Hackers weaponize pentesting tools – it sounds like a scene from a cyberpunk thriller, right? But the reality is far more chilling. These tools, initially designed to identify vulnerabilities in systems, are increasingly being twisted into weapons by malicious actors. This isn’t just about technical prowess; it’s about the ethical gray area where the line between protecting systems and exploiting them blurs. We’ll delve into the dark side of cybersecurity, exploring how hackers repurpose these tools, the techniques they employ, and what you can do to protect yourself.
From network scanners morphing into stealthy intrusion tools to vulnerability assessment software becoming a precision-guided missile for data breaches, the misuse of pentesting tools is a growing threat. Understanding how these tools are weaponized is crucial for building stronger defenses. We’ll examine real-world examples, dissect attack scenarios, and ultimately equip you with the knowledge to navigate this complex landscape.
Types of Pentesting Tools Weaponized by Hackers
The world of cybersecurity is a constant arms race. Legitimate penetration testing tools, designed to identify vulnerabilities, are unfortunately also readily adaptable for malicious purposes. Understanding these tools, both their ethical applications and their potential for misuse, is crucial for bolstering our defenses. This section explores various types of pentesting tools and how they can be weaponized by malicious actors.
Categorization of Weaponized Pentesting Tools
Pentesting tools are incredibly diverse, each serving a specific purpose in the security assessment process. Understanding their categorization helps us grasp their potential for misuse. The following table organizes commonly used tools based on their function and illustrates their potential for malicious adaptation.
| Tool Name | Category | Common Uses | Potential for Weaponization |
|---|---|---|---|
| Nmap | Network Scanning | Identifying open ports, services, and operating systems on a network. Used for initial reconnaissance. | Used for large-scale network mapping to identify vulnerable systems for subsequent attacks. Can be used to evade detection through techniques like port scanning randomization. |
| Nessus | Vulnerability Assessment | Identifying known vulnerabilities in software and hardware. Provides a comprehensive security audit. | Hackers can leverage the vulnerability information identified by Nessus to launch targeted attacks, exploiting known weaknesses before they are patched. |
| Metasploit | Exploitation | Testing the exploitability of identified vulnerabilities. Provides a framework for launching and testing exploits. | A primary tool for launching sophisticated attacks. Hackers can modify existing exploits or create new ones to bypass security measures. |
| Wireshark | Packet Capture & Analysis | Capturing and analyzing network traffic to identify security flaws and malicious activity. Used for forensic analysis. | Used to intercept sensitive data, such as login credentials and financial information, from network traffic. Can be used to build sophisticated man-in-the-middle attacks. |
| Burp Suite | Web Application Security Testing | Identifying vulnerabilities in web applications, such as SQL injection and cross-site scripting (XSS). | Used to exploit vulnerabilities in web applications for data theft, unauthorized access, or website defacement. Can be used to launch sophisticated attacks against web services. |
Ethical Use of Pentesting Tools by Security Researchers
Ethical hackers, or penetration testers, use these same tools to proactively identify vulnerabilities before malicious actors can exploit them. They perform security assessments under contract, providing valuable insights to organizations to improve their security posture. For instance, a penetration tester might use Nmap to scan a company’s network, then use Nessus to identify vulnerabilities and finally Metasploit to test the exploitability of those vulnerabilities in a controlled environment, all while reporting their findings to the client to strengthen their security. This ethical use ensures that weaknesses are addressed before they can be weaponized by attackers.
Modifications for Malicious Purposes
Hackers often modify these tools to enhance their malicious capabilities. This can involve integrating evasion techniques to bypass intrusion detection systems (IDS) or antivirus software. They might also customize exploits to target specific vulnerabilities or combine multiple tools into automated attack scripts for increased efficiency. For example, a hacker might modify Metasploit to incorporate custom exploits targeting a newly discovered vulnerability in a specific application, or they might combine Nmap and Metasploit into a single script that automatically scans a network for vulnerable systems and then exploits them. The modifications can range from simple scripting changes to complex code rewrites, often focusing on stealth and automation.
Techniques for Weaponizing Pentesting Tools

Source: dreamstime.com
Hackers aren’t just using readily available pentesting tools; they’re weaponizing them, crafting sophisticated attacks by cleverly bypassing security measures and combining tools in unexpected ways. This involves a deep understanding of both the tools themselves and the vulnerabilities they exploit. It’s a cat-and-mouse game of constant evolution, with hackers adapting to new security protocols and defenses.
Methods for circumventing security measures often involve exploiting the blind spots in security systems. This isn’t about brute force; it’s about finesse and strategic application. Hackers might utilize techniques like obfuscation to disguise malicious code within seemingly benign scripts, or employ social engineering to trick users into granting access. The goal is to gain unauthorized access and control, often without triggering alarms.
Bypassing Security Measures
Hackers employ several techniques to evade detection while using pentesting tools. One common method is to modify the tools themselves, removing or altering identifying characteristics like unique signatures. This makes it harder for intrusion detection systems (IDS) and antivirus software to recognize the malicious activity. Another approach is to leverage vulnerabilities in the target system’s security infrastructure, exploiting weaknesses in firewalls, intrusion prevention systems (IPS), or even the operating system itself to slip past defenses. For example, a hacker might exploit a known zero-day vulnerability in a web server to gain initial access before deploying other tools. Finally, timing is crucial; attackers often operate during off-peak hours or periods of low network activity to reduce the chances of detection.
Combining Pentesting Tools for Enhanced Attacks
The real power lies in combining tools for synergistic effects. A lone tool might be easily detected, but a coordinated assault utilizing several tools can be far more devastating. Imagine a scenario where a hacker first uses Nmap to scan a network, identifying open ports and vulnerabilities. They then use Metasploit to exploit a weakness in a vulnerable service, gaining initial access. Finally, they employ tools like Mimikatz to harvest credentials and gain deeper access within the network. This layered approach increases the chances of success while making attribution far more difficult.
Hypothetical Attack Scenario: Weaponizing Nmap and Metasploit
Let’s consider a hypothetical attack against a small business. The attacker begins by using Nmap to perform a port scan of the target’s network. Nmap reveals an open port 3389 (Remote Desktop Protocol), a common vulnerability if not properly secured. This discovery provides a clear entry point. The attacker then uses Metasploit to craft an exploit targeting the vulnerable RDP service. This exploit is customized to bypass any basic authentication measures. Once the exploit is successful, the attacker gains remote access to the target machine. From there, they can deploy further tools to move laterally within the network, exfiltrate sensitive data, or install malware for persistent access. The potential outcomes range from data breaches and financial loss to complete system compromise and disruption of business operations. The speed and efficiency of this attack highlight the dangers of unpatched systems and poorly configured security measures.
Identifying Weaponized Pentesting Tools in an Attack
Spotting a malicious actor using a legitimate pentesting tool is like finding a needle in a digital haystack. The tools themselves are inherently benign; it’s their *application* that determines their intent. Understanding the subtle differences between legitimate security assessments and malicious attacks is crucial for effective incident response. This requires a keen eye for unusual patterns and a solid grasp of typical pentesting methodologies.
Identifying the weaponization of pentesting tools requires a multi-faceted approach, combining technical analysis with contextual awareness. The key is to look beyond the tools themselves and examine the broader context of the attack, including the attacker’s goals, techniques, and the overall impact on the victim’s systems. By understanding the digital fingerprints left behind, security professionals can effectively distinguish between legitimate security audits and malicious activities.
Indicators of Weaponized Pentesting Tools
Several indicators can point towards the malicious use of pentesting tools. These range from the timing and scope of the activity to the techniques employed and the overall impact on the system. A combination of these indicators is often necessary to build a conclusive case.
- Unusual Timing and Scope: Legitimate penetration testing is usually conducted during pre-agreed-upon times and within a defined scope. Suspicious activity outside these parameters, especially during off-hours or targeting unexpected systems, is a major red flag. For example, a scan targeting all systems across an organization at 3 AM is highly suspicious.
- Aggressive Scanning Techniques: While pentests might involve scanning, malicious actors often employ aggressive techniques, such as high-frequency port scans or vulnerability scans without consent, aiming to overwhelm systems or quickly identify exploitable weaknesses. Legitimate scans are usually more targeted and less intense.
- Exploitation Attempts: Legitimate penetration testing might involve vulnerability identification, but it stops short of actual exploitation. Malicious actors, however, will actively exploit discovered vulnerabilities to gain unauthorized access or deploy malware.
- Data Exfiltration: The transfer of large amounts of sensitive data outside the organization’s network is a clear indicator of a malicious attack. Legitimate pentesting activities might involve limited data access for testing purposes, but this is always carefully controlled and documented.
- Persistence Mechanisms: Malicious actors often try to establish persistent access to compromised systems. This could involve installing backdoors, creating scheduled tasks, or modifying system configurations. Legitimate pentests typically avoid leaving any persistent access behind.
Comparing Digital Footprints
The digital footprints left by legitimate pentesting and malicious activities using similar tools can be surprisingly different. A crucial distinction lies in the intent and the actions taken.
| Characteristic | Legitimate Pentesting | Malicious Activity |
|---|---|---|
| Target Scope | Defined and limited to agreed-upon systems. | Broad and often indiscriminate, targeting numerous systems. |
| Scanning Intensity | Moderate, focused on specific vulnerabilities. | Aggressive, high-frequency scans, potentially causing denial-of-service. |
| Exploitation | Vulnerabilities identified but not exploited without explicit authorization. | Active exploitation of vulnerabilities to gain unauthorized access. |
| Data Access | Limited access to specific data for testing purposes, with strict controls and documentation. | Unauthorized access and exfiltration of sensitive data. |
| Persistence | No persistent access left behind after the test. | Installation of backdoors and other mechanisms for maintaining access. |
Network Traffic Analysis for Detection
Network traffic analysis is invaluable in identifying the use of weaponized pentesting tools. By examining network flows, security analysts can identify suspicious patterns and correlate them with other indicators of compromise.
Analyzing network traffic for suspicious patterns, such as unusual connections to known malicious IP addresses or the use of obfuscation techniques, is crucial. Furthermore, observing high volumes of data transfer to external servers, particularly during unusual hours, can signal data exfiltration. Correlating this information with other indicators, such as log entries and system events, provides a more complete picture of the attack. For instance, a sudden surge in traffic to a command-and-control server, coupled with unusual activity on a database server, strongly suggests a malicious intrusion.
Mitigation Strategies Against Weaponized Pentesting Tools
The weaponization of legitimate security tools poses a significant threat to organizations of all sizes. Understanding how these tools are misused and implementing robust mitigation strategies are crucial for minimizing risk and protecting valuable assets. A multi-layered approach, encompassing proactive security measures and reactive incident response plans, is the most effective defense.
Effective mitigation requires a proactive and layered security approach. This involves strengthening foundational security practices, regularly assessing vulnerabilities, and implementing robust access controls. By combining these strategies, organizations can significantly reduce their exposure to attacks leveraging weaponized pentesting tools.
Security Best Practices to Reduce Exploitation Risk
Implementing a range of security best practices significantly reduces the likelihood of successful exploitation via weaponized pentesting tools. These practices act as a layered defense, making it harder for attackers to gain a foothold and escalate privileges.
- Regular Software Updates and Patching: Promptly applying security patches to all software, including operating systems, applications, and firmware, is paramount. Outdated software often contains known vulnerabilities that attackers exploit. Automated patching systems can significantly improve the speed and efficiency of this process.
- Principle of Least Privilege: Users and processes should only have the minimum necessary access rights required to perform their tasks. This limits the damage an attacker can inflict even if they compromise a single account.
- Network Segmentation: Dividing the network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the attacker’s access to other parts of the network is restricted.
- Intrusion Detection and Prevention Systems (IDPS): Deploying IDPS solutions allows for real-time monitoring of network traffic and system activity, enabling early detection and response to malicious activity. These systems can identify suspicious patterns indicative of weaponized pentesting tool usage.
- Security Information and Event Management (SIEM): SIEM systems collect and analyze security logs from various sources, providing a centralized view of security events. This allows for the identification of potential threats and security incidents. Real-time alerts are crucial for rapid response.
- Regular Security Awareness Training: Educating employees about phishing scams, social engineering tactics, and safe internet practices significantly reduces the risk of human error, a common entry point for attackers.
- Data Loss Prevention (DLP): Implementing DLP measures prevents sensitive data from leaving the organization’s control, even if an attacker gains access to systems. This includes encryption, access controls, and monitoring of data transfer.
Importance of Regular Security Audits and Vulnerability Assessments, Hackers weaponize pentesting tools
Regular security audits and vulnerability assessments are essential for identifying and mitigating weaknesses in an organization’s security posture. These assessments provide a comprehensive overview of existing vulnerabilities and help prioritize remediation efforts.
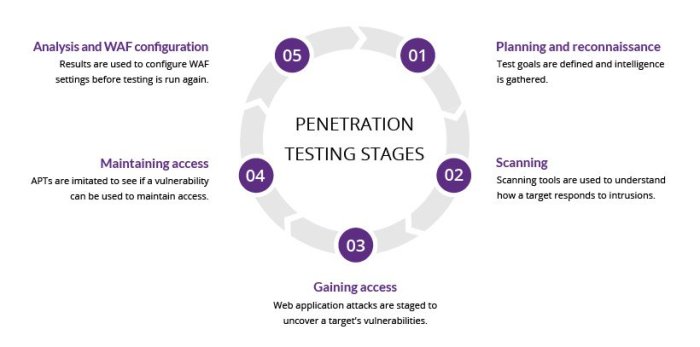
Penetration testing, when conducted by qualified ethical hackers, simulates real-world attacks to identify vulnerabilities that automated scanners might miss. This proactive approach allows organizations to address security weaknesses before they can be exploited by malicious actors. Regular vulnerability scans using automated tools provide a baseline understanding of known vulnerabilities and aid in prioritizing patching efforts. The combination of these methods offers a robust approach to identifying potential attack vectors.
Strong Password Policies and Multi-Factor Authentication
Strong password policies and multi-factor authentication (MFA) are fundamental security controls that significantly enhance the protection against unauthorized access. These measures make it exponentially harder for attackers to gain access to accounts, even if they possess stolen credentials.
Implementing strong password policies, which include requirements for password length, complexity, and regular changes, reduces the likelihood of easily guessed or cracked passwords. MFA adds an extra layer of security by requiring users to provide multiple forms of authentication, such as a password and a one-time code from a mobile app or hardware token. This significantly reduces the risk of unauthorized access, even if an attacker compromises a user’s password.
Case Studies of Real-World Attacks

Source: simeononsecurity.com
The weaponization of legitimate penetration testing tools represents a significant threat in the cybersecurity landscape. These tools, designed to identify vulnerabilities, can be easily misused by malicious actors to exploit those same weaknesses, leading to devastating consequences. Examining real-world attacks highlights the effectiveness of these tactics and underscores the need for robust security measures. Understanding these case studies provides valuable insights into attacker methodologies and informs the development of more effective defensive strategies.
Notable Attacks Involving Weaponized Pentesting Tools
The following table details three significant cyberattacks that leveraged weaponized penetration testing tools. Analyzing these incidents reveals common attack vectors and highlights the critical need for proactive security measures.
| Attack Name | Tools Used | Techniques | Impact |
|---|---|---|---|
| NotPetya (2017) | EternalBlue (exploit for Microsoft Windows), PSExec (remote command execution), Mimikatz (credential theft) | Supply chain attack leveraging a vulnerability in Ukrainian accounting software. The malware spread rapidly through networks using EternalBlue and PSExec. Mimikatz was used to steal credentials, escalating privileges and expanding the attack’s reach. | Widespread disruption across multiple industries globally, estimated billions of dollars in damages. Significant operational downtime and data loss. |
| Stuxnet (2010) | Various custom-built tools, potentially incorporating elements of commercial security software. Specific tools are not publicly known in detail. | Advanced Persistent Threat (APT) targeting Iranian nuclear facilities. The malware used a combination of techniques, including zero-day exploits, to damage centrifuges and disrupt the enrichment process. This involved manipulating industrial control systems (ICS). | Significant setback to Iran’s nuclear program. Demonstrated the potential for highly sophisticated cyberattacks to target critical infrastructure. |
| SolarWinds Supply Chain Attack (2020) | Orion platform (SolarWinds’ network management software) compromised and used to distribute malware (SUNBURST). | Supply chain attack targeting SolarWinds customers. The malware was embedded within updates to the Orion platform, allowing attackers to gain access to numerous organizations’ networks. Further lateral movement and data exfiltration followed. | Compromise of numerous government agencies and private sector organizations. Extensive data breaches and intelligence gathering. Significant damage to reputation and trust. |
Lessons Learned and Future Security Strategies
These case studies demonstrate that sophisticated attackers can effectively weaponize readily available penetration testing tools. The common thread is the exploitation of vulnerabilities in software, often through supply chain attacks. Effective mitigation requires a multi-layered approach focusing on proactive vulnerability management, robust security awareness training, and the implementation of advanced threat detection and response capabilities. Regular security audits, penetration testing from trusted sources, and incident response planning are crucial for minimizing the impact of such attacks. Furthermore, strong supply chain security practices are essential to prevent the compromise of software updates and other critical components. The development and implementation of more secure software design principles, coupled with effective threat intelligence sharing, are critical elements in mitigating future risks.
The Ethical Implications of Pentesting Tools: Hackers Weaponize Pentesting Tools
The dual-edged sword of penetration testing tools presents a significant ethical challenge. These tools, designed to uncover vulnerabilities and strengthen cybersecurity, can easily be misused for malicious purposes, highlighting the crucial need for responsible development and deployment. The line between ethical security research and malicious hacking often blurs, demanding a clear understanding of individual responsibilities and the potential consequences of actions.
The development and use of pentesting tools raise several ethical considerations. The potential for misuse, leading to data breaches, system compromise, and financial losses, necessitates a robust ethical framework guiding their creation and application. This framework should prioritize responsible disclosure, transparency, and adherence to legal and professional standards. Ignoring these ethical considerations can lead to significant harm, undermining trust and damaging reputations.
Responsibilities of Security Researchers Versus Malicious Actors
Security researchers have a professional obligation to use pentesting tools responsibly. This involves obtaining explicit permission before conducting any security assessments, adhering to strict non-disclosure agreements, and promptly reporting vulnerabilities to the affected parties. Their primary goal is to improve security, not to cause damage or exploit weaknesses for personal gain. Malicious actors, conversely, disregard these ethical principles. They use similar tools to breach systems, steal data, or disrupt services for personal profit or malicious intent. The key difference lies in intent and adherence to established ethical guidelines and legal frameworks. Researchers prioritize remediation, while malicious actors prioritize exploitation.
Responsible Disclosure Practices and Ethical Hacking
Responsible disclosure is a cornerstone of ethical hacking. It involves a structured process of identifying a vulnerability, privately reporting it to the affected party, allowing them time to address the issue, and then publicly disclosing the vulnerability after a reasonable period. This approach ensures that vulnerabilities are addressed without causing widespread harm. The timeline and specific steps may vary depending on the severity of the vulnerability and the agreement between the researcher and the affected organization. For example, a critical vulnerability that could lead to widespread data breaches might require immediate notification, while a less severe vulnerability could allow for a longer timeframe for remediation. Ethical hacking promotes a proactive approach to cybersecurity, fostering collaboration between security researchers and organizations to enhance overall security posture. Organizations should establish clear communication channels and processes for receiving and addressing vulnerability reports.
Conclusive Thoughts
Source: imperva.com
The weaponization of pentesting tools highlights a critical issue in cybersecurity: the double-edged sword of security research. While these tools are essential for identifying vulnerabilities and strengthening defenses, their potential for misuse is undeniable. Staying vigilant, adopting robust security practices, and understanding the tactics of malicious actors are paramount. The fight against cybercrime is an ongoing battle, and awareness is our strongest weapon.


