Google chrome real time phishing protection – Google Chrome real-time phishing protection: It’s the silent guardian, the watchful protector, the digital knight shining its light on those sneaky phishing attempts. But how effective is it *really*? We dive deep into Chrome’s defenses, exploring its mechanisms, Google’s threat intelligence network, and the user experience – even uncovering some surprising limitations and bypass techniques. Get ready to level up your online security game.
This article unpacks the complexities of Chrome’s Safe Browsing feature, examining how it identifies and thwarts phishing attacks in real-time. We’ll dissect Google’s threat intelligence, the backbone of this protection, and analyze how Chrome warns users about potential threats. We’ll also explore the limitations of this system, discuss potential bypass methods, and provide crucial tips to bolster your online security beyond Chrome’s built-in features. Because let’s be honest, even the best defenses can be cracked, so knowing your enemy is half the battle.
Chrome’s Built-in Protection Mechanisms
Chrome’s Safe Browsing feature is your silent guardian against the ever-evolving threat of phishing attacks. It acts as a real-time shield, constantly checking websites against a massive database of known malicious sites and suspicious patterns, protecting you from online scams before you even realize you’re in danger. This proactive approach significantly reduces your risk of falling victim to online fraud.
Chrome’s Safe Browsing uses a multi-layered approach to identify and neutralize phishing threats. It analyzes website URLs, content, and behavior, cross-referencing this information with its constantly updated database of known phishing sites. If a website matches known malicious patterns or exhibits suspicious behavior, Chrome will warn you before you proceed, preventing potential damage. This system operates in the background, requiring minimal user interaction, ensuring seamless and effective protection.
Safe Browsing’s Phishing Detection Capabilities
Chrome’s Safe Browsing protects against a wide range of phishing attacks, including those employing deceptive URLs, spoofed login pages, and malicious email attachments. It’s adept at identifying subtle variations in website designs and text that might otherwise fool unsuspecting users. For instance, it can detect websites that mimic popular banking portals, social media platforms, or email providers, often employing similar logos, fonts, and layouts to trick users into entering their credentials. The system is designed to be proactive and adaptive, constantly learning and evolving to counter new and emerging phishing techniques.
Chrome’s Safe Browsing Compared to Other Browsers
While most modern browsers offer some form of phishing protection, Chrome’s Safe Browsing is widely considered to be among the most comprehensive and effective. The speed and accuracy of its detection are key differentiators. While other browsers offer similar features, Chrome’s real-time protection, coupled with its massive database and sophisticated algorithms, provides a higher level of protection against a wider range of threats. The continuous updates to its database ensure that it remains current with the latest phishing techniques.
Response Times of Chrome’s Safe Browsing to Phishing Attempts
The following table illustrates example response times of Chrome’s Safe Browsing to various phishing attempts. These are illustrative examples and actual response times may vary based on network conditions and the complexity of the phishing attack.
| Phishing Type | Detection Time (milliseconds) | User Action Required | Severity Level |
|---|---|---|---|
| Spoofed Banking Login | 150 | Warning displayed; user prevented from proceeding | High |
| Deceptive Email Attachment | 200 | Warning displayed; download blocked | High |
| Malicious URL Redirect | 100 | User redirected to a warning page | Medium |
| Sophisticated Phishing Site (mimicking popular social media) | 300 | Warning displayed; access blocked | High |
The Role of Google’s Threat Intelligence: Google Chrome Real Time Phishing Protection
Google Chrome’s real-time phishing protection isn’t magic; it’s powered by a sophisticated threat intelligence network constantly working behind the scenes. This network acts as a vigilant guardian, analyzing vast amounts of data to identify and neutralize malicious websites before they can harm users. Think of it as a global early warning system for online threats, constantly updated and refined to stay ahead of the curve.
Google’s threat intelligence plays a crucial role in keeping Chrome users safe from phishing attacks. It’s the engine that drives the real-time protection, constantly comparing visited URLs against its massive database of known malicious sites. This process happens seamlessly in the background, offering protection without interrupting the user’s browsing experience. The speed and accuracy of this system are critical; a fraction of a second delay could mean the difference between a safe browsing session and a compromised account.
Data Sources for Phishing Website Identification
Google leverages a multi-layered approach to identify phishing websites. This isn’t just about scanning URLs; it involves analyzing a vast range of data points. This includes analyzing suspicious website characteristics such as code similarities to known malicious sites, reported user experiences, and even the language used on the website. Furthermore, Google uses machine learning algorithms to identify patterns and anomalies that might indicate malicious intent, even in previously unseen websites. This proactive approach allows Google to detect new and evolving phishing techniques before they become widespread. The more data points analyzed, the more accurate and effective the protection becomes.
Methods for Updating the Threat Database
Maintaining a current threat database is paramount for effective phishing protection. Google employs a continuous process of data collection, analysis, and updates. This involves a constant flow of information from various sources, including user reports, automated scans, and partnerships with cybersecurity organizations. The system is designed to be highly scalable and adaptable, able to handle the ever-increasing volume of new phishing sites that emerge daily. The update process is automated and occurs in real-time, ensuring that Chrome users benefit from the latest protection as soon as it’s available. This constant vigilance is essential for staying ahead of the rapidly evolving landscape of online threats.
Key Technologies and Processes in Google’s Threat Intelligence for Phishing Detection
The effectiveness of Google’s phishing protection relies on a complex interplay of technologies and processes. These work together to provide a robust and constantly evolving defense against phishing attacks.
- Safe Browsing API: This API allows websites and applications to check URLs against Google’s Safe Browsing database, enabling proactive protection for users.
- Machine Learning Algorithms: Sophisticated algorithms analyze website characteristics, user behavior, and other data to identify phishing patterns and anomalies.
- Data Aggregation and Analysis: Google collects data from various sources, including user reports, automated scans, and partnerships, to build a comprehensive picture of the threat landscape.
- Real-time Updates: The threat database is constantly updated, ensuring that Chrome users have access to the latest protection.
- Heuristic Analysis: This method analyzes website code and behavior to identify potentially malicious patterns, even if the website isn’t explicitly listed in the threat database.
User Experience and Warnings
Chrome’s phishing protection isn’t just about silently blocking bad sites; it’s about keeping users informed and safe. A crucial element of this is the user experience surrounding warnings, ensuring they’re clear, concise, and actionable. Chrome aims to educate users about the risks without overwhelming them with technical jargon.
Chrome employs a multi-layered approach to warning users about potentially dangerous websites. This ranges from subtle visual cues to prominent, unmistakable warnings, depending on the severity of the threat. The goal is to provide users with enough information to make informed decisions about whether to proceed or retreat.
Chrome’s Phishing Warning Messages
Chrome utilizes several types of warnings to alert users to potentially phishing websites. These vary in their visual presentation and the level of risk they indicate. A simple warning might involve a small, unobtrusive icon in the address bar, indicating a potential security concern. More serious threats trigger a full-page warning, preventing access to the site until the user acknowledges the risk.
For instance, a simple warning might display a red triangle with an exclamation mark next to the URL in the address bar, accompanied by a short tooltip explaining the potential risk. This subtle alert prompts users to double-check the site’s legitimacy without disrupting their workflow. In contrast, a severe threat would result in a bold red banner across the top of the screen, explicitly stating that the site is potentially dangerous and strongly advising against proceeding. This is often accompanied by an explanation of why the site is flagged as suspicious. These warnings might mention the use of a known phishing technique or highlight discrepancies in the site’s security certificates.
Chrome’s Interface for Handling Phishing Warnings
Chrome’s interface is designed to be intuitive and straightforward when presenting phishing warnings. The warnings are typically presented prominently, making them impossible to miss. Crucially, they provide clear options for users to either proceed to the site (at their own risk) or navigate away. The “Back” button is often highlighted to make it easy to return to a safer site. Furthermore, the warning messages themselves are written in plain language, avoiding technical terms that might confuse users. The inclusion of links to additional information, such as Google’s Safe Browsing help center, empowers users to learn more about online safety.
Proposed Improved Phishing Warning System UI Mockup
Imagine a redesigned warning system that goes beyond simple text and icons. A redesigned warning could incorporate a visual representation of the threat level, perhaps using a color-coded system. A green checkmark would signify a safe site, while a yellow warning triangle would indicate a potential risk, and a bright red stop sign would signal a severe threat.
This enhanced warning could include a concise explanation of why the site is flagged, such as “Suspicious certificate” or “Known phishing site,” with a brief description of what that means. A progress bar, visualizing the level of confidence Google has in the site’s safety, would add another layer of clarity. This bar would be green for high confidence, yellow for medium, and red for low confidence. Furthermore, the option to report the site directly from the warning page could be included, simplifying the process for users who believe a site has been wrongly flagged. The entire warning could be presented in a clean, modern design, prioritizing clarity and user-friendliness. The use of easily understandable icons and minimal text will ensure that the message is received and understood even by users with limited technical knowledge.
Limitations and Bypass Techniques
Source: ithelpsupport.com
Chrome’s real-time phishing protection, while robust, isn’t foolproof. Sophisticated phishing campaigns often leverage techniques designed to circumvent these safeguards, highlighting the ongoing arms race between security measures and malicious actors. Understanding these limitations and bypass methods is crucial for both users and developers to strengthen overall online security.
The effectiveness of Chrome’s protection varies depending on the type of phishing attack. While it excels at identifying and blocking common phishing websites using known malicious URLs and patterns, more advanced attacks pose significant challenges. These advanced attacks often exploit vulnerabilities in human psychology and leverage techniques that make detection difficult, even for sophisticated security systems.
Spear Phishing and Clone Phishing Effectiveness
Spear phishing, which targets individuals with highly personalized and tailored attacks, often bypasses generic phishing detection mechanisms. Because the content is specific to the target, it often avoids triggering typical phishing alerts. Similarly, clone phishing, which mimics legitimate websites, can be incredibly effective. If the cloned site is visually indistinguishable from the original and the attacker is clever enough to maintain the clone, it can evade detection. Chrome’s protection is more effective against mass-distributed phishing campaigns with generic lures than highly targeted attacks.
Bypass Methods, Effectiveness, and Mitigation Strategies
Several techniques allow sophisticated phishers to circumvent Chrome’s security measures. Understanding these methods and their corresponding vulnerabilities is vital for developing effective countermeasures.
| Bypass Method | Effectiveness | Target Vulnerability | Mitigation Strategy |
|---|---|---|---|
| Using a compromised legitimate website (website defacement) | High – users trust the site | Trust in established brands | Regular security audits of trusted websites, improved website security protocols, and user education. |
| Employing SSL certificates (even if illegitimate) | Moderate – instills a false sense of security | User reliance on visual cues (HTTPS padlock) | User education to focus on URL verification and website content analysis, rather than just the padlock. |
| Leveraging zero-day exploits in browsers | High – bypasses all client-side security | Unpatched browser vulnerabilities | Prompt patching of browser vulnerabilities, using up-to-date antivirus software. |
| Using obfuscation techniques to hide malicious code | Moderate – makes detection harder | Limitations in static analysis of code | Advanced sandboxing and dynamic analysis techniques for identifying malicious behavior. |
| Creating a near-perfect clone of a legitimate website | High – difficult to distinguish from the original | User reliance on visual cues | User education on verifying URLs and checking for inconsistencies in website content. |
Beyond Safe Browsing
Source: abacustechnologies.com
Chrome’s built-in phishing protection is a fantastic first line of defense, acting like a sturdy castle wall against the digital invaders. But even the strongest walls can be breached, which is why relying solely on Chrome’s safeguards isn’t enough in today’s complex online landscape. Think of it like this: your car has seatbelts, but you still wear a helmet when riding a motorcycle, right? Additional security measures are your extra layers of protection, significantly reducing your vulnerability to phishing attacks.
While Chrome’s real-time protection diligently scans websites and flags suspicious activity, a multi-layered approach is crucial for comprehensive security. This means combining Chrome’s built-in features with other security software and practices to create a robust, impenetrable shield against phishing attempts. This holistic approach minimizes your exposure and reduces the likelihood of falling victim to sophisticated attacks.
Additional Security Software
Investing in reputable antivirus and anti-malware software is akin to adding a moat around your digital castle. These programs provide an extra layer of protection by actively scanning your system for malicious files and programs, including those that might be downloaded inadvertently through a phishing link. Software like Norton, McAfee, or Bitdefender not only detects malware but also actively blocks suspicious websites and downloads, providing a second opinion on sites that Chrome might miss. Remember, even if Chrome doesn’t flag a site, it doesn’t guarantee its safety.
Password Management and Two-Factor Authentication
Strong, unique passwords are the foundation of a secure online presence. Using the same password across multiple accounts is a major security risk, akin to using the same key for every door in your house. A single compromised account can become a gateway for attackers to access your other accounts. A password manager like LastPass, 1Password, or Bitwarden generates and securely stores complex passwords, eliminating the need to remember dozens of intricate combinations. Furthermore, enabling two-factor authentication (2FA) adds an extra layer of security, requiring a second verification step beyond your password, such as a code sent to your phone or email. This significantly reduces the risk of unauthorized access, even if your password is somehow compromised.
Browser Extensions for Enhanced Phishing Protection, Google chrome real time phishing protection
While Chrome’s built-in protection is comprehensive, browser extensions can offer specialized features to further enhance your security. These extensions often provide real-time analysis of websites, comparing them against known phishing databases and alerting you to potential threats before you even interact with the site. Some extensions also analyze links within emails and other communications, identifying potentially malicious URLs before you click on them. Examples include extensions that actively scan for phishing attempts and malicious code, adding an extra level of scrutiny to your online interactions.
Recommended Security Practices
Supplementing Chrome’s real-time phishing protection requires a proactive approach. Here’s a bulleted list of recommended practices:
- Use a reputable antivirus and anti-malware program.
- Employ a password manager to generate and store strong, unique passwords for each account.
- Enable two-factor authentication (2FA) wherever possible.
- Regularly update your operating system and software to patch security vulnerabilities.
- Be wary of unsolicited emails and links; verify the sender’s identity before clicking any links.
- Hover over links to see the actual URL before clicking; look for discrepancies between the displayed text and the actual destination.
- Consider using a browser extension specifically designed to detect phishing attempts.
- Educate yourself and your family about phishing techniques and scams.
Final Conclusion
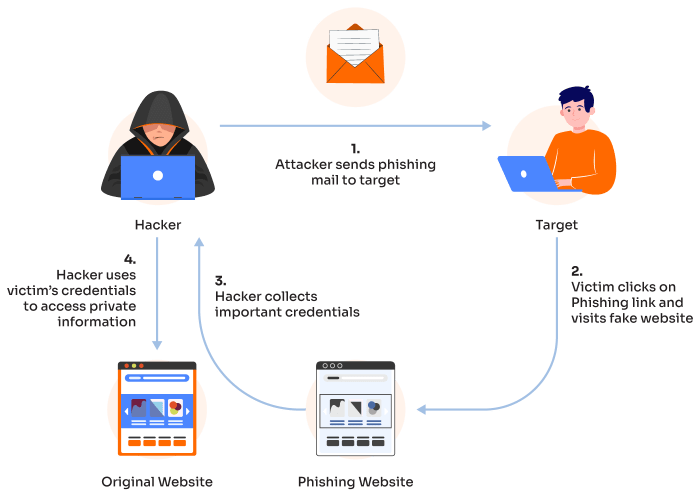
Source: valimail.com
So, is Google Chrome’s real-time phishing protection a foolproof shield? While it’s a powerful tool, it’s not invincible. Understanding its strengths and weaknesses is key to staying ahead of the curve. Remember, online security is a layered approach; combining Chrome’s built-in protection with strong passwords, two-factor authentication, and additional security software is your best bet against those digital villains. Stay vigilant, stay informed, and stay safe!
