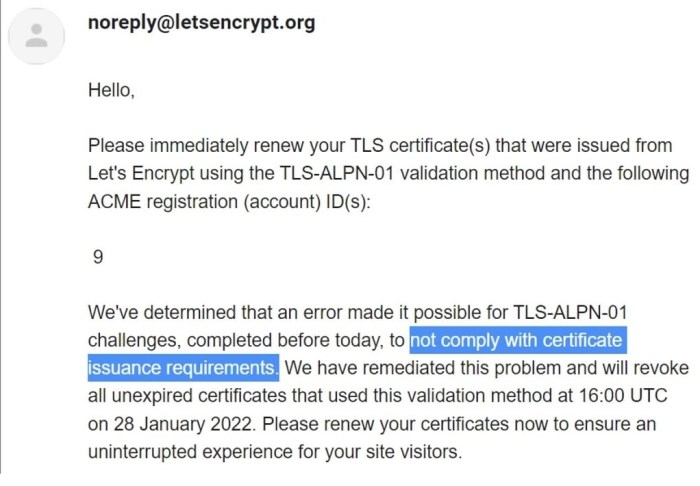
Lets encrypt 6 day certificates – Let’s Encrypt 6-day certificates: Sounds like a fleeting romance, right? But these short-lived digital keys are actually a serious player in the world of website security. Think of them as the ultimate commitment-phobe of SSL/TLS certificates, constantly renewing themselves to stay ahead of the ever-evolving threat landscape. This deep dive explores why these certificates exist, how they work, and whether they’re the right fit for your website.
We’ll unpack the technical reasons behind their short lifespan, comparing them to their longer-lived counterparts. We’ll also explore the practical implications for website owners, from the increased frequency of renewals to the potential benefits in enhanced security. Get ready to navigate the world of fleeting certificates and discover if they’re the perfect match for your digital needs.
Understanding Let’s Encrypt 6-Day Certificates
Source: https.in
Let’s Encrypt, the wildly popular free, automated, and open certificate authority, offers certificates with varying lifespans. While their standard certificates are valid for 90 days, a lesser-known option exists: the 6-day certificate. This shorter lifespan might seem unusual, but it serves a specific purpose and addresses particular technical challenges. Let’s delve into the specifics of these short-lived digital keys.
Reasons for Issuing 6-Day Certificates
The primary reason for Let’s Encrypt’s 6-day certificates lies in the need for rapid certificate turnover in dynamic environments. Think of situations where server configurations change frequently, such as during continuous integration and continuous deployment (CI/CD) pipelines. With frequent updates and deployments, using a longer-lived certificate could lead to inconsistencies and potential security vulnerabilities if the certificate isn’t promptly updated to reflect the new configuration. These short certificates enable a smoother workflow for rapid deployments and minimize security risks associated with outdated certificates. They are particularly useful in automated processes where frequent certificate renewals are easily handled.
Technical Limitations and Shorter Lifespans, Lets encrypt 6 day certificates
Several technical factors contribute to the necessity of shorter certificate lifespans. The core issue revolves around the challenge of maintaining consistent cryptographic keys and configurations within rapidly changing environments. Frequent updates, especially in automated systems, demand a mechanism to ensure that certificates always reflect the current server state. Using a 90-day certificate would introduce a window of vulnerability if a server configuration change occurs before the renewal. The 6-day certificate minimizes this window, providing a more secure approach for environments characterized by high dynamism.
Comparison of 6-Day and Longer-Lived Let’s Encrypt Certificates
Let’s Encrypt’s 90-day certificates are the standard, offering a balance between security and administrative overhead. The renewal process, while automated, still requires some management. 6-day certificates, on the other hand, demand more frequent renewals, increasing the automation demands on the system. This higher renewal frequency reduces the window of vulnerability in constantly changing environments, making them ideal for CI/CD pipelines and other dynamic situations. However, the increased automation requirement might be a challenge for less sophisticated systems.
Obtaining a 6-Day Certificate Using the Let’s Encrypt Client
Obtaining a 6-day certificate uses the same client as longer-lived certificates, primarily `certbot`. The key difference lies in specifying the desired certificate lifespan. While the exact command-line options might vary slightly depending on your certbot version and configuration, the core principle remains the same: you will need to use flags to specify the short certificate duration. Consult the `certbot` documentation for precise instructions tailored to your specific setup. The process involves the usual steps of domain validation, and then the certificate issuance. The crucial step is specifying the short validity period during the issuance process. This typically involves a flag like `–days` or a similar option within the `certbot` command.
Let’s Encrypt Certificate Validity Periods
| Certificate Type | Validity Period | Renewal Frequency | Advantages/Disadvantages |
|---|---|---|---|
| 6-Day Certificate | 6 days | Every 6 days | Ideal for highly dynamic environments; minimizes vulnerability window; increased automation overhead. |
| 90-Day Certificate (Standard) | 90 days | Every 90 days | Standard Let’s Encrypt offering; balance between security and administrative effort. |
Impact of Short Certificate Lifespans: Lets Encrypt 6 Day Certificates
The rapid rise of Let’s Encrypt’s 6-day certificates, while offering enhanced security through frequent renewal, introduces a new set of challenges for website administrators. This shorter lifespan, while beneficial for security, necessitates a shift in how we manage and deploy SSL/TLS certificates, impacting both security protocols and operational workflows. Understanding these implications is crucial for maintaining a secure and smoothly functioning online presence.
The frequent renewal inherent in short-lived certificates significantly strengthens security. By reducing the window of vulnerability, a compromised certificate’s impact is minimized. If a certificate is compromised, the damage is limited to a shorter timeframe, lessening the potential for data breaches or other malicious activities. This proactive approach to security, though demanding more frequent attention, offers a substantial advantage over longer-lived certificates that remain vulnerable for extended periods.
Security Implications of Frequent Renewals
Frequent certificate renewals enhance security by minimizing the potential damage from a compromised certificate. A shorter validity period reduces the time window during which a malicious actor could exploit a weakness. For example, if a 6-day certificate is compromised, the attacker has only six days to exploit it before the certificate is automatically replaced. This contrasts sharply with a certificate valid for one or two years, where the window of vulnerability is considerably larger. This proactive approach directly addresses the risk of prolonged exploitation.
Challenges Posed by Frequent Certificate Renewals
Managing the frequent renewal process for numerous certificates can be a significant administrative burden. Website administrators face the challenge of setting up automated renewal systems, monitoring for potential failures, and ensuring seamless integration with their existing infrastructure. Failure to do so can lead to website downtime, impacting user experience and potentially causing reputational damage. For instance, a large e-commerce platform with hundreds of subdomains would require a robust automated system to avoid service disruptions due to expired certificates.
Solutions to Mitigate Administrative Burden
Automating the certificate renewal process is paramount. This can be achieved through various methods, including using tools like Certbot, which offers automated renewal capabilities. These tools typically integrate with existing server configurations, making the process seamless and efficient. Regular testing and monitoring of the automated system are also critical to ensure it functions correctly. For example, setting up email alerts for failed renewals allows for timely intervention, preventing website downtime.
Automated Certificate Renewal and Deployment System Design
A robust automated system should include several key components: a scheduling mechanism (e.g., cron jobs), a certificate management tool (like Certbot), and a deployment mechanism to update the server configuration automatically. The system should also include error handling and logging capabilities to facilitate troubleshooting. The entire process should be designed for minimal human intervention, relying on automated scripts and checks to ensure uninterrupted service. Regular testing, ideally using a staging environment, is crucial before deploying updates to production servers.
Best Practices for Managing Certificates with Short Validity Periods
Implementing a robust monitoring system to track certificate expiration dates is crucial. Regular backups of certificates and keys are essential in case of unforeseen issues. Utilizing a centralized certificate management system can simplify the process of managing multiple certificates across various domains and subdomains. Furthermore, documenting the entire process, including the automated scripts and configuration details, is vital for maintenance and troubleshooting. This ensures that even with personnel changes, the system remains functional and secure.
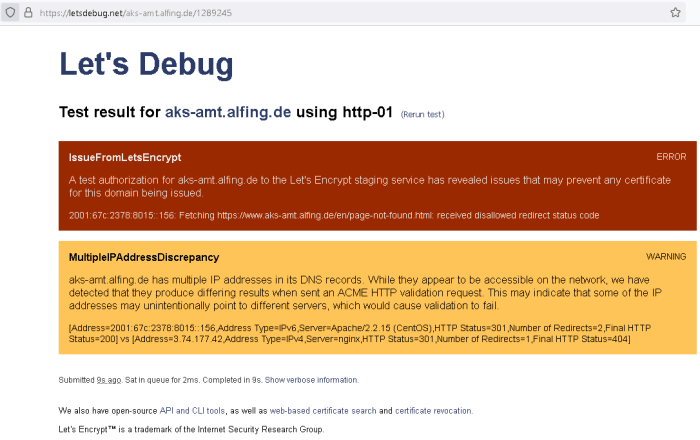
Use Cases for 6-Day Certificates
Source: discourse-cdn.com
Let’s Encrypt’s standard 90-day certificates are perfectly adequate for most websites. But sometimes, you need a shorter lifespan – enter the 6-day certificate. While seemingly limiting, these short-lived certs offer unique advantages in specific scenarios where rapid turnover and enhanced security are paramount. Think of it like this: a frequently changed password versus one that stays the same for years. The more frequent the change, the more secure your system becomes, even if it requires a little more maintenance.
These rapid-renewal certificates aren’t a replacement for standard certificates; they’re a specialized tool for specific situations. Their usefulness hinges on your ability to automate the renewal process, making the frequent updates seamless and largely invisible to the end-user. Let’s explore where these short-lived digital keys truly shine.
Scenarios Benefiting from 6-Day Certificates
6-day certificates find their niche in environments demanding frequent security updates. Imagine a temporary website for a short-term event, a highly sensitive internal application, or a situation where a compromise is particularly risky. The reduced window of vulnerability significantly minimizes the impact of any potential breach. A compromised 6-day certificate is only active for a short period, limiting the potential damage. The rapid turnover makes it far less attractive to attackers, as the reward is limited by the short lifespan.
Applications Requiring Frequent Certificate Renewal
The value of frequent certificate renewal is most apparent in high-stakes environments. Here’s a list of situations where the benefits are clearly evident:
Frequent certificate renewal significantly improves security by limiting the exposure window in case of compromise. This is particularly crucial for:
- Short-lived, event-based websites: Think temporary sites for conferences, webinars, or product launches. Once the event ends, the certificate expires, removing any potential lingering security risk.
- Highly sensitive internal applications: For applications handling critical data or financial transactions within a company’s intranet, frequent renewal minimizes the impact of a potential breach.
- Development and testing environments: Frequent certificate changes in these environments can help prevent issues that might arise from using outdated or compromised certificates.
- IoT devices with limited update capabilities: For devices where software updates are infrequent or difficult, frequent certificate renewal offers a layer of enhanced security.
Security Improvements with 6-Day Certificates
Using 6-day certificates directly enhances security by reducing the window of vulnerability. If a certificate is compromised, the damage is limited to a maximum of six days. This is particularly beneficial in scenarios where a breach could have severe consequences. The shorter lifespan also makes brute-force attacks significantly less effective, as attackers have less time to exploit a vulnerability. Think of it as constantly changing the locks on your house – the thief needs to find a new key every six days.
Suitability for Different Website Types
The suitability of 6-day certificates varies greatly depending on the website type and its associated risk profile.
Here’s a comparison of how well 6-day certificates fit different website types:
| Website Type | Suitability | Rationale |
|---|---|---|
| Personal Blog | Low | The overhead of managing frequent renewals outweighs the benefits for a low-risk site. |
| E-commerce Platform | Medium | While beneficial for enhanced security, the complexity of automation might be challenging. |
| High-Security Internal Application | High | The reduced window of vulnerability significantly outweighs the management overhead. |
| Temporary Event Website | High | Ideal for minimizing risk after the event concludes. |
Advantages and Disadvantages of 6-Day Certificates
Weighing the pros and cons is essential before adopting 6-day certificates. The decision depends heavily on your specific needs and infrastructure capabilities.
- Advantages: Significantly reduced window of vulnerability in case of compromise; improved security against brute-force attacks; ideal for temporary or high-risk applications; better suited for automated certificate management systems.
- Disadvantages: Requires robust automation to manage frequent renewals; increased administrative overhead if not automated; potential for disruptions if renewal fails; may not be suitable for all website types.
Alternatives and Comparisons

Source: githubassets.com
Let’s Encrypt’s 6-day certificates offer a unique approach to SSL/TLS, but they’re not the only game in town. Several other Certificate Authorities (CAs) and certificate management tools cater to the need for shorter-lived certificates, each with its own strengths and weaknesses. Understanding these alternatives is crucial for choosing the right solution for your specific needs. This section dives into the landscape of short-lived certificates, comparing pricing, features, and the overall experience.
Alternative Certificate Authorities Offering Shorter Lifespans
While Let’s Encrypt dominates the free and automated certificate market, other CAs offer shorter-lived certificates, though often at a price. These CAs might provide options for certificates with lifespans ranging from a few days to a few weeks, catering to specific security needs or deployment strategies that benefit from frequent rotation. For instance, some cloud providers offer integrated certificate management with shorter lifecycles as part of their managed services. The availability of these shorter lifespans and their exact durations will vary depending on the CA.
Pricing and Features Comparison of Short-Lived Certificate Providers
The pricing model for short-lived certificates differs significantly across providers. Let’s Encrypt remains the undisputed champion in the free certificate arena. However, commercial CAs offering shorter certificate lifespans typically charge on a per-certificate or per-domain basis, with pricing influenced by factors like the certificate type (e.g., DV, OV, EV), validation method, and the number of certificates required. Features beyond basic SSL/TLS encryption, such as enhanced validation, warranty coverage, and support levels, also affect the cost. Direct comparison requires checking individual CA pricing pages as these prices fluctuate. One might find that paying for a commercial solution becomes worthwhile if the automation and support outweigh the cost of the certificates themselves, particularly for organizations with large-scale deployments.
Certificate Validation Process Differences Across Providers
The validation process for certificates varies among providers. Let’s Encrypt’s automated validation, typically using DNS or HTTP challenges, is famously streamlined. Commercial CAs might employ more manual processes, particularly for higher assurance certificates like OV and EV, involving human review and verification of organizational information. This manual process often adds to the validation time, making it less suitable for scenarios requiring rapid certificate rotation. The level of automation and the speed of validation are key differentiators to consider when selecting a certificate provider.
Pros and Cons of Different Certificate Management Tools
Various certificate management tools help streamline the process of obtaining, installing, and renewing certificates. Tools range from simple command-line utilities to sophisticated platforms offering automation, monitoring, and integration with other infrastructure management tools. Simpler tools are often free and easy to use, ideal for small deployments. However, more advanced tools offer features like automated renewal, certificate lifecycle management, and centralized dashboards, becoming crucial for larger-scale deployments. The choice depends on your technical expertise, budget, and the complexity of your infrastructure. For example, Certbot is a popular and free client for Let’s Encrypt, offering automated certificate issuance and renewal. In contrast, paid solutions often provide more features, such as monitoring, alerting, and integrated support.
Certificate Lifecycle Flowchart: 6-Day vs. Longer-Lived Certificate
Imagine two flowcharts. The first depicts a 6-day certificate lifecycle. It shows a shorter cycle: Certificate Request -> Validation -> Issuance -> Deployment -> Monitoring -> Renewal Request (after 6 days) -> Validation -> Issuance -> Deployment… and repeats. The second chart shows a longer-lived certificate (e.g., 90 days). The overall process is similar, but the time between renewal requests is significantly longer. The key visual difference is the frequency of the ‘Renewal Request’ and subsequent steps. The 6-day certificate flowchart displays a more rapid and repetitive cycle, highlighting the need for robust automation to manage the frequent renewals effectively. The longer-lived certificate shows a more relaxed pace, with longer intervals between renewal activities.
Future of Short-Lived Certificates
The rapid evolution of cyber threats necessitates a constant reassessment of our security protocols. The rise of Let’s Encrypt’s 6-day certificates, while initially met with some skepticism, highlights a growing trend towards shorter certificate lifespans. This shift isn’t just a fleeting fad; it’s a strategic response to a landscape where breaches happen faster and vulnerabilities are exploited more aggressively. The future of digital security hinges, in part, on how we adapt to and embrace this shorter lifespan paradigm.
The shrinking lifespan of SSL/TLS certificates reflects a proactive approach to mitigating the risk of compromised keys. Longer-lived certificates, even with robust security measures, present a larger window of vulnerability. A compromised key, whether through a sophisticated attack or an internal breach, can have devastating consequences for a prolonged period if the certificate’s lifespan is extensive. Shorter lifespans significantly reduce the impact of such a breach. This is especially crucial in the face of increasingly sophisticated AI-powered attacks that can automate the process of identifying and exploiting vulnerabilities.
Potential Advancements in Certificate Technology
Advancements in automation and cryptographic agility will be key drivers in the wider adoption of shorter-lived certificates. Imagine a future where certificate issuance and renewal are completely automated, handled seamlessly by AI-driven systems. This would minimize the operational overhead associated with managing frequent renewals, making the switch to shorter lifespans far more practical for organizations of all sizes. Improved cryptographic algorithms, offering enhanced security with less computational overhead, would further facilitate the transition. This could involve advancements in post-quantum cryptography, preparing for a future where quantum computers could potentially break current encryption standards.
Emerging Challenges and Opportunities
Widespread adoption of 6-day certificates will undoubtedly present challenges. The increased frequency of renewals necessitates robust automation systems and careful monitoring to prevent lapses in security. Scalability will be a key consideration for Certificate Authorities (CAs) and organizations alike. However, the opportunities are equally significant. Reduced exposure to compromised keys translates to a significant reduction in the potential damage from security breaches. This strengthens the overall security posture of the internet, benefiting both businesses and individuals. Furthermore, the move towards shorter-lived certificates could stimulate innovation in automated security management, leading to more efficient and resilient systems.
Illustrative Depiction of Future Impact
Imagine a visual representation: Two timelines, one representing a website using a traditional, long-lived certificate (perhaps a year) and the other using a 6-day certificate. The long-lived certificate timeline is depicted with a thick, dark line, representing a larger vulnerability window. Several points along this line are marked with red “X”s, symbolizing potential breaches during its lifespan. The shorter-lived certificate timeline, however, is represented by a series of shorter, thinner, lighter lines, each representing a 6-day certificate. While there might be a few red “X”s on these shorter segments, the overall impact of each breach is minimized because the compromised period is significantly shorter. The visual contrast emphasizes how shorter lifespans drastically reduce the overall risk and damage associated with potential breaches, even if the frequency of breaches remains similar.
Final Conclusion
So, are Let’s Encrypt 6-day certificates the right choice for you? The answer, as with most things in life, is “it depends.” While the constant renewal might seem like a hassle, the enhanced security offered by these short-lived digital guardians is undeniable. Weigh the pros and cons, consider your website’s specific needs, and don’t be afraid to embrace the whirlwind romance of frequently renewing certificates. The digital world is fast-paced; your security should be too.


