Microsoft Fics Azure Entra: The words alone conjure images of robust security and seamless cloud integration. But what exactly *is* this powerful combination, and how does it revolutionize how businesses manage their digital identities and access to sensitive Azure resources? It’s not just about ticking compliance boxes; it’s about building a truly secure and efficient digital ecosystem, one that’s both resilient and adaptable to the ever-evolving threat landscape. This deep dive explores the architecture, functionality, and future of this potent pairing.
We’ll unpack the intricate dance between Microsoft Entra’s identity management capabilities and Azure’s extensive cloud services. We’ll examine how this integration simplifies complex tasks, enhances security posture through conditional access policies, and helps organizations meet stringent compliance standards like FICS. Prepare to navigate the complexities of authentication methods, role-based access control, and troubleshooting common integration hurdles – all while uncovering the potential of future developments in this dynamic field.
Microsoft Entra and Azure Integration
Source: microsoft.com
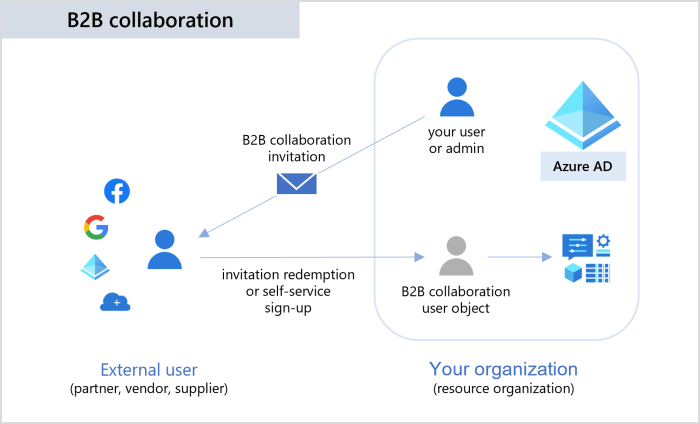
Microsoft Entra, formerly Azure Active Directory (Azure AD), is Microsoft’s identity and access management (IAM) solution. Its deep integration with Azure services streamlines the management of user identities and access to cloud resources, offering a more secure and efficient approach to managing your organization’s digital assets. This integration is crucial for organizations leveraging the power of Azure’s cloud services.
Microsoft Entra Architecture and Azure Service Integration
Microsoft Entra integrates with Azure services through a variety of mechanisms, primarily leveraging its core identity management capabilities. The architecture is built on a foundation of cloud-based services, allowing for seamless integration with various Azure resources, including Azure Virtual Machines, Azure SQL Database, and Azure Storage. This integration relies on protocols like OAuth 2.0 and OpenID Connect for secure authentication and authorization, ensuring that only authorized users and applications can access specific Azure resources. Essentially, Microsoft Entra acts as the central identity provider, verifying user identities and granting access based on pre-defined policies. This centralized approach simplifies management and enhances security across all your Azure services.
Authentication Methods for Accessing Azure Resources
Microsoft Entra supports a range of authentication methods for accessing Azure resources. These methods cater to various security needs and user preferences. Password-based authentication remains a common method, but Microsoft Entra strongly encourages the use of more secure options like multi-factor authentication (MFA) to enhance security. MFA adds an extra layer of protection, requiring users to verify their identity through a secondary method, such as a phone call, text message, or authentication app. Certificate-based authentication provides another strong authentication method, ideal for machines and applications. Finally, federated identity provides a way for organizations to integrate their on-premises Active Directory with Microsoft Entra, allowing for single sign-on (SSO) access to both on-premises and cloud-based resources.
Conditional Access Policies and Enhanced Azure Security
Microsoft Entra’s conditional access policies are a cornerstone of enhanced Azure security. These policies allow administrators to define granular access rules based on various conditions, such as user location, device posture, and application type. For example, a policy might require MFA for users accessing sensitive data from untrusted networks or block access to specific applications from compromised devices. This granular control significantly reduces the risk of unauthorized access and data breaches, providing a powerful mechanism for enforcing security policies across Azure resources. By tailoring access based on context, organizations can minimize their attack surface and protect their valuable data.
Microsoft Entra Simplifying Identity and Access Management in Hybrid Cloud Environments, Microsoft fics azure entra
For organizations operating in hybrid cloud environments—a blend of on-premises infrastructure and Azure—Microsoft Entra simplifies identity and access management significantly. It enables single sign-on (SSO) across both environments, allowing users to access both on-premises and Azure resources with a single set of credentials. This eliminates the need for managing separate credentials for different environments, improving user experience and reducing administrative overhead. Moreover, it allows for consistent policy enforcement across both environments, simplifying security management and improving overall security posture. This seamless integration makes it easier to migrate workloads to the cloud while maintaining a unified identity and access management strategy.
Comparison of Microsoft Entra ID and Azure Active Directory
The following table compares Microsoft Entra ID and Azure Active Directory, highlighting key differences:
| Feature | Entra ID | Azure AD | Differences |
|---|---|---|---|
| Branding | Customizable branding options | Limited branding options | Entra ID offers greater flexibility in customizing the user experience. |
| External Identity Management | Enhanced support for managing external identities (B2B, B2C) | Support for external identities | Entra ID provides more advanced features for managing external users and partners. |
| Security features | Advanced security features like passwordless authentication and risk-based access control | Strong security features | Entra ID offers more sophisticated security capabilities to address evolving threats. |
| Pricing | Different pricing tiers based on features and usage | Different pricing tiers based on features and usage | Pricing models may vary slightly depending on the specific features used. |
FICS (Financial Industry Cybersecurity Standards) Compliance with Microsoft Entra and Azure

Source: ictpower.it
Navigating the complex world of financial cybersecurity requires robust solutions. Microsoft Entra and Azure, when integrated effectively, offer a powerful combination to help financial institutions meet the stringent requirements of FICS (Financial Industry Cybersecurity Standards). This synergy provides a comprehensive approach to identity and access management, bolstering security posture significantly.
Microsoft Entra significantly contributes to FICS compliance by providing a centralized identity and access management (IAM) platform. This allows for streamlined management of user identities, access permissions, and authentication methods across various systems and applications within a financial organization. This centralized approach simplifies compliance efforts, enabling easier auditing and reporting, crucial aspects of meeting FICS requirements. The granular control over access rights minimizes the risk of unauthorized access and data breaches, directly addressing several key FICS controls.
Microsoft Entra’s Role in Meeting FICS Identity and Access Management Requirements
Microsoft Entra’s capabilities directly support several FICS requirements related to identity and access management. Its multi-factor authentication (MFA) capabilities, for instance, strengthen access controls, mitigating the risk of unauthorized logins, a common vulnerability addressed by numerous FICS controls. Furthermore, its conditional access policies allow for dynamic adjustments to access based on various factors like location, device, and user risk profile, thus enhancing security posture and compliance. The comprehensive auditing features within Entra provide detailed logs of all access attempts and activities, simplifying the process of demonstrating compliance to regulatory bodies. The ability to manage user lifecycle events, from onboarding to offboarding, within a single platform ensures consistent application of security policies and reduces vulnerabilities associated with account management.
Azure Security Features Relevant to FICS Compliance
Azure’s robust security features, when integrated with Microsoft Entra, further strengthen FICS compliance. Azure Active Directory (Azure AD) Conditional Access, integrated seamlessly with Microsoft Entra, provides granular control over access based on various risk factors. Azure Security Center offers continuous threat detection and protection, providing alerts and recommendations to address potential vulnerabilities. Azure’s built-in encryption capabilities, both at rest and in transit, protect sensitive data from unauthorized access. The Azure platform’s compliance certifications, including those relevant to FICS, provide an additional layer of assurance for financial institutions. Regular security assessments and penetration testing within the Azure environment, conducted in line with best practices, further enhance compliance posture.
Specific FICS Controls Addressed by Microsoft Entra and Azure
The combined power of Microsoft Entra and Azure directly addresses several key FICS controls. For example, the combination effectively addresses controls related to access control, authentication, authorization, data encryption, audit logging, and incident response. Specific FICS controls relating to privileged access management (PAM) are also addressed through features like Azure AD Privileged Identity Management (PIM), which allows for just-in-time elevation of privileges, reducing the overall attack surface. The ability to enforce multi-factor authentication (MFA) for all users, regardless of their role, significantly contributes to meeting FICS requirements for strong authentication.
Best Practices for Implementing Microsoft Entra and Azure for FICS Compliance
Implementing Microsoft Entra and Azure for FICS compliance requires a well-defined strategy. This includes thorough risk assessments to identify critical assets and potential vulnerabilities. A phased approach to implementation, starting with high-risk areas, is recommended. Regular security audits and penetration testing are crucial to ensure ongoing compliance. Comprehensive training for employees on security best practices and the use of Microsoft Entra and Azure features is essential. Finally, establishing clear roles and responsibilities for security management ensures effective oversight and accountability.
Hypothetical Scenario Demonstrating FICS Vulnerability Mitigation
Imagine a scenario where a financial institution experiences a phishing attack targeting employee credentials. Without robust security measures, this could lead to unauthorized access and potential data breaches, violating several FICS controls. However, with Microsoft Entra’s MFA and Azure AD Conditional Access in place, even if an employee’s credentials are compromised, access is denied. The MFA requirement forces attackers to bypass an additional security layer, while Conditional Access policies can block access based on the location or device used, effectively preventing unauthorized access and mitigating the risk of a successful attack. The integrated logging and alerting systems within Azure and Entra allow for swift identification and response to such incidents, minimizing potential damage and facilitating compliance with FICS incident response requirements.
Microsoft Entra’s Role in Securing Azure Resources: Microsoft Fics Azure Entra
Microsoft Entra acts as the central nervous system for securing your Azure environment, providing a unified platform to manage identities, access, and compliance. It’s not just about logging in; it’s about granular control over who can access what, and how they access it, ensuring only authorized users can interact with your valuable Azure resources. This comprehensive approach significantly strengthens your overall security posture.
Role-Based Access Control (RBAC) in Azure via Microsoft Entra
Microsoft Entra allows for fine-grained control over Azure resources through its robust Role-Based Access Control (RBAC) system. You can assign specific roles, each with a predefined set of permissions, to users, groups, or managed identities. This ensures that individuals only have access to the resources necessary for their job functions, minimizing the risk of unauthorized access or data breaches. For example, a database administrator might be assigned the “SQL Server Contributor” role, granting them the ability to manage a specific SQL database instance, but not other Azure services. Conversely, a developer might only have “Contributor” access to a specific resource group, limiting their actions to that scope. This granular control is crucial for maintaining a secure and efficient environment.
Microsoft Entra Access Reviews for Secure Access Management
Regularly reviewing access permissions is vital for maintaining a secure environment. Microsoft Entra’s access reviews automate this process, allowing you to periodically assess who has access to specific Azure resources and ensure those permissions are still valid. These reviews can be scheduled to occur automatically, for instance, every 30 days, prompting designated approvers to confirm or deny access. This proactive approach helps identify and revoke unnecessary or outdated access, mitigating potential security risks and preventing unauthorized access to sensitive data. For example, a departing employee’s access can be easily identified and removed through these automated reviews, preventing lingering access points.
Managing Privileged Access to Sensitive Azure Resources with Microsoft Entra
Privileged access to sensitive Azure resources, such as administrative accounts, requires extra layers of security. Microsoft Entra provides mechanisms to manage this elevated access effectively, including Just-In-Time (JIT) access, which grants temporary elevated privileges only when needed. This limits the exposure time for high-privilege accounts, reducing the window of opportunity for attackers. Additionally, Microsoft Entra allows for the creation of separate, highly secure privileged identity management (PIM) accounts, ensuring that even privileged users only have access when explicitly approved and monitored. These accounts, often requiring multi-factor authentication, are carefully monitored to identify suspicious activity.
Setting Up Multi-Factor Authentication (MFA) for Azure Access using Microsoft Entra
Implementing MFA is paramount for enhanced security. Here’s a step-by-step guide for setting it up using Microsoft Entra:
1. Navigate to Azure Active Directory: Log in to the Azure portal and go to Azure Active Directory.
2. Security: Select “Security” from the left-hand menu.
3. Multi-factor authentication: Find and select “Multi-factor authentication”.
4. Enable MFA: Choose to enable MFA for all users or specific groups. For enhanced security, it’s best practice to enable MFA for all users.
5. Configure MFA methods: Select the preferred MFA methods, such as authenticator apps, phone calls, or text messages.
6. Assign users/groups: Select the users or groups that will be required to use MFA.
7. Test MFA: Test the configuration by attempting to log in with a user who has MFA enabled.
This straightforward process adds a significant layer of security to your Azure environment.
Azure Services and Their Security Considerations with Microsoft Entra Integration
Implementing strong security practices is essential for every Azure service. Here’s a look at some key services and their security considerations when integrated with Microsoft Entra:
- Azure Virtual Machines (VMs): Utilize managed identities for VMs to access other Azure resources without requiring secrets. Implement network security groups (NSGs) and just-in-time VM access to further enhance security.
- Azure SQL Database: Leverage Azure Active Directory authentication to control access to your database instances. Implement row-level security and always encrypt your data at rest and in transit.
- Azure Storage: Utilize role-based access control (RBAC) to manage access to storage accounts. Implement strong encryption and ensure only authorized users have access to sensitive data.
- Azure Active Directory (Azure AD): Regularly review and update user access permissions, leveraging access reviews and conditional access policies to further secure your environment. Enable MFA for all users.
- Azure Kubernetes Service (AKS): Implement role-based access control (RBAC) within the Kubernetes cluster to manage access to pods and other Kubernetes resources. Secure your Kubernetes API server and integrate with Azure AD for authentication and authorization.
Troubleshooting Common Issues with Microsoft Entra and Azure
Integrating Microsoft Entra with Azure offers robust security, but troubleshooting hiccups is inevitable. This section dives into common problems, their causes, and practical solutions, empowering you to navigate these challenges effectively. Understanding these issues is crucial for maintaining a smooth and secure access experience.
Authentication Errors
Authentication failures are frequent roadblocks when using Microsoft Entra to access Azure resources. These errors often stem from incorrect credentials, password expiration, multi-factor authentication (MFA) failures, or issues with the Entra ID service itself. Solutions involve verifying user credentials, resetting passwords, ensuring MFA is properly configured and functioning, and checking the Microsoft Entra service health dashboard for any reported outages. Common error messages might include “Incorrect username or password,” “MFA required,” or generic “Authentication failed” messages. Careful examination of the specific error message provides vital clues. For example, an error referencing a specific MFA method suggests problems with that specific authentication pathway.
Conditional Access Policy Issues
Conditional Access policies, while enhancing security, can inadvertently block legitimate access if not configured correctly. Troubleshooting involves reviewing the policy’s conditions (location, device, application, user/group) and actions (grant access, block access, require MFA). A common problem is overly restrictive policies that block access from legitimate users or devices. The solution often lies in refining the policy conditions to allow for exceptions or adjusting the actions to be less restrictive. For example, a policy blocking access from all non-corporate devices might need exceptions for specific trusted devices or users. Thorough testing of policies after modification is critical.
User Provisioning and De-provisioning Problems
Synchronization issues between Microsoft Entra and Azure can lead to problems with user access. Troubleshooting these issues requires checking the synchronization status in the Azure portal, verifying that the user’s account exists in both Entra ID and Azure Active Directory, and confirming that the correct attributes are being synchronized. Problems might stem from incorrect configuration of the synchronization settings, network connectivity issues, or errors in the user’s profile attributes. Resolving these issues may involve re-running the synchronization process, correcting attribute mapping, or investigating network connectivity problems. Error messages might indicate specific attribute conflicts or synchronization failures.
Error Message Examples and Interpretations
Understanding error messages is paramount. For example, “AADSTS50058: AADSTS50058: AADSTS50058: The user account does not exist in the tenant” clearly points to a user account not being present in the Microsoft Entra tenant. Another example, “Error code: 500 Internal Server Error” suggests a problem with the Microsoft Entra service itself, requiring checking the service health status. A message indicating a specific attribute mismatch during synchronization highlights a problem with the user profile data or synchronization settings. These examples highlight the importance of carefully analyzing the error messages provided.
Troubleshooting Flowchart: Conditional Access Policy Block
A flowchart illustrating troubleshooting a blocked access due to a Conditional Access Policy might look like this:
(Descriptive text instead of image):
Start -> User reports access denied -> Check Conditional Access policies affecting user/resource -> Policy found affecting access? Yes -> Review policy conditions (location, device, app, user/group) -> Conditions too restrictive? Yes -> Modify policy to allow access (add exceptions, adjust actions) -> Test access -> Access granted? Yes -> End. No -> Check policy configuration for errors -> Rectify errors -> Test access -> Access granted? Yes -> End. No -> Contact Microsoft Support -> End. No -> Investigate other potential causes (network issues, authentication problems) -> Resolve identified issues -> Test access -> Access granted? Yes -> End. No -> Contact Microsoft Support -> End.
Future Trends and Developments in Microsoft Entra and Azure Integration

Source: 848.co
Microsoft Entra and Azure’s integration is rapidly evolving, driven by the increasing sophistication of cyber threats and the expanding demands of cloud-based services. The future of this integration promises tighter security, streamlined management, and enhanced user experiences, all while adapting to the ever-changing landscape of digital security. This section explores the key trends shaping this evolution.
Anticipated Enhancements to Microsoft Entra’s Azure Integration
Microsoft is likely to focus on simplifying the management of identities and access across both Entra and Azure. We can anticipate improvements in automation, allowing for more efficient provisioning and de-provisioning of users and resources. Expect to see more seamless integration with other Microsoft services, creating a truly unified security and identity platform. This might include tighter integration with Microsoft 365, enabling a single pane of glass for managing all aspects of user access and security across the entire Microsoft ecosystem. Think of it like a well-oiled machine, where every part works in harmony to maximize efficiency and security. For example, imagine automatic user provisioning to Azure resources upon onboarding to Microsoft 365, eliminating manual configuration and reducing the risk of human error.
Emerging Security Technologies Impacting Microsoft Entra and Azure Integration
The integration will increasingly leverage emerging security technologies like AI and machine learning. These technologies will enhance threat detection and response capabilities within the integrated platform. For instance, AI-powered anomaly detection could flag suspicious login attempts or data access patterns in real-time, proactively mitigating potential breaches. Furthermore, the integration will likely incorporate passwordless authentication methods, such as biometric authentication or FIDO2 security keys, strengthening security while improving user experience. The adoption of zero trust principles will also play a major role, ensuring that every user and device is continuously verified before access is granted, regardless of location. A real-world example is the increased use of behavioral biometrics, analyzing user typing patterns and mouse movements to detect unauthorized access attempts.
Microsoft Entra’s Evolution to Meet Future Cybersecurity Challenges in Azure
As cloud environments become more complex and attacks grow more sophisticated, Microsoft Entra will need to evolve to address these challenges. We predict that the platform will incorporate advanced threat intelligence feeds and integrate more closely with security information and event management (SIEM) systems. This enhanced threat intelligence will enable proactive threat hunting and more effective incident response. Furthermore, the platform will likely need to adapt to support new cloud-native security models, such as serverless computing and containerized environments. For example, the platform could automatically detect and secure newly deployed serverless functions, ensuring consistent security posture across all Azure resources. This proactive approach would help organizations maintain a strong security posture, even as their cloud infrastructure evolves.
Potential Areas for Improvement in the Current Integration Between Microsoft Entra and Azure
While the current integration offers significant capabilities, there’s always room for improvement. One area for improvement could be enhanced reporting and analytics. More comprehensive dashboards and reporting features would provide greater visibility into security posture and allow for more effective security management. Another potential area is simplifying the onboarding process for new users and resources. Streamlining this process would reduce administrative overhead and minimize the risk of misconfigurations. Finally, improved documentation and user-friendly interfaces could enhance the overall user experience and make it easier for administrators to manage the integrated platform effectively. A simplified user interface could resemble the intuitive design of popular consumer applications, making complex security tasks more accessible to administrators.
Hypothetical Future Integration Enhancement: Unified Security Posture Management
Imagine a future where a single dashboard provides a comprehensive view of the security posture across all Azure resources, managed through Microsoft Entra. This hypothetical enhancement would offer a unified security posture management (USPM) capability, consolidating security alerts, configuration assessments, and compliance reports from various Azure services into a single, easily digestible view. This would dramatically improve an organization’s ability to identify and respond to threats, and ensure compliance with various security standards. The benefits would include simplified security management, reduced risk of misconfigurations, and improved visibility into overall security posture. However, the challenge would lie in integrating data from diverse Azure services and ensuring the accuracy and reliability of the consolidated information. This would require robust data aggregation and analysis capabilities, and careful consideration of data privacy and security implications.
Conclusion
Mastering Microsoft Fics Azure Entra isn’t just about checking off a security checklist; it’s about strategically weaving a robust, adaptable security fabric into the very core of your organization’s digital infrastructure. By understanding the intricacies of its integration, leveraging its powerful features, and proactively addressing potential challenges, businesses can unlock the true potential of the cloud while mitigating risks and ensuring compliance. The future of secure cloud operations hinges on such intelligent, integrated solutions – and Microsoft Fics Azure Entra is leading the charge.