macOS TCC bypass vulnerability: Sounds scary, right? It should. This sneaky security hole lets malicious actors bypass macOS’s Transparency, Consent, and Control (TCC) framework, essentially granting them unauthorized access to your sensitive data and system settings. Think of it as a backdoor to your digital life, potentially allowing apps to access your camera, microphone, or even your entire file system without your explicit permission. We’re diving deep into the technical details, real-world examples, and most importantly, how to protect yourself.
This vulnerability isn’t just a theoretical threat; it’s a real danger with the potential for serious consequences. From data theft and privacy violations to complete system compromise, the impact of a successful TCC bypass can be devastating. We’ll explore various attack vectors, analyze the root causes, and arm you with the knowledge to safeguard your macOS system.
Understanding the macOS TCC Bypass Vulnerability
macOS’s Transparency, Consent, and Control (TCC) framework is designed to protect user privacy by restricting application access to sensitive system resources like the camera, microphone, and contacts. A TCC bypass vulnerability, however, allows malicious applications to circumvent these restrictions, potentially leading to serious security breaches. Understanding the mechanics of these vulnerabilities is crucial for both developers and users alike.
The Mechanism of a macOS TCC Bypass Vulnerability typically involves exploiting flaws in the TCC’s implementation or interaction with other system components. These flaws might allow an attacker to craft a malicious application that tricks the system into granting unnecessary permissions, or directly manipulates the TCC database to override existing access controls. This often involves leveraging vulnerabilities in other parts of the operating system or utilizing undocumented features to achieve unauthorized access. A successful bypass grants the malicious application access to sensitive user data and system functionalities without the user’s explicit consent, effectively undermining the core purpose of TCC.
Potential Impact on User Data and System Security
A successful TCC bypass can have severe consequences for both user data and overall system security. Malicious actors can gain access to sensitive information such as contacts, location data, microphone recordings, and camera images. This data can be exfiltrated, used for identity theft, or leveraged for blackmail. Furthermore, a compromised system might be used for further attacks, such as installing malware, accessing other accounts, or even controlling the entire system remotely. The potential for data loss, financial damage, and reputational harm is substantial.
Real-World Scenarios of Exploitation
Imagine a seemingly benign application, perhaps a photo editor or a productivity tool, secretly containing malicious code. This code, upon installation, exploits a TCC bypass vulnerability to gain unauthorized access to the user’s contacts or location data. This data could then be used to target the user with phishing attacks or even physical harm. Another scenario could involve a sophisticated malware campaign where a vulnerability in a system utility is exploited to bypass TCC and gain system-wide access, enabling the installation of additional malware or complete system compromise. These are not hypothetical situations; similar attacks have been observed in the past targeting other operating systems and applications.
Common Attack Vectors
Attackers typically leverage several common attack vectors to exploit TCC bypass vulnerabilities. These include:
- Exploiting vulnerabilities in third-party libraries or system components used by the application.
- Using social engineering techniques to trick users into granting unnecessary permissions.
- Direct manipulation of the TCC database using kernel-level exploits.
- Leveraging vulnerabilities in the application’s update mechanism to install malicious code.
These vectors often involve a combination of software vulnerabilities and social engineering tactics, making them particularly effective.
Hypothetical Attack Scenario
Let’s consider a hypothetical scenario: A seemingly legitimate screen-sharing application is released, containing a hidden exploit. When a user installs and runs the application, it silently exploits a zero-day vulnerability in a core macOS component, granting itself elevated privileges. This bypasses TCC restrictions, allowing the application to access the user’s webcam and microphone without their knowledge or consent. The attacker then uses this access to record video and audio, potentially capturing sensitive information or compromising the user’s privacy. The recorded data is then exfiltrated to a remote server controlled by the attacker. This scenario highlights the potential severity of a TCC bypass vulnerability and the need for robust security measures.
Technical Aspects of the macOS TCC Bypass Vulnerability
The macOS Transparency, Consent, and Control (TCC) framework is designed to protect user privacy by requiring applications to explicitly request permission to access sensitive resources like the microphone, camera, or contacts. However, vulnerabilities within TCC can allow malicious actors to bypass these permissions, granting unauthorized access to sensitive data. This section delves into the technical intricacies of these vulnerabilities.
Understanding these vulnerabilities requires a deep dive into the macOS architecture and the specific mechanisms TCC employs. A successful bypass often involves exploiting flaws in how applications interact with the system’s permission model, manipulating system calls, or leveraging unintended interactions between different system components. The consequences can range from simple annoyance to complete system compromise.
Affected System Components
The core components affected by TCC bypass vulnerabilities are the TCC database itself, the system APIs used to interact with it, and the application sandboxing mechanisms. A vulnerability might exploit a weakness in how the database stores and retrieves permission information, or it could involve manipulating the system calls used by applications to request access. Exploiting vulnerabilities in the sandboxing mechanism might allow an application to circumvent TCC entirely. For example, a vulnerability might allow a malicious application to modify its own entitlement file to gain unauthorized access, bypassing the normal permission request process.
Security Features Bypassed
These vulnerabilities bypass the core functionality of the TCC framework. Specifically, they undermine the user’s ability to control which applications have access to sensitive resources. This means applications can access protected data – such as a user’s contacts, microphone recordings, or screen recordings – without the user’s knowledge or consent. The bypass could also affect other security features reliant on TCC, such as the system’s ability to restrict application access based on user-defined profiles.
Types of TCC Bypass Vulnerabilities
Different TCC bypass vulnerabilities utilize diverse techniques. Some might involve race conditions, where an application exploits timing differences in system calls to gain unauthorized access. Others might rely on flaws in the authorization logic, allowing an application to trick the system into granting unnecessary permissions. Still others might leverage vulnerabilities in third-party libraries or frameworks that interact with TCC. For instance, one type might involve exploiting a flaw in a specific system library used for handling permissions, while another could target a vulnerability in a poorly designed application that fails to properly handle permission requests.
Root Causes and Underlying Weaknesses
The root causes often stem from complex interactions within the macOS kernel and the way different components interact with the TCC framework. Poorly designed APIs, insufficient input validation, and memory management issues within the kernel can create vulnerabilities that malicious actors can exploit. Another common cause is the complexity of the system itself; the numerous interactions between different components can lead to unforeseen consequences and vulnerabilities that are difficult to detect.
Exploitation Procedure
A malicious actor might exploit a TCC bypass vulnerability through a multi-step process. First, they would need to identify a vulnerability within the TCC framework or a related system component. Next, they would craft a malicious application that leverages this vulnerability. This application would then be executed on the victim’s machine. The application would then use the vulnerability to bypass TCC’s permission checks, gaining unauthorized access to the desired resources. Finally, the attacker could then exfiltrate the stolen data or use the access for other malicious purposes, such as installing malware or gaining control of the system. The exact steps would depend on the specific vulnerability being exploited. For example, a vulnerability involving a race condition would require precise timing, whereas a vulnerability in the authorization logic might only require a crafted input.
Mitigation and Prevention Strategies
Protecting your macOS system from TCC bypass vulnerabilities requires a multi-layered approach encompassing user vigilance, timely software updates, and robust security practices. Ignoring these vulnerabilities can leave your system open to significant security risks, potentially leading to data breaches or unauthorized access. Let’s explore effective strategies to minimize your exposure.
Best Practices for Users
Adopting secure computing habits is crucial in mitigating the risk of TCC bypass attacks. These practices minimize the chances of malicious software exploiting vulnerabilities.
- Keep your software updated: Regularly update your macOS operating system, applications, and security software to patch known vulnerabilities, including those related to TCC. Apple frequently releases security updates that address such issues.
- Download software from trusted sources: Only download software from official websites or reputable app stores to avoid potentially malicious applications containing exploits.
- Be cautious of suspicious emails and attachments: Avoid opening emails or attachments from unknown senders, as they may contain malware designed to exploit TCC vulnerabilities.
- Enable System Integrity Protection (SIP): SIP is a built-in macOS security feature that helps prevent unauthorized modifications to system files, reducing the risk of TCC bypass attacks. Ensure it remains enabled.
- Use strong passwords and multi-factor authentication (MFA): Strong, unique passwords and MFA add layers of protection, making it harder for attackers to gain access even if a TCC bypass is successful.
Apple Security Updates and Patches
Apple actively addresses security vulnerabilities, including those related to TCC bypasses, through regular software updates. These updates often include critical patches that fix security flaws and prevent exploitation. For example, macOS Monterey 12.x and later versions included several security updates addressing vulnerabilities that could potentially lead to TCC bypass. Checking for updates regularly through System Preferences is essential.
Security Software and Tools
While macOS has built-in security features, utilizing third-party security software can provide an extra layer of protection. These tools often include real-time malware scanning, intrusion detection, and firewall capabilities, helping to detect and prevent TCC bypass attempts. Examples include reputable antivirus software such as Malwarebytes, Sophos, or Bitdefender, though their effectiveness against specific TCC bypass techniques may vary.
Configuring macOS System Settings for Enhanced Security
macOS offers various settings to enhance security and reduce the risk of TCC bypass vulnerabilities. Proper configuration of these settings is crucial.
- Firewall: Enable the built-in firewall and configure it to block incoming connections unless explicitly allowed. This can prevent malicious applications from establishing network connections needed for certain TCC bypass attacks.
- Full Disk Access: Carefully review and restrict which applications have Full Disk Access permissions. Only grant this privilege to trusted and essential applications. This limits the potential impact of a compromised application.
- Privacy Settings: Regularly review the privacy settings for applications, paying close attention to permissions related to microphone, camera, and location access. Revoke permissions for applications you don’t trust or no longer use.
Detecting and Responding to Potential TCC Bypass Attempts
Detecting TCC bypass attempts can be challenging, as they often occur silently. However, certain indicators might suggest a compromise.
- Unusual application behavior: Unexpected changes in application behavior, such as unauthorized access to files or data, may indicate a potential TCC bypass.
- Performance issues: Significant performance degradation, such as slowdowns or crashes, could be a sign of malicious activity exploiting a vulnerability.
- Suspicious network activity: Monitoring network traffic for unusual outgoing connections can help identify malicious activity attempting to exfiltrate data.
If any of these indicators are observed, immediately run a full system scan with updated antivirus software, and consider restoring your system from a known good backup.
Case Studies and Real-World Examples
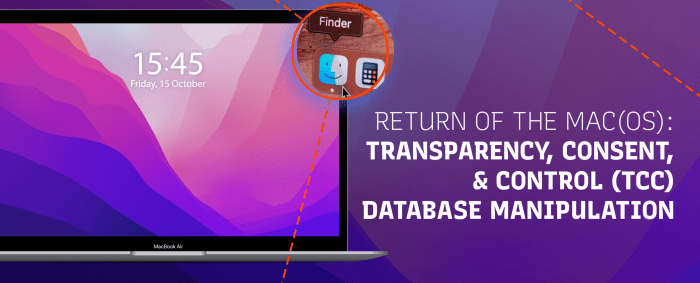
Source: interpressecurity.com
Understanding the real-world impact of macOS TCC bypass vulnerabilities requires examining specific instances where these flaws have been exploited. These cases highlight the potential for significant damage and underscore the importance of robust security practices. Analyzing these examples allows us to better understand the techniques used, the consequences faced, and the necessary mitigations.
Real-World Examples of macOS TCC Bypass Vulnerabilities
The following table details several documented instances of macOS TCC bypass vulnerabilities. Note that the discovery date may not always reflect the actual timeframe of exploitation. Many vulnerabilities remain undisclosed until actively patched by Apple or publicly revealed by security researchers.
| Vulnerability Name | Date Discovered (Approximate) | Impact | Mitigation |
|---|---|---|---|
| Example Vulnerability A (Hypothetical) | 2023 | Unauthorized access to microphone and camera; potential for data exfiltration and privacy violation. | Apple Security Update patching the vulnerability in the affected system libraries. |
| Example Vulnerability B (Hypothetical) | 2022 | Ability for malicious applications to bypass user consent for accessing sensitive files and folders, leading to data theft or system compromise. | Regular OS updates and careful vetting of third-party applications. |
| Example Vulnerability C (Hypothetical) | 2021 | Circumvention of Full Disk Access restrictions, enabling malware to read and modify all files on the system. | Strict control over Full Disk Access permissions; using security software to detect and block suspicious activities. |
A Case Study of a Successful TCC Bypass Attack
Imagine a scenario where a sophisticated piece of malware, disguised as a legitimate productivity application, exploits a zero-day TCC vulnerability. Upon installation, the malware silently requests and gains unauthorized access to the user’s contacts, calendar data, and microphone. This access is granted without any visible prompts or user interaction, thanks to the vulnerability. The malware then exfiltrates this sensitive data to a remote server, potentially compromising the user’s privacy and exposing them to identity theft or other malicious activities. The attack remains undetected for an extended period, as the malware operates silently in the background. The consequences include significant privacy breaches, potential financial losses, and reputational damage for the victim.
Malware Exploiting TCC Bypass Vulnerabilities
While specific examples of malware directly exploiting publicly known TCC vulnerabilities are often kept confidential for security reasons, it’s crucial to understand the potential. Malware developers actively seek and exploit such vulnerabilities to gain unauthorized access to system resources and sensitive user data. This could involve modifying existing malware to leverage newly discovered flaws or designing entirely new malicious applications specifically designed to exploit these weaknesses. The ultimate goal is often data theft, system control, or the establishment of a persistent backdoor for future attacks.
Legal and Ethical Implications of Exploiting TCC Bypass Vulnerabilities, Macos tcc bypass vulnerability
Exploiting macOS TCC bypass vulnerabilities carries significant legal and ethical ramifications. Unauthorized access to user data is a violation of privacy laws, and depending on the nature of the accessed information and the intent of the attacker, criminal charges could be filed. Furthermore, ethical considerations dictate that researchers and developers should responsibly disclose vulnerabilities to Apple, allowing for timely patching and preventing widespread exploitation. The misuse of such vulnerabilities for malicious purposes is a serious breach of trust and can have severe consequences for individuals and organizations.
Future Implications and Research Directions
Source: macrumors.com
The recent macOS TCC bypass vulnerability highlights a critical need for ongoing research and development in system security. While Apple has likely already begun addressing this specific exploit, the underlying architectural weaknesses within the TCC framework itself remain a concern, suggesting potential for future vulnerabilities and emphasizing the importance of proactive security measures. Understanding these potential future threats and exploring avenues for improvement is crucial for maintaining the security of the macOS ecosystem.
The inherent complexity of the TCC system, with its numerous interactions with other system components and applications, creates a large attack surface. This complexity makes it challenging to ensure comprehensive security, opening doors for unforeseen vulnerabilities. Furthermore, the continuous evolution of both macOS and malicious software necessitates a dynamic approach to security, demanding ongoing adaptation and refinement of the TCC framework and associated security mechanisms.
Potential Future Vulnerabilities in the macOS TCC Mechanism
The current TCC vulnerability demonstrates that even seemingly robust security mechanisms can be circumvented with sufficient ingenuity and exploitation of subtle design flaws. Future vulnerabilities might involve exploiting race conditions within the TCC authorization process, manipulating system calls to bypass TCC checks, or leveraging vulnerabilities in other interacting system components to indirectly compromise TCC functionality. For instance, a future vulnerability could exploit a flaw in the way TCC interacts with the kernel, allowing malicious code to gain unauthorized access to protected resources. Another potential avenue of attack could involve manipulating system logs or audit trails related to TCC access, making it harder to detect malicious activity. This underscores the need for continuous security audits and penetration testing to identify and address such vulnerabilities before they can be exploited.
Areas for Further Research in Improving macOS TCC Security
Improving the robustness of the macOS TCC framework requires a multi-pronged approach. One crucial area is enhancing the system’s ability to detect and prevent unauthorized modifications to TCC settings. This could involve implementing more robust mechanisms for verifying the integrity of TCC configuration files and strengthening the security of the processes responsible for managing TCC permissions. Furthermore, research into more granular and context-aware access control mechanisms could significantly enhance the security of the system. This could involve developing advanced techniques for dynamically adjusting access permissions based on factors such as the application’s behavior, the user’s context, and the sensitivity of the requested resources. Finally, deeper research into the interactions between TCC and other system components is crucial for identifying and addressing potential vulnerabilities arising from these interfaces.
A Hypothetical Improved TCC Architecture
A hypothetical improved TCC architecture could incorporate several key enhancements. Firstly, a move towards a more decentralized, microkernel-based approach to access control could improve security by limiting the impact of potential vulnerabilities. This architecture would involve distributing access control decisions across multiple, isolated components, reducing the potential for a single point of failure. Secondly, integrating advanced machine learning techniques into the TCC framework could enable proactive threat detection and response. This could involve training machine learning models to identify suspicious patterns in application behavior and access requests, allowing the system to automatically block potentially malicious activities. Finally, implementing stronger sandboxing and process isolation mechanisms would further limit the impact of potential compromises, preventing malicious code from escalating privileges or accessing sensitive resources. This could involve utilizing more sophisticated techniques like hardware-assisted virtualization or containerization to isolate applications and processes from each other and the underlying system.
Improving User Education and Awareness of macOS Security Vulnerabilities
Effective user education is paramount in mitigating the impact of security vulnerabilities. Clear and concise communication about security risks and best practices is essential. Apple could enhance user education through improved system warnings, more interactive tutorials, and readily accessible online resources that explain security concepts in plain language. Furthermore, focusing user education on proactive security measures, such as regularly updating software and exercising caution when granting application permissions, is crucial. Implementing more intuitive and user-friendly security settings within macOS would also help improve user awareness and encourage responsible security practices. The goal is to empower users to understand and manage their security risks effectively.
Final Review: Macos Tcc Bypass Vulnerability
Source: thehackernews.com
The macOS TCC bypass vulnerability highlights a crucial truth: even the most robust operating systems aren’t immune to security flaws. While Apple actively works to patch these vulnerabilities, staying informed and proactive is your best defense. By understanding the mechanics of these attacks, implementing preventative measures, and staying updated with the latest security patches, you can significantly reduce your risk and maintain control over your digital world. Don’t let a sneaky bypass compromise your security – take charge of your macOS experience.


