Flowerstorm phishing as a service? Sounds like a sci-fi thriller, right? Wrong. It’s a terrifyingly real threat, a sophisticated, scalable way for cybercriminals to unleash a deluge of phishing attacks. Think of it as a dark, digital flower shop, delivering bouquets of malicious emails designed to steal your data, your money, and your peace of mind. This isn’t your grandpappy’s phishing scam; we’re talking about a highly organized, profitable enterprise with a chillingly efficient business model. Buckle up, because we’re about to explore the underbelly of this digital dark web phenomenon.
We’ll dissect the technical infrastructure powering these attacks, from the cleverly crafted emails to the sneaky methods used to bypass security measures. We’ll explore the financial incentives driving this lucrative business, examining the pricing models and marketing strategies employed by these shadowy operators. We’ll also delve into the legal and ethical quagmires, examining the potential consequences for those involved and exploring preventative measures you can take to protect yourself. Get ready to uncover the secrets behind Flowerstorm phishing, a threat that’s closer than you think.
Defining “Flowerstorm Phishing as a Service”
Flowerstorm phishing as a service (PhaaS) represents a worrying evolution in cybercrime. It leverages the power of automation and scalability to deliver highly targeted and sophisticated phishing campaigns at an unprecedented rate, making it a significant threat to both individuals and organizations. Think of it as a dark web marketplace for customized phishing attacks, offering everything from pre-built templates to fully managed campaigns.
Flowerstorm phishing attacks are characterized by their speed and volume. Instead of relying on individual phishing emails sent one at a time, Flowerstorm utilizes automated systems to blast out thousands, even millions, of highly personalized messages. This personalization often involves incorporating details gleaned from publicly available data or data breaches, making the phishing attempts far more convincing. The sheer volume of attacks increases the likelihood of success, overwhelming security systems and catching unsuspecting victims off guard.
Flowerstorm Phishing Attack Characteristics
Flowerstorm phishing attacks typically share several key characteristics. These attacks are highly targeted, leveraging publicly available information to personalize emails and increase their effectiveness. The scale of these attacks is massive, utilizing automated systems to send out a large number of emails in a short time frame. They often mimic legitimate organizations or services, creating a sense of urgency or trust to manipulate victims into clicking malicious links or providing sensitive information. Finally, the attacks are often incredibly difficult to detect due to their sophisticated nature and volume. Imagine a hurricane of phishing emails, each personalized to its recipient, making it almost impossible to filter them all effectively.
Comparison with Other Phishing Attacks
Unlike traditional phishing attacks which might rely on generic templates and mass-mailing, Flowerstorm phishing distinguishes itself through its automation, personalization, and scale. Spear phishing, while targeted, usually focuses on a smaller number of high-value targets. Whaling, another sophisticated form of phishing, targets specific high-profile individuals. Flowerstorm, however, sits somewhere in between, capable of targeting large numbers of individuals with highly personalized messages, making it both broad and highly effective. It’s the difference between a sniper (spear phishing) and a barrage of well-aimed missiles (Flowerstorm).
Key Actors in Flowerstorm Phishing as a Service
Several key players contribute to the Flowerstorm PhaaS ecosystem. There are the developers who create and maintain the automated systems, often selling their services on dark web marketplaces. Then there are the operators who purchase these services and customize the campaigns to target specific victims or industries. Finally, there are the affiliates or resellers who promote and distribute these services to other criminals. This complex web of actors makes tracking and disrupting Flowerstorm operations extremely challenging. Think of it like a sophisticated supply chain for cybercrime, with each player fulfilling a specific role in the overall operation.
Technical Aspects of Flowerstorm Phishing: Flowerstorm Phishing As A Service
Source: intellipaat.com
Flowerstorm phishing, as a service, relies on a sophisticated technical infrastructure to achieve its malicious goals. Understanding these technical aspects is crucial to recognizing and mitigating the threat. This section delves into the infrastructure, email delivery methods, security bypass techniques, and the crucial role of social engineering in making these attacks effective.
Infrastructure Components
Flowerstorm phishing attacks leverage a complex network of interconnected components. The following table Artikels the key infrastructure elements involved:
| Component | Description | Example | Security Implications |
|---|---|---|---|
| Command & Control (C&C) Servers | Central servers that orchestrate the entire phishing campaign, managing communication with compromised systems and distributing phishing kits. | A server hosted in a data center with obfuscated IP addresses and using encrypted communication channels. | Securing these servers is paramount; compromise reveals the entire operation. |
| Email Delivery Systems | Services used to send phishing emails en masse. These can range from legitimate email providers (compromised or abused) to botnets and specialized email sending platforms. | Bulk email services, compromised SMTP servers, or botnets sending millions of emails. | Identifying and blocking these sources is vital to preventing delivery. |
| Phishing Kits | Pre-built, customizable templates for creating phishing websites. These kits often include features like credential harvesting, form submissions, and malware delivery. | Templates with pre-designed login pages mimicking legitimate services, often incorporating JavaScript for data exfiltration. | Constant updates and analysis are needed to identify and block new kits. |
| Payment Processors | Used to process payments for the phishing-as-a-service platform. These can be legitimate payment gateways or more clandestine methods. | Cryptocurrency exchanges, anonymous payment systems, or even gift card exchanges. | Tracing payments is difficult but essential for identifying and disrupting the operation. |
Email Delivery Methods
The success of a Flowerstorm phishing attack hinges on effectively delivering malicious emails. Several methods are employed to achieve widespread distribution:
Various methods are used to maximize the reach of these phishing emails, often employing a combination of techniques to circumvent security measures.
- Bulk Email Services: Legitimate bulk email services can be compromised or abused to send large volumes of phishing emails. This method offers a degree of anonymity, but leaves a digital trail that can be traced.
- Compromised SMTP Servers: Attackers often compromise legitimate email servers to send phishing emails, leveraging the server’s reputation to increase deliverability. This requires advanced technical skills to bypass security protocols.
- Botnets: Large networks of compromised computers (botnets) are used to send emails en masse, obscuring the origin and making it difficult to trace back to the attacker. The sheer volume can overwhelm email filters.
- Email Spoofing: Attackers forge email headers to make it appear as though the email originates from a trusted source, such as a bank or online retailer. This is a common tactic to deceive recipients.
Email Security Filter Bypass Techniques
Flowerstorm operators employ various techniques to evade email security filters:
These techniques aim to make the phishing emails appear legitimate and avoid detection by spam filters. The constant arms race between attackers and defenders makes this a dynamic challenge.
- Obfuscation: Attackers use techniques to hide malicious content within the email, making it difficult for filters to identify. This can involve encoding malicious links or using image-based URLs.
- Spoofing Techniques: Advanced spoofing techniques go beyond simply forging headers, involving manipulating various email metadata to appear authentic.
- Use of Legitimate Services: Leveraging compromised accounts on legitimate email providers can bypass many filters due to the sender’s established reputation.
- Dynamic Content: Using dynamic content in emails, generated at the time of delivery, makes it harder for filters to create effective signatures based on static email content.
The Role of Social Engineering
Social engineering is paramount to the success of Flowerstorm phishing. It involves manipulating human psychology to trick victims into clicking malicious links or revealing sensitive information.
Without effective social engineering, even the most technically sophisticated phishing campaign would likely fail. The human element is the weakest link in security.
- Urgency and Scarcity: Creating a sense of urgency or scarcity (e.g., “Your account will be suspended,” “Limited-time offer”) pressures victims into immediate action without critical thinking.
- Authority and Trust: Phishing emails often impersonate legitimate organizations or individuals to build trust and encourage victims to comply.
- Personalization: Using personal information obtained through data breaches or other means to personalize emails increases the chances of success. This makes the email appear more legitimate and trustworthy.
The Business Model of Flowerstorm Phishing as a Service
Flowerstorm Phishing as a Service (PaaS) operates on a lucrative, albeit morally reprehensible, business model. Its success hinges on providing a readily accessible and technically sophisticated platform for malicious actors, eliminating the need for extensive technical expertise and significantly lowering the barrier to entry for large-scale phishing campaigns. This translates into substantial profits for the providers, fueled by the sheer volume of potential clients and the high returns generated from successful phishing attacks.
The financial incentives are undeniably powerful. The providers profit directly from subscription fees, often tiered based on features and volume of phishing attempts. They also may profit indirectly through affiliate programs or by charging a percentage of the stolen funds, creating a perverse incentive structure that rewards successful criminal activity. The ease of use and scalability offered by Flowerstorm PaaS dramatically increase the potential for profit compared to individual phishing efforts.
Pricing Models for Flowerstorm Phishing as a Service
Flowerstorm PaaS providers typically employ a variety of pricing strategies to maximize revenue and cater to different customer needs. Common models include subscription-based access, offering varying levels of service and features at different price points. Some providers might charge per campaign, with prices scaling according to the complexity and targeted audience size. Others might operate on a revenue-sharing model, taking a percentage of the ill-gotten gains. The pricing often reflects the sophistication of the platform, the level of support provided, and the guaranteed success rate (or at least the claimed success rate) offered to clients. A hypothetical example could be a basic package offering 1000 email sends for $50, a premium package with advanced features and unlimited sends for $500 per month, or a custom package tailored to specific client needs at a negotiated price.
Marketing Strategies for Flowerstorm Phishing as a Service
Attracting customers to Flowerstorm PaaS requires a discreet yet effective marketing approach. Providers often leverage underground forums, dark web marketplaces, and peer-to-peer networks to reach their target audience. Marketing materials might emphasize the ease of use, the advanced features (like advanced email spoofing or social engineering tools), and the anonymity provided by the service. Testimonials or success stories, however fabricated, are commonly used to build trust and attract new customers. The marketing often focuses on the efficiency and cost-effectiveness compared to building and maintaining an in-house phishing operation.
Hypothetical Marketing Campaign for Flowerstorm Phishing as a Service
A hypothetical marketing campaign might utilize a multi-pronged approach. The campaign would focus on showcasing the ease of use and high success rate through carefully crafted videos demonstrating the platform’s capabilities. These videos would avoid explicit mention of illegal activity, instead highlighting the platform’s efficiency in delivering targeted messages and gathering information. The campaign might also utilize targeted advertising on dark web forums and marketplaces, focusing on the anonymity and security features of the service, and highlighting the competitive advantage offered by the platform compared to other similar services. A network of affiliates would be used to spread awareness and drive traffic to the platform. The entire campaign would be designed to subtly attract those seeking to conduct phishing campaigns, without overtly promoting illegal activities. The focus would be on presenting the platform as a powerful tool for various, unspecified, data collection purposes.
Legal and Ethical Considerations
Flowerstorm Phishing as a Service (PaaS) operates in a murky legal and ethical landscape, raising significant concerns for both the individuals and organizations involved. The potential for widespread harm, coupled with the often-anonymous nature of these services, makes addressing these concerns paramount. Understanding the legal ramifications and ethical dilemmas is crucial for mitigating the risks associated with this emerging threat.
Legal Ramifications for Individuals and Organizations
Individuals involved in Flowerstorm PaaS, whether as developers, operators, or clients, face serious legal consequences. Depending on jurisdiction, charges could range from conspiracy to commit fraud, aiding and abetting criminal activity, money laundering, and violations of data privacy laws like GDPR or CCPA. Organizations utilizing these services are equally vulnerable, facing potential lawsuits from victims, hefty fines from regulatory bodies, and reputational damage that can be devastating. The severity of penalties often depends on the scale of the phishing campaign and the resulting financial losses or data breaches. For example, a large-scale Flowerstorm PaaS operation leading to millions of dollars in losses could result in lengthy prison sentences and substantial financial penalties for all involved parties.
Ethical Concerns Surrounding Flowerstorm Phishing as a Service
The ethical implications of Flowerstorm PaaS are deeply troubling. These services facilitate the theft of sensitive information, financial fraud, and identity theft, causing significant harm to individuals and businesses. The anonymity offered by these platforms shields perpetrators, allowing them to operate with impunity and evade accountability. Furthermore, the ease of use provided by Flowerstorm PaaS lowers the barrier to entry for malicious actors, even those lacking technical expertise. This democratization of malicious activity is a significant ethical concern, potentially leading to a surge in phishing attacks and a widening digital divide between those who can protect themselves and those who cannot. The erosion of trust in online interactions is another major ethical consequence.
Vulnerabilities in the Flowerstorm Phishing as a Service Ecosystem
The Flowerstorm PaaS ecosystem itself is not without vulnerabilities. While designed for anonymity, these services often rely on various third-party infrastructure components, creating points of potential failure and exposure. Law enforcement agencies can leverage these vulnerabilities to track down operators and clients. For example, tracing financial transactions linked to the service or identifying compromised infrastructure components can lead to the identification and apprehension of individuals involved. Additionally, security researchers can uncover vulnerabilities within the Flowerstorm PaaS platform itself, potentially allowing for disruption of its operations or even the identification of its users.
Preventative Measures Against Flowerstorm Phishing Attacks
The threat posed by Flowerstorm PaaS necessitates a multi-faceted approach to prevention. Organizations and individuals should implement the following measures:
- Strengthening Email Security: Implementing robust email authentication protocols like SPF, DKIM, and DMARC can help prevent phishing emails from reaching inboxes.
- Employee Security Awareness Training: Educating employees about phishing tactics and best practices for identifying suspicious emails is crucial.
- Utilizing Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to gain access to accounts, even if they obtain credentials through phishing.
- Regular Security Audits and Penetration Testing: Identifying vulnerabilities in organizational systems helps prevent attackers from exploiting them.
- Monitoring Network Traffic for Suspicious Activity: Implementing intrusion detection and prevention systems can help identify and block malicious activity.
- Reporting Phishing Attempts: Promptly reporting suspected phishing attempts to relevant authorities can help in identifying and disrupting malicious operations.
Case Studies and Examples
Source: mdpi.com
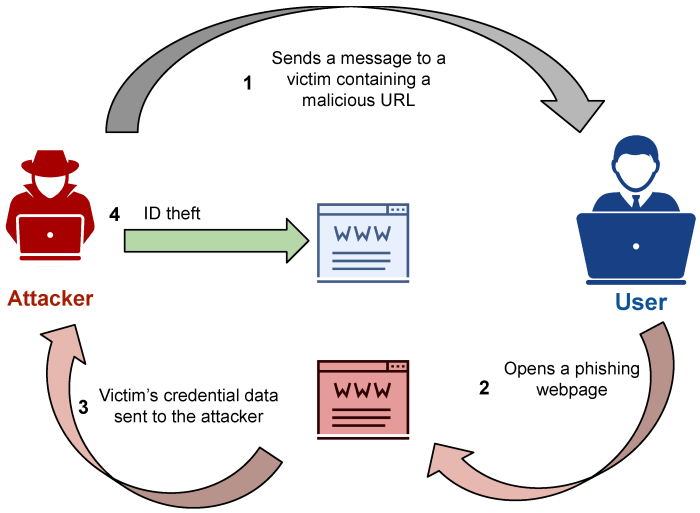
Understanding the real-world impact of Flowerstorm phishing-as-a-service requires examining both hypothetical scenarios and generalized examples of actual attacks. This helps illustrate the effectiveness of these techniques and highlights potential vulnerabilities.
Analyzing successful attacks, even hypothetical ones, allows us to understand the attacker’s methods, the targets’ vulnerabilities, and the potential consequences. This knowledge is crucial for developing effective countermeasures.
Hypothetical Flowerstorm Phishing Attack: The “Green Thumb” Campaign, Flowerstorm phishing as a service
This case study details a hypothetical Flowerstorm phishing attack targeting a small-to-medium sized enterprise (SME) specializing in organic gardening supplies. The attackers leveraged the SME’s reliance on email communication for ordering supplies from various vendors. The campaign, dubbed “Green Thumb,” used a sophisticated multi-stage approach.
| Timeline | Method | Target | Outcome |
|---|---|---|---|
| Week 1: Reconnaissance | Open-source intelligence gathering on the SME’s suppliers and communication patterns. | SME’s email infrastructure and supplier information. | Attackers identified key suppliers and typical email formats. |
| Week 2: Spear Phishing | Spoofed emails mimicking legitimate supplier invoices were sent to the SME’s accounts payable department. The emails contained malicious links leading to a fake login page. | Accounts payable staff. | One employee fell victim, entering login credentials on the fake page. |
| Week 3: Data Exfiltration | After gaining access, the attackers exfiltrated financial records, supplier contact information, and customer data. | SME’s internal network and databases. | Sensitive data was stolen and potentially sold on the dark web. |
| Week 4: Lateral Movement (Attempted) | Attackers attempted to move laterally within the network to gain access to other systems. | Internal servers and applications. | This attempt was unsuccessful due to existing network segmentation. |
Mitigation strategies for this hypothetical attack could have included multi-factor authentication (MFA) for all accounts, regular security awareness training for employees focusing on phishing detection, email authentication protocols like SPF, DKIM, and DMARC, and robust intrusion detection/prevention systems.
Examples of Real-World Flowerstorm Phishing Attacks
While specific details cannot be shared due to confidentiality concerns, several generalized examples illustrate the common characteristics of Flowerstorm phishing attacks. These attacks often target organizations with lax security practices, utilizing a combination of spear phishing, social engineering, and malware to achieve their goals. The scale of these attacks varies, from targeting individual employees to compromising entire organizational networks. In some cases, stolen credentials were used to launch further attacks, highlighting the cascading impact of successful Flowerstorm campaigns. Other attacks involved the deployment of ransomware, demanding payment for the release of critical data. The common thread in these examples is the use of readily available, inexpensive tools and services, making these attacks increasingly accessible to malicious actors.
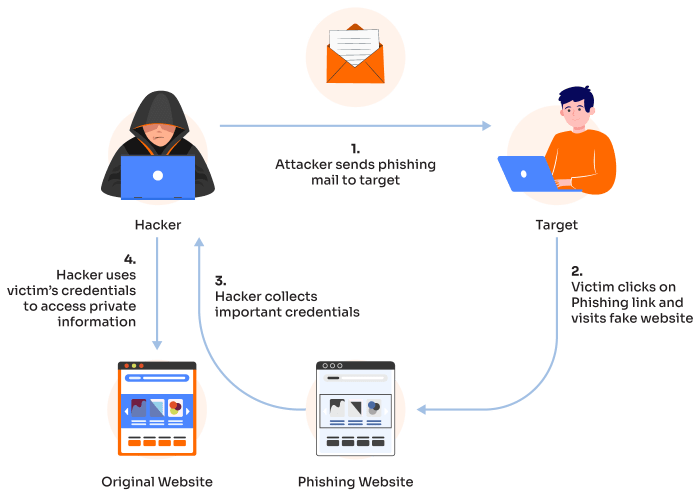
Concluding Remarks
Source: valimail.com
Flowerstorm phishing as a service represents a significant escalation in the cybercrime landscape. Its scalability, sophistication, and profitability make it a formidable threat to individuals and organizations alike. Understanding its mechanics, business model, and legal ramifications is crucial for developing effective countermeasures. While the fight against this digital menace is ongoing, awareness and proactive security measures are our strongest weapons. Remember, staying informed is the first step towards safeguarding yourself and your data in this ever-evolving digital battlefield.


