Eagerbee malware expands arsenal—that’s the chilling headline. This isn’t your grandpappy’s computer virus; we’re talking about a sophisticated piece of malicious code that’s gotten a serious upgrade. Imagine a digital ninja, suddenly armed with a whole new set of deadly weapons. That’s the threat Eagerbee now poses, and it’s time to understand just how dangerous it has become.
This enhanced malware isn’t just targeting your average user; it’s aiming for the jugular of corporate networks and sensitive data. From its sneaky infection methods to its devastating consequences, we’ll dissect Eagerbee’s new capabilities, exploring how it works, who it targets, and what you can do to protect yourself from its wrath. Get ready, because this isn’t a drill.
Eagerbee Malware
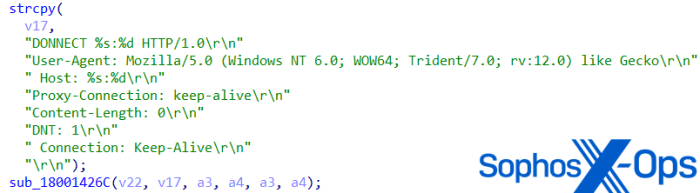
Source: sophos.com
Eagerbee, a relatively new player in the malware landscape, has quickly gained notoriety for its sophisticated techniques and adaptability. Unlike simpler malware that relies on brute force, Eagerbee exhibits a more nuanced approach, leveraging multiple infection vectors and employing advanced evasion tactics to remain undetected. Understanding its core functionalities and lifecycle is crucial for effective mitigation and prevention strategies.
Eagerbee Malware Core Functionalities
Eagerbee’s primary function is data exfiltration. It targets sensitive information, including credentials, financial data, and intellectual property. This is achieved through a combination of techniques, including keylogging, screen capturing, and file exfiltration. Furthermore, Eagerbee possesses the capability to establish persistent access on the compromised system, allowing for continued data theft and potential further malicious activities. The malware is also designed to self-propagate, expanding its reach across networks and maximizing its impact. It achieves this through various methods, including exploiting software vulnerabilities and leveraging social engineering tactics.
Eagerbee Malware Infection Vectors and Propagation Methods
Eagerbee primarily spreads through phishing emails containing malicious attachments or links. These attachments often appear as legitimate documents or software updates, tricking unsuspecting users into executing the malware. Another common vector is through compromised websites or software downloads. Once installed, Eagerbee employs various techniques to propagate, including exploiting vulnerabilities in network infrastructure to spread laterally within an organization’s network. The malware’s ability to evade detection makes it particularly dangerous, as it can remain active for extended periods without being discovered.
Eagerbee Malware Lifecycle Stages
The Eagerbee malware lifecycle can be broken down into several distinct stages. First, the initial infection occurs, usually through one of the previously mentioned vectors. Next, the malware establishes persistence, ensuring it remains active even after a system reboot. Then, the data exfiltration phase begins, where the malware collects and transmits stolen data to a command-and-control server. Finally, the malware may further propagate itself, infecting other systems within the network. This multi-stage approach enhances the malware’s effectiveness and resilience.
Comparison of Eagerbee with Other Malware Families
Eagerbee shares similarities with other advanced persistent threats (APTs), such as Carbanak and Lazarus, in its focus on data exfiltration and its use of sophisticated evasion techniques. However, unlike some APTs that target specific high-value targets, Eagerbee demonstrates a broader range of targets, suggesting a more opportunistic approach. Compared to simpler malware like ransomware, Eagerbee prioritizes stealth and long-term access over immediate disruption. This makes detection and remediation significantly more challenging.
Eagerbee Malware Components and Functions
| Component | Function | Component | Function |
|---|---|---|---|
| Downloader | Downloads additional malware components. | Persistence Module | Ensures the malware remains active after a system reboot. |
| Keylogger | Records keystrokes entered by the user. | Exfiltration Module | Steals and transmits data to a command-and-control server. |
| Screen Capture Module | Captures screenshots of the user’s activity. | Self-Propagation Module | Spreads the malware to other systems. |
Expanded Arsenal

Source: sectrio.com
Eagerbee malware, initially a relatively simple threat, has undergone a significant transformation. Its developers have dramatically expanded its capabilities, turning it into a far more dangerous and versatile tool for malicious actors. This evolution presents a growing threat to individuals and organizations alike, demanding a closer examination of its new functionalities and the potential damage they can inflict.
The enhanced Eagerbee malware now boasts a range of new capabilities, significantly increasing its effectiveness and the scope of its potential impact. These advancements go beyond simple data theft, introducing sophisticated evasion techniques and functionalities designed for persistent, stealthy operations. This makes detection and remediation significantly more challenging.
New Capabilities of Eagerbee Malware
The expanded Eagerbee arsenal includes several key enhancements. Most notably, the malware now incorporates advanced anti-analysis techniques, making it harder for security researchers and antivirus software to identify and neutralize it. It also features improved persistence mechanisms, ensuring it remains active on infected systems even after reboots. Furthermore, the malware has been equipped with lateral movement capabilities, allowing it to spread within a network, compromising multiple systems. Finally, the addition of data exfiltration tools allows for the seamless transfer of stolen information to remote servers controlled by the attackers.
Impact on Targeted Systems, Eagerbee malware expands arsenal
The consequences of an Eagerbee infection are far-reaching. The advanced anti-analysis techniques make detection difficult, potentially allowing the malware to remain undetected for extended periods, leading to significant data loss and financial damage. The improved persistence mechanisms guarantee the malware’s continued presence, hindering remediation efforts and potentially enabling long-term espionage or sabotage. Lateral movement capabilities amplify the damage, allowing the malware to infect numerous systems within a network, potentially paralyzing operations and causing widespread disruption. Finally, the efficient data exfiltration tools facilitate the theft of sensitive information, including intellectual property, financial data, and personal details, with potentially devastating consequences.
Security Risks to Individuals and Organizations
The expanded Eagerbee malware poses substantial risks to both individuals and organizations. Individuals risk identity theft, financial fraud, and reputational damage if their personal information is compromised. Organizations face significant financial losses due to data breaches, operational disruptions, and the cost of remediation. The potential for intellectual property theft and sabotage can also have long-term, crippling effects on a business. Furthermore, the malware’s stealthy nature can make it difficult to determine the extent of the damage, leading to prolonged recovery periods and increased costs.
Real-World Scenarios of Damage
Imagine a scenario where a small business is infected with the enhanced Eagerbee malware. The malware remains undetected for months, silently exfiltrating sensitive customer data and financial records. The attackers then use this information to perpetrate identity theft and financial fraud against the business’s clients, severely damaging its reputation and leading to significant financial losses. Simultaneously, the malware disables critical business systems, causing operational disruptions and lost revenue. In another scenario, a large corporation might suffer a breach impacting its intellectual property, potentially giving competitors a significant advantage. The subsequent investigation and remediation could cost millions.
Potential Targets of Eagerbee Malware
The expanded capabilities of Eagerbee make it a versatile tool, targeting various sectors. The attackers can tailor its functionalities to exploit vulnerabilities specific to each industry.
- Financial Institutions: Access to sensitive financial data, customer information, and internal systems.
- Healthcare Providers: Theft of patient records, disruption of medical services, and potential for ransomware attacks.
- Government Agencies: Compromise of sensitive government information, disruption of critical infrastructure, and potential for espionage.
- Manufacturing Companies: Disruption of production lines, theft of intellectual property, and potential for sabotage.
- Educational Institutions: Theft of student and faculty data, disruption of academic operations, and potential for ransomware attacks.
Eagerbee’s Impact on Various Systems
The expansion of the Eagerbee malware arsenal significantly broadens its potential for damage across various operating systems and network infrastructures. This enhanced capability allows for more sophisticated attacks, targeting vulnerabilities in specific applications and leading to potentially devastating consequences for both individual users and large organizations. Understanding its impact is crucial for effective mitigation strategies.
Eagerbee’s effects are multifaceted and depend heavily on the specific variant and the targeted system. While initial reports focused primarily on Windows, the expanded capabilities suggest a wider reach.
Eagerbee’s Impact on Windows Operating Systems
The malware’s expanded capabilities on Windows systems likely include enhanced persistence mechanisms, enabling it to survive reboots and system scans. It might leverage known vulnerabilities in common Windows applications like browsers or email clients to gain initial access. Once inside, Eagerbee could steal sensitive data such as credentials, financial information, and intellectual property. Furthermore, it could install additional malware, turning the infected machine into a botnet node for distributed denial-of-service (DDoS) attacks or other malicious activities. The impact ranges from data loss and financial fraud to complete system compromise and operational disruption.
Eagerbee’s Impact on MacOS and Linux Systems
While initially less prevalent, the expanded Eagerbee malware might now target MacOS and Linux systems, exploiting known vulnerabilities specific to these operating systems. For example, it could exploit vulnerabilities in less frequently updated applications or leverage weaknesses in system libraries. The impact on these systems could include data exfiltration, system instability, and the creation of backdoors for future access. However, the specific methods and extent of the impact will depend on the specific vulnerabilities exploited and the capabilities of the deployed variant.
Eagerbee’s Interaction with Network Infrastructure
Eagerbee’s interaction with network infrastructure is critical to its functionality and the scope of its potential damage. Once inside a system, it could scan the network for other vulnerable machines, creating a chain of infection. It might also establish command-and-control (C&C) channels to communicate with malicious actors, sending stolen data and receiving further instructions. Furthermore, the malware could exploit network protocols and vulnerabilities to move laterally within a network, gaining access to sensitive servers and databases. This lateral movement increases the potential damage exponentially.
Exploitation of Vulnerabilities in Specific Software Applications
The expanded Eagerbee malware likely exploits vulnerabilities in various software applications to gain initial access and maintain persistence. This could involve exploiting zero-day vulnerabilities (unknown vulnerabilities) or known vulnerabilities that haven’t been patched. Examples include exploiting vulnerabilities in web browsers to execute malicious code through drive-by downloads or leveraging vulnerabilities in email clients to deliver malicious attachments. The malware might also target specific enterprise applications, exploiting vulnerabilities to steal sensitive business data or disrupt operations.
Hypothetical Scenario: Eagerbee Attack on a Corporate Network
Imagine a scenario where an employee clicks a malicious link in a phishing email. This link downloads a seemingly harmless file containing the Eagerbee malware. The malware then uses known vulnerabilities in the company’s email client to gain a foothold on the employee’s machine. From there, it scans the network, identifying and exploiting vulnerabilities in other systems, including servers containing sensitive financial data. The malware exfiltrates this data to a remote server controlled by the attackers, causing significant financial losses and reputational damage to the company. The attackers might then use the compromised systems to launch further attacks against other organizations, using the corporate network as a springboard.
Mitigation and Countermeasures
Eagerbee malware, with its expanding arsenal of attack vectors, demands a proactive and multi-layered approach to security. Ignoring its potential impact can lead to significant data loss, financial damage, and reputational harm. Understanding how to mitigate the risks and effectively counter Eagerbee is crucial for both individuals and organizations. This section Artikels preventative measures, detection and removal strategies, data recovery processes, antivirus solution comparisons, and a robust security implementation guide.
Preventative Measures Against Eagerbee Infections
Proactive security is the first line of defense against Eagerbee and similar malware. A robust security posture minimizes the chances of infection and limits the malware’s potential damage. This involves a combination of software updates, secure browsing habits, and user education.
- Maintain updated software: Regularly update your operating system, applications, and antivirus software to patch known vulnerabilities exploited by Eagerbee.
- Practice safe browsing habits: Avoid clicking on suspicious links or downloading files from untrusted sources. Be wary of phishing emails and websites mimicking legitimate services.
- Use strong passwords: Employ complex and unique passwords for all online accounts, and consider using a password manager to streamline this process.
- Enable two-factor authentication (2FA): Whenever possible, enable 2FA for added security to your accounts, making unauthorized access significantly harder.
- Educate users: Regularly train users on cybersecurity best practices, including recognizing phishing attempts and avoiding risky online behaviors.
Detecting and Removing Eagerbee Malware
Detecting and removing Eagerbee requires a systematic approach, starting with identifying suspicious activity and then employing specialized tools for removal.
- Monitor system performance: Look for unusual slowdowns, high CPU or disk usage, or unexpected processes running in the background.
- Run a full system scan: Use a reputable antivirus program to conduct a thorough scan of your system for malware. This should detect and quarantine Eagerbee if present.
- Check for unusual network activity: Monitor your network traffic for suspicious outbound connections, which might indicate Eagerbee communicating with command-and-control servers.
- Utilize specialized malware removal tools: If the antivirus fails to completely remove Eagerbee, consider using specialized malware removal tools designed to handle persistent infections.
- Restore from a system backup: If the infection is severe, restoring your system from a clean backup is the safest option to ensure complete removal.
Data Recovery After Eagerbee Compromise
Data recovery after an Eagerbee infection can be challenging, depending on the extent of the damage. The process involves data recovery tools, backup restoration, and potentially professional assistance.
Data recovery options range from using data recovery software to restoring from backups. If backups are unavailable or corrupted, professional data recovery services might be necessary. The success rate depends on the type of data loss and the level of damage caused by Eagerbee.
Comparison of Antivirus Solutions Against Eagerbee
Various antivirus solutions offer varying levels of protection against Eagerbee. The effectiveness depends on the specific antivirus engine, its update frequency, and its ability to detect and neutralize new malware variants.
A comprehensive comparison would require testing multiple antivirus solutions against live Eagerbee samples. However, factors like real-time protection, heuristic analysis, and sandboxing capabilities are crucial for effective detection and prevention.
Implementing Robust Security Practices
Establishing robust security practices is vital for preventing future Eagerbee infections. This requires a layered approach that combines technical safeguards with user education and awareness.
- Regular software updates: Implement a system for automatically updating operating systems, applications, and antivirus software.
- Network security: Utilize firewalls, intrusion detection systems, and virtual private networks (VPNs) to protect your network from external threats.
- Data backups: Regularly back up important data to an offsite location, ensuring data protection in case of infection or system failure.
- Security awareness training: Conduct regular security awareness training for all users to educate them about phishing, malware, and other online threats.
- Incident response plan: Develop and regularly test an incident response plan to effectively handle malware infections and minimize their impact.
Future Trends and Predictions
Eagerbee’s current capabilities represent only the tip of the iceberg. Its modular design and demonstrated adaptability suggest a concerning trajectory for future iterations. The malware’s evolution will likely be driven by the continuous arms race between cybercriminals and security researchers, leading to increasingly sophisticated attacks and evasion techniques.
The expanded arsenal already showcased hints at this evolution. We can expect Eagerbee to become even more polymorphic, leveraging advanced obfuscation techniques to evade detection by traditional antivirus software. Furthermore, its ability to integrate with other malware families and exploit emerging vulnerabilities will undoubtedly increase, leading to more complex and devastating attacks.
Eagerbee’s Evolving Attack Vectors
The methods used to distribute and deploy Eagerbee will become increasingly subtle and difficult to trace. We might see a shift towards more targeted attacks, leveraging spear-phishing campaigns, zero-day exploits, and compromised legitimate software supply chains. The reliance on sophisticated social engineering techniques, coupled with the exploitation of human psychology, will become crucial in the malware’s success. For example, a future campaign might involve highly personalized phishing emails targeting specific individuals within a company, containing malicious attachments disguised as legitimate business documents. The success of such an attack hinges on the credibility of the email and the lack of awareness of the recipient.
Hypothetical Large-Scale Eagerbee Attack Scenario
Imagine a scenario where a highly advanced version of Eagerbee, leveraging AI-powered automation, simultaneously infects thousands of industrial control systems (ICS) across a critical infrastructure sector like energy or transportation. The malware’s polymorphic nature would allow it to evade detection, and its ability to self-propagate would exponentially amplify the impact. The coordinated attack could cripple operations, leading to widespread disruption, financial losses, and potentially even loss of life. The scale and complexity of such an attack would make containment extremely challenging, demanding a rapid and coordinated response from multiple agencies and organizations. This scenario draws parallels to the Stuxnet attack, albeit on a potentially far larger scale, exploiting vulnerabilities across diverse systems with sophisticated automation capabilities.
The Impact of AI on Eagerbee’s Development
The integration of artificial intelligence (AI) will significantly accelerate Eagerbee’s evolution. AI can automate various stages of the malware lifecycle, from vulnerability discovery and exploit development to evasion techniques and target selection. AI-powered machine learning algorithms could enable the malware to dynamically adapt to changing security landscapes, making it incredibly difficult to neutralize. This could manifest as self-learning capabilities, allowing the malware to improve its effectiveness over time by analyzing its interactions with security systems and adjusting its tactics accordingly. For example, AI could optimize the malware’s payload delivery to maximize its impact while minimizing detection, or even dynamically generate unique variations to evade signature-based detection. This resembles the development of autonomous weapons systems, where AI plays a significant role in the decision-making process, though in this case, the “decisions” are related to infecting and compromising systems.
Closure: Eagerbee Malware Expands Arsenal
Source: founderjar.com
The expansion of Eagerbee’s arsenal marks a significant escalation in the cyber threat landscape. While the initial version was concerning, the new capabilities showcased by this malware are nothing short of alarming. Understanding its evolution, potential targets, and mitigation strategies is crucial for both individuals and organizations. Staying informed and proactive in implementing robust security measures is no longer a luxury—it’s a necessity in this ever-evolving digital battlefield. The fight against Eagerbee, and malware like it, is far from over.


