D link routers under attack – D-Link routers under attack? It’s a scarier scenario than a dial-up modem screech. Millions rely on these devices, making them prime targets for hackers. This isn’t just about slow Wi-Fi; we’re talking potential data breaches, network disruptions, and even control of your entire home network. Let’s unpack the vulnerabilities, the attacks, and most importantly, how to protect yourself.
From brute-force password cracking to sophisticated malware injections, the methods used to compromise D-Link routers are diverse and constantly evolving. We’ll explore the technical nitty-gritty of these attacks, examining common vulnerabilities like buffer overflows and SQL injection. We’ll also delve into the real-world consequences, from stolen personal information to the potential for larger-scale network damage. But don’t worry, we’ll arm you with the knowledge and strategies to safeguard your network and stay ahead of the digital bad guys.
D-Link Router Vulnerabilities: D Link Routers Under Attack

Source: soyacincau.com
D-Link routers, like many other networking devices, have a history of security vulnerabilities. These weaknesses, often stemming from flawed software design or inadequate security practices, can leave users exposed to a range of attacks, from simple data breaches to complete device compromise. Understanding these vulnerabilities is crucial for maintaining a secure home or business network.
D-Link Router Vulnerabilities: A Historical Perspective
Significant security breaches involving D-Link routers have highlighted the need for robust security measures. These incidents have ranged from relatively minor vulnerabilities allowing for unauthorized access to critical flaws enabling remote code execution. While D-Link has released patches for many of these issues, the lag time between discovery and patching has often left many users vulnerable. One notable example (though specifics are difficult to pinpoint without naming a specific, publicly known breach, as many are patched quietly) might involve a vulnerability allowing attackers to gain administrative control, leading to data theft or network manipulation. The impact of these breaches often depends on the specific vulnerability exploited and the attacker’s goals.
Comparison with Other Brands
The vulnerability landscape for D-Link routers is not unique. Many networking device manufacturers have faced similar challenges, although the frequency and severity of vulnerabilities can vary. Some brands are perceived as having more robust security practices than others, leading to fewer publicly reported vulnerabilities. However, it’s important to remember that even seemingly secure brands can have hidden vulnerabilities, highlighting the need for constant vigilance and up-to-date firmware. The key is not to focus solely on brand reputation, but rather on actively managing security practices, including regular firmware updates and secure password usage.
Technical Aspects of Vulnerabilities
Many D-Link router vulnerabilities stem from common weaknesses in software design. Buffer overflows, for instance, occur when a program attempts to write data beyond the allocated buffer size, potentially allowing attackers to inject malicious code. SQL injection attacks exploit vulnerabilities in the router’s database interactions, allowing attackers to manipulate queries and potentially gain unauthorized access. Cross-site scripting (XSS) vulnerabilities can allow attackers to inject malicious scripts into web pages displayed by the router’s interface, potentially stealing user credentials or redirecting users to malicious websites. These are just a few examples of the technical flaws that can compromise D-Link routers.
Common D-Link Router Vulnerabilities
Understanding the specific vulnerabilities affecting D-Link routers is vital for mitigation. The following table summarizes some common examples, illustrating their potential impact. Note that the specific affected models can vary widely and details on CVE IDs are often not publicly released by the manufacturer. This is not an exhaustive list, and many more vulnerabilities exist.
| Vulnerability Type | CVE ID (if available) | Affected Models (Examples) | Potential Impact |
|---|---|---|---|
| Remote Code Execution | N/A (often undisclosed) | DIR-615, DIR-825, and others | Complete compromise of the router, allowing attackers to control the device and network. |
| Cross-Site Scripting (XSS) | N/A (often undisclosed) | DIR-600, DIR-850L, and others | Potential theft of user credentials or redirection to malicious websites. |
| Command Injection | N/A (often undisclosed) | DSL-2750U, DIR-605L, and others | Ability to execute arbitrary commands on the router, potentially allowing for complete control. |
| Denial of Service (DoS) | N/A (often undisclosed) | Various models | Making the router unavailable to legitimate users. |
Attack Vectors and Methods
D-Link routers, like many other internet-connected devices, are susceptible to various attack methods. These attacks exploit vulnerabilities in the router’s firmware, its default settings, or weaknesses in user security practices. Understanding these attack vectors is crucial for bolstering your home network’s security.
Attackers employ a range of techniques to compromise D-Link routers, often leveraging readily available tools and exploiting known vulnerabilities. These attacks can range from simple brute-force attempts to more sophisticated malware infections. The consequences can be severe, including data breaches, network hijacking, and the transformation of your router into a part of a botnet.
Common Attack Vectors
Several common attack vectors are used to compromise D-Link routers. These methods often exploit weaknesses in the router’s security configuration or known vulnerabilities in its firmware. Failing to update firmware and using weak passwords are significant contributing factors.
- Brute-force attacks: Attackers use automated tools to try numerous password combinations until they guess the correct one. This is particularly effective against routers with weak or default passwords.
- SQL injection: This technique involves injecting malicious SQL code into the router’s web interface to manipulate the database and gain unauthorized access. This is often exploited through vulnerabilities in the router’s web management portal.
- Cross-site scripting (XSS): Attackers inject malicious scripts into the router’s web interface to steal user credentials or redirect users to malicious websites. This exploits vulnerabilities in how the router handles user input.
- Malware infections: Malicious software can infect the router through various means, such as phishing emails, infected websites, or compromised devices on the network. Once infected, the malware can provide attackers with remote access to the router.
Malware Targeting D-Link Routers
While specific malware strains targeting *only* D-Link routers aren’t widely publicized (due to the attackers’ desire for secrecy), many generic router malware strains can and do infect D-Link devices. These often leverage known vulnerabilities in the firmware or weak security configurations. Examples include Mirai and its variants, which are known to infect large numbers of IoT devices, including routers from various manufacturers, to create botnets used for DDoS attacks. The malware often propagates through automated scanning and exploitation of known vulnerabilities.
Gaining Initial Access
Attackers typically gain initial access to vulnerable routers through a combination of techniques. They may exploit known vulnerabilities in the router’s firmware, guess default or weak passwords, or use phishing techniques to trick users into revealing their credentials. Often, a successful attack leverages a combination of these methods, starting with automated scans to identify vulnerable devices and then employing targeted attacks based on the identified vulnerabilities. For example, an attacker might scan for routers using default credentials and then attempt to exploit known vulnerabilities in the identified routers’ firmware.
Typical Attack Scenario, D link routers under attack
A typical attack might unfold as follows:
1. Scanning: The attacker uses automated tools to scan the internet for vulnerable D-Link routers, looking for devices with default passwords or known firmware vulnerabilities.
2. Exploitation: Once a vulnerable router is identified, the attacker attempts to exploit a known vulnerability, such as a command injection flaw or a weak password.
3. Access Gain: If successful, the attacker gains access to the router’s administrative interface.
4. Compromise: The attacker installs malware on the router, granting persistent remote access and potentially turning it into a botnet node.
5. Control and Exploitation: The attacker uses the compromised router for malicious activities such as DDoS attacks, data theft, or further network infiltration.
Visual Representation of a Successful Attack
Imagine a diagram with five distinct stages represented by boxes connected by arrows.
Box 1: Scanning: This box shows a computer screen displaying a network map with many routers highlighted in different colors, indicating vulnerability levels. Some routers are clearly labeled “D-Link,” and a few are highlighted in red, indicating vulnerability.
Box 2: Exploitation: This box depicts a close-up of a terminal window showing the attacker using a tool to exploit a vulnerability (e.g., a command injection script targeting a specific D-Link firmware version).
Box 3: Access Gain: This box shows the attacker’s computer screen displaying the router’s administrative interface, with various configuration options visible. A success message is clearly visible.
Box 4: Compromise: This box illustrates the installation of malware on the router. A visual representation of malware code injecting itself into the router’s system could be used.
Box 5: Control and Exploitation: This box shows the attacker’s computer screen displaying a control panel that allows them to manage the compromised router and use it for malicious activities, such as launching a DDoS attack or stealing data. A map depicting numerous internet targets under attack could be included. The arrows connecting the boxes represent the progression of the attack.
Impact and Consequences

Source: dlink.com
A compromised D-Link router represents a significant security risk, potentially impacting both the individual owner and the broader network it connects to. The consequences can range from minor inconveniences to severe financial and legal repercussions, depending on the nature of the attack and the data accessed. Understanding these potential impacts is crucial for proactive security measures.
The severity of the consequences hinges on several factors, including the type of vulnerability exploited, the attacker’s goals, and the level of protection implemented by the router owner. A seemingly minor vulnerability could be leveraged to gain complete control of the network, while a more sophisticated attack might target specific data or devices. The lack of regular updates and strong passwords significantly increases the risk of compromise.
Data Breaches and Theft
A compromised D-Link router can provide attackers with access to a wealth of sensitive information traversing the network. This includes passwords stored in web browsers and applications, personal financial details, email communications, photos, videos, and other confidential documents. Furthermore, the router itself may store log files containing network activity data, potentially revealing browsing habits and other sensitive information about the network users. The attacker might also use the compromised router to intercept and decrypt communications, leading to a significant privacy violation. For example, an attacker could intercept online banking transactions, leading to financial losses for the user.
Network Performance Degradation and Instability
Successful attacks on D-Link routers can significantly impact network performance and stability. Attackers might overload the router with traffic, causing slowdowns or complete outages. They could also install malware that consumes system resources, leading to instability and unpredictable behavior. Imagine a scenario where a family’s internet access is completely disrupted because of a compromised router, affecting their work, education, and communication. This disruption can extend beyond the immediate household, impacting other devices and users on the network. In more severe cases, the compromised router could be used as a launchpad for further attacks on other devices within the network or even beyond, turning it into a part of a larger botnet.
Real-World Examples of Significant Harm
Numerous real-world incidents illustrate the devastating consequences of compromised D-Link routers. While specific details of many incidents are not publicly available due to privacy concerns and ongoing investigations, news reports have documented cases where compromised routers have been used to launch distributed denial-of-service (DDoS) attacks, targeting websites and online services. Other incidents have involved the theft of sensitive personal data, leading to identity theft and financial losses for victims. These incidents underscore the need for proactive security measures and regular software updates. The Mirai botnet, for instance, famously utilized vulnerable IoT devices, including routers, to launch massive DDoS attacks, demonstrating the far-reaching impact of such compromises.
Legal and Financial Repercussions
The potential legal and financial repercussions for individuals and organizations resulting from a compromised D-Link router are significant.
- Financial Losses: Identity theft, unauthorized financial transactions, and the costs associated with remediation and recovery efforts can lead to substantial financial losses.
- Legal Liability: Organizations may face legal action from customers or regulatory bodies for failing to adequately protect sensitive data. Individuals may also face legal consequences if their compromised router is used to commit crimes.
- Reputational Damage: For organizations, a data breach resulting from a compromised router can severely damage their reputation, leading to loss of customer trust and business.
- Regulatory Fines: Non-compliance with data protection regulations can result in significant fines and penalties.
- Insurance Claims: While insurance may cover some losses, the process of filing claims and obtaining reimbursement can be complex and time-consuming.
Mitigation and Prevention Strategies
Securing your D-Link router is crucial in today’s digital landscape. A compromised router can expose your entire network to attacks, leading to data breaches, identity theft, and financial loss. Implementing robust security measures is not just a good idea; it’s a necessity. This section Artikels practical steps to significantly reduce your vulnerability.
Proactive security is far more effective and less costly than reactive damage control. By taking the steps Artikeld below, you can significantly bolster your home or small business network’s resilience against attacks targeting your D-Link router.
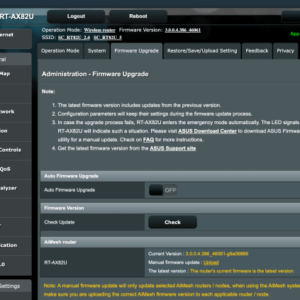
Router Firmware Updates
Regularly updating your D-Link router’s firmware is paramount. Firmware updates often include critical security patches that address known vulnerabilities. Failing to update leaves your router susceptible to exploits that could have been prevented. Check the D-Link website regularly for updates, and enable automatic updates if your router supports this feature. Outdated firmware is like leaving your front door unlocked – an open invitation for trouble. Think of it as a regular software checkup for your digital home’s gateway.
Strong and Unique Passwords
Using a strong, unique password for your router’s administration interface is non-negotiable. Avoid easily guessable passwords like “password” or “123456.” Instead, opt for a complex password that combines uppercase and lowercase letters, numbers, and symbols. A password manager can help you generate and securely store strong, unique passwords for all your devices, including your router. Consider a passphrase – a longer, more memorable string of words – as an alternative. Remember, a weak password is the weakest link in your network’s security chain.
Robust Network Security Measures
Implementing a multi-layered security approach is essential. This includes enabling the router’s built-in firewall, configuring access control lists (ACLs) to restrict access to specific devices or services, and regularly monitoring network activity for suspicious behavior. Consider using a Virtual Private Network (VPN) for added security, especially when using public Wi-Fi networks. A VPN encrypts your internet traffic, making it more difficult for attackers to intercept your data. Think of this as building a fortress around your network, making it significantly harder for intruders to breach.
Firewall Configurations
D-Link routers offer various firewall configurations, ranging from basic to advanced. The default firewall settings often provide a reasonable level of protection, but customizing them can enhance security. Understanding the different firewall types (e.g., stateful inspection firewalls) and configuring appropriate rules based on your network needs is crucial. Consider enabling features like intrusion detection/prevention systems (IDS/IPS) if available. Choosing the right firewall configuration is like selecting the best lock for your door – it needs to be strong enough to deter intruders, but also easy to use for authorized access. Experimenting with different configurations requires technical knowledge; if uncertain, consult online resources or seek professional help.
Responding to a Compromised Router
So, you suspect your D-Link router might be acting…suspiciously. Maybe it’s slower than a snail on Valium, or your internet connection keeps dropping like a bad habit. Don’t panic! While a compromised router is a serious issue, taking swift action can minimize the damage. This guide will walk you through identifying the problem, fixing it, and preventing future attacks.
Identifying Signs of Compromise is crucial in preventing further damage. A compromised router can act as a gateway for malicious activity, potentially exposing your entire network to hackers.
Signs of a Compromised Router
Several indicators suggest your D-Link router might be under attack. Noticeably slower internet speeds, even when no other devices are heavily using the network, are a major red flag. Unusual network activity, like unexpected login attempts or unfamiliar devices connected to your Wi-Fi, warrants immediate investigation. Furthermore, a router exhibiting strange behavior, such as constantly restarting or displaying error messages you’ve never seen before, could point to a security breach. Finally, be wary of changes to your router’s settings, particularly if you haven’t made them yourself. These subtle clues, taken together, can signal a serious problem.
Resetting the Router to Factory Settings
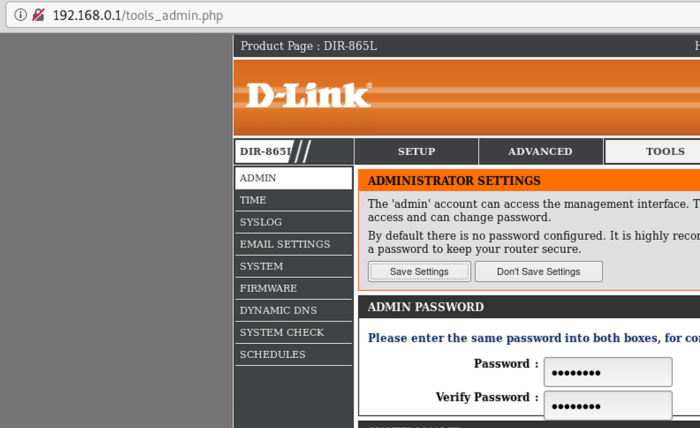
If you suspect a compromise, resetting your D-Link router to its factory settings is often the most effective first step. This will erase all custom configurations and remove any malicious software or unauthorized access. The process typically involves locating a small reset button on the router’s casing (often a tiny pinhole), holding it down for several seconds (usually 10-30 seconds) using a paperclip or similar object, while the router is powered on. This action will wipe the router clean, returning it to its original state. Remember, this will require you to reconfigure your Wi-Fi network name (SSID), password, and other settings after the reset.
Restoring Data and Configurations After a Security Incident
After resetting your router, you’ll need to reconfigure your network settings. Begin by connecting your computer directly to the router using an Ethernet cable. Then, access the router’s administration interface through your web browser (usually by typing an address like 192.168.0.1 or 192.168.1.1 into the address bar). Use your new admin password (set during the initial setup). Carefully recreate your network settings, including the Wi-Fi name and password, and any other custom configurations you previously had. If you backed up your router settings before the incident, restoring from this backup can save you time and effort, but be cautious – a compromised backup could reintroduce the problem. Remember to change all passwords for your network devices (including routers, computers, and smartphones) to prevent future attacks.
Checklist for Responding to a D-Link Router Security Breach
- Disconnect from the Internet: Immediately disconnect your router from the internet to prevent further compromise.
- Change your router’s admin password: Choose a strong, unique password that’s difficult to guess.
- Check for unusual network activity: Monitor your router’s logs for suspicious connections or login attempts.
- Reset your router to factory settings: This will remove any malicious software and unauthorized access.
- Update the router’s firmware: Ensure your router is running the latest firmware version to patch any known vulnerabilities.
- Change all network device passwords: Update passwords for all your computers, smartphones, and other devices connected to your network.
- Run a malware scan on all connected devices: Check for any malware that might have been installed during the attack.
- Monitor your network traffic: Keep an eye on your network for any unusual activity after the reset.
- Consider professional help: If you’re unsure about any step, seek assistance from a cybersecurity professional.
Conclusion
Source: paloaltonetworks.com
In the ever-evolving landscape of cybersecurity, protecting your D-Link router is paramount. Understanding the vulnerabilities, recognizing attack vectors, and implementing robust security measures are crucial steps in safeguarding your data and network integrity. While the threat is real, proactive measures, including regular firmware updates, strong passwords, and a vigilant approach to network security, can significantly mitigate the risk. Stay informed, stay protected, and keep those hackers at bay!