Black Basta abusing Teams chat for nefarious purposes? It sounds like a cyberpunk thriller, but it’s a chilling reality. This ransomware group isn’t just encrypting data; they’re infiltrating the very fabric of your communication, using Microsoft Teams as a backdoor to wreak havoc. Think of it: your everyday chat app, suddenly weaponized against your company. We’ll delve into the sneaky tactics Black Basta uses to compromise Teams accounts, how they exploit these breaches for lateral movement, and the devastating consequences for organizations caught in their crosshairs.
From subtle phishing campaigns to cleverly disguised malicious files, Black Basta’s mastery of social engineering is a masterclass in deception. We’ll unpack their methods, explore the damage they inflict – financial losses, reputational damage, operational disruptions – and arm you with the knowledge to defend against this evolving threat. Get ready to learn how to spot the red flags, implement robust security measures, and protect your organization from this insidious attack vector.
Defining “Black Basta” and its Activities
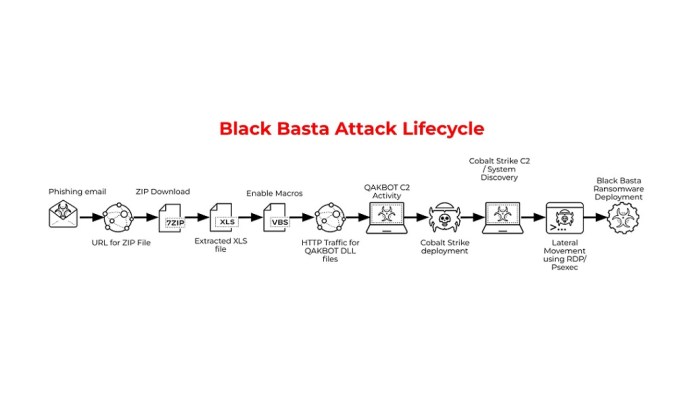
Black Basta is a prolific ransomware-as-a-service (RaaS) group that emerged in 2022, quickly establishing itself as a significant threat in the cybercrime landscape. Unlike some groups that focus solely on encryption, Black Basta distinguishes itself through a dual extortion model, combining data encryption with the theft and subsequent publication of sensitive data. This aggressive approach significantly increases the pressure on victims to pay ransoms.
Black Basta’s operational methods are characterized by a sophisticated and highly organized approach. Their attacks typically begin with initial access, often achieved through exploiting vulnerabilities in exposed systems or employing phishing campaigns. Once inside a network, they move laterally, mapping the system and identifying high-value data. This data is then exfiltrated before the encryption process begins, ensuring a secondary pressure point for victims even if they manage to recover from the encryption.
Operational Methods of Black Basta
Black Basta leverages a combination of techniques to gain initial access and move laterally within a victim’s network. This includes exploiting known vulnerabilities in software applications and systems, using stolen credentials obtained through phishing or other means, and potentially employing various social engineering tactics. Post-compromise, the group demonstrates advanced capabilities in navigating complex network environments, demonstrating a high level of technical expertise. Their persistence within compromised networks is often notable, allowing for extensive data exfiltration before the ransomware deployment.
Targets of Black Basta Attacks
Black Basta exhibits a preference for targeting organizations across various sectors, focusing primarily on those with access to sensitive data and a high likelihood of paying a ransom. While specific industry targeting may fluctuate, their victims have included healthcare providers, manufacturing companies, and technology firms – organizations holding valuable intellectual property, patient data, or financial information. The group’s targeting demonstrates a calculated approach, prioritizing organizations that are likely to experience significant disruption and financial loss from a data breach and encryption. This calculated approach maximizes their potential return on investment.
Ransom Negotiation Tactics of Black Basta
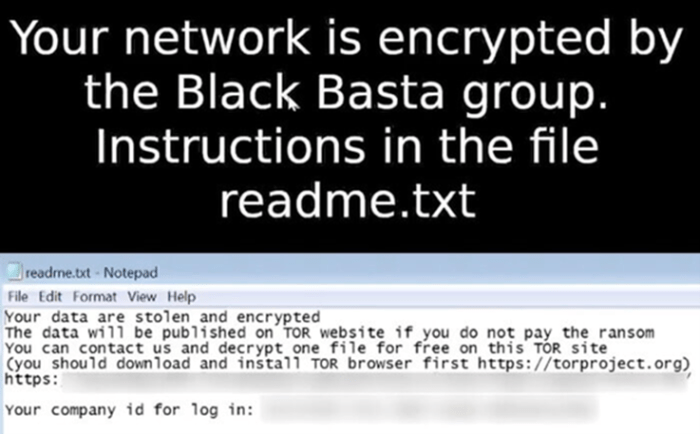
Black Basta’s ransom negotiation tactics are typically aggressive and focused on maximizing their financial gain. They often communicate directly with victims through encrypted channels, demanding significant ransoms in cryptocurrency. They usually provide a timeframe for payment, threatening to leak stolen data publicly if the ransom is not met. The leaked data is often showcased on their data leak site, serving as a stark warning to potential victims and a demonstration of their capabilities. Black Basta has also been known to engage in protracted negotiations, leveraging the pressure of data exposure to extract the highest possible ransom.
Data Exfiltration Techniques Employed by Black Basta
Black Basta utilizes various techniques for data exfiltration, often employing sophisticated methods to avoid detection. These techniques may include using encrypted channels, splitting large files into smaller parts, and employing multiple exfiltration pathways to enhance resilience. They often target databases, email servers, and file shares, focusing on extracting data with high value and sensitivity. The exfiltrated data is then stored and used as leverage during ransom negotiations. Examples of data exfiltrated include patient medical records, financial records, and intellectual property blueprints, all of which hold significant value to both the victim and the threat actors.
Teams Chat Abuse
Source: snewsonline.com
Black Basta’s sophisticated attacks extend beyond traditional ransomware deployment. Their exploitation of Microsoft Teams, a widely used collaboration tool, demonstrates a keen understanding of modern workplace infrastructure and a willingness to leverage readily available communication channels for malicious purposes. This approach allows for a more insidious and less easily detected infiltration, blurring the lines between legitimate activity and malicious intent.
Black Basta’s methods for compromising Microsoft Teams accounts are multifaceted, often relying on initial access gained through phishing campaigns, exploiting vulnerabilities in other applications, or leveraging compromised credentials obtained through other means. Once inside, they skillfully use the platform to move laterally within the network and maintain persistent access, all while evading traditional security measures.
Compromised Account Exploitation for Lateral Movement
After gaining access to a single Teams account, Black Basta can leverage its features to infiltrate deeper into the target network. They might use the account to join existing team channels, gaining access to shared files and conversations. From there, they can identify other valuable accounts or sensitive data. For example, they might exploit shared drives to plant malicious files or gain access to sensitive financial documents. The ability to seamlessly blend into legitimate team activity makes detection incredibly challenging. This method allows for a stealthy and efficient spread of malware or the exfiltration of data.
Teams Chat as a Command and Control (C2) Channel
Black Basta can utilize the seemingly innocuous Teams chat function for covert communication and control. Encrypted private messages allow for the transmission of commands, the receipt of stolen data, and the coordination of further attacks without raising immediate suspicion. This is particularly effective as security monitoring often focuses on more traditional communication channels, leaving Teams chat relatively unchecked. The use of seemingly innocuous language within these messages further obfuscates malicious activity. Imagine a seemingly casual message containing an encoded command to deploy a specific payload.
Malicious File and Link Distribution via Teams Chat
The sharing of files within Teams is a common practice, making it an ideal vector for delivering malicious payloads. Black Basta might share seemingly legitimate documents containing embedded malware, or links to malicious websites disguised as harmless resources. These could include invoices, project updates, or other documents relevant to the target’s business. The attacker’s goal is to blend in with the normal workflow, making the malicious file or link appear completely natural. An example might be a seemingly innocuous PDF containing a malicious macro, or a link to a website hosting a drive-by download attack. The sophistication lies in the attacker’s ability to create a convincing and believable pretext for the malicious content.
Impact of Teams Chat Abuse on Organizations
Black Basta’s exploitation of Microsoft Teams chat represents a significant shift in ransomware tactics, moving beyond simple data encryption to infiltrate the very fabric of organizational communication. This breach of trust, facilitated by seemingly innocuous platforms, can have devastating consequences far exceeding the immediate financial losses associated with data theft. The insidious nature of this attack vector lies in its ability to undermine operational efficiency, damage reputation, and compromise sensitive information in ways that are difficult to detect and remediate.
The damage inflicted by Black Basta’s abuse of Teams chat extends beyond the typical ransomware scenario. While data encryption remains a core component of their attacks, the compromise of internal communications channels introduces a new layer of complexity and risk. The ability to monitor sensitive conversations, strategic planning sessions, or even informal discussions can provide attackers with invaluable intelligence, enabling them to tailor future attacks or exploit vulnerabilities more effectively. This insider knowledge can be used to target specific individuals, departments, or systems, maximizing the impact of the ransomware deployment.
Financial and Reputational Risks
The financial repercussions of a Black Basta attack leveraging Teams chat are substantial. Direct costs include the ransom payment itself (if paid), the costs associated with data recovery and system restoration, legal fees, and potential regulatory fines for data breaches. Beyond these direct costs, there are indirect costs to consider, such as lost productivity, damaged customer relationships, and decreased investor confidence. Reputational damage can be equally devastating, leading to a loss of market share, difficulty attracting and retaining talent, and long-term damage to brand image. For example, a healthcare provider compromised through Teams chat might face significant legal challenges and loss of patient trust, impacting their ability to operate effectively and maintain profitability.
Operational Continuity and Data Security
The impact on operational continuity can be crippling. Disruption to internal communications caused by the compromise of Teams chat can severely hinder daily operations, impacting everything from project management and customer service to internal collaboration and emergency response. Critical business processes may be delayed or halted entirely, leading to significant financial losses and potential legal repercussions. Furthermore, the exfiltration of sensitive data through compromised Teams channels poses a significant risk to data security. This could include intellectual property, confidential client information, or sensitive employee data, all of which can be exploited for further malicious purposes or sold on the dark web. The long-term consequences of a data breach can be far-reaching, impacting the organization’s ability to operate securely and maintain customer trust.
Consequences of Different Levels of Teams Compromise
| Severity | Impact Area | Example | Mitigation Strategy |
|---|---|---|---|
| Low | Minor data breach | Unauthorized access to a single chat channel containing non-sensitive information. | Strengthen password policies, implement multi-factor authentication (MFA). |
| Medium | Significant data breach | Exfiltration of sensitive project plans and client data from multiple chat channels. | Regular security audits, employee security awareness training, data loss prevention (DLP) tools. |
| High | Critical system compromise | Ransomware deployment facilitated by compromised Teams credentials, leading to widespread system disruption and data encryption. | Robust endpoint detection and response (EDR), incident response plan, regular software updates and patching. |
| Critical | Total organizational disruption | Complete system shutdown, significant data loss, and severe reputational damage resulting from widespread data breach and operational halt. | Comprehensive cybersecurity strategy including threat intelligence, proactive security measures, and business continuity planning. |
Detection and Prevention Strategies
Source: indusface.com
Black Basta’s sophisticated attacks necessitate a multi-layered approach to detection and prevention. Successfully thwarting their efforts requires a blend of robust security protocols, advanced technologies, and well-trained personnel. Ignoring any one of these elements significantly increases your vulnerability.
Security protocols must go beyond basic antivirus and firewalls. They need to actively monitor and analyze Teams chat activity for anomalies that might indicate malicious activity. This proactive approach is crucial in identifying threats before they can cause significant damage.
Security Protocols for Detecting Suspicious Activity
Effective security protocols should incorporate real-time monitoring of Teams chat logs for unusual patterns. This includes analyzing message content for suspicious links, attachments, or language indicative of phishing attempts or social engineering. Additionally, monitoring for unusual user behavior, such as sudden increases in file sharing or communication with unknown contacts, can be highly effective. Automated alerts should be triggered when predefined thresholds are breached, enabling rapid response to potential threats. Consider implementing data loss prevention (DLP) tools to monitor sensitive data shared within Teams and prevent unauthorized exfiltration. Regular security audits of Teams configurations and user permissions are essential to identify and address potential vulnerabilities.
Security Tools and Technologies, Black basta abusing teams chat for
Several security tools can significantly enhance your ability to detect and mitigate Black Basta’s tactics. Security information and event management (SIEM) systems provide centralized logging and analysis of security events across various platforms, including Teams. These systems can identify patterns indicative of malicious activity, such as unusual login attempts or data exfiltration. User and entity behavior analytics (UEBA) tools can detect anomalous behavior by analyzing user activity within Teams, flagging suspicious interactions that might indicate a compromise. Advanced threat protection solutions, integrated with Teams, can identify and block malicious links, attachments, and messages before they reach users. Finally, endpoint detection and response (EDR) solutions can monitor endpoint activity for malicious behavior, providing valuable context for investigating potential breaches.
Employee Training on Phishing and Social Engineering
Comprehensive employee training is paramount in mitigating the risk of Black Basta attacks. Regular security awareness training should cover various phishing techniques, including spear phishing and whaling, educating employees on how to identify and report suspicious emails, messages, and attachments. Simulations of phishing attacks can effectively test employee awareness and identify training gaps. Training should emphasize the importance of verifying the authenticity of requests before sharing sensitive information or clicking on links. Employees should be instructed to report any suspicious activity immediately to the security team. Furthermore, training should cover the basics of social engineering, highlighting tactics used by attackers to manipulate individuals into divulging sensitive information.
Indicators of Compromise (IOCs)
Identifying indicators of compromise (IOCs) is crucial for timely detection and response. Several IOCs might suggest Black Basta activity within Teams:
- Unusual communication patterns, such as sudden increases in messages with external users or unusual communication times.
- Suspicious attachments or links within Teams messages, potentially leading to malware downloads or phishing websites.
- Unexpected file sharing activity, particularly of sensitive data or large files.
- Compromised user accounts exhibiting unusual login attempts or activity.
- Detection of known Black Basta malware or tools within Teams environment through endpoint detection.
- Unusual activity related to the creation or modification of Teams channels or groups.
Monitoring for these IOCs, combined with robust security tools and employee training, provides a strong defense against Black Basta attacks.
Case Studies and Analysis of Past Incidents
Black Basta’s reliance on Microsoft Teams for exfiltration and communication during ransomware attacks represents a concerning evolution in cybercrime tactics. Analyzing specific incidents reveals patterns in their methods and highlights vulnerabilities exploited. Understanding these past attacks is crucial for developing effective preventative measures.
Unfortunately, precise details about specific Black Basta attacks leveraging Microsoft Teams are often kept confidential by victims due to reputational concerns and ongoing investigations. Publicly available information is limited, and much of the detail remains obscured. However, by examining general attack patterns and reported methods, we can infer potential scenarios and extract valuable lessons.
Black Basta’s Teams Chat Abuse Methods
While specific case details are scarce, reports indicate Black Basta uses Teams in several ways. These methods often involve a combination of social engineering and technical exploitation to gain access and maintain persistence within a victim’s network.
- Compromised Accounts: Black Basta may exploit already compromised accounts, using them to access Teams channels and communicate with victims or exfiltrate data directly.
- Credential Stuffing/Brute-forcing: Attempts to gain access through stolen credentials or brute-force attacks targeting employee accounts, granting access to Teams and internal communication channels.
- Lateral Movement: Once inside the network, the threat actor may leverage Teams to move laterally, communicating instructions or exfiltrating data from compromised accounts within different departments or teams.
- Data Exfiltration: Data may be directly shared via Teams chat (smaller files), or Teams may be used to coordinate the use of other exfiltration methods such as file sharing services or compromised cloud storage accounts.
Potential Preventative Measures and Mitigation Strategies
Several security measures could significantly reduce the risk of Black Basta exploiting Microsoft Teams.
- Multi-Factor Authentication (MFA): Mandatory MFA for all accounts significantly reduces the effectiveness of credential stuffing and brute-force attacks, a primary method for gaining initial access.
- Access Control and Least Privilege: Implementing the principle of least privilege, limiting user access to only the necessary Teams channels and features, restricts the potential damage from a compromised account.
- Regular Security Awareness Training: Educating employees about phishing attempts, social engineering tactics, and the importance of strong passwords reduces the likelihood of successful initial compromises.
- Network Segmentation: Isolating sensitive data and systems from the rest of the network limits the impact of a compromise, preventing lateral movement within the organization.
- Intrusion Detection and Prevention Systems (IDPS): Deploying robust IDPS solutions can detect and prevent malicious activity within the network, including attempts to access or abuse Teams channels.
- Data Loss Prevention (DLP): Implementing DLP tools can monitor and prevent sensitive data from being exfiltrated via Teams or other channels.
- Regular Security Audits and Penetration Testing: Regular assessments identify vulnerabilities and weaknesses within the organization’s security posture, allowing for proactive mitigation.
Lessons Learned and Improved Security Posture
The incidents, while lacking in specific public details, highlight the critical need for a layered security approach. Relying on a single security measure is insufficient; a robust defense requires a combination of technical controls and employee awareness.
Organizations must prioritize proactive security measures, focusing on preventing initial access and limiting the impact of a successful compromise. Regular training, robust authentication, and strong access controls are paramount in mitigating the risk of Black Basta and similar ransomware groups leveraging collaboration tools for malicious purposes.
Visual Representation of Attack Flow: Black Basta Abusing Teams Chat For

Source: wizcase.com
Understanding the mechanics of a Black Basta attack leveraging Microsoft Teams requires visualizing the distinct phases. This hypothetical scenario illustrates how an attacker might exploit the platform for data exfiltration and disruption. We will trace the steps from initial compromise to the successful theft of sensitive information.
Imagine a scenario where a compromised employee receives a seemingly innocuous phishing email containing a malicious link. This link downloads a seemingly harmless document, but actually contains malware that establishes a foothold on the victim’s machine. The malware then spreads laterally across the network, eventually gaining access to sensitive data.
Initial Compromise and Lateral Movement
The attack begins with a spear-phishing email targeting a specific employee within the organization. The email contains a malicious attachment or link disguised as a legitimate document. Once the employee interacts with the malicious content, malware is downloaded and executed on their machine. This malware, possibly a custom-built tool designed for stealth, then uses various techniques to move laterally across the network, gaining access to other systems and sensitive data repositories. This phase involves exploiting vulnerabilities in network security, weak passwords, or other security gaps to reach the targeted data.
Data Exfiltration via Teams Chat
Once the malware has access to sensitive data, the attacker begins the exfiltration process. Instead of using traditional methods like FTP or email, the attacker leverages the seemingly innocuous Microsoft Teams chat function. The attacker might use a compromised account or create a new account that blends in with legitimate users. The attacker could then use the chat function to send small chunks of stolen data to a compromised account outside the organization. These chunks could be encoded or encrypted to avoid detection by security systems. The use of Teams chat provides a seemingly legitimate communication channel, making it harder for security systems to identify the malicious activity. The volume of data exfiltrated in each message is carefully controlled to avoid triggering alerts.
Data Exfiltration Process Details
Let’s envision a specific example. The attacker gains access to a database containing customer records. Instead of downloading the entire database at once, a process that would likely trigger alerts, the attacker uses a script to extract the data in small batches. Each batch might contain a few hundred records, encoded using a robust encryption algorithm. These encoded batches are then sent as individual chat messages to a pre-arranged external account. The attacker might use a pre-defined naming convention for the files or employ steganography to further conceal the data transfer within the chat messages. The entire process is designed to be slow and stealthy, making it harder to detect. After all data is exfiltrated, the attacker might delete the malware and cover their tracks, leaving no immediate trace of their activity.
Post-Exfiltration Activities
Following successful data exfiltration, the attacker typically engages in further actions. This might include deleting logs, disabling security systems, or modifying system configurations to hinder investigations. The attacker might then move to the next phase: data encryption and extortion demands. This is a crucial step where the attacker leverages the stolen data to pressure the victim organization into paying a ransom to prevent the release of sensitive information. The attacker’s ultimate goal is financial gain, achieved through the exploitation of vulnerabilities and the manipulation of legitimate communication channels like Microsoft Teams.
Concluding Remarks
Black Basta’s exploitation of Microsoft Teams highlights a critical vulnerability in our increasingly interconnected digital world. While the sophistication of their tactics is undeniably alarming, understanding their methods is the first step towards effective defense. By strengthening our security protocols, enhancing employee training, and leveraging advanced security tools, we can significantly reduce our vulnerability to these attacks. Remember, vigilance and proactive security measures are your strongest weapons in this ongoing battle against cybercriminals. Don’t wait for the next headline; start safeguarding your organization today.


