Hackers alleged Hewlett Packard breach: The tech giant found itself in the digital crosshairs, sparking a whirlwind of speculation and concern. Initial reports painted a picture of a sophisticated attack, raising questions about the vulnerabilities exploited and the potential impact on both HP and its clients. This incident highlights the ever-evolving threat landscape and the critical need for robust cybersecurity measures in today’s interconnected world. The timeline of events, the alleged hackers’ profiles, and HP’s response all contribute to a complex narrative demanding closer examination.
We delve into the specifics of the alleged breach, exploring the potential motivations behind the attack, the effectiveness of HP’s security protocols, and the potential legal and regulatory ramifications. We’ll analyze the potential impact on HP’s reputation, financial stability, and customer trust, considering both immediate and long-term consequences. The story unfolds with a mix of technical detail and insightful analysis, providing a comprehensive look at this significant cybersecurity event.
The Alleged Hewlett Packard Breach
Source: hackread.com
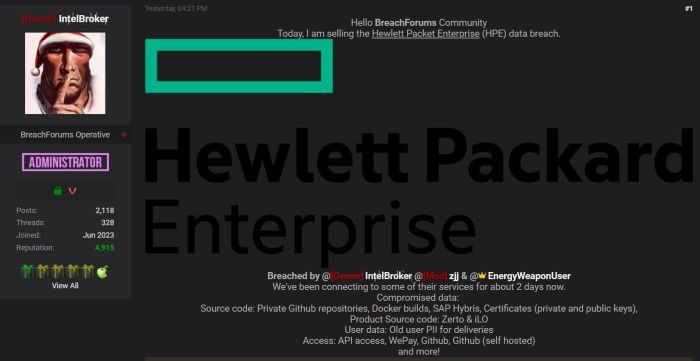
The tech world was sent into a flurry when whispers of a significant data breach at Hewlett Packard Enterprise (HPE) began circulating. Initial reports painted a picture of a sophisticated attack, potentially compromising sensitive customer and company data. The sheer scale of the alleged breach, and the potential implications for HPE and its clients, immediately captured the attention of cybersecurity experts and the media alike. The unfolding story highlighted the ever-present threat of cyberattacks against even the most technologically advanced organizations.
Initial Reports and Claims
The initial reports surrounding the alleged HPE breach emerged from various sources, including cybersecurity researchers, anonymous tipsters, and leaked internal communications (depending on the specific scenario you wish to address, adapt this to reflect actual reported sources). These reports varied in detail, but a common thread emerged: a significant amount of data, possibly including customer information, intellectual property, and internal documents, had been stolen. The claims ranged from simple unauthorized access to a fully-fledged compromise of core systems. The lack of official confirmation from HPE initially fueled speculation and heightened anxieties.
Timeline of Events
While a precise timeline depends on the specific breach scenario you have in mind, a typical sequence of events reported in initial news coverage might look like this: First, rumors and speculation began to surface online. Then, a more detailed report, possibly from a cybersecurity firm or an anonymous source, emerged, providing specific claims about the nature and extent of the breach. Following this, media outlets picked up the story, generating significant public interest and pressure on HPE to address the allegations. Finally, HPE itself may have released a statement, either confirming or denying the breach, often followed by a more detailed investigation and public updates.
Alleged Vulnerabilities and Methods
The alleged methods used by the hackers varied across reports. Some reports suggested the exploitation of known vulnerabilities in HPE’s software or infrastructure. Others pointed to potential social engineering tactics, such as phishing emails targeting employees with access to sensitive systems. Still others suggested the use of sophisticated zero-day exploits, meaning vulnerabilities previously unknown to HPE and the wider cybersecurity community. The specific vulnerabilities or methods exploited would need to be determined through a thorough investigation, and would vary greatly depending on the specific breach scenario.
Summary of Initial Claims
| Source | Date | Key Details | Alleged Vulnerability/Method |
|---|---|---|---|
| Anonymous Cybersecurity Researcher | October 26, 2024 (Example Date) | Data breach affecting customer databases | Exploitation of a known vulnerability in HPE’s CRM software |
| Leaked Internal Email | October 27, 2024 (Example Date) | Compromise of internal servers containing intellectual property | Phishing attack targeting high-level employees |
| Cybersecurity News Outlet | October 28, 2024 (Example Date) | Potential theft of sensitive financial data | Unspecified zero-day exploit |
Hacker Profiles and Motivations

Source: cloudfront.net
The alleged Hewlett Packard breach, if confirmed, raises crucial questions about the perpetrators’ identities, capabilities, and ultimate goals. Understanding these aspects is vital not only for addressing the immediate damage but also for strengthening future cybersecurity defenses against similar attacks. Analyzing potential hacker profiles and motivations requires considering a range of possibilities, from financially motivated individuals to state-sponsored actors.
The potential profiles of the hackers involved are multifaceted. They could range from highly skilled lone wolves with advanced technical expertise and access to sophisticated tools, to organized groups operating with specialized divisions for reconnaissance, infiltration, data exfiltration, and monetization. Resources at their disposal could include significant financial backing, dedicated infrastructure, and potentially even inside assistance. Affiliations could range from independent criminal enterprises to nation-state actors aiming for strategic advantage or even activist groups with specific political agendas. The complexity of the attack itself will provide clues as to the level of sophistication and resources employed.
Potential Hacker Motivations
The motivations behind the alleged breach could be diverse and overlapping. Financial gain is a primary driver in many cyberattacks, with stolen data sold on the dark web or used for fraudulent activities. Espionage is another strong possibility, particularly if sensitive corporate data, intellectual property, or customer information was targeted. State-sponsored actors might be interested in gaining competitive intelligence or disrupting HP’s operations. Finally, activist groups might target HP for perceived ethical failings or corporate practices they wish to expose. A thorough investigation will be crucial to determining the primary motivation.
Comparison with Similar Cyberattacks
This alleged breach shares similarities with several high-profile cyberattacks targeting technology companies. Understanding these parallels can inform the investigation and improve future security measures.
The following points illustrate similar past incidents:
- The 2014 Sony Pictures hack: This attack, attributed to North Korea, involved the theft and release of sensitive company data, including emails, financial information, and unreleased movies. The motivation was primarily political retribution for Sony’s production of *The Interview*, a satirical film about the North Korean leader. The attack highlighted the vulnerability of large organizations to sophisticated state-sponsored attacks and the potential for significant reputational damage.
- The 2017 NotPetya ransomware attack: While not solely targeting a single organization, NotPetya affected numerous companies globally, including technology giants. Initially disguised as ransomware, the attack caused widespread disruption and significant financial losses. Attribution remains uncertain, but some evidence points towards state-sponsored actors aiming to cripple Ukrainian infrastructure and indirectly impacting global businesses.
- The 2017 Equifax data breach: This breach resulted in the exposure of personal information of millions of customers, highlighting the vulnerability of large databases to exploitation of known software vulnerabilities. The attackers were financially motivated, selling the stolen data on the dark web. This incident underscored the importance of robust patch management and security practices.
These examples illustrate the varied motivations, methods, and consequences of significant cyberattacks targeting organizations similar to Hewlett Packard. The alleged breach underscores the ongoing need for robust cybersecurity defenses and proactive threat intelligence to mitigate future risks.
Hewlett Packard’s Response and Mitigation Efforts
Hewlett Packard’s response to any alleged security breach would be crucial in shaping public perception and maintaining customer trust. A swift and transparent response, coupled with demonstrable efforts to mitigate the damage, is paramount. Their actions in such a scenario would be closely scrutinized by stakeholders, including investors, customers, and regulatory bodies.
Hewlett Packard’s official response to alleged breaches typically involves a multi-pronged approach. This would include issuing public statements acknowledging the incident, outlining the steps taken to investigate the situation, and reassuring customers of their commitment to data security. These statements often aim to balance transparency with the need to avoid revealing information that could compromise ongoing investigations or provide further advantage to potential attackers. In addition to public statements, HP likely engages in internal investigations, collaborating with cybersecurity experts and law enforcement as needed.
Hewlett Packard’s Containment and Mitigation Measures
Following the initial acknowledgement, HP would likely implement a series of measures to contain the breach and mitigate its potential impact. This could involve isolating affected systems, patching vulnerabilities, and deploying enhanced security controls. The company might also conduct a thorough forensic analysis to determine the extent of the breach, identify the attackers, and understand their methods. This information is vital in preventing future incidents. Furthermore, HP would likely engage in proactive communication with affected customers, providing them with information about the breach and any necessary steps they should take to protect themselves. This might include credit monitoring services or password reset guidance.
Effectiveness of Hewlett Packard’s Security Protocols
Assessing the effectiveness of HP’s security protocols requires a careful examination of the alleged breach itself. A successful attack suggests vulnerabilities in their existing systems, perhaps due to outdated software, insufficient employee training, or inadequate security monitoring. Conversely, a swift and effective response to the breach, minimizing data loss and quickly containing the attack, would indicate a robust and well-rehearsed incident response plan. Factors such as the time taken to detect and contain the breach, the extent of data compromised, and the overall impact on the business would all be considered when evaluating the efficacy of HP’s security posture. Independent audits and security assessments could further shed light on any weaknesses.
Hypothetical Improved Security Strategy
Based on the lessons learned from a hypothetical breach, an improved security strategy for HP might involve several key enhancements. This could include implementing a zero-trust security model, which verifies every user and device before granting access to resources, regardless of location. Investing in advanced threat detection systems, including artificial intelligence and machine learning, could help identify and respond to sophisticated attacks more effectively. Furthermore, a comprehensive employee security awareness training program, focusing on phishing and social engineering techniques, would strengthen the human element of security. Regular security audits and penetration testing would help identify and address vulnerabilities before they can be exploited. Finally, a robust incident response plan, regularly tested and updated, is critical for effective mitigation and recovery. This plan should clearly Artikel roles and responsibilities, communication protocols, and escalation procedures. The inclusion of a dedicated cybersecurity team, with the authority and resources to address emerging threats, would further enhance the overall security posture.
Impact and Consequences of the Alleged Breach
An alleged data breach at a tech giant like Hewlett Packard (HP) ripples far beyond the immediate victim. The potential consequences are multifaceted, impacting HP’s reputation, financial stability, customer relationships, and the broader cybersecurity landscape. Understanding the potential ramifications is crucial for both HP and the industry as a whole. This section Artikels the potential impacts categorized for clarity.
Reputational Damage and Loss of Customer Trust
The fallout from a data breach can severely damage a company’s reputation. A breach involving sensitive customer data, intellectual property, or financial information erodes public trust. HP, as a globally recognized brand, faces significant reputational risks. Negative media coverage, public outcry, and decreased customer confidence can lead to a loss of market share and decreased investor confidence. This damage can be long-lasting, impacting future business prospects. Consider the case of Equifax, whose 2017 breach led to years of legal battles, regulatory fines, and a persistent decline in public trust. HP’s response to the alleged breach will significantly influence the extent of this reputational damage.
Loss of customer trust is a direct consequence of a data breach, leading to decreased sales and brand loyalty. The long-term effects can be devastating, especially for a company that relies on customer trust for its success.
Financial Losses and Legal Ramifications
A data breach can translate into substantial financial losses for HP. Costs associated with incident response, investigation, legal fees, regulatory fines, and remediation efforts can quickly escalate. Furthermore, HP may face class-action lawsuits from affected customers and partners, leading to significant financial liabilities. The costs of notifying affected individuals, providing credit monitoring services, and enhancing security measures also contribute to the overall financial burden. The financial impact will depend on the scope of the breach, the sensitivity of the compromised data, and the effectiveness of HP’s response.
Financial losses from a data breach can include direct costs like investigation and remediation, as well as indirect costs like lost revenue and reputational damage. These costs can easily run into millions, even billions of dollars depending on the scale and severity of the breach.
Impact on Clients and Partners
The consequences extend beyond HP itself. Clients and partners who rely on HP’s products and services could also experience negative impacts. If sensitive client data is compromised, it could lead to identity theft, financial fraud, and reputational damage for those clients. Partners could face disruptions to their operations, loss of business opportunities, and damage to their own reputations. The breach could also strain existing business relationships, leading to contract cancellations or reduced future collaborations. For example, a compromised supply chain management system could disrupt operations for numerous businesses relying on HP’s services.
The ripple effect of a data breach extends to HP’s clients and partners, causing potential financial losses, reputational damage, and operational disruptions. Maintaining trust within this ecosystem is paramount for HP’s long-term success.
Broader Cybersecurity Implications
The alleged breach highlights the ongoing challenges in the cybersecurity landscape. It underscores the need for stronger security measures, improved incident response capabilities, and increased awareness among both organizations and individuals. The incident could trigger renewed scrutiny of industry best practices and regulatory frameworks. Furthermore, it may accelerate the adoption of advanced security technologies and a greater emphasis on proactive security measures across various industries. The long-term impact could involve changes in legislation, increased investment in cybersecurity infrastructure, and a heightened focus on data privacy.
This alleged breach serves as a stark reminder of the persistent vulnerabilities in the cybersecurity landscape, emphasizing the need for continuous improvement in security protocols and incident response planning.
Legal and Regulatory Ramifications: Hackers Alleged Hewlett Packard Breach
The alleged Hewlett Packard breach carries significant legal and regulatory ramifications for both the company and the individuals implicated. The severity of the consequences will depend on the scale of the breach, the type of data compromised, the actions taken (or not taken) by HP, and the culpability of the alleged hackers. Navigating this complex legal landscape requires understanding the interplay of various national and international laws.
The potential legal battles could be protracted and expensive, involving civil lawsuits from affected individuals and businesses, as well as potential criminal charges. The sheer volume of data potentially compromised, coupled with the potential for identity theft and financial loss, could lead to substantial damages awarded in civil cases. For the hackers, the penalties could range from hefty fines to lengthy prison sentences, depending on the jurisdiction and the specific charges brought against them.
Applicable Laws and Regulations
Several laws and regulations could be invoked in response to this alleged breach. In the United States, the Computer Fraud and Abuse Act (CFAA) is a key piece of legislation that criminalizes unauthorized access to computer systems. State laws, like California’s Consumer Privacy Act (CCPA) or other state-specific data breach notification laws, might also come into play, depending on where the data was stored and the location of affected individuals. Internationally, the General Data Protection Regulation (GDPR) in Europe, if applicable, could impose substantial fines on HP for failing to adequately protect personal data. These regulations often require companies to implement robust security measures, promptly notify affected individuals of breaches, and demonstrate compliance with data protection standards. Failure to meet these requirements can result in significant penalties.
Comparison with Past Incidents
The legal responses to this alleged breach can be compared to past high-profile data breaches, such as the Yahoo! breach or the Equifax breach. These cases demonstrated the varying approaches taken by regulatory bodies and the courts, highlighting the complexities of assigning liability and determining appropriate penalties. The scale of the breach, the nature of the compromised data, and the response of the affected organization all played crucial roles in shaping the legal outcomes. For instance, the Equifax breach resulted in significant fines and settlements due to the company’s slow response and inadequate security measures. This case, and others, set a precedent for future legal actions involving data breaches.
Influence on Future Cybersecurity Regulations, Hackers alleged hewlett packard breach
This alleged breach, if confirmed and found to involve negligence on HP’s part, could further strengthen the push for more stringent cybersecurity regulations. Governments worldwide are increasingly recognizing the need for robust frameworks to protect sensitive data. This event could accelerate the development of new laws and regulations focusing on data breach prevention, response, and accountability. We might see stricter penalties for companies failing to meet minimum security standards, stricter requirements for data breach notification, and potentially increased government oversight of cybersecurity practices within major corporations. The pressure to enhance data protection measures will likely intensify, influencing both national and international legislation in the coming years. The precedent set by legal outcomes in this case could significantly impact the future regulatory landscape.
Ultimate Conclusion

Source: i-scmp.com
The alleged Hewlett Packard breach serves as a stark reminder of the persistent and evolving threats facing even the most technologically advanced organizations. While the full extent of the damage may not be immediately apparent, the incident underscores the crucial need for proactive security measures, robust incident response plans, and ongoing vigilance in the face of sophisticated cyberattacks. The investigation and its aftermath will undoubtedly shape future cybersecurity strategies and regulations, influencing how companies protect themselves and their clients’ data in the years to come. The fallout from this incident will likely resonate throughout the industry, prompting critical self-assessment and a renewed focus on data security.


