Free Microsoft Expanded Cloud Logging Playbook: Level up your cloud security game! This playbook isn’t just another tech manual; it’s your secret weapon against those sneaky digital threats. We’re diving deep into how to implement this free resource, boosting your defenses, and making your cloud environment a fortress of impenetrable awesomeness. Get ready to become a cloud security ninja.
This guide breaks down the playbook’s core components, showing you how to leverage expanded logging for improved threat detection and response. We’ll walk you through step-by-step implementation, integration with existing security tools, and even strategies for optimizing costs. Think of it as your ultimate guide to transforming your cloud logging from a sleepy afterthought to a proactive security powerhouse.
Understanding the “Free Microsoft Expanded Cloud Logging Playbook”
This playbook isn’t just another tech document; it’s your secret weapon for bolstering cloud security. Think of it as a comprehensive guide to maximizing Microsoft’s built-in logging capabilities, helping you detect threats faster and respond more effectively. It’s free, it’s powerful, and it’s designed to help you get the most out of your cloud investment, regardless of your current security posture.
The core components revolve around leveraging Microsoft’s various logging services to create a unified, comprehensive view of your cloud environment’s activity. This includes Azure Monitor Logs, Azure Security Center, and potentially other third-party tools integrated into the Azure ecosystem. The playbook guides you through configuring these services to collect, analyze, and alert on critical security events, ultimately giving you a single pane of glass for security monitoring.
Benefits of Utilizing the Playbook for Enhanced Security
The primary benefit is improved threat detection. By centralizing and analyzing logs from diverse sources, you gain a much clearer picture of what’s happening within your cloud environment. This allows for quicker identification of suspicious activities, reducing the time it takes to respond to security incidents. This speed is crucial; the faster you detect and react, the less damage a potential breach can inflict. Furthermore, the playbook streamlines compliance efforts by providing a structured approach to logging and monitoring, making it easier to meet regulatory requirements. Finally, the playbook facilitates proactive security improvements. By analyzing log data, you can identify vulnerabilities and weaknesses in your infrastructure before they’re exploited.
Step-by-Step Implementation of Key Features
Implementing the playbook involves several key steps. First, you need to assess your current logging infrastructure. This involves identifying existing logging solutions and determining which data sources are most critical for security monitoring. Next, you’ll configure the selected logging services (like Azure Monitor Logs) to collect the relevant data. This might involve setting up diagnostic settings to send logs from various Azure services to a central location. Third, you’ll configure alerts based on predefined or custom rules. These alerts will notify you of potential security events, such as unusual login attempts or suspicious file activity. Finally, you’ll regularly review and refine your logging strategy based on the insights gained from analyzing log data. This iterative process is crucial for maintaining an effective security posture.
Best Practices for Optimizing the Playbook Across Different Cloud Environments
The playbook’s flexibility allows adaptation to various cloud environments. For example, in a hybrid cloud setup, you’ll need to ensure seamless integration between on-premises logging solutions and cloud-based logging services. This might involve using tools like Azure Arc to extend Azure monitoring capabilities to on-premises resources. In multi-cloud environments, the challenge lies in consolidating logs from different cloud providers into a unified view. This often requires using a centralized logging platform that can ingest and correlate data from diverse sources. Regardless of the environment, regular review and optimization of log retention policies are crucial to manage storage costs and ensure compliance with data retention regulations. For instance, you might archive less critical logs to a cheaper storage tier after a certain period.
Security Enhancements with Expanded Logging
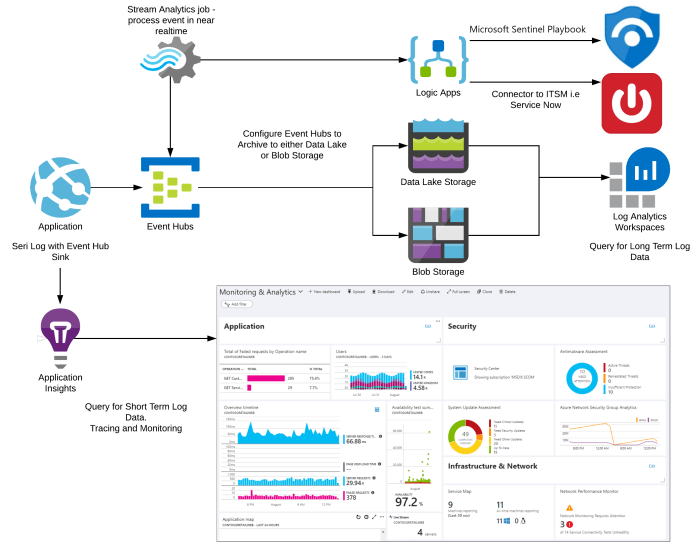
Source: microsoft.com
Leveling up your cloud security game often means seeing more, not less. Expanded logging isn’t just about generating more data; it’s about gaining crucial insights into your cloud environment’s security posture, allowing for proactive threat mitigation and faster incident response. This playbook helps you achieve that by guiding you through the process of configuring comprehensive logging across various Microsoft cloud services.
The Microsoft Expanded Cloud Logging Playbook directly addresses several key security vulnerabilities. Insufficient logging is a common weakness, hindering effective threat detection and incident investigation. By implementing the playbook’s recommendations, organizations can gain a more complete picture of user activity, system events, and potential security breaches, enabling timely identification and remediation of threats. This includes improved visibility into data access patterns, configuration changes, and potential malicious activities, providing a more robust defense against various attack vectors like data exfiltration, insider threats, and external intrusions.
Improved Threat Detection and Response
Enhanced logging capabilities significantly improve threat detection and response times. With more granular data, security teams can correlate events across different services and identify patterns indicative of malicious behavior. For instance, unusual login attempts from unfamiliar locations, suspicious data access requests, or unexpected configuration changes can be readily detected and investigated. This allows for quicker containment of threats, minimizing potential damage and reducing recovery time. The playbook’s emphasis on centralized logging and analysis further enhances this capability by providing a single pane of glass for security monitoring.
Challenges in Implementing the Playbook and Proposed Solutions
While the benefits of expanded logging are clear, implementation can present certain challenges. One common hurdle is the sheer volume of log data generated. Efficient storage, processing, and analysis require robust infrastructure and tools. Solutions include leveraging cloud-based log analytics platforms like Azure Log Analytics, which offer scalable storage and powerful query capabilities. Another challenge is the need for skilled personnel to manage and analyze the increased data volume. Addressing this requires investing in training and potentially outsourcing parts of the security monitoring function to managed security service providers (MSSPs). Finally, ensuring compliance with data retention policies and privacy regulations is crucial. This necessitates careful planning and configuration of log retention settings, ensuring compliance with relevant laws and industry best practices.
Comparison of Standard and Expanded Logging
The following table highlights the key differences between standard and expanded logging capabilities, illustrating the improvements achieved through the implementation of the Expanded Cloud Logging Playbook.
| Feature | Standard Logging | Expanded Logging | Improvement |
|---|---|---|---|
| Log Volume | Limited to essential system events | Comprehensive logs from multiple services | Increased visibility into system activity and potential threats |
| Data Granularity | High-level summaries | Detailed event information with timestamps and context | Improved accuracy in threat detection and incident investigation |
| Log Retention | Short retention periods | Flexible and configurable retention policies | Enhanced ability to analyze historical data for security trends and compliance audits |
| Integration with Security Tools | Limited integration | Seamless integration with SIEM and other security tools | Streamlined threat detection and response workflows |
Integration with Existing Security Tools

Source: mailinblue.com
Unlocking the full potential of the free Microsoft Expanded Cloud Logging playbook isn’t just about collecting more logs; it’s about seamlessly integrating that rich data stream into your existing security infrastructure. This allows for a more cohesive and effective security posture, enhancing threat detection and response capabilities. Think of it as connecting the dots, transforming raw log data into actionable intelligence.
The playbook’s design emphasizes compatibility, allowing for smooth integration with both Microsoft’s own security suite and various third-party Security Information and Event Management (SIEM) systems. This integration streamlines your security workflows, providing a unified view of your security landscape and significantly improving efficiency. By centralizing log analysis, you can reduce alert fatigue and focus on truly critical threats.
Integration with Microsoft Security Products
The Expanded Cloud Logging playbook works hand-in-glove with a range of Microsoft security solutions. For instance, data ingested through the playbook can be directly fed into Microsoft Sentinel, Microsoft’s cloud-native SIEM. This allows for enhanced threat detection using Sentinel’s advanced analytics and automation capabilities. Similarly, integration with Azure Security Center allows for improved vulnerability management and proactive threat mitigation. The playbook’s data can enrich alerts generated by these platforms, providing crucial context and speeding up incident response times. Imagine identifying a suspicious login attempt – the playbook’s detailed logs can provide the exact location, device, and user activity leading up to the event, enabling faster and more informed decisions.
Integrating with Third-Party SIEM Systems
The playbook’s data can be exported in various formats, making it readily compatible with numerous third-party SIEM solutions. Common methods include using Azure Log Analytics to export logs to a chosen SIEM via APIs or dedicated connectors. Many SIEM vendors offer pre-built integrations or connectors specifically designed for Azure logs, simplifying the process. Once integrated, the playbook’s detailed logs can be correlated with data from other sources within the SIEM, providing a holistic view of security events across your entire IT landscape. This allows security analysts to identify patterns and relationships that might otherwise go unnoticed, improving overall threat detection effectiveness. For example, a SIEM might correlate a suspicious network connection identified through the playbook with malware activity detected by an endpoint detection and response (EDR) solution.
Leveraging Playbook Data in Security Workflows
The real power of the playbook lies in its ability to enrich existing security workflows. By integrating the expanded logs into your existing processes, you can significantly improve the effectiveness of threat detection, incident response, and security investigations. For example, threat hunting becomes significantly more efficient with access to comprehensive log data. Analysts can proactively search for specific indicators of compromise (IOCs) or unusual patterns across various services, uncovering threats that might otherwise remain hidden. Similarly, during incident response, the detailed logs can help pinpoint the root cause of an incident faster, minimizing the impact and accelerating recovery efforts. The playbook’s data essentially provides the crucial context needed for more accurate and timely security actions.
Commonly Compatible Security Tools, Free microsoft expanded cloud logging playbook
The following list showcases some common security tools that seamlessly integrate with the data generated by the Expanded Cloud Logging playbook:
- Microsoft Sentinel
- Azure Security Center
- Splunk
- QRadar
- Elastic Stack (ELK)
- LogRhythm
This list is not exhaustive, but it represents a selection of popular and widely used security tools that readily integrate with the data generated by the Expanded Cloud Logging playbook. The specific integration methods may vary depending on the chosen tool and its capabilities. However, the flexibility and standardization of the data exported by the playbook ensure compatibility across a wide range of security solutions.
Data Analysis and Reporting
Unlocking the true power of Microsoft’s expanded cloud logging isn’t just about collecting data; it’s about turning that data into actionable insights. Effective analysis and reporting are crucial for proactive threat detection, performance optimization, and overall security posture improvement. This section Artikels strategies for leveraging your expanded log data to achieve these goals.
A well-designed reporting strategy transforms raw log data into meaningful information, enabling security teams to identify trends, pinpoint vulnerabilities, and respond swiftly to security incidents. This involves choosing the right KPIs, visualizing the data effectively, and establishing processes for anomaly detection and response.
Reporting Strategy and Key Performance Indicators
A robust reporting strategy should focus on providing clear, concise, and actionable information. This means selecting relevant KPIs that align with your organization’s security objectives. KPIs should be regularly monitored and analyzed to track progress and identify areas needing attention. Examples of key performance indicators that can be effectively tracked using expanded logging data include:
Consider these KPIs as a starting point, customizing them based on your specific security needs and organizational priorities. For example, a company focused on PCI compliance might prioritize metrics related to data exfiltration attempts, while a SaaS provider might focus on service availability and user authentication failures.
- Mean Time To Detect (MTTD): The average time it takes to detect a security incident from its initial occurrence. Lower MTTD indicates a more effective security posture.
- Mean Time To Respond (MTTR): The average time it takes to respond to and resolve a security incident. Lower MTTR indicates faster incident response capabilities.
- Number of Security Alerts: Tracks the total number of security alerts generated within a specific timeframe. High numbers might indicate a need for improved security controls or tuning of alert thresholds.
- Successful Login Attempts vs. Failed Login Attempts: This ratio can highlight potential brute-force attacks or compromised credentials. A significantly high failure rate warrants investigation.
- Data Exfiltration Attempts: The number of attempts to transfer sensitive data outside the organization’s network. Zero is the ideal target, but trends should be monitored closely.
Sample Dashboard Visualization
Imagine a dashboard with two main sections.
The left section features a line graph charting the number of security alerts over time (daily or weekly). The X-axis represents the time period, and the Y-axis represents the number of alerts. Different colored lines could represent various alert types (e.g., intrusion attempts, suspicious logins, data breaches). This visual representation quickly highlights trends and potential spikes in security events.
The right section presents a series of pie charts showing the breakdown of alert types. Each slice of the pie represents a different alert category, with its size proportional to the percentage of total alerts it constitutes. This provides a clear overview of the types of security events occurring within the organization. For example, one slice might represent “Suspicious Login Attempts,” another “Data Exfiltration Attempts,” and so on. This allows for quick identification of prevalent threat vectors.
Anomaly Detection and Response
Identifying anomalies within the expanded logs requires a combination of automated tools and human expertise. Automated systems can use machine learning algorithms to establish baselines for normal behavior and flag deviations.
For instance, a sudden surge in failed login attempts from a specific IP address, or a significant increase in data access requests from an unusual location, might be flagged as an anomaly. These anomalies should be investigated further by security analysts to determine their cause and potential impact. Response procedures should be clearly defined, including escalation paths and remediation strategies. This might involve blocking malicious IP addresses, resetting compromised credentials, or initiating a full security audit.
Cost Optimization and Resource Management
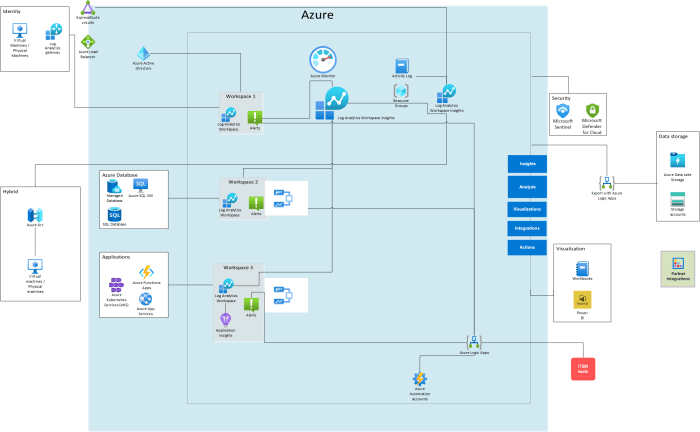
Source: microsoft.com
Expanded cloud logging offers unparalleled security insights, but the sheer volume of data generated can significantly impact your cloud spending. Smart resource management is crucial to reaping the benefits of enhanced security without breaking the bank. This section details strategies for optimizing your logging infrastructure and minimizing costs.
Effectively managing the costs associated with expanded logging requires a multi-pronged approach. It’s not just about reducing expenses; it’s about finding the sweet spot between comprehensive security monitoring and budgetary constraints. This involves careful planning, leveraging cost-effective storage solutions, and implementing efficient log retention policies.
Log Retention Policy Optimization
Balancing security needs with storage costs necessitates a well-defined log retention policy. Overly long retention periods inflate storage costs, while overly short periods might compromise investigations into security incidents. A tiered approach is often the most effective solution. For example, critical logs related to security events might be retained for a longer duration (e.g., 90 days) in a more expensive, readily accessible storage tier. Less critical logs, such as application logs, can be retained for a shorter period (e.g., 30 days) in a less expensive, archive storage tier. Regular review and adjustment of this policy based on data analysis and evolving security requirements are essential.
Comparison of Log Storage Solutions
Several log storage solutions cater to different needs and budgets. Azure Log Analytics offers a scalable and cost-effective solution for storing and analyzing large volumes of log data. Azure Blob Storage provides a cost-effective long-term archive solution for less frequently accessed logs. Choosing the right solution depends on factors such as the volume of logs, access frequency, and retention requirements. For instance, if you require quick access to all logs for immediate security analysis, Azure Log Analytics might be preferable, while Azure Blob Storage is more suitable for long-term archival needs where immediate access is less critical. Careful consideration of these factors is crucial for optimal cost management.
Implementing Cost-Saving Measures: A Step-by-Step Guide
- Analyze Current Spending: Begin by thoroughly reviewing your current cloud spending on logging. Identify areas where costs are high and pinpoint the contributing factors.
- Optimize Log Volume: Implement filtering and aggregation techniques to reduce the volume of logs stored. Focus on retaining only essential data. For example, filter out unnecessary debug logs in non-critical applications.
- Implement a Tiered Retention Strategy: As mentioned earlier, categorize logs based on their importance and implement a tiered retention policy. Store critical logs in a higher-cost, readily accessible tier, and less critical logs in a lower-cost, archive tier.
- Utilize Cost-Effective Storage: Explore different storage options and choose the most cost-effective solution that meets your needs. Consider using Azure Blob Storage for long-term archiving.
- Regularly Review and Adjust: Regularly review your logging costs and retention policies. Adjust them based on your evolving security needs and budget constraints. This ensures you maintain a balance between security and cost-effectiveness.
Ultimate Conclusion: Free Microsoft Expanded Cloud Logging Playbook
So, there you have it – your complete guide to conquering cloud security with the Free Microsoft Expanded Cloud Logging Playbook. By implementing these strategies, you’ll not only enhance your security posture but also optimize your resources. Remember, proactive security is the key to a peaceful, productive, and worry-free cloud experience. Now go forth and secure your digital kingdom!