Ldap exploit malware install – LDAP Exploit: Malware Install – sounds scary, right? It should. This isn’t your grandpappy’s network vulnerability. We’re talking about attackers using the Lightweight Directory Access Protocol (LDAP) – a system usually used for managing user information – as a sneaky backdoor to plant malware. Think of it as a digital Trojan horse, hiding in plain sight within your network’s directory services. We’ll unpack the methods, the impact, and most importantly, how to protect yourself from this insidious attack vector.
This deep dive explores the various ways malicious actors exploit weaknesses in LDAP servers to install malware. From compromised credentials to cleverly crafted attacks that bypass security measures, we’ll examine the techniques used and the devastating consequences that can follow. We’ll cover everything from identifying vulnerabilities to implementing robust prevention strategies and conducting thorough forensic analysis to uncover and neutralize these threats. Get ready to level up your cybersecurity game.
LDAP Vulnerability Overview
Lightweight Directory Access Protocol (LDAP) servers, while crucial for managing user identities and access control, are unfortunately susceptible to various vulnerabilities that can be exploited by malicious actors for malware installation. Understanding these weaknesses is critical for bolstering network security. This section explores common LDAP vulnerabilities, different attack types, and how attackers leverage them.
Common LDAP Vulnerabilities
Several vulnerabilities within LDAP servers allow attackers to gain unauthorized access and execute malicious code. These vulnerabilities often stem from weak configurations, outdated software, or insufficient security practices. For instance, a lack of proper authentication and authorization mechanisms can leave the server open to various attacks. Similarly, unpatched vulnerabilities in the LDAP server software itself can be exploited.
Types of LDAP Attacks
Attackers employ a range of techniques to exploit LDAP vulnerabilities. These include:
- Anonymous Bind Attacks: These attacks exploit the lack of authentication required to access certain LDAP server resources. An attacker can leverage this to retrieve sensitive information or even modify directory entries.
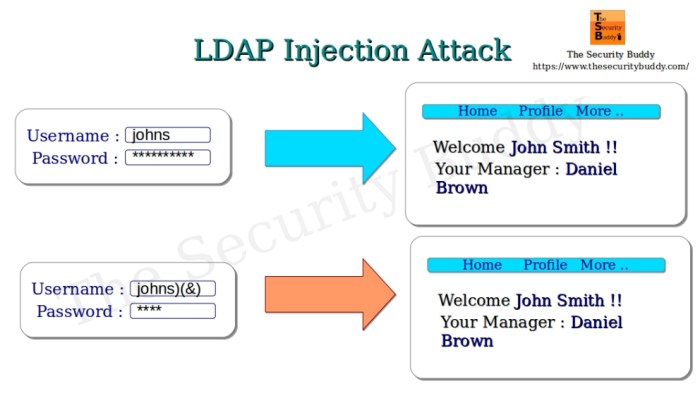
- Injection Attacks: Similar to SQL injection, LDAP injection involves injecting malicious code into LDAP queries. This can lead to unauthorized data access or modification.
- Denial-of-Service (DoS) Attacks: These attacks aim to overwhelm the LDAP server, making it unavailable to legitimate users. This can be achieved through various techniques, including flooding the server with requests.
- Man-in-the-Middle (MitM) Attacks: Attackers intercept communication between clients and the LDAP server, potentially capturing credentials or injecting malware into the communication stream.
Malware Installation via LDAP Exploits
Attackers can leverage compromised LDAP servers as a foothold for malware installation. For example, an attacker might inject malicious code into a directory entry that is then accessed by a legitimate user. This code could then execute on the user’s system, installing malware. Alternatively, attackers could modify the server’s configuration to redirect users to malicious websites or download malware.
LDAP Vulnerability Comparison
The following table compares various LDAP vulnerabilities based on their severity and exploitation methods.
| Vulnerability Type | Description | Severity | Exploitation Method |
|---|---|---|---|
| Anonymous Bind | Lack of authentication allows unauthorized access. | High | Exploiting weak authentication mechanisms. |
| LDAP Injection | Injecting malicious code into LDAP queries. | High | Crafting malicious LDAP queries. |
| Unpatched Server | Exploiting known vulnerabilities in the LDAP server software. | Critical | Leveraging publicly known exploits. |
| Improper Access Control | Insufficient authorization controls allow unauthorized modifications. | Medium to High | Exploiting weak access control lists (ACLs). |
Malware Installation Techniques via LDAP
LDAP, while designed for directory services, can become a sneaky backdoor for malware if vulnerabilities exist. Attackers exploit these weaknesses to install malicious code, often leveraging compromised credentials to slip past security defenses. This section details the methods employed and the role of compromised accounts in this malicious process.
LDAP-based malware installations rely on manipulating the server’s functionality to execute malicious code or deploy malicious files. This differs significantly from traditional methods, often leveraging the inherent trust placed in the LDAP server itself.
Compromised Credentials in LDAP Malware Deployments
Access to an LDAP server, even with limited privileges, can be a powerful tool for attackers. Compromised credentials, obtained through phishing, brute-force attacks, or other means, provide the necessary keys to unlock malicious actions. With valid credentials, attackers can modify existing LDAP entries, adding malicious scripts or commands to be executed by unsuspecting users or applications that query the directory. For instance, an attacker might modify a user’s login script to download and execute a malicious payload upon login. The seemingly legitimate LDAP server becomes the unsuspecting conduit for the malware.
LDAP Bypass of Security Measures
Attackers cleverly use LDAP to sidestep security controls. They might leverage vulnerabilities in the LDAP server itself, such as insecure configurations or unpatched software, to inject malicious code. This could involve exploiting known vulnerabilities to execute arbitrary commands or gain unauthorized access to sensitive data. Another technique involves using LDAP to manipulate authentication processes, potentially bypassing multi-factor authentication or other security layers. By modifying user attributes or creating fake accounts, attackers can create a foothold within the network and then use this to deploy further malware.
LDAP Malware Installation Flowchart, Ldap exploit malware install
The following illustrates a typical LDAP-based malware installation:
Imagine a flowchart. It begins with the attacker gaining access to compromised credentials (e.g., through a phishing campaign). This leads to a connection to the vulnerable LDAP server. The attacker then uses these credentials to modify a specific LDAP entry, for example, adding a malicious script path to a user’s profile configuration. This modified entry is then accessed by a legitimate user or application, which unknowingly executes the malicious script. The script then downloads and installs the actual malware payload onto the victim’s system. Finally, the malware establishes a command-and-control connection to the attacker, allowing for further actions.
Impact and Consequences of LDAP Exploits
Source: medium.com
LDAP exploits, when successful, can unleash a cascade of devastating consequences for organizations. The breach of this often-overlooked directory service can lead to significant data loss, system compromise, and substantial financial repercussions, impacting an organization’s reputation and operational capabilities. The severity of the impact depends heavily on the specific vulnerability exploited, the type of malware deployed, and the organization’s security posture.
The consequences of a successful LDAP exploit and subsequent malware installation are far-reaching and can significantly affect the CIA triad: Confidentiality, Integrity, and Availability. Compromised LDAP servers can expose sensitive data, allowing attackers to modify critical information or disrupt services, leading to operational downtime and financial losses. The ramifications extend beyond immediate technical issues, potentially impacting legal compliance, customer trust, and shareholder confidence.
Data Integrity, Confidentiality, and Availability Impacts
A successful LDAP exploit directly compromises the integrity, confidentiality, and availability of data within an organization. Attackers can alter directory entries, granting themselves unauthorized access or manipulating user permissions. Confidential information, such as employee details, customer records, and internal network configurations, becomes vulnerable to exposure. Moreover, the disruption of LDAP services can render critical applications and systems inaccessible, leading to significant downtime and operational disruptions. The cascading effect of these breaches can cripple an organization’s ability to function effectively.
Real-World Examples of LDAP Exploits Leading to Security Breaches
While specific details of many LDAP-related breaches are often kept confidential for security reasons, numerous instances demonstrate the potential for significant damage. For example, imagine a scenario where an attacker exploits a vulnerability in an organization’s LDAP server to gain administrative privileges. This allows them to modify user accounts, granting themselves access to sensitive systems and data. They could then deploy ransomware, encrypting critical files and demanding a ransom for their release. This directly impacts data availability and potentially leads to significant financial loss and reputational damage. Another example could involve an attacker using a compromised LDAP server to launch further attacks against other systems within the network, creating a wider security breach. The attacker might leverage the compromised credentials obtained through the LDAP server to move laterally within the network, escalating privileges and gaining access to even more sensitive information.
Potential Impacts Categorized by Severity
The following list categorizes potential impacts based on severity, highlighting the wide-ranging consequences of successful LDAP exploits:
The following impacts illustrate the potential consequences, ranging from relatively minor disruptions to catastrophic failures. Understanding these potential outcomes is crucial for implementing effective security measures.
- High Severity:
- Complete data loss due to ransomware or data deletion.
- System compromise leading to complete operational shutdown.
- Significant financial loss due to ransomware payments, legal penalties, and reputational damage.
- Large-scale identity theft impacting numerous users.
- Medium Severity:
- Partial data loss or corruption.
- Compromise of sensitive user accounts.
- Service disruptions leading to temporary downtime.
- Unauthorized access to confidential data.
- Low Severity:
- Minor data inconsistencies.
- Limited service interruptions.
- Detection of unauthorized access attempts.
Mitigation and Prevention Strategies
LDAP vulnerabilities, while offering attackers a sneaky route into your systems, aren’t insurmountable. Robust security practices can significantly reduce your risk of exploitation. By implementing a multi-layered approach focusing on authentication, authorization, network security, and regular audits, organizations can create a significantly more resilient defense against LDAP-based attacks.
Proactive security is key to preventing LDAP exploits. This involves implementing a combination of technical controls and security policies to minimize the attack surface and enhance the overall security posture of your LDAP infrastructure.
Strong Authentication and Authorization
Strong authentication ensures only authorized users can access your LDAP server. This means moving beyond basic passwords and implementing multi-factor authentication (MFA), which adds an extra layer of security by requiring multiple forms of verification, such as a password and a one-time code from a mobile app. Furthermore, robust password policies, including enforced complexity and regular changes, are crucial. Authorization, on the other hand, controls what authenticated users can *do* within the LDAP directory. Implementing the principle of least privilege—granting users only the access rights necessary for their roles—significantly limits the potential damage from a compromised account. For instance, a help desk user shouldn’t have the same permissions as a system administrator.
Firewall and Intrusion Detection System (IDS) Configuration
Firewalls act as the first line of defense, filtering network traffic and blocking unauthorized access attempts. Configuring your firewall to allow only necessary LDAP traffic—typically on port 389 (or 636 for LDAPS, the secure version)—is crucial. Intrusion Detection Systems (IDS) actively monitor network traffic for malicious activity, including known LDAP attack patterns. A well-configured IDS can detect and alert you to suspicious LDAP requests, allowing for timely intervention and preventing successful exploitation. Consider implementing an intrusion prevention system (IPS) for automated responses to identified threats. For example, an IPS could automatically block an IP address exhibiting malicious LDAP activity.
Security Measures Checklist
Implementing a comprehensive security strategy requires a multi-faceted approach. The following checklist highlights essential security measures:
A robust security plan isn’t a one-time event; it requires ongoing monitoring, updates, and adaptation to the evolving threat landscape. Regular security audits and penetration testing are vital to identify vulnerabilities before attackers do.
- Regular Security Audits and Penetration Testing: Identify and address vulnerabilities proactively.
- Strong Password Policies: Enforce complexity, length, and regular changes.
- Multi-Factor Authentication (MFA): Implement MFA for all LDAP users.
- Principle of Least Privilege: Grant only necessary access rights.
- Firewall Configuration: Restrict LDAP access to authorized sources and ports.
- Intrusion Detection/Prevention System (IDS/IPS): Monitor and block malicious LDAP activity.
- Regular Software Updates and Patching: Address known vulnerabilities promptly.
- LDAP Server Hardening: Configure the server to minimize its attack surface.
- Secure LDAP (LDAPS): Use LDAPS (port 636) for encrypted communication.
- Regular Backups: Enable rapid recovery from data loss or compromise.
Forensic Analysis of LDAP-Based Attacks: Ldap Exploit Malware Install
Source: thesecuritybuddy.com
Investigating an LDAP-based malware infection requires a methodical approach, combining network analysis with system forensics. Understanding the attacker’s techniques is crucial for effective remediation and prevention of future incidents. This involves meticulously tracing the malware’s actions from initial entry to its ultimate impact on the system.
Identifying the Malware Entry Point
Pinpointing the initial infection vector is paramount. This often involves examining LDAP server logs for suspicious queries or modifications. Analyzing network traffic around the time of the suspected infection, using tools like Wireshark, can reveal malicious LDAP bind requests or unexpected data transfers. Examining system logs, particularly those related to authentication and access control, can provide further clues. For example, unusual login attempts or modifications to user accounts can indicate the point of compromise. A thorough review of the LDAP directory itself is essential, searching for newly created accounts, modified attributes (like passwords or group memberships), or unexpected data entries that might suggest the malware’s presence.
Tracing Malware Actions Within the System
Once the entry point is identified, the next step is tracing the malware’s activities. This involves analyzing system logs for suspicious processes, registry modifications, and file system changes. Memory forensics, using tools like Volatility, can reveal malware processes running in memory, even if they’ve been deleted from the disk. Analyzing network connections can help identify command-and-control (C2) servers used by the malware. Analyzing the malware’s code, if a sample is obtained, will provide insight into its functionality, targets, and data exfiltration techniques. This often reveals the specific LDAP queries used by the malware to manipulate the directory or retrieve sensitive information. For instance, a malware might query for all users with specific attributes to target specific individuals or groups.
Recovering Compromised Data and Restoring System Integrity
Data recovery and system restoration are crucial final steps. This begins with identifying which data has been compromised. The extent of the compromise depends on the malware’s capabilities. Data might have been encrypted, exfiltrated, or deleted. If data has been encrypted, specialized decryption tools may be required, depending on the type of encryption used. If data has been exfiltrated, network traffic analysis may reveal the location of the stolen data. System integrity is restored by removing the malware, cleaning up malicious files and registry entries, and patching any vulnerabilities exploited by the attacker. This often involves reinstalling the operating system or critical system components. Regular backups are crucial for data recovery, and the restoration process should involve verifying the integrity of the restored system and data. Post-incident analysis should be conducted to understand the full scope of the attack and improve security measures to prevent future incidents. This may involve vulnerability scanning and penetration testing to identify and address any remaining weaknesses.
Case Studies of LDAP Exploits
Source: medium.com
LDAP vulnerabilities, while often overlooked, can serve as a critical entry point for malware into an organization’s network. Exploiting these weaknesses can lead to significant data breaches and operational disruptions. Examining real-world incidents helps highlight the methods used by attackers and the crucial steps needed for effective mitigation.
One notable example involves a 2018 attack on a large financial institution. The attackers leveraged a known vulnerability in the organization’s LDAP server, specifically a flaw in authentication that allowed for bypassing standard security checks. This vulnerability was not patched, despite being publicly known for several months. The attackers exploited this weakness to gain unauthorized access to the LDAP directory, enabling them to enumerate user accounts and extract sensitive information, including usernames, passwords, and employee details.
Attack Techniques
The attackers employed a multi-stage approach. First, they used automated tools to scan the organization’s network for vulnerable LDAP servers. Upon identifying the vulnerable server, they utilized a publicly available exploit to bypass authentication. Once inside the LDAP directory, they employed a custom-written script to extract user account data. This data was then used in subsequent attacks, including credential stuffing attempts against other internal systems. Finally, the extracted information facilitated the installation of malware capable of lateral movement and data exfiltration. This allowed the attackers to maintain persistent access to the network and exfiltrate sensitive data over an extended period.
Exploited Vulnerabilities
The primary vulnerability exploited was a known flaw in the LDAP server’s authentication mechanism. This flaw allowed attackers to bypass standard authentication protocols, effectively granting them unauthorized access to the directory. A secondary vulnerability was the lack of timely patching of the known vulnerability. The failure to implement appropriate security measures, including regular patching and vulnerability scanning, allowed the attackers to exploit this weakness. Furthermore, the lack of robust logging and monitoring hindered early detection of the attack.
Lessons Learned
This case study underscores the importance of proactive security measures. Regular patching and vulnerability scanning are crucial for preventing LDAP-based attacks. Robust logging and monitoring mechanisms are essential for early detection of malicious activity. Security awareness training for employees is also vital, as attackers often exploit human error to gain initial access. Finally, the incident highlights the need for a comprehensive incident response plan to minimize the impact of a successful attack. This includes procedures for containment, eradication, recovery, and post-incident analysis. The attackers’ ability to move laterally within the network also points to the need for robust network segmentation and access control policies.
Final Thoughts
So, LDAP Exploit: Malware Install isn’t just another tech buzzword; it’s a real and present danger. Understanding the vulnerabilities, the methods employed by attackers, and the potential impact is crucial for any organization. By implementing the mitigation strategies discussed – strengthening authentication, leveraging firewalls and intrusion detection systems, and maintaining a vigilant security posture – you can significantly reduce your risk. Remember, proactive defense is the best offense in the ever-evolving landscape of cybersecurity threats. Stay informed, stay vigilant, and stay safe.


