AWS Patches Multiple Vulnerabilities: Think your cloud is a fortress? Think again. Recent AWS patch releases address a slew of vulnerabilities, ranging from annoying inconveniences to full-blown security nightmares. We’re diving deep into the nitty-gritty of these patches, exploring the severity of the threats, the patching process itself, and how to keep your AWS environment safe from the digital bad guys. This isn’t your grandpappy’s server room; this is the wild west of the cloud, and we’re here to help you survive.
From SQL injection vulnerabilities to cross-site scripting attacks, we’ll break down the types of threats addressed, the tools AWS provides to help you patch effectively, and the potential impact on various AWS services like EC2, S3, and RDS. We’ll even give you a peek into real-world incidents to show you why staying on top of patches isn’t just a good idea—it’s essential.
Severity and Impact of AWS Patches
Source: sysdig.com
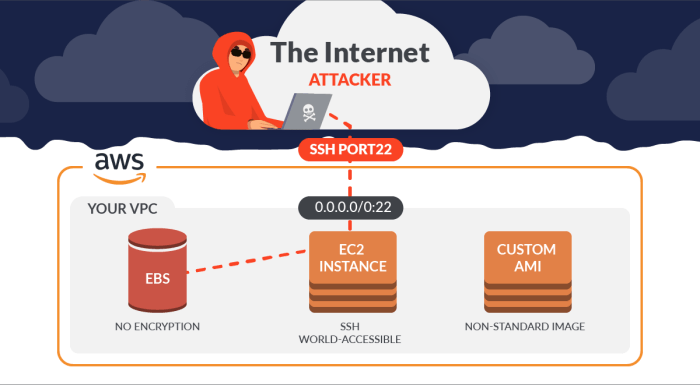
Ignoring critical AWS security patches is like leaving your front door unlocked in a high-crime neighborhood – it’s an open invitation for trouble. These patches address vulnerabilities that, if exploited, can lead to significant data breaches, service disruptions, and hefty financial losses. Understanding the severity and impact of these patches is crucial for maintaining a secure cloud environment.
The potential consequences of unpatched AWS vulnerabilities are far-reaching and can significantly impact your business. From unauthorized access to sensitive data to complete system compromise and crippling downtime, the risks are substantial. The cost of remediation following a successful attack often far outweighs the cost of proactively applying security patches. Think reputational damage, legal fees, and the potential loss of customer trust – all adding up to a potentially devastating blow.
Types of Vulnerabilities Addressed in AWS Patches
Recent AWS patch releases have addressed a wide range of vulnerabilities, including critical flaws in various services. These vulnerabilities can range from common weaknesses like cross-site scripting (XSS) and SQL injection to more sophisticated attacks targeting authentication mechanisms and server-side code. The patches often address multiple vulnerabilities simultaneously, improving the overall security posture of your AWS infrastructure. For example, a single patch might address both a denial-of-service vulnerability and a privilege escalation vulnerability within a specific service.
Real-World Security Incidents Caused by Unpatched AWS Systems
Numerous high-profile data breaches have been directly linked to unpatched AWS systems. While specific details are often kept confidential due to ongoing investigations, news reports frequently highlight incidents involving compromised databases, exposed credentials, and significant data exfiltration. These breaches highlight the real-world consequences of neglecting security updates and the importance of a robust patch management strategy. One example (though details are often obfuscated) might involve a company failing to patch a known vulnerability in its Amazon S3 storage, leading to the exposure of sensitive customer data. The resulting reputational damage and legal repercussions can be catastrophic.
Severity Levels of AWS Vulnerabilities, Aws patches multiple vulnerabilities
AWS typically uses the Common Vulnerability Scoring System (CVSS) to rate the severity of vulnerabilities. The CVSS score ranges from 0 to 10, with 10 representing the most critical vulnerabilities. High-severity vulnerabilities (typically CVSS scores of 7 or higher) often pose an immediate threat and require immediate patching. Medium-severity vulnerabilities (scores between 4 and 6) should also be addressed promptly, while low-severity vulnerabilities (scores below 4) might have a lower priority but should still be patched as part of a comprehensive security strategy. The severity level is determined by factors like the ease of exploitation, the potential impact, and the availability of exploits.
Examples of Patched Vulnerabilities
| Vulnerability Type | CVSS Score | Affected Services | Description |
|---|---|---|---|
| Cross-Site Scripting (XSS) | 7.5 | Amazon EC2, Amazon S3 | Allows attackers to inject malicious scripts into web pages viewed by other users. |
| SQL Injection | 9.0 | Amazon RDS | Allows attackers to execute arbitrary SQL commands against a database. |
| Denial of Service (DoS) | 6.5 | Amazon Elastic Load Balancing | Causes a service disruption by overwhelming a system with traffic. |
| Improper Access Control | 8.0 | Amazon IAM | Allows unauthorized access to resources due to misconfiguration. |
Patching Procedures and Best Practices: Aws Patches Multiple Vulnerabilities

Source: techgenix.com
Keeping your AWS infrastructure secure requires a robust patching strategy. Ignoring updates leaves your systems vulnerable to exploits, potentially leading to data breaches, service disruptions, and hefty fines. This section Artikels effective patching procedures and best practices to minimize risk and maximize uptime. We’ll explore different patching methods, detail a typical patching process, and discuss the pros and cons of automation.
Applying AWS security patches involves several methods, each with its own strengths and weaknesses. The choice depends on factors such as the size of your environment, your team’s expertise, and your risk tolerance. Understanding these options is crucial for developing a tailored patching strategy.
AWS Systems Manager Patch Manager
AWS Systems Manager Patch Manager provides a centralized solution for patching your Amazon EC2 instances, on-premises servers, and virtual machines. It supports both Windows and Linux operating systems and offers automated patching capabilities, simplifying the process and reducing the risk of human error. Patch Manager integrates seamlessly with other AWS services, such as AWS Identity and Access Management (IAM) for granular control over access and permissions. It allows you to create patch baselines, schedule patching windows, and track the progress of your patching efforts. Detailed reports provide insights into the patching status of your instances, helping you identify and address any outstanding issues.
AWS OpsWorks
AWS OpsWorks is a configuration management service that allows you to automate the deployment and management of your applications and infrastructure. It provides features for automating patching, allowing you to schedule regular updates and apply patches to your instances without manual intervention. OpsWorks integrates with various configuration management tools, such as Chef and Puppet, giving you flexibility in how you manage your infrastructure.
Manual Patching
Manual patching involves directly connecting to each instance and applying patches using the operating system’s built-in tools. This method is time-consuming and error-prone, particularly in large environments. However, it can be useful for situations requiring precise control or when dealing with complex patching scenarios not easily handled by automated tools. It is generally not recommended for production environments due to the increased risk of human error and downtime.
Steps in a Typical AWS Patching Process
A well-defined process is crucial for efficient and secure patching. A typical process involves these steps:
- Assessment: Identify all systems requiring patching and determine the applicable patches. This often involves scanning for vulnerabilities using tools like Amazon Inspector or third-party vulnerability scanners.
- Testing: Test patches in a non-production environment (e.g., a staging environment) to ensure they don’t introduce new problems. This is a critical step to minimize disruptions in your production systems.
- Scheduling: Schedule patching windows that minimize disruption to your applications and users. Consider off-peak hours or periods of low activity.
- Deployment: Deploy patches using your chosen method (e.g., AWS Systems Manager Patch Manager, OpsWorks, or manual patching). This step may involve rebooting instances, requiring careful planning and coordination.
- Verification: Verify that patches have been successfully applied and that systems are functioning correctly. This often involves post-patch testing and monitoring.
- Documentation: Document the entire patching process, including the patches applied, the dates, and any issues encountered. This is essential for auditing and troubleshooting.
Best Practices for Scheduling and Deploying Patches in a Production Environment
Successful patching in a production environment requires careful planning and execution. Prioritization, testing, and rollback strategies are key.
- Prioritize critical patches: Focus on addressing high-severity vulnerabilities first.
- Use a phased rollout: Deploy patches to a small subset of instances first to identify and address any unforeseen issues before deploying to the entire environment.
- Implement a rollback plan: Have a plan in place to quickly revert to the previous state if a patch causes problems.
- Monitor system health: Closely monitor system performance and logs after patching to detect any anomalies.
- Automate the process: Automate as much of the patching process as possible to reduce manual effort and human error.
Automated Versus Manual Patching: A Comparison
| Feature | Automated Patching | Manual Patching |
|---|---|---|
| Efficiency | High | Low |
| Scalability | High | Low |
| Error Rate | Low | High |
| Cost | Potentially higher initial investment, lower long-term cost | Lower initial investment, higher long-term cost |
| Complexity | Moderate to High (depending on the chosen tool) | Low |
Patching AWS Instances Using AWS Systems Manager
Here’s a step-by-step guide for patching AWS instances using AWS Systems Manager:
- Enable Systems Manager on your instances: Ensure the Systems Manager agent is installed and running on all target instances.
- Create a patch baseline: Define a patch baseline specifying the operating systems and patches to be applied.
- Create a maintenance window: Schedule a maintenance window to minimize disruption.
- Associate the patch baseline with the maintenance window: Link the patch baseline to the maintenance window to schedule the patching process.
- Deploy the patch baseline: Initiate the patching process. Systems Manager will automatically apply the patches during the scheduled maintenance window.
- Monitor the patching process: Track the progress and address any issues encountered.
- Verify patch application: Confirm that patches have been successfully applied and systems are functioning correctly.
Vulnerability Types Addressed
AWS regularly patches a wide range of vulnerabilities affecting its various services. Understanding these vulnerabilities is crucial for maintaining a secure cloud environment. This section details the common types of vulnerabilities addressed by AWS patches, the affected technologies, and provides illustrative examples.
AWS’s patching efforts cover a broad spectrum of security weaknesses, reflecting the diverse nature of its cloud services. These vulnerabilities are not limited to a single technology stack; rather, they span various layers, from the underlying infrastructure to the application services themselves. Understanding the specific vulnerabilities patched is key to proactively securing your AWS deployments.
Common Vulnerability Types
AWS patches address many vulnerability types. These frequently include SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), insecure direct object references (IDORs), denial-of-service (DoS) vulnerabilities, and various authentication and authorization flaws. These are often categorized by the Common Vulnerabilities and Exposures (CVE) system. The specific vulnerabilities patched vary depending on the service and the release cycle.
Technologies and Services Affected
The vulnerabilities patched by AWS impact a wide range of services and technologies. For example, vulnerabilities related to database interaction (SQL injection) might affect services like Amazon RDS or DynamoDB. Web application vulnerabilities (XSS, CSRF) could affect services like Elastic Beanstalk or EC2 instances running web applications. Network-based vulnerabilities (DoS) might impact EC2 instances or networking services like Elastic Load Balancing. Furthermore, vulnerabilities in the underlying operating systems of EC2 instances are also frequently addressed.
Example: Cross-Site Scripting (XSS) Vulnerability
Cross-site scripting is a common vulnerability that allows attackers to inject malicious scripts into websites viewed by other users. Here’s an example illustrating a vulnerable and a patched code snippet in a hypothetical AWS Lambda function processing user input:
Vulnerable Code (Python):
import json def lambda_handler(event, context): name = event['queryStringParameters']['name'] response = 'statusCode': 200, 'body': json.dumps('Hello, ' + name + '!') return response
Patched Code (Python):
import json import html def lambda_handler(event, context): name = event['queryStringParameters'].get('name', '') safe_name = html.escape(name) response = 'statusCode': 200, 'body': json.dumps('Hello, ' + safe_name + '!') return response
The patched code uses the `html.escape()` function to sanitize user input, preventing the injection of malicious scripts.
Frequency of Vulnerability Types Patched (Illustrative Data)
Precise data on the frequency of specific vulnerability types patched by AWS is not publicly available in a comprehensive, aggregated format. However, based on publicly disclosed CVEs and security advisories, we can illustrate a hypothetical distribution:
Imagine a bar chart representing the relative frequency of vulnerability types patched in the last year. The chart would show that:
Authentication/Authorization issues would likely represent the largest portion (e.g., 35%). Next, might be Web Application vulnerabilities (XSS, CSRF, IDORs) at around 25%. Then, Infrastructure vulnerabilities (network configuration, OS flaws) would likely make up 20%. Database vulnerabilities (SQL injection) would account for approximately 15%, and the remaining 5% would cover other miscellaneous vulnerabilities.
This is a simplified representation; the actual distribution varies depending on the specific services and their usage patterns.
AWS Patch Management Tools and Services
Automating security patching is crucial in today’s cloud-native world. Manual processes are slow, error-prone, and simply can’t keep up with the constant stream of vulnerabilities. AWS offers a suite of robust tools to streamline this process, significantly improving your security posture and reducing operational overhead. Let’s dive into the key players and how they work together.
AWS provides several services designed to simplify and automate the patching of your EC2 instances and other resources. These services offer varying levels of functionality and integration, allowing you to choose the best fit for your specific needs and infrastructure complexity. Effective patch management requires a well-defined strategy, and understanding the strengths and weaknesses of each tool is paramount to successful implementation.
AWS Systems Manager (SSM) Patch Manager
SSM Patch Manager is a centralized service for managing patches across your AWS environment. It integrates with various operating systems and applications, allowing you to automate patch deployments, track compliance, and gain visibility into your patching status. It supports both Windows and Linux instances, offering a unified patching solution for diverse workloads.
SSM Patch Manager utilizes a flexible approach, allowing you to define patch baselines—sets of patches to be applied—and schedule their deployment according to your operational windows. You can also create automation documents to customize the patching process further, integrating with other AWS services for comprehensive management. The service provides detailed reporting and auditing capabilities, offering insights into patch compliance and identifying potential security gaps.
Workflow using SSM Patch Manager (Illustrative Flowchart):
1. Define Patch Baselines: Specify the operating systems and the patches to be included in each baseline. This might include critical, security, or recommended updates.
2. Create Patch Groups: Group EC2 instances based on criteria like operating system, environment (dev, test, prod), or application. This allows for targeted patching.
3. Schedule Patch Deployments: Specify the schedule for applying patches to each group, considering operational downtime windows to minimize disruption.
4. Approve and Deploy: Review the patch deployment plan and approve the execution. SSM Patch Manager will then automatically apply the patches to the selected instances.
5. Monitor and Report: Track the progress of the patch deployments and review compliance reports to ensure all instances are up-to-date.
Advantages and Disadvantages of SSM Patch Manager:
- Advantages: Centralized management, automation capabilities, detailed reporting, supports multiple operating systems, integrates well with other AWS services.
- Disadvantages: Requires some initial configuration and setup, may require expertise in AWS Systems Manager, potential for unexpected reboots depending on patch content.
AWS Inspector
AWS Inspector is a vulnerability assessment service that automatically discovers and assesses security vulnerabilities in your AWS resources. While not directly a patch management tool, it plays a crucial role in identifying the *need* for patching. Inspector scans your instances and applications, providing detailed reports of discovered vulnerabilities, allowing you to prioritize patching efforts based on severity and risk. This integration with SSM Patch Manager allows for a more efficient and targeted patching strategy.
Advantages and Disadvantages of AWS Inspector:
- Advantages: Automated vulnerability detection, detailed reports, integrates with other AWS services (like SSM), helps prioritize patching efforts.
- Disadvantages: Requires configuration and setup, may not detect all vulnerabilities, results require manual review and action.
Impact on Different AWS Services

Source: scnsoft.com
Patching AWS services is crucial for maintaining security and stability, but it’s not a one-size-fits-all process. The impact of patching varies significantly depending on the service, the patching method employed, and the scale of your deployment. Understanding these differences is key to minimizing disruption and ensuring a smooth patching experience. Let’s dive into the specifics for some major AWS services.
EC2 Instance Patching
Patching Amazon Elastic Compute Cloud (EC2) instances involves updating the underlying operating system and any installed applications. The method depends on your chosen AMI (Amazon Machine Image) and your preferred patching strategy. You can use tools like AWS Systems Manager (SSM) for automated patching, or manually patch instances using SSH or other remote access methods. Potential downtime depends on the patching method and the specific updates. For example, a reboot might be required for kernel updates, leading to temporary service interruption. To mitigate downtime, consider using rolling updates, patching instances in stages, and scheduling patches during off-peak hours. Implementing robust monitoring during the patching process allows for swift identification and resolution of any issues.
S3 Service Updates
Unlike EC2 instances, Amazon Simple Storage Service (S3) doesn’t require patching in the traditional sense. AWS handles the underlying infrastructure updates automatically. However, new features and security enhancements are regularly rolled out. These updates typically have minimal to no impact on your S3 buckets and data. There’s generally no downtime associated with these updates. Monitoring your S3 bucket activity and logging are good practices to ensure everything remains functional after any AWS-initiated updates.
RDS Database Patching
Patching Amazon Relational Database Service (RDS) instances involves applying updates to the database software itself. AWS provides automated patching options, allowing you to choose between minor and major versions. Major version updates often require a brief outage, while minor updates can often be applied with minimal or no downtime. The downtime depends on the chosen update type and the database engine (e.g., MySQL, PostgreSQL, SQL Server). To minimize downtime, consider using RDS features like read replicas to maintain service availability during patching. Point-in-time recovery can also be used to quickly restore service if issues arise.
Patching Procedures and Potential Downtime Comparison
| AWS Service | Patching Procedure | Potential Downtime | Downtime Mitigation |
|---|---|---|---|
| EC2 | SSM Automation, Manual SSH, etc. | Variable, depending on update type and method; reboots may be required. | Rolling updates, off-peak patching, robust monitoring. |
| S3 | Automatic AWS updates | Generally none | Monitoring and logging |
| RDS | Automated patching via AWS console; minor/major version updates. | Minor updates: minimal to none; Major updates: brief outage possible. | Read replicas, point-in-time recovery, scheduled maintenance windows. |
Final Thoughts
Staying secure in the cloud isn’t a one-time fix; it’s an ongoing battle. Understanding the severity of unpatched AWS vulnerabilities, mastering efficient patching procedures, and leveraging AWS’s robust patch management tools are key to maintaining a secure environment. By proactively addressing these vulnerabilities, you not only protect your data but also avoid the headaches (and potential financial losses) of a security breach. So, ditch the procrastination and get patching!