Samsung 0-Click Vulnerability Fixed
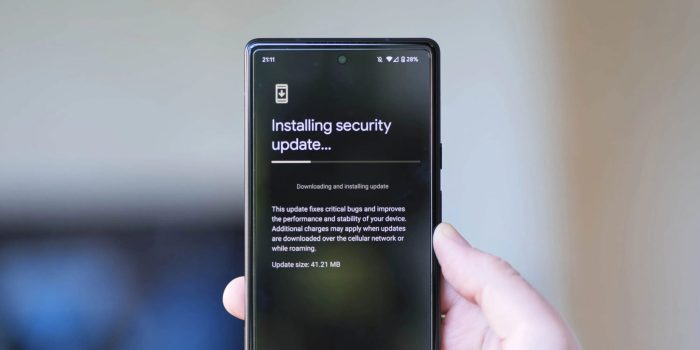
Samsung 0 click vulnerability fixed – Samsung 0-click vulnerability fixed! Phew, that’s a relief, right? Remember that terrifying zero-click exploit that let hackers into your phone without you even touching it? The one that made headlines and had everyone scrambling for updates? Yeah, that’s officially been patched. But before you breathe a sigh of complete … Read more