuring that all necessary steps are completed correctly and thoroughly.
- Verify isolation: Confirm that the affected segment is completely isolated from the rest of the network.
- Document the process: Record all actions taken, including timestamps and justifications for each step.
Stages of the Containment Process
The containment process can be organized into distinct stages for a more efficient and effective response. Each stage builds upon the previous one, leading to a comprehensive and layered defense.
- Initial Response: Immediate actions to contain the spread of the incident, such as disconnecting infected systems or implementing network segmentation.
- Investigation and Analysis: Thorough investigation to determine the scope and nature of the incident, identify the root cause, and gather evidence.
- Eradication: Removal of malware, compromised accounts, and other malicious artifacts from affected systems.
- Recovery: Restoration of systems and data to a functional state, including data recovery and system rebuilds.
- Post-Incident Activity: Review of the incident response process, identification of vulnerabilities, and implementation of preventative measures to avoid future incidents.
Recovery and Mitigation Procedures
Okay, so the bad guys have been dealt with, the immediate threat is neutralized. Now comes the hard part: putting everything back together. This isn’t just about rebooting servers; it’s about restoring trust, minimizing business disruption, and learning from the experience to prevent future incidents. Think of it like this: you’ve just survived a major house fire – putting out the flames is one thing, rebuilding your life is a whole other ball game. A robust recovery plan is crucial for a swift and effective return to normal operations.
The process of restoring systems and data after a major cyber incident involves a systematic approach, moving from the immediate stabilization of the affected systems to the full restoration of functionality and data integrity. This is where meticulous planning pays off. It’s not just about technical fixes; it also includes restoring confidence among stakeholders, including employees, customers, and partners. The speed and efficiency of this recovery directly impacts the organization’s reputation and its ability to continue operating effectively.
Data Backup and Disaster Recovery Strategies
Data backups are your safety net. They’re the insurance policy you hope you never need to use, but are incredibly grateful to have when disaster strikes. A comprehensive backup strategy involves regular backups of critical data, stored both on-site and off-site (consider cloud storage for redundancy). Different types of backups exist – full, incremental, differential – each with its pros and cons in terms of storage space and recovery time. Disaster recovery planning, on the other hand, goes beyond just data backups. It encompasses a comprehensive plan that Artikels the procedures for restoring business operations in the event of a major disruption, including cyberattacks. This involves identifying critical systems and data, establishing recovery time objectives (RTOs) and recovery point objectives (RPOs), and testing the plan regularly to ensure its effectiveness. Think of it as a detailed blueprint for rebuilding after a significant event. For example, a financial institution might have an RTO of 4 hours and an RPO of 24 hours for its core banking system, ensuring minimal disruption to customer service.
System Restoration and Data Recovery Procedures
This stage involves the actual process of bringing systems back online and restoring data from backups. This needs to be a carefully orchestrated process, following a prioritized approach based on the criticality of systems. This isn’t a “one size fits all” approach. Consider a phased restoration, starting with essential services and gradually bringing other systems back online as they’re verified to be secure. Regular security scans and vulnerability assessments are crucial throughout this phase to ensure that no lingering malware or vulnerabilities remain. Imagine a hospital needing to prioritize patient care systems over administrative functions during recovery.
Recovery Plan Timeline, National cyber incident response plan
The importance of a well-defined timeline cannot be overstated. It provides a roadmap for coordinated action and helps ensure accountability.
- Day 1-3: Initial Assessment & Emergency Response. Responsibility: Incident Response Team
- Day 4-7: System Stabilization & Data Recovery. Responsibility: IT Department, Security Team
- Day 8-14: Full System Restoration & Verification. Responsibility: IT Department, Security Team, Business Units
- Day 15-30: Post-Incident Analysis & Reporting. Responsibility: Incident Response Team, Management
- Ongoing: Security Enhancements & Plan Updates. Responsibility: Security Team, IT Department
This timeline, of course, is a flexible framework. The actual duration of each phase will depend on the scale and complexity of the cyber incident. However, a structured timeline ensures that everyone knows their roles and responsibilities, fostering efficient collaboration and reducing the overall recovery time.
Post-Incident Activity and Lessons Learned
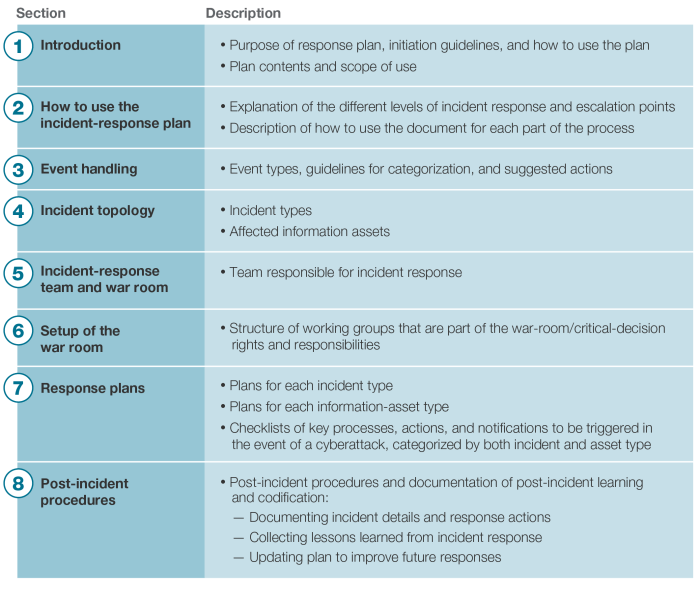
Source: alistechnology.com
A thorough post-incident analysis is the cornerstone of continuous improvement in cybersecurity. It’s not just about cleaning up the mess; it’s about understanding *why* the incident happened, how it was handled, and what can be done to prevent similar incidents in the future. This proactive approach transforms reactive responses into strategic defenses, significantly bolstering national cybersecurity resilience.
Post-incident reviews offer invaluable insights into vulnerabilities, weaknesses in response protocols, and areas needing improvement in incident detection and prevention mechanisms. These reviews are not merely exercises in blame-fixing; instead, they’re crucial opportunities for organizational learning and growth, ensuring the nation’s cyber defenses are constantly evolving and adapting to the ever-changing threat landscape. The goal is to transform past mistakes into future strengths.
Methods for Conducting Thorough Post-Incident Reviews
Effective post-incident reviews require a structured approach. A multi-disciplinary team, comprising technical experts, legal counsel, and representatives from affected departments, should be assembled. This team needs to objectively analyze the timeline of events, identify the root cause of the incident, and evaluate the effectiveness of the response strategy. This might involve analyzing logs, network traffic, and security tools’ performance. Techniques like threat modeling, vulnerability assessments, and tabletop exercises can also be employed to simulate scenarios and identify potential weaknesses before they are exploited. Formal interviews with individuals involved in the incident can provide critical qualitative data, providing crucial context beyond technical logs. The use of specialized software for log analysis and security information and event management (SIEM) systems can aid in this process, providing automated analysis of large datasets. For example, analyzing firewall logs might reveal weaknesses in access control policies that allowed attackers to gain a foothold.
Documenting and Disseminating Lessons Learned
Documenting lessons learned ensures that the knowledge gained from an incident isn’t lost. This documentation serves as a valuable resource for future incident response teams and contributes to the overall improvement of national cybersecurity preparedness. A centralized repository, accessible to relevant personnel, is essential for effective knowledge sharing. This could involve regular reports, updated standard operating procedures (SOPs), or even a dedicated knowledge base. Regular training exercises, incorporating the lessons learned from past incidents, should be implemented to reinforce best practices and ensure that personnel are prepared for future challenges. Sharing these lessons learned across different government agencies and private sector organizations through collaborative platforms and information-sharing initiatives can help to foster a national culture of continuous improvement in cybersecurity.
Structured Format for Documenting Lessons Learned
A standardized format for documenting lessons learned ensures consistency and facilitates easy retrieval of information. The following format is suggested:
| Section | Content |
|---|---|
| Incident Details | Date, time, type of incident, affected systems, initial impact, initial assessment of damage. |
| Response Actions | Timeline of actions taken, individuals involved, technologies used, effectiveness of each action, challenges encountered, successes and failures. |
| Recommendations for Improvement | Specific, actionable recommendations for improving incident detection, response, and prevention strategies. This includes improvements to technology, processes, and training. For example, “Implement multi-factor authentication on all critical systems,” or “Develop a more comprehensive incident response plan for ransomware attacks.” |
This structured approach ensures that critical information is readily available and allows for consistent analysis across multiple incidents. The use of such a format allows for easier identification of recurring issues and patterns, enabling the development of more effective preventative measures. For example, repeated failures in a particular security control might highlight the need for investment in improved technology or training.
International Cooperation and Information Sharing
In today’s hyper-connected world, massive cyberattacks often transcend national borders, demanding a collaborative global response. International cooperation in cybersecurity isn’t just a good idea; it’s a necessity for effectively mitigating risks and protecting critical infrastructure. A robust, internationally coordinated approach is crucial for sharing threat intelligence, coordinating responses, and building collective resilience against sophisticated cyber threats.
International collaboration significantly enhances the effectiveness of national cyber incident response plans. By pooling resources and expertise, nations can leverage a wider range of capabilities to address complex cyberattacks that might overwhelm individual countries. This shared intelligence helps identify attack vectors, anticipate future threats, and develop more effective defensive strategies. Furthermore, coordinated action can deter malicious actors and disrupt their operations more effectively than unilateral efforts.
Successful International Information-Sharing Initiatives
Several successful initiatives highlight the power of international collaboration in cybersecurity. The First Responders Group (FRG), a forum bringing together cybersecurity experts from various countries, exemplifies this. The FRG facilitates the rapid exchange of information about emerging threats, enabling quicker responses and more effective mitigation strategies. Another example is the Computer Emergency Response Team (CERT) coordination, where national CERTs collaborate to share threat intelligence and coordinate responses to large-scale cyber incidents, often involving cross-border attacks. These collaborative efforts demonstrate the tangible benefits of international cooperation, leading to faster incident resolution and reduced overall damage.
Challenges of International Cooperation in Cyber Incident Response
Despite the clear benefits, international cooperation in cyber incident response faces significant challenges. Differing legal frameworks and data privacy regulations can hinder the seamless exchange of sensitive information between nations. Varying levels of cybersecurity capabilities and expertise among countries also pose a challenge, creating disparities in response effectiveness. Furthermore, political tensions and mistrust between nations can impede information sharing and coordinated action, even when facing a common cyber threat. Building trust and establishing clear protocols for information sharing are paramount to overcoming these obstacles.
Framework for Facilitating Secure Information Sharing
A framework for secure international information sharing should prioritize trust-building measures, establishing clear legal and ethical guidelines, and employing robust technical security mechanisms. This framework should incorporate a tiered system for information sharing, allowing for different levels of access based on the sensitivity of the data and the level of trust established between nations. It should also include mechanisms for verifying the authenticity and integrity of shared information, ensuring its confidentiality, and establishing clear accountability for its use. Regular exercises and joint training programs are crucial for building interoperability and fostering trust among participating nations. A robust framework must also incorporate mechanisms for dispute resolution and conflict management to address potential disagreements or misunderstandings during a crisis. This framework should leverage existing international agreements and organizations, building upon existing structures to avoid duplication and ensure efficiency.
Public Communication and Awareness

Source: register.bank
In the high-stakes world of national cybersecurity, effective communication isn’t just a good idea—it’s a critical lifeline. During a major cyber incident, public trust and confidence can be as vulnerable as our digital infrastructure. Clear, consistent, and timely communication is the key to mitigating panic, preventing further damage, and ensuring a swift and coordinated recovery. A well-defined communication strategy is paramount to a successful national cyber incident response.
Public communication during a national cyber incident requires a multifaceted approach, encompassing transparency, accuracy, and empathy. The goal is not only to inform the public about the incident but also to build confidence in the government’s ability to handle the situation and reassure citizens that their safety and security are being prioritized. This involves careful consideration of the target audience, the medium of communication, and the message itself. Failing to effectively manage public perception can amplify the impact of the incident, leading to widespread panic, economic instability, and even social unrest.
Best Practices for Public Communication During Cyber Crises
Effective communication during a cyber crisis hinges on several key best practices. First, establish a central communication hub to ensure consistent messaging across all channels. Second, identify key spokespeople who are knowledgeable, credible, and capable of delivering complex information in a clear and concise manner. Third, utilize a multi-channel approach, leveraging traditional media outlets (press releases, TV appearances), social media platforms, and government websites to reach a broad audience. Finally, proactively address misinformation and rumors by providing timely updates and corrections. This proactive approach helps maintain public trust and prevents the spread of inaccurate or harmful information.
Key Messages for Public Communication
The key messages disseminated during a cyber incident should be simple, consistent, and reassuring. They should clearly explain the nature of the incident, the steps being taken to address it, and the potential impact on citizens. Crucially, they should also provide practical advice on how individuals and organizations can protect themselves. Examples of key messages include: confirmation of the incident, assessment of the impact, actions being taken to mitigate the threat, advice for individuals and businesses, and updates on the progress of the response effort. Maintaining a consistent tone and message across all communication channels is vital to avoid confusion and maintain public confidence.
Sample Press Release Templates
The following templates offer a framework for crafting press releases for different types of cyber incidents. Remember to adapt these templates to reflect the specific details of each incident.
Template 1: Data Breach Incident
FOR IMMEDIATE RELEASE
[Date]
[Organization Name] Announces Data Breach and Steps to Mitigate Impact
[City, State] – [Organization Name] today announced a data breach affecting [number] individuals. The breach involved [type of data compromised]. We are working with law enforcement and cybersecurity experts to investigate the incident and take appropriate steps to mitigate the impact. Affected individuals will be notified directly. We sincerely apologize for any inconvenience this may cause. For more information, please visit [website address].
Template 2: Ransomware Attack
FOR IMMEDIATE RELEASE
[Date]
[Organization Name] Undergoes Ransomware Attack; Operations Partially Disrupted
[City, State] – [Organization Name] is currently experiencing a ransomware attack that has temporarily disrupted some of our operations. We are working diligently to restore our systems and ensure the safety of our data. We are cooperating fully with law enforcement and cybersecurity experts to investigate the incident. We will provide updates as they become available. For inquiries, please contact [contact information].
Template 3: Phishing Campaign
FOR IMMEDIATE RELEASE
[Date]
[Organization Name] Warns Public of Widespread Phishing Campaign
[City, State] – [Organization Name] is warning the public of a widespread phishing campaign targeting [target group]. The phishing emails appear to be from [source] and attempt to [goal of phishing campaign]. Do not click on links or open attachments from unknown sources. For more information on how to identify and avoid phishing scams, please visit [website address].
Legal and Regulatory Frameworks

Source: miloriano.com
Navigating the digital landscape requires a strong understanding of the legal terrain. National cyber incident response plans must be built on a solid foundation of relevant laws and regulations to ensure actions are both effective and legally sound. Ignoring legal implications can lead to costly mistakes and hinder effective response efforts.
The legal implications of cyber incident response actions are multifaceted. Actions taken during a response, such as seizing data, accessing private systems, or even disclosing sensitive information, must adhere strictly to existing laws. Failure to do so can expose organizations and individuals to legal challenges, including lawsuits and criminal prosecution. This section will delve into the legal frameworks governing cyber incidents, highlighting key considerations and comparing approaches across different nations.
Relevant Laws and Regulations
National laws governing cybersecurity vary significantly. Many countries have enacted specific legislation addressing cybercrime, data protection, and critical infrastructure protection. These laws often define prohibited activities, establish reporting requirements, and Artikel the powers of law enforcement and government agencies in responding to cyber incidents. For instance, the Computer Fraud and Abuse Act (CFAA) in the United States, the Data Protection Act in the United Kingdom, and the General Data Protection Regulation (GDPR) in the European Union all play crucial roles in shaping national cyber incident response strategies. These laws often intersect, requiring careful consideration of multiple legal frameworks in complex incidents.
Legal Implications of Response Actions
The legal implications of various response actions must be carefully weighed. For example, seizing a compromised server might be necessary to prevent further damage, but it could also raise concerns about violating privacy rights or due process. Similarly, disclosing sensitive information to the public might be crucial for mitigating risks, but it could also lead to legal repercussions under data protection laws. A thorough understanding of relevant legal frameworks is crucial for balancing the need for effective response with the need to adhere to legal obligations. This often involves consulting with legal counsel to ensure compliance.
Comparison of Legal Frameworks: United States vs. European Union
The legal frameworks of the United States and the European Union offer a stark contrast in their approach to cyber incident response. The US system, largely based on common law, tends to be more reactive and emphasizes individual responsibility. The EU, with its emphasis on data protection and privacy under the GDPR, adopts a more proactive and regulatory approach. The GDPR, for example, mandates specific data breach notification procedures and imposes significant fines for non-compliance. The US approach often relies on voluntary cooperation and industry self-regulation, though recent legislation shows a shift towards a more prescriptive approach. This difference highlights the complexities of international cooperation in cyber incident response, where legal frameworks and enforcement mechanisms vary considerably.
Key Legal Considerations
| Legal Area | Relevant Laws/Regulations (Examples) | Potential Legal Implications of Response Actions | International Cooperation Challenges |
|---|---|---|---|
| Data Protection | GDPR (EU), CCPA (California), PIPEDA (Canada) | Unauthorized access, disclosure, or processing of personal data | Differing data protection standards and enforcement mechanisms |
| Cybercrime | CFAA (US), Computer Misuse Act (UK) | Unauthorized access, data theft, malicious code distribution | Jurisdictional issues, extradition treaties, and differing definitions of cybercrime |
| Critical Infrastructure Protection | Various sector-specific regulations (e.g., energy, finance) | Disruption of essential services, compromising national security | Harmonizing national security interests and differing regulatory approaches |
| Evidence Collection and Admissibility | Rules of evidence in respective jurisdictions | Improperly obtained evidence can be inadmissible in court | Ensuring cross-border admissibility of digital evidence |
Outcome Summary: National Cyber Incident Response Plan
In a world increasingly reliant on interconnected systems, a robust National Cyber Incident Response Plan is no longer a luxury—it’s a necessity. From the intricate mechanisms for detecting and containing cyberattacks to the crucial post-incident analysis and international collaboration, the plan’s effectiveness hinges on proactive measures, rapid response, and continuous improvement. Understanding its components empowers individuals, organizations, and nations to better prepare for, respond to, and ultimately mitigate the risks inherent in the digital realm. The future of cybersecurity depends on it.


