Malware attacking Linux servers? Yeah, it happens. Think impenetrable fortress? Think again. This isn’t just some Windows-only drama; Linux servers, despite their reputation for security, are increasingly becoming targets for sophisticated malware attacks. From sneaky rootkits to devastating ransomware, the digital bad guys are getting creative, finding new ways to exploit vulnerabilities and wreak havoc. This deep dive explores the various types of malware, how they infiltrate systems, the damage they inflict, and – most importantly – how to defend against them. Get ready to level up your Linux server security game.
We’ll cover everything from the common infection vectors – like phishing emails and compromised software – to the specific behaviors of different malware families. We’ll dissect real-world case studies, showing you exactly what went wrong and how it could have been prevented. By the end, you’ll have a solid understanding of the threats facing Linux servers and a practical toolkit for staying ahead of the curve. Let’s get started.
Types of Malware Targeting Linux Servers
Linux servers, once considered a bastion of security, are increasingly becoming targets for sophisticated malware. The open-source nature and widespread adoption of Linux have unfortunately made it a lucrative platform for cybercriminals. Understanding the different types of malware and their attack vectors is crucial for effective server security.
Several families of malware are specifically designed to exploit vulnerabilities in Linux systems. These malicious programs employ diverse methods to compromise servers, ranging from subtle rootkits to destructive ransomware attacks. The consequences can be devastating, leading to data breaches, system outages, and significant financial losses.
Common Linux Malware Families
Linux malware families exhibit a wide range of capabilities and attack strategies. Some focus on establishing persistent backdoors, while others aim for data exfiltration or denial-of-service attacks. Understanding these distinctions is critical for effective defense. Notable examples include Mirai, which is known for its botnet capabilities, and various rootkits that stealthily grant attackers control. Ransomware, though less prevalent on Linux than on Windows, is a growing threat.
Comparison of Malware Attack Methods
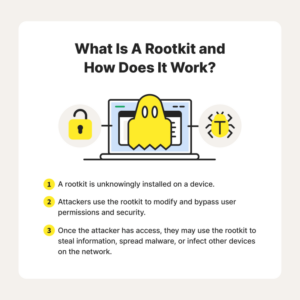
Rootkits, botnets, and ransomware represent distinct categories of Linux malware, each employing different techniques to achieve their malicious goals. Rootkits operate by concealing their presence on the system, granting attackers persistent, undetected access. Botnets, on the other hand, compromise numerous systems to form a network of controlled machines, often used for DDoS attacks or spam distribution. Ransomware encrypts critical data, demanding a ransom for its release. The vulnerabilities exploited vary considerably; rootkits often leverage kernel vulnerabilities or weaknesses in system utilities, while botnets frequently target exposed services or weak passwords. Ransomware might exploit vulnerabilities in applications or use social engineering to gain initial access.
Vulnerability Exploitation by Malware Types
The success of any malware hinges on exploiting system vulnerabilities. For instance, outdated software packages, misconfigured services, and weak passwords are common entry points. Rootkits might exploit kernel vulnerabilities to gain elevated privileges, hiding their malicious processes and files from standard system tools. Botnets often leverage vulnerabilities in network services like SSH or exposed databases to gain initial access, while ransomware might target vulnerabilities in applications to deliver its payload.
| Malware Name | Target Vulnerability | Infection Method | Impact |
|---|---|---|---|
| Mirai | Weak SSH credentials, default credentials on IoT devices | Network scanning, brute-force attacks | Distributed Denial-of-Service (DDoS) attacks |
| Rootkit (e.g., rkhunter) | Kernel vulnerabilities, compromised user accounts | Exploiting software vulnerabilities, social engineering | Persistent backdoor access, data theft, system compromise |
| Ransomware (various) | Software vulnerabilities, weak passwords, phishing | Phishing emails, malicious attachments, exploiting vulnerabilities | Data encryption, ransom demands, business disruption |
| Linux.Encoder | Vulnerabilities in web applications | Exploiting vulnerabilities in web servers | Data encryption, ransom demands |
Infection Vectors and Entry Points
Linux servers, despite their reputation for security, aren’t immune to malware. Understanding how these attacks happen is crucial for effective defense. This section delves into the common methods malicious actors use to infiltrate Linux systems and the steps involved in a successful infection.
Malicious code finds its way onto Linux servers through various vectors, each exploiting vulnerabilities in the system’s software or human oversight. These infections aren’t always sophisticated; sometimes, a simple oversight opens the door for disaster. Let’s explore the most prevalent pathways.
Common Malware Delivery Methods
Several methods facilitate the delivery of malware to Linux servers. These range from targeted phishing campaigns to exploiting known vulnerabilities in widely used software packages. Understanding these methods is the first step in building a robust defense.
- Phishing: Social engineering remains a potent weapon. Attackers craft convincing emails or messages, often mimicking legitimate organizations, to trick users into clicking malicious links or downloading infected attachments. These attachments might contain shell scripts or executables that install malware silently. A successful phishing attack often hinges on exploiting human psychology rather than technical vulnerabilities.
- Exploit Kits: These automated tools scan for known vulnerabilities in web servers and applications. Once a vulnerability is identified, the exploit kit automatically downloads and installs malware onto the compromised server. This automated approach allows attackers to target many systems simultaneously, increasing the efficiency of their attacks.
- Compromised Software: Software downloaded from untrusted sources or containing backdoors can act as a vector for malware. This is particularly true for open-source software that hasn’t undergone rigorous security audits. Even seemingly legitimate software can be compromised and used to distribute malware, highlighting the importance of using reputable sources.
- Software Vulnerabilities: Unpatched software represents a significant entry point. Attackers actively seek out and exploit known vulnerabilities in popular applications and operating systems. A timely patching strategy is paramount to mitigating this risk. Exploiting these flaws allows for remote code execution, enabling the attacker to gain control of the server.
Stages of a Typical Malware Infection
A successful malware infection usually follows a predictable pattern. While the specifics vary depending on the malware, understanding these stages is vital for effective incident response.
- Initial Access: The attacker gains initial access to the target server using one of the methods discussed above (e.g., exploiting a vulnerability, successful phishing attempt).
- Persistence: The malware establishes persistence, ensuring it survives reboots and system restarts. This often involves adding itself to the system’s startup processes or modifying system configuration files.
- Privilege Escalation: The malware attempts to elevate its privileges, gaining root access to the system. This allows it to execute commands with maximum authority and control.
- Payload Execution: The malware executes its intended payload. This could range from data exfiltration to launching denial-of-service attacks or using the server as part of a botnet.
- C&C Communication: The malware communicates with a command-and-control (C&C) server, receiving further instructions from the attacker.
Examples of Malicious Code Snippets
While providing specific malicious code snippets is irresponsible due to potential misuse, it’s important to understand the general techniques used. Attackers often leverage shell commands and scripting languages to exploit vulnerabilities. For example, a script might leverage a known vulnerability in a specific application to execute arbitrary code with elevated privileges. The code would typically involve system calls or library functions that allow the attacker to perform malicious actions. Analyzing these techniques helps security professionals develop better defenses.
Flowchart Illustrating Malware Attack Stages
Imagine a flowchart starting with “Initial Access” (e.g., via exploit kit), branching to “Persistence” (cron job modification, etc.), then “Privilege Escalation” (exploiting sudo vulnerabilities), followed by “Payload Execution” (data theft, botnet activity), and finally “C&C Communication.” Each stage would represent a node in the flowchart, with arrows indicating the progression of the attack. The flowchart visually represents the step-by-step process, illustrating how a seemingly small vulnerability can lead to a complete system compromise.
Malware Behavior and Impact: Malware Attacking Linux Servers
Linux malware, while less prevalent than its Windows counterpart, can be equally devastating. Understanding its behavior and impact is crucial for effective prevention and mitigation. Different malware types exhibit varying levels of aggression, ranging from subtle performance degradation to complete system compromise. The consequences can be severe, impacting everything from data integrity to the overall security posture of your server.
The insidious nature of Linux malware lies in its ability to silently infiltrate systems, often remaining undetected for extended periods. This stealthy behavior allows attackers to achieve their objectives—be it data exfiltration, system control, or the establishment of a persistent foothold for future attacks—before any signs of compromise become apparent. The longer the malware remains undetected, the more extensive the damage it can inflict.
System Performance Degradation and Security Risks
Malware impacts system performance in various ways. Resource-intensive malware can consume significant CPU cycles, memory, and disk I/O, leading to slowdowns, application crashes, and overall system instability. For example, a rootkit might hide its processes, making it difficult to identify the source of the performance issues. Furthermore, some malware actively disables security mechanisms, such as firewalls or intrusion detection systems, making the server more vulnerable to further attacks. This compromised security can lead to more severe consequences, such as complete system takeover. The presence of malware weakens the overall security posture, increasing the risk of additional exploits and vulnerabilities.
Data Integrity and Confidentiality Breaches
Malware can compromise data integrity by modifying or deleting files, corrupting databases, or manipulating system logs. Ransomware, for instance, encrypts critical data, rendering it inaccessible unless a ransom is paid. Data confidentiality is also at risk, as some malware is designed to steal sensitive information, such as user credentials, intellectual property, or financial records. This stolen data can then be sold on the dark web or used for further malicious activities. Imagine a scenario where a data breach exposes customer information, leading to significant financial and reputational damage for a company.
Unauthorized Access and Control
Malware can grant attackers unauthorized access and control over a Linux server. Backdoors, for example, provide attackers with a persistent entry point, allowing them to remotely access and control the system. Rootkits can elevate the privileges of malicious processes, giving attackers complete control over the server. This level of access allows attackers to perform various malicious actions, including installing additional malware, modifying system settings, and exfiltrating data. Consider a scenario where an attacker gains root access to a web server, enabling them to inject malicious code into the website, potentially leading to the compromise of user data.
Common Indicators of Compromise (IOCs)
Identifying Linux malware requires vigilance and attention to detail. Several indicators can signal a compromise. Unexpected network traffic, unusual system processes, modified system files, and unusual login attempts are all potential IOCs. A sudden spike in disk I/O or CPU usage, especially during off-peak hours, might indicate malicious activity. Furthermore, changes to system logs or the appearance of unfamiliar files or directories should raise suspicion. Regular security audits, including log analysis and vulnerability scanning, are essential for detecting these IOCs and mitigating potential threats. An example of a clear IOC would be the discovery of a previously unknown user account with elevated privileges.
Mitigation and Prevention Strategies

Source: blackhatethicalhacking.com
Protecting your Linux servers from malware requires a proactive and multi-layered approach. Neglecting security best practices leaves your systems vulnerable to a wide range of threats, from data breaches to complete system compromise. A robust security strategy is not just about reacting to attacks; it’s about preventing them in the first place.
Implementing a comprehensive security strategy involves a combination of technical measures and sound operational procedures. This includes regular updates, strong firewall configurations, and vigilant monitoring. Think of it as building a castle with multiple defenses – each layer adds to the overall strength and makes it significantly harder for attackers to breach your defenses.
Regular Software Updates and Patching
Keeping your software up-to-date is paramount. Outdated software often contains known vulnerabilities that attackers exploit. Regular patching closes these security holes, significantly reducing the risk of infection. This applies not only to the operating system but also to all applications and services running on your server. A delay in patching can be the difference between a secure system and a compromised one. Consider automating the update process to ensure timely patching across all your servers. For instance, using tools like `apt` (for Debian/Ubuntu) or `yum` (for CentOS/RHEL) with scheduled tasks ensures patches are applied automatically. Prioritize critical security updates and test them in a staging environment before deploying them to production servers.
Firewall Configuration and Intrusion Detection
Firewalls act as the first line of defense, controlling network traffic in and out of your server. A properly configured firewall blocks unauthorized access attempts, preventing malicious connections from establishing a foothold. It’s crucial to define clear rules, allowing only necessary ports and services. For example, only allow SSH access from trusted IP addresses and block all other incoming connections to port 22. Similarly, web servers should only allow HTTP and HTTPS traffic on ports 80 and 443, respectively. Intrusion Detection Systems (IDS) monitor network traffic and system activity for suspicious patterns. An IDS can detect and alert you to potential attacks, allowing you to respond swiftly and prevent further damage. Both firewalls and IDS should be configured to generate logs for later analysis and incident response.
Implementing a Robust Security Strategy
A strong security posture isn’t achieved overnight. It requires a systematic and ongoing effort. Here’s a step-by-step guide to implement a robust security strategy:
- Regular Security Audits: Conduct regular security assessments to identify vulnerabilities and weaknesses in your systems. Tools like Nessus or OpenVAS can automate this process.
- Principle of Least Privilege: Grant users only the necessary permissions to perform their tasks. Avoid granting excessive privileges that could be exploited.
- Strong Passwords and Authentication: Enforce strong password policies, including password complexity and regular changes. Consider using multi-factor authentication (MFA) for enhanced security.
- Regular Backups: Implement a robust backup and recovery strategy. Regular backups ensure data can be restored in case of a malware attack or other data loss scenarios. Employ the 3-2-1 rule (3 copies of your data, on 2 different media, with 1 copy offsite).
- Intrusion Detection and Prevention: Deploy and configure an IDS/IPS to monitor network traffic and system activity for malicious activity. This will help detect and prevent attacks before they can cause significant damage.
- Security Information and Event Management (SIEM): Implement a SIEM system to collect, analyze, and correlate security logs from various sources. This allows for centralized monitoring and incident response.
- Vulnerability Management: Regularly scan your systems for vulnerabilities and apply patches promptly. Utilize automated vulnerability scanners and integrate them into your workflow.
- Security Awareness Training: Educate users about security best practices to reduce the risk of social engineering attacks. This includes phishing awareness and safe browsing habits.
Incident Response and Remediation

Source: kifarunix.com
A Linux server malware infection can be a serious headache, but swift and decisive action can minimize damage. Effective incident response hinges on a structured approach, combining rapid containment with thorough investigation and recovery. This involves identifying the infection’s scope, eradicating the malware, and restoring your system to a functional state. Let’s break down the crucial steps.
Effective incident response requires a multi-stage process that blends speed with meticulousness. A rapid response is key to preventing further damage, while thorough investigation ensures complete eradication and minimizes future risks. Remember, prevention is always better than cure, but having a robust response plan is crucial.
Identifying and Containing a Malware Infection
The first step involves isolating the infected system to prevent further spread. This might involve disconnecting it from the network and disabling network interfaces. Next, gather evidence – system logs, network traffic logs, and any suspicious files – to understand the malware’s behavior and point of entry. Use tools like tcpdump to capture network traffic and analyze it for malicious activity. Analyze system logs for unusual processes, file modifications, or network connections. Look for signs like unusually high CPU or disk I/O usage, or unexpected network traffic. A compromised system might exhibit sluggish performance, application crashes, or unexpected reboots. The earlier these anomalies are detected, the better the chance of successful containment.
Performing a Thorough System Analysis
Once contained, a thorough analysis is necessary to determine the malware’s full impact. This involves a deep dive into the system’s files and processes. Utilize tools like lsof to list open files and connections, identifying potential malware processes. ps aux and top can help pinpoint resource-intensive processes. Examine file system changes using tools like find to locate unusual files or modifications. Consider using forensic tools like Autopsy or The Sleuth Kit for a more comprehensive analysis. Remember to create backups of crucial data before attempting any remediation steps.
Removing Malware and Restoring System Functionality
Malware removal is a delicate process. Start by terminating any identified malicious processes using kill or pkill. Then, remove the malware files themselves. Be cautious, as incorrect removal could damage the system. If unsure, consult a security professional. After removing the malware, it’s crucial to update the system’s software and security tools to the latest versions. This helps patch any vulnerabilities exploited by the malware. Consider reinstalling the operating system as a last resort, particularly if the infection is severe or the extent of compromise is unclear.
Data Recovery and Impact Mitigation
A robust data recovery plan is essential. Before starting any remediation, create a complete backup of the affected system. This ensures you have a clean copy to restore from. Prioritize recovering critical data first. If data was encrypted by ransomware, consider negotiating with the attackers or using decryption tools if available. However, paying ransoms is not always recommended, as it doesn’t guarantee decryption and encourages further attacks. Once the system is restored, review security policies and procedures to identify weaknesses exploited by the malware. Implement stronger security measures, including regular security audits, intrusion detection systems, and robust access controls. This proactive approach helps minimize the impact of future attacks.
- Isolate the infected system: Disconnect from the network and disable network interfaces.
- Gather evidence: Collect system logs, network traffic logs, and suspicious files.
- Analyze the system: Use tools like
lsof,ps aux,top, andfindto identify malware activity. - Remove malware: Terminate malicious processes and remove infected files.
- Update systems: Apply all necessary software and security updates.
- Restore system functionality: Reinstall the operating system if necessary.
- Recover data: Prioritize recovering critical data from backups.
- Review security policies: Strengthen security measures to prevent future attacks.
Advanced Persistent Threats (APTs) on Linux
Linux servers, once considered a safer haven from malware, are increasingly becoming targets for sophisticated Advanced Persistent Threats (APTs). These aren’t your run-of-the-mill ransomware attacks; APTs are stealthy, long-term operations designed to extract valuable data or disrupt critical infrastructure. Understanding their characteristics and tactics is crucial for effective defense.
APT actors are highly skilled, often state-sponsored or linked to organized crime, possessing significant resources and expertise. Unlike opportunistic malware that spreads widely, APTs are meticulously targeted, focusing on specific organizations or individuals to achieve strategic goals. Their operations often involve multiple attack vectors and stages, making detection and attribution exceptionally challenging.
APT Characteristics and Tactics Targeting Linux Servers, Malware attacking linux servers
APTs targeting Linux leverage a combination of techniques to maintain persistence and evade detection. This often involves exploiting zero-day vulnerabilities, using custom-built malware, and employing advanced social engineering tactics. Initial access might be gained through phishing emails containing malicious attachments or exploiting vulnerabilities in web applications. Once inside, the attackers establish persistent backdoors, often using rootkits or other stealthy techniques to maintain control and access. Data exfiltration is typically slow and methodical, avoiding detection by using techniques like tunneling or steganography to hide their actions. The attackers’ ultimate goal is often long-term access to sensitive information or the ability to manipulate the target’s systems for espionage or sabotage. A common tactic involves using compromised servers as stepping stones to further penetrate the target’s network.
Comparison of APTs with Other Malware Attacks
Unlike common malware like ransomware or worms that aim for rapid propagation and immediate impact, APTs prioritize stealth and persistence. Ransomware, for example, encrypts data and demands a ransom for its release. This is a relatively short-term operation with a clear objective. In contrast, APTs may remain undetected for months or even years, slowly gathering intelligence or manipulating systems. Worms aim for widespread infection, whereas APTs focus on specific, high-value targets. The scale and impact are vastly different; a worm might infect thousands of machines, while an APT might compromise a single, highly sensitive server. The level of sophistication also differs dramatically; APTs employ advanced techniques such as custom malware, zero-day exploits, and advanced evasion tactics, far surpassing the capabilities of typical malware.
Challenges in Detecting and Responding to APT Attacks
Detecting and responding to APTs is exceptionally difficult due to their stealthy nature and advanced techniques. Traditional security solutions often fail to detect these attacks because the malware is highly customized and designed to evade signature-based detection. The long-term nature of the attack makes it difficult to pinpoint the initial compromise. Furthermore, attribution is often challenging, as APT actors employ sophisticated techniques to mask their origin and activities. The need for highly skilled security personnel and advanced threat intelligence capabilities further complicates the response process. Even after detection, remediation can be complex and time-consuming, requiring thorough investigation and system cleanup to ensure complete removal of the malware and any backdoors.
Hypothetical APT Scenario Targeting a Linux Server
Imagine a scenario where a financial institution’s Linux server, responsible for processing high-value transactions, is targeted by an APT group. The attack begins with a spear-phishing email sent to a high-level employee, containing a malicious document that exploits a previously unknown vulnerability in the server’s operating system. Upon execution, the malware establishes a persistent backdoor, allowing the attackers remote access. Over several months, the attackers use this access to exfiltrate sensitive financial data, using steganography to hide their actions within seemingly innocuous network traffic. The attackers carefully monitor security logs and system activity to avoid detection. The impact of this attack could be devastating, leading to significant financial losses, reputational damage, and regulatory penalties. The attackers might also use the compromised server as a launchpad to target other systems within the institution’s network, expanding the scope and impact of the attack. Only after a significant data breach is discovered through an external audit is the presence of the APT revealed, highlighting the challenges in detecting and responding to these sophisticated threats.
Case Studies of Linux Malware Attacks
Linux servers, while often perceived as more secure than their Windows counterparts, are not immune to malware attacks. Understanding real-world examples helps us learn from past mistakes and strengthen our defenses. The following case studies highlight significant incidents, detailing the malware involved, the vulnerabilities exploited, and the resulting impact. Analyzing these cases provides invaluable insights for bolstering security postures.
Analysis of Notable Linux Malware Attacks
The following table summarizes several notable Linux malware attacks, focusing on the malware used, the vulnerabilities exploited, the impact of the attacks, and key lessons learned for future prevention. Understanding these details allows for more proactive and effective security measures.
| Case Name | Malware Type | Impact | Lessons Learned |
|---|---|---|---|
| Operation Shady RAT | Custom-built malware, including backdoors and keyloggers | Data theft from numerous organizations across various sectors, including government agencies and private companies. Significant financial and reputational damage. | The need for robust network segmentation, strong password policies, regular security audits, and employee security awareness training. Early detection systems and proactive threat hunting are crucial. |
| Mirai Botnet Attacks | Mirai botnet malware targeting IoT devices, including Linux-based routers and embedded systems | Large-scale Distributed Denial-of-Service (DDoS) attacks targeting various online services, causing significant outages and disruptions. | The importance of securing IoT devices with strong passwords and regular firmware updates. Implementing robust DDoS mitigation strategies is essential. Regular vulnerability scanning and patching are vital for IoT devices connected to the network. |
| Linux.Encoder.1 | Ransomware that encrypts files on Linux systems | Data loss, business disruption, and financial losses due to ransom demands. | Regular backups are crucial, stored offline or in an immutable storage location. Implementing strong access controls and regular security audits can help prevent infections. Employing robust endpoint detection and response (EDR) solutions can help identify and contain ransomware attacks quickly. |
| The 2017 Equifax Data Breach (Indirect Linux Involvement) | Exploitation of the Apache Struts vulnerability (CVE-2017-5638) which affected many systems, including Linux servers | Massive data breach affecting millions of individuals, resulting in significant financial and reputational damage for Equifax. While not directly targeting Linux, the vulnerability was widespread and impacted many Linux-based systems. | The critical need for timely patching of vulnerabilities, especially in widely used software components. Implementing a robust vulnerability management program is paramount. Regular penetration testing can help identify and address vulnerabilities before they are exploited. |
Ultimate Conclusion

Source: itsyndicate.org
The threat landscape for Linux servers is constantly evolving, but with proactive security measures and a keen awareness of the latest attack vectors, you can significantly reduce your risk. Remember, staying updated on security patches, implementing robust firewalls, and practicing good security hygiene are crucial for safeguarding your systems. This isn’t just about protecting data; it’s about maintaining business continuity and preventing costly downtime. Don’t wait for a disaster to strike; take control of your Linux server security today. The digital bad guys are persistent – let’s be more so.