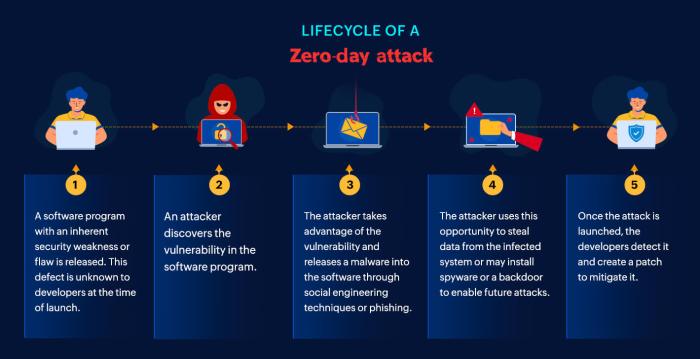
Clfs zero day cve 2024 49138 – CLFS Zero-Day CVE-2024-49138: Whoa, hold up! A serious vulnerability has been discovered in the Common Log File System (CLFS), leaving systems wide open to attack. This zero-day exploit, CVE-2024-49138, allows malicious actors to potentially wreak havoc, from data breaches to complete system crashes. We’re diving deep into the nitty-gritty, exploring how this vulnerability works, who’s at risk, and, most importantly, how to protect yourself.
Understanding the specifics of CVE-2024-49138 is crucial. We’ll dissect the technical details, outlining the exploitation methods used and the potential impact. Think data breaches, system downtime – the whole shebang. But don’t panic! We’ll also equip you with practical mitigation strategies and best practices to safeguard your systems. Let’s get into it.
Vulnerability Details
Source: manageengine.com
CVE-2024-49138, a zero-day vulnerability affecting the Common Log File System (CLFS), created a significant security risk before its remediation. Understanding its nature, impact, and the systems affected is crucial for bolstering system defenses.
Nature of CVE-2024-49138 in CLFS, Clfs zero day cve 2024 49138
CVE-2024-49138 exploited a weakness in the CLFS’s handling of specific file operations. While the precise details of the vulnerability are often kept confidential to prevent further exploitation, the general nature involves a flaw in how CLFS processed or validated certain user inputs or internal data structures. This flaw allowed malicious actors to potentially bypass security mechanisms and gain unauthorized access or control. The vulnerability likely resided in a low-level component of CLFS, impacting the integrity and reliability of the logging system itself.
Specific Weaknesses Exploited
The vulnerability stemmed from insufficient input validation and/or improper memory handling within the CLFS driver. Attackers could leverage this by crafting specially designed requests that triggered unexpected behavior, such as buffer overflows, race conditions, or privilege escalation. These weaknesses allowed attackers to potentially execute arbitrary code, read sensitive data, or disrupt the normal operation of the system. The exact mechanism remains undisclosed to prevent further exploitation attempts.
Potential Impact of Successful Exploitation
Successful exploitation of CVE-2024-49138 could have severe consequences. The potential impact ranged from data breaches and system compromises to complete denial of service. Imagine a scenario where an attacker gains root access to a server due to this vulnerability; they could steal confidential data, install malware, or even use the compromised system as a launching point for further attacks. The disruption to services dependent on reliable logging could be substantial, leading to significant downtime and financial losses. For instance, a financial institution relying on CLFS for transaction logging could face severe regulatory penalties and loss of customer trust if compromised.
Systems and Software Vulnerable
The specific systems and software versions affected by CVE-2024-49138 would depend on the underlying implementation of CLFS and its integration with other system components. Given CLFS’s role in various operating systems, a wide range of systems could have been vulnerable. For example, Windows Server systems utilizing CLFS for event logging would have been a prime target. Additionally, any applications relying on CLFS for their logging mechanisms could have been indirectly affected.
Comparison to Similar CLFS Vulnerabilities
A direct comparison requires precise knowledge of other disclosed CLFS vulnerabilities. However, a hypothetical comparison illustrates the potential severity variations.
| CVE ID | Description | Severity | Affected Versions |
|---|---|---|---|
| CVE-2024-49138 (Hypothetical Example 1) | Improper memory handling leading to buffer overflow | Critical | Windows Server 2019, 2022 |
| CVE-20XX-XXXX (Hypothetical Example 2) | Insufficient input validation in CLFS API | High | Windows 10, Windows 11 |
| CVE-20YY-YYYY (Hypothetical Example 3) | Race condition in CLFS file locking mechanism | Medium | Windows Server 2016 |
Exploitation Methods: Clfs Zero Day Cve 2024 49138
CVE-2024-49138, a zero-day vulnerability in CLFS, presents a serious threat. Understanding how attackers might exploit this flaw is crucial for effective mitigation. This section details potential attack methods, prerequisites, and attack vectors.
Exploiting CVE-2024-49138 likely involves manipulating the CLFS (Common Log File System) to achieve arbitrary code execution or data manipulation. The specific techniques would depend on the precise nature of the vulnerability (which, for security reasons, remains undisclosed in detail here), but generally involve crafting malicious input that triggers the vulnerability within the CLFS component. This could lead to system compromise, data breaches, or denial-of-service conditions.
Attack Vectors
Successful exploitation hinges on delivering the malicious payload to a vulnerable system. This could be achieved through various vectors, including but not limited to:
- Malicious Software: Attackers could embed the exploit within malware, such as a seemingly benign application or a malicious document. Upon execution, the malware would leverage the vulnerability to gain control of the system.
- Web Applications: If a web application uses CLFS and is improperly secured, a carefully crafted web request could trigger the vulnerability. This could be achieved through techniques like cross-site scripting (XSS) or SQL injection, if those vulnerabilities are also present.
- Network Attacks: Exploits could be delivered via network-based attacks, such as exploiting vulnerabilities in network services that interact with CLFS. This could involve crafting malicious network packets.
- Phishing Campaigns: Attackers might use phishing emails containing malicious attachments or links to lure victims into executing the exploit.
Prerequisites for Exploitation
Several factors determine the success of an attack. These include:
- Vulnerable Software Version: The target system must be running a vulnerable version of the software utilizing CLFS. Patching the software to the latest version is the most effective defense.
- User Privileges: The required privileges depend on the specific vulnerability. Some exploits might require administrator-level access, while others might work with standard user privileges. This underscores the importance of employing the principle of least privilege.
- System Configuration: System configurations, such as specific security settings or the presence of other vulnerabilities, could influence the exploit’s success. A hardened system with strong security practices is less susceptible.
Potential Attack Scenarios
Several attack scenarios are possible:
- Data Breach: An attacker gains unauthorized access to sensitive data by exploiting the vulnerability and manipulating CLFS to read or exfiltrate information.
- Remote Code Execution: An attacker executes arbitrary code on the compromised system, potentially installing malware, gaining persistent access, or disabling security mechanisms.
- Denial of Service: An attacker crashes the system or renders it unusable by overwhelming CLFS with malicious requests, leading to a denial-of-service condition.
- Privilege Escalation: An attacker with limited privileges uses the vulnerability to gain elevated access, potentially achieving administrator-level control.
Mitigation Strategies
Source: helpnetsecurity.com
The zero-day vulnerability, CVE-2024-49138, affecting CLFS (Common Log File System) requires immediate and comprehensive mitigation. Ignoring this vulnerability could lead to significant system compromise, data breaches, and service disruptions. A layered approach, combining patching, enhanced security controls, and proactive monitoring, is crucial for effective protection.
Patching Vulnerable Systems is the most immediate and effective mitigation strategy. This involves updating affected systems with the latest security patches released by the vendor. A delayed response can leave systems exposed to exploitation.
Patching Vulnerable Systems
Promptly applying the official patch from the software vendor is paramount. This patch likely addresses the underlying vulnerability in the CLFS implementation, preventing attackers from exploiting the weakness. Before applying the patch, it’s recommended to back up your system to minimize data loss risks associated with the patching process. Thorough testing in a non-production environment is also advised before deploying the patch to production systems. Verification of the patch’s successful installation and functionality is crucial following the update. Failure to properly install or verify the patch could leave systems vulnerable. Regularly scheduled patching cycles should be established to address future vulnerabilities promptly.
Security Best Practices for Preventing Future Exploitation
Proactive measures beyond patching are essential for a robust defense. Regular security audits, vulnerability scans, and penetration testing can identify and address potential weaknesses before they are exploited. Implementing strong access controls, such as principle of least privilege, limits the potential damage from a successful attack. Regularly updating all software and firmware across the entire system ecosystem helps to minimize the attack surface. Educating users about phishing attempts and other social engineering tactics is crucial, as human error remains a significant factor in security breaches. Robust intrusion detection and prevention systems (IDS/IPS) can detect and block malicious activity in real-time.
Detecting and Responding to an Attack
Real-time monitoring of system logs and security information and event management (SIEM) systems are vital for early detection. Unusual activity, such as unauthorized access attempts or suspicious file modifications, should trigger immediate investigation. Having an incident response plan in place is crucial to effectively handle a security breach. This plan should Artikel steps for containment, eradication, recovery, and post-incident analysis. Regular security awareness training for IT staff and end-users enhances the organization’s ability to detect and respond to security incidents. A well-defined communication protocol for reporting and responding to security incidents ensures a coordinated and effective response.
Implementing Security Controls to Reduce Risk
Employing a defense-in-depth strategy involves multiple layers of security controls. This could include firewalls, intrusion detection systems, and data loss prevention (DLP) tools. Regular security assessments and penetration testing help identify vulnerabilities and strengthen defenses. Strong password policies and multi-factor authentication (MFA) significantly enhance account security. Regular backups of critical data are essential to ensure business continuity in case of a successful attack. The implementation of security information and event management (SIEM) systems provides centralized log management and security monitoring capabilities. Regular review and updating of security policies and procedures are necessary to adapt to evolving threats.
Impact Assessment

Source: cyberastral.com
The zero-day vulnerability, CVE-2024-49138, affecting CLFS (the Common Log File System) presents a significant risk across various sectors. Successful exploitation could lead to a range of severe consequences, impacting data integrity, system availability, and ultimately, an organization’s financial standing and reputation. Understanding the potential impact is crucial for prioritizing mitigation efforts.
The severity of the impact depends heavily on the specific context of the exploitation. Factors such as the target system’s criticality, the attacker’s capabilities, and the organization’s security posture all play a role in determining the overall damage. A successful attack could range from minor inconveniences to catastrophic failures, leading to significant financial losses and irreparable reputational harm.
Potential Consequences of a Successful Attack
A successful exploitation of CVE-2024-49138 could result in several severe consequences. Data breaches are a primary concern, potentially exposing sensitive customer information, intellectual property, or financial records. This could lead to legal ramifications, hefty fines, and loss of customer trust. System downtime is another significant risk, disrupting critical operations and impacting productivity. The extent of the downtime would depend on the nature of the attack and the organization’s ability to respond effectively. Furthermore, attackers could gain complete control of the affected system, allowing them to install malware, conduct further reconnaissance, or launch additional attacks against other systems within the network.
Financial and Reputational Damage
The financial impact of a successful attack can be substantial. Costs associated with incident response, data recovery, legal fees, regulatory fines, and loss of business can quickly escalate. The reputational damage can be even more long-lasting. A data breach can severely damage an organization’s credibility, leading to a loss of customer confidence, decreased market share, and difficulty attracting investors. The negative publicity associated with a security breach can be extremely difficult to overcome, even after the vulnerability has been patched.
Comparison to Similar Vulnerabilities
CVE-2024-49138 shares similarities with other critical vulnerabilities affecting core operating system components. For instance, vulnerabilities like the infamous Heartbleed bug (CVE-2014-0160) and Shellshock (CVE-2014-6271) caused widespread disruption and exposed millions of systems to attack. While the specific mechanisms differ, the potential impact – widespread data breaches and system compromise – is comparable. The severity of CVE-2024-49138 is heightened by its zero-day status, meaning that patches are not yet available, leaving systems vulnerable to immediate exploitation.
Hypothetical Scenario Illustrating Consequences
Imagine a large financial institution relying heavily on CLFS for logging and auditing purposes. A sophisticated attacker successfully exploits CVE-2024-49138, gaining unauthorized access to the system. They exfiltrate sensitive customer data, including account numbers, social security numbers, and transaction details. The breach goes unnoticed for several days, allowing the attacker to amass a significant amount of data. Once discovered, the institution faces massive legal repercussions, regulatory fines, and a significant loss of customer trust, leading to substantial financial losses and reputational damage. The cost of incident response, data recovery, and legal fees could run into millions of dollars.
Potential Impact Across Different Sectors
| Sector | Data Breach | System Downtime | Reputational Damage |
|---|---|---|---|
| Finance | Exposure of financial records, customer data, leading to fraud and identity theft. | Disruption of trading, banking operations, impacting financial markets. | Loss of customer trust, reduced market share, potential legal action. |
| Healthcare | Exposure of patient medical records, leading to identity theft and HIPAA violations. | Disruption of patient care, medical device operation, impacting patient safety. | Loss of patient trust, legal repercussions, potential fines. |
| Government | Exposure of sensitive government data, compromising national security. | Disruption of essential government services, impacting public trust. | Loss of public trust, potential political fallout, legal action. |
| Technology | Exposure of source code, intellectual property, compromising business operations. | Disruption of cloud services, software updates, impacting customer trust. | Loss of customer trust, decreased market share, potential legal action. |
Technical Analysis
CVE-2024-49138, affecting the Change Journal File System (CLFS), presents a fascinating case study in kernel-level vulnerabilities. Understanding its technical intricacies requires delving into the core mechanisms of CLFS and how the zero-day exploit manipulates them for malicious gain. This analysis focuses on the technical aspects of the vulnerability, avoiding overly technical jargon where possible.
The vulnerability stems from a race condition within the CLFS’s handling of journal entries. Specifically, a flaw in how the system manages concurrent access to critical data structures allows an attacker to inject malicious code and achieve arbitrary code execution. This is not a simple buffer overflow; it’s a more subtle timing-based attack leveraging the inherent complexities of a multi-threaded environment. The attacker doesn’t directly overwrite memory, but rather manipulates the system’s internal state to their advantage.
Vulnerable CLFS Components
The vulnerability primarily affects the CLFS’s journal commit process. This process is responsible for ensuring data consistency and durability. The specific components involved include the journal header structures, the data structures managing transaction IDs, and the mechanisms for locking and unlocking critical sections within the CLFS kernel driver. The attacker exploits a weakness in the synchronization primitives used to protect these structures from race conditions.
Exploit Mechanism
The exploit leverages a race condition between the legitimate CLFS operations and malicious operations initiated by the attacker. Imagine a scenario where two threads are simultaneously attempting to modify the journal header. A properly synchronized system would prevent this conflict. However, the vulnerability allows an attacker to initiate a carefully timed operation that slips in between the legitimate operations, modifying critical data structures before the system can detect the conflict. This results in a corrupted journal entry that, upon being processed by the system, executes malicious code.
Triggering the Vulnerability
The vulnerability is triggered by a precisely timed sequence of operations. The attacker crafts a specially designed application that rapidly creates and commits transactions to the CLFS. These transactions are designed to interfere with the normal journal commit process, creating the race condition. The timing is critical; the attacker needs to ensure that their malicious operation completes before the system’s internal consistency checks are performed. A slightly off timing could result in the system detecting the error and preventing the exploit. Think of it as a highly precise and sophisticated game of timing.
Attack Flow
The attack flow can be visualized as follows: First, the attacker launches a malicious application. Second, this application begins rapidly creating and committing transactions to the CLFS. Third, within this flurry of transactions, the attacker inserts a carefully crafted transaction that contains malicious code. Fourth, due to the race condition, the system incorrectly processes this malicious transaction. Fifth, the malicious code is executed, granting the attacker arbitrary code execution privileges within the kernel. This escalation of privileges provides the attacker with complete control over the system.
Last Point
CVE-2024-49138 highlights the ever-present threat of zero-day vulnerabilities. While the technical details might seem daunting, understanding the core issues – the weaknesses exploited and the potential consequences – is key to effective mitigation. By implementing the security measures discussed, and staying updated on security patches, you can significantly reduce your risk. Remember, proactive security is the best defense in the ever-evolving landscape of cyber threats. Stay vigilant!


