Mitre launches d3fend 1 0 – MITRE Launches D3FEND 1.0—and the cybersecurity world just got a whole lot more interesting. Forget everything you thought you knew about threat detection; this isn’t your grandpappy’s framework. D3FEND 1.0 promises a revolutionary approach, packing a punch of innovative features designed to help organizations fight back against increasingly sophisticated cyberattacks. Get ready to dive into a deep-dive of this game-changing technology.
This new framework boasts a redesigned architecture, enhanced functionalities, and a laser focus on practical application. We’ll unpack the key components, explore its real-world use cases across various industries, and even peek into the future of D3FEND. Think of it as your cheat sheet to mastering the art of modern threat detection.
MITRE D3FEND 1.0 Overview
MITRE’s D3FEND 1.0 is a significant leap forward in cybersecurity framework development, offering a comprehensive and structured approach to defending against advanced persistent threats (APTs). It moves beyond simple detection and response, focusing on a proactive and adaptable defense strategy. This framework isn’t just another checklist; it’s a dynamic tool designed to evolve with the ever-changing threat landscape.
D3FEND 1.0 provides a detailed model for building and maintaining robust cybersecurity defenses. It’s built upon a foundation of threat intelligence, incorporating various techniques and technologies to identify, analyze, and neutralize threats effectively. Think of it as a sophisticated blueprint for building a resilient cybersecurity fortress, tailored to the specific needs of an organization.
Key Features and Functionalities of D3FEND 1.0
The framework’s core strength lies in its structured approach. It provides a clear methodology for organizations to map their existing security controls against the MITRE ATT&CK framework, allowing for a comprehensive assessment of their current posture. This enables organizations to identify gaps in their defenses and prioritize improvements. Furthermore, D3FEND 1.0 offers guidance on implementing and managing various security technologies, providing a practical roadmap for enhancing their overall security. This includes strategies for threat hunting, incident response, and proactive threat mitigation. The framework also emphasizes the importance of collaboration and information sharing, recognizing that a robust defense requires a collective effort.
Target Audience for D3FEND 1.0
D3FEND 1.0 is designed for a broad audience within the cybersecurity field. This includes security professionals, incident responders, threat hunters, and security architects. Essentially, anyone involved in designing, implementing, or managing an organization’s cybersecurity defenses can benefit from this framework. From large enterprises to smaller organizations, the adaptable nature of D3FEND 1.0 makes it relevant across a wide spectrum of users. Its detailed approach is particularly beneficial for organizations seeking to improve their ability to defend against sophisticated attacks.
Comparison with Previous Versions (if applicable)
While specific details on previous versions might require access to MITRE’s internal documentation, we can illustrate a potential comparison structure. Assuming there were prior versions focusing on different aspects of threat detection or response, the following table would demonstrate the improvements introduced in D3FEND 1.0. Remember, this is a hypothetical example to illustrate the table structure; actual comparisons would need to be verified against official MITRE information.
| Version | Feature | Improvement | Notes |
|---|---|---|---|
| D3FEND 0.9 | Threat Detection | Enhanced automation and integration with threat intelligence feeds | Improved accuracy and reduced false positives |
| D3FEND 0.9 | Incident Response | Streamlined incident response processes | Faster containment and recovery times |
| D3FEND 1.0 | Proactive Threat Hunting | New module dedicated to proactive threat hunting techniques | More efficient threat identification before exploitation |
| D3FEND 1.0 | MITRE ATT&CK Alignment | Full integration with the MITRE ATT&CK framework | Improved mapping of security controls and better gap analysis |
D3FEND 1.0 Architecture and Components
D3FEND 1.0 isn’t your grandpappy’s cybersecurity framework. It’s a modular, adaptable system designed to ingest, process, and analyze massive amounts of security data, providing a comprehensive view of your network’s health. Think of it as a highly sophisticated, always-on detective, constantly monitoring for suspicious activity. Its architecture is key to its effectiveness.
The underlying architecture of D3FEND 1.0 is built around a flexible, component-based design. This allows for easy customization and scalability, adapting to the specific needs of different organizations. The system is designed to be extensible, allowing for the integration of new data sources and analytical capabilities as needed. Data flows seamlessly between components, enabling rapid threat detection and response. Imagine it as a well-oiled machine, where each part plays a crucial role in the overall function.
Core Components and Their Interactions, Mitre launches d3fend 1 0
D3FEND 1.0 comprises several key components that work together to provide a holistic security posture. These components include data ingestion modules, data processing engines, analytical modules, and visualization dashboards. The interaction between these components is crucial for effective threat detection and response. Data ingested from various sources flows through the processing engines, which then feed the analytical modules. Finally, the results are presented on user-friendly dashboards.
Data Flow within the Framework
The data flow within D3FEND 1.0 follows a logical progression. First, data is ingested from various sources, such as security information and event management (SIEM) systems, network devices, and endpoint sensors. This raw data is then pre-processed and normalized by the data processing engines. Next, the processed data is fed into analytical modules, which apply various algorithms and techniques to identify potential threats. Finally, the results of the analysis are presented on dashboards, providing users with a clear and concise view of their security posture.
System Architecture Diagram
Imagine a layered architecture. At the bottom, we have the Data Ingestion Layer, responsible for collecting data from various sources (SIEMs, firewalls, endpoint detection and response systems, etc.). This layer acts as the intake valve, funneling raw security information into the system. Above that is the Data Processing Layer, where the raw data undergoes cleaning, transformation, and normalization. Think of this as a refinery, preparing the data for analysis. The next layer, the Analytics Layer, is where the magic happens. This layer uses various machine learning algorithms and threat intelligence to identify anomalies and potential threats. Finally, at the top, the Visualization Layer presents the findings in a user-friendly dashboard, allowing security analysts to quickly assess the situation and respond accordingly. The entire system operates in a continuous loop, constantly monitoring, analyzing, and providing insights. The interaction between layers is facilitated by a robust communication infrastructure ensuring seamless data flow and coordination.
Use Cases and Applications of D3FEND 1.0
D3FEND 1.0, MITRE’s open-source threat detection framework, offers a powerful toolkit for enhancing cybersecurity across various sectors. Its modular design and adaptable architecture allow organizations to tailor its capabilities to their specific needs and threat landscapes. This adaptability makes it a valuable asset for organizations of all sizes, from small businesses to large enterprises. Let’s explore some practical applications.
Financial Services Threat Detection
The financial services industry faces constant pressure from sophisticated cyberattacks targeting sensitive customer data and financial transactions. D3FEND 1.0 can be instrumental in bolstering defenses. For instance, it can be configured to detect anomalies in transaction patterns, flagging potentially fraudulent activities. The framework’s ability to integrate with existing security information and event management (SIEM) systems allows for a comprehensive view of security events, improving response times and minimizing financial losses. Imagine D3FEND 1.0 identifying unusual login attempts from geographically disparate locations, triggering an alert and preventing unauthorized access to crucial systems.
Healthcare Data Breach Prevention
The healthcare industry handles extremely sensitive patient data, making it a prime target for cybercriminals. D3FEND 1.0’s capabilities in detecting data exfiltration attempts are particularly valuable in this sector. By monitoring network traffic for suspicious patterns and unusual data transfers, the framework can help prevent breaches and protect patient privacy. Consider a scenario where D3FEND 1.0 detects unauthorized access attempts to patient databases, alerting security personnel to investigate and mitigate the threat before sensitive data is compromised.
Critical Infrastructure Protection
Protecting critical infrastructure, such as power grids and water treatment facilities, is paramount for national security and public safety. D3FEND 1.0 can be leveraged to monitor these systems for intrusions and malicious activities. Its ability to analyze network traffic and system logs allows for early detection of anomalies that might indicate a cyberattack. A real-world example could involve D3FEND 1.0 detecting unusual command and control traffic targeting a power grid’s control systems, providing valuable time for intervention and preventing a widespread outage.
Government Agency Cybersecurity Enhancement
Government agencies handle vast amounts of sensitive information, making them prime targets for state-sponsored attacks and espionage. D3FEND 1.0 provides a robust framework for enhancing cybersecurity posture, helping to detect and respond to advanced persistent threats (APTs). By integrating with existing security tools and leveraging its advanced analytics capabilities, government agencies can gain a deeper understanding of their threat landscape and proactively defend against sophisticated attacks. For example, D3FEND 1.0 could detect unusual access patterns to classified databases, enabling a swift investigation and containment of potential breaches.
Implementation and Deployment of D3FEND 1.0: Mitre Launches D3fend 1 0
Deploying D3FEND 1.0 isn’t a simple plug-and-play operation; it requires careful planning and execution. Think of it like building a high-performance engine – you need the right parts, the right tools, and a skilled mechanic to get it running smoothly. This section details the process, highlighting key considerations and potential roadblocks.
Successfully implementing D3FEND 1.0 hinges on a thorough understanding of your existing infrastructure and security posture. A phased approach, starting with a pilot program in a controlled environment, is highly recommended before a full-scale rollout. This minimizes disruption and allows for iterative improvements based on real-world feedback.
Necessary Infrastructure and Resources
The infrastructure requirements for D3FEND 1.0 depend on the scale of your deployment and the complexity of your environment. Generally, you’ll need sufficient compute resources (servers, virtual machines, or cloud instances) to handle the workload, along with robust network connectivity to ensure efficient data flow. Storage capacity is also crucial, especially if you plan to retain extensive log data for analysis. Furthermore, skilled personnel with expertise in cybersecurity, system administration, and data analysis are essential for successful implementation and ongoing maintenance. Consider the need for dedicated security information and event management (SIEM) systems to integrate with D3FEND 1.0 for enhanced threat detection and response capabilities. For example, a large enterprise might require a cluster of high-powered servers, while a smaller organization might be able to leverage cloud-based resources.
Step-by-Step Deployment Guide (Hypothetical Environment)
Let’s imagine deploying D3FEND 1.0 in a mid-sized financial institution.
- Phase 1: Assessment and Planning: This involves a thorough assessment of the existing IT infrastructure, security policies, and threat landscape. This phase identifies potential integration points and areas requiring adjustments or upgrades. For example, they might need to upgrade their SIEM system to handle the increased volume of data from D3FEND 1.0.
- Phase 2: Pilot Deployment: A limited deployment in a non-production environment (e.g., a test network segment) allows for testing and refinement of the configuration and integration with existing systems. This minimizes risk and allows for identification and resolution of any unforeseen issues before a full rollout.
- Phase 3: Full Deployment and Integration: Once the pilot is successful, D3FEND 1.0 is deployed across the entire network. This includes configuring the system to integrate with various security tools and data sources, ensuring seamless data flow and consistent monitoring.
- Phase 4: Ongoing Monitoring and Maintenance: Continuous monitoring is crucial to identify and address potential issues, ensure optimal performance, and adapt to evolving threats. Regular updates and patches are necessary to maintain the security and functionality of the system.
Potential Challenges and Solutions
Deploying any complex security framework presents challenges. One common hurdle is integrating D3FEND 1.0 with existing security tools and systems. This might require custom scripting or API integrations, potentially demanding significant development effort. Another challenge could be the sheer volume of data generated by D3FEND 1.0, requiring sufficient storage and processing power. Data privacy and compliance regulations also need careful consideration. Solutions include careful planning, phased deployment, robust testing, and collaboration with experienced cybersecurity professionals. For example, a staged rollout allows for incremental increases in data volume, minimizing the risk of overwhelming the system. Addressing compliance requirements might involve anonymizing sensitive data or implementing strict access control measures.
Security and Privacy Considerations with D3FEND 1.0
D3FEND 1.0, while a powerful tool for enhancing cybersecurity, isn’t a magic bullet. Like any sophisticated system, it introduces its own set of security and privacy concerns that need careful consideration during implementation and ongoing operation. Understanding these potential risks and proactively mitigating them is crucial for ensuring the framework delivers on its promise of improved defense capabilities without compromising sensitive information.
The inherent complexity of D3FEND 1.0, with its numerous interconnected components and data flows, presents a larger attack surface than simpler systems. This increased complexity increases the potential for vulnerabilities to exist, some perhaps undiscovered initially. Furthermore, the very nature of the framework, designed to analyze and respond to security threats, means it handles sensitive data—network traffic, system logs, and potentially personally identifiable information (PII)—making data breaches a serious concern.
Potential Security Risks Associated with D3FEND 1.0
The potential for unauthorized access to D3FEND 1.0’s components and the data it processes is a significant concern. This could stem from vulnerabilities in the framework itself, insecure configurations, or malicious actors exploiting weaknesses in the underlying infrastructure. For example, a successful compromise of the central management console could grant attackers complete control over the entire system, allowing them to manipulate alerts, disable defenses, or exfiltrate sensitive data. Another potential risk lies in the integration of D3FEND 1.0 with existing security tools and systems. If these integrations aren’t properly secured, they could create new attack vectors, allowing attackers to move laterally within the network.
Privacy Implications of D3FEND 1.0
D3FEND 1.0’s functionality necessitates the collection and analysis of network traffic and system logs. This data may contain sensitive information, including PII, which raises significant privacy concerns, especially in regulated environments like healthcare or finance. The framework’s ability to identify and respond to threats relies on processing this information, and ensuring compliance with relevant privacy regulations (like GDPR or CCPA) is paramount. Failure to properly anonymize or de-identify sensitive data before analysis could lead to significant legal and reputational damage.
Mitigation Strategies for Identified Risks
A robust security posture for D3FEND 1.0 requires a multi-layered approach. This includes regular security audits and penetration testing to identify and address vulnerabilities. Strong access control mechanisms, including multi-factor authentication and least privilege principles, should be implemented to restrict access to sensitive components and data. Data encryption, both in transit and at rest, is essential to protect sensitive information from unauthorized access. Furthermore, regular software updates and patching are crucial to address newly discovered vulnerabilities. Finally, comprehensive security monitoring and incident response plans are necessary to detect and respond to security incidents promptly and effectively.
Best Practices for Secure Implementation and Usage
Prior to deploying D3FEND 1.0, a thorough risk assessment should be conducted to identify potential vulnerabilities and develop appropriate mitigation strategies. This assessment should cover all aspects of the implementation, from the underlying infrastructure to the integration with existing security systems. Regular security training for personnel involved in managing and using the framework is crucial to ensure they understand potential risks and best practices. The establishment of clear security policies and procedures is also vital to ensure consistent and secure operation. These policies should cover areas such as access control, data handling, incident response, and vulnerability management. Finally, adherence to industry best practices and relevant security standards is essential to maintain a robust security posture.
Comparison with other threat detection frameworks
Source: malwarebytes.com
D3FEND 1.0 isn’t the only game in town when it comes to threat detection frameworks. To understand its unique position, we need to compare it to other established players, highlighting its strengths and weaknesses relative to them. This comparison will focus on key features, providing a clearer picture of D3FEND 1.0’s capabilities and limitations within the broader cybersecurity landscape.
Several frameworks offer similar functionalities to D3FEND 1.0, each with its own approach and focus. A direct comparison helps determine which framework best suits specific organizational needs and priorities. Consider factors like data sources, analysis methods, and reporting capabilities when making a choice.
D3FEND 1.0 Compared to Other Frameworks
The following table compares D3FEND 1.0 with other prominent threat detection frameworks, focusing on key features, strengths, and weaknesses. This comparative analysis provides a nuanced understanding of D3FEND 1.0’s place within the existing ecosystem.
| Framework Name | Key Features | Strengths | Weaknesses |
|---|---|---|---|
| MITRE D3FEND 1.0 | Data ingestion from diverse sources, automated threat detection, customizable workflows, integrated visualization tools. | Comprehensive data integration, flexible architecture, strong visualization capabilities, focus on automation. | Relatively new framework, limited community support compared to established frameworks, potential complexity for smaller organizations. |
| MITRE ATT&CK | Adversarial tactics, techniques, and common knowledge (TTPs) framework, knowledge base for threat hunting and detection. | Widely adopted industry standard, provides a common language for threat description, facilitates knowledge sharing. | Not a detection framework itself; requires integration with other tools for practical application, can be complex to fully understand. |
| Elastic Stack (ELK) | Centralized log management, real-time data visualization, powerful search and analytics capabilities. | Highly scalable and flexible, open-source with a large community, extensive ecosystem of plugins and integrations. | Requires significant expertise to configure and manage effectively, can be resource-intensive for large datasets. |
| Splunk | Comprehensive security information and event management (SIEM) platform, log management, threat detection, and security analytics. | Mature platform with robust features, strong vendor support, wide range of integrations. | Can be expensive, complex to implement and manage, requires specialized skills. |
| TheHive | Open-source platform for security orchestration, automation, and response (SOAR), incident management, threat intelligence integration. | Flexible and customizable, open-source with a growing community, supports automation of security workflows. | Requires technical expertise to configure and maintain, may require significant customization for specific needs. |
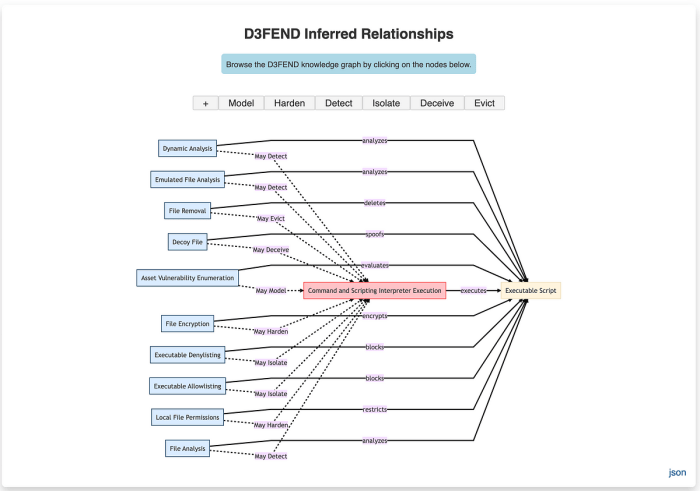
Future Developments and Enhancements for D3FEND
Source: medium.com
D3FEND 1.0 represents a significant leap forward in threat detection, but like any robust framework, it’s built for growth and adaptation. The ever-evolving landscape of cyber threats demands continuous improvement, and several avenues exist for enhancing D3FEND’s capabilities and broadening its applicability. Future iterations should focus on increased automation, improved integration with existing security tools, and enhanced user experience.
The potential for future D3FEND enhancements is vast, encompassing improvements across its architecture, functionality, and user interface. Expanding its capabilities to address emerging threat vectors and incorporating machine learning for more sophisticated threat hunting are key areas of focus. Imagine a future where D3FEND proactively identifies and mitigates threats before they even impact an organization’s systems – that’s the kind of transformative potential we’re talking about.
Automated Threat Response
D3FEND’s current capabilities primarily focus on detection. Future versions could integrate automated response mechanisms, allowing the framework to not only identify threats but also automatically take actions to neutralize them. This could include automated blocking of malicious IPs, isolation of compromised systems, or even automated patching of vulnerabilities. This level of automation would significantly reduce the response time to threats, minimizing potential damage. For example, imagine a scenario where D3FEND detects a ransomware attack in progress; an automated response could immediately quarantine the affected system, preventing further spread.
Enhanced Integration with Existing Security Tools
Seamless integration with existing Security Information and Event Management (SIEM) systems, endpoint detection and response (EDR) solutions, and other security tools is crucial for maximizing D3FEND’s effectiveness. Future versions should prioritize interoperability, allowing for a more unified and comprehensive security posture. This could involve developing standardized APIs or utilizing existing industry standards to facilitate data exchange and automated workflows between D3FEND and other security tools. Think of a scenario where D3FEND receives an alert from an EDR system about suspicious activity on a specific endpoint; seamless integration would allow D3FEND to automatically enrich this alert with additional context and initiate a more targeted investigation.
Improved User Interface and User Experience
The current user interface should be streamlined for better usability. Future iterations could focus on improving the visual representation of threat data, providing more intuitive navigation, and offering customized dashboards tailored to different user roles and responsibilities. This enhanced user experience would empower security analysts to more effectively utilize D3FEND’s capabilities, leading to faster threat detection and response. A more intuitive interface could mean the difference between a security analyst quickly identifying a critical threat and missing it altogether.
Potential Features for Future Releases
The following enhancements would significantly improve D3FEND’s capabilities:
- Support for more diverse data sources: Expanding the range of data sources integrated into D3FEND, including cloud-based services, IoT devices, and industrial control systems.
- Advanced analytics and machine learning: Incorporating machine learning algorithms for more accurate threat prediction and anomaly detection.
- Improved threat intelligence integration: Seamless integration with external threat intelligence feeds to provide richer context and improve detection accuracy.
- Scalability and performance improvements: Optimizing D3FEND’s architecture to handle larger volumes of data and support larger organizations.
- Enhanced reporting and visualization: Providing more comprehensive and customizable reporting capabilities to facilitate better security monitoring and compliance.
Concluding Remarks
Source: malwarebytes.com
MITRE’s launch of D3FEND 1.0 marks a significant leap forward in cybersecurity. Its innovative approach, combined with a focus on practical application, positions it as a powerful tool for organizations of all sizes. While challenges remain, the potential for improved threat detection and response is undeniable. The future of cybersecurity looks brighter—and more D3FEND-powered—than ever before. Buckle up, because this is just the beginning.


