Art4sqli SQLi detection method: Ever wondered how those sneaky SQL injection attacks get thwarted? Dive into the world of Art4sqli, a powerful tool that’s changing the game in database security. We’ll unpack its inner workings, from its core functionality to its advanced techniques, exploring how it identifies and neutralizes malicious SQL code before it can wreak havoc on your data. Get ready to level up your web app security game.
This deep dive will explore Art4sqli’s architecture, its various detection methods, and its strengths and weaknesses compared to other SQL injection detection tools. We’ll cover practical applications, integration strategies, and even peek into the future of AI-powered enhancements. Think of it as your ultimate guide to mastering Art4sqli and safeguarding your digital assets.
Understanding Art4sqli
Source: amazonaws.com
Art4sqli is a powerful, open-source tool designed to detect SQL injection vulnerabilities in web applications. It goes beyond simple -based detection, employing advanced techniques to identify potentially exploitable flaws even in obfuscated or complex code. Think of it as a highly trained cybersecurity detective, meticulously examining web application code for subtle signs of SQL injection weaknesses.
Art4sqli’s Core Functionality
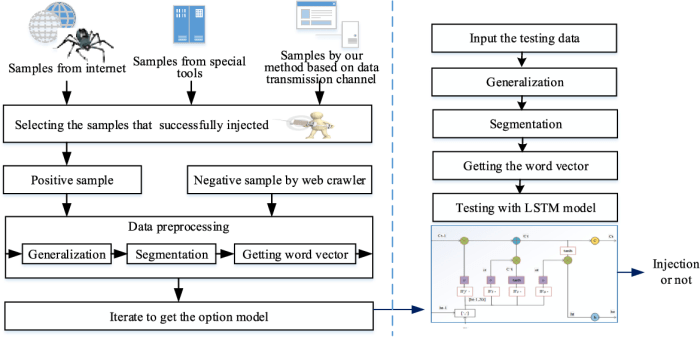
Art4sqli’s core functionality revolves around static analysis of web application source code. Unlike dynamic analysis tools that interact with a running application, Art4sqli examines the code itself, searching for patterns and constructs indicative of vulnerable SQL queries. This allows it to identify vulnerabilities even before the application is deployed, offering a proactive approach to security. It achieves this by parsing the code, identifying database interaction points, and analyzing how user inputs are incorporated into SQL queries. If it finds a potential injection point where untrusted user input directly affects the database query structure, it flags it as a potential vulnerability.
Art4sqli Components and Modules
Art4sqli is modular, allowing for customization and extension. While the exact composition might vary depending on the version, core components typically include a parser to understand different programming languages (like PHP, Java, Python), a query analyzer to dissect SQL statements, and a vulnerability detector that identifies potentially dangerous patterns. These components work together, creating a robust pipeline for identifying SQL injection flaws. For instance, the parser might identify a vulnerable `SELECT` statement, the query analyzer would then break down the statement, and the vulnerability detector would flag it based on how user inputs are integrated.
Art4sqli Architecture and Data Processing
Art4sqli operates on a multi-stage process. First, it parses the input source code, extracting all database interaction points. Next, it analyzes the SQL queries, identifying variables and parameters. Finally, it assesses how user-supplied data is incorporated into these queries, looking for patterns that indicate SQL injection vulnerabilities. The results are then presented to the user, highlighting potential vulnerabilities with details such as the location and type of vulnerability. This systematic approach ensures thorough analysis and minimizes false positives.
Comparison with Other SQL Injection Detection Tools
Several tools offer SQL injection detection, each with its own strengths and weaknesses. Below is a comparison of Art4sqli with two other prominent tools:
| Tool Name | Key Features | Strengths | Weaknesses |
|---|---|---|---|
| Art4sqli | Static analysis, multiple language support, customizable, open-source | Proactive detection, thorough analysis, customizable, free and open-source | Requires source code access, might produce false positives in complex applications |
| SQLmap | Automated detection and exploitation, multiple database systems support | Comprehensive testing, identifies both blind and error-based SQLi | Requires a running application, potentially intrusive, can be misused |
| RIPS | Static analysis, supports various frameworks, detailed vulnerability reports | Good accuracy, provides detailed reports, supports multiple frameworks | Can be resource-intensive, commercial license required |
Art4sqli’s Detection Methods
Art4sqli, a powerful SQL injection detection tool, leverages a multi-pronged approach to identify vulnerabilities. It goes beyond simple matching, employing sophisticated techniques to analyze user input and database interactions, effectively uncovering even the most cleverly disguised attacks. This detailed examination ensures a comprehensive security assessment.
Art4sqli’s core functionality centers around analyzing the structure and behavior of user-supplied data within the context of SQL queries. It doesn’t just passively look for suspicious s; instead, it actively simulates the execution of SQL queries with the provided input, meticulously observing the resulting database interactions for anomalies that indicate malicious intent. This proactive approach allows for the detection of a wide range of SQL injection techniques.
SQL Injection Attack Detection Techniques
Art4sqli utilizes several advanced techniques to pinpoint SQL injection attempts. These include analyzing query syntax for irregularities, monitoring database response times for unusual delays (indicative of a slow, potentially malicious query), and comparing the expected database output with the actual results. The tool also examines the structure of the SQL queries themselves, looking for patterns that are often associated with SQL injection attacks. By combining these different methods, Art4sqli offers robust protection against a wide variety of threats.
Art4sqli’s Input Analysis Process
The process begins with the interception of user input. Art4sqli then parses this input, carefully examining its structure and content for potentially harmful elements. It subsequently integrates this input into simulated SQL queries, meticulously observing the database’s response. Any deviations from expected behavior—such as unexpected delays, error messages, or unusual data returned—trigger an alert, indicating a possible SQL injection attempt. The tool’s ability to simulate the execution of queries allows it to detect attacks even before they can cause significant damage.
Examples of Detectable SQL Injection Attacks
Several types of SQL injection attacks are readily identified by Art4sqli. The tool’s advanced analysis capabilities ensure that even sophisticated attacks are not missed.
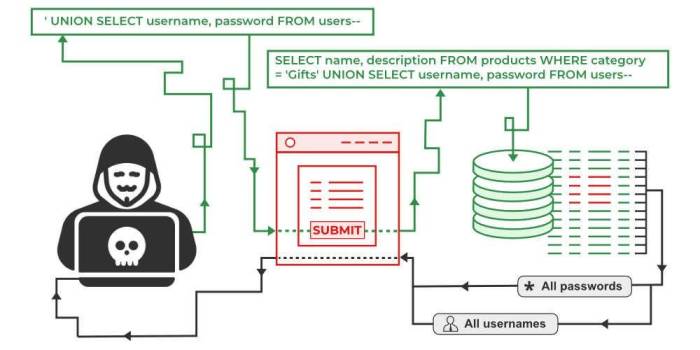
- Classic SQL Injection: Simple injection attempts, such as appending malicious code directly to a query (e.g., adding `’ OR ‘1’=’1` to a login form).
- Blind SQL Injection: Attacks that infer data from the application’s response time or other indirect indicators, rather than directly retrieving data.
- Union-Based SQL Injection: Attacks that leverage the `UNION` operator to retrieve data from unintended tables.
- Second-Order SQL Injection: Attacks where malicious code is stored and executed later, for example, within a database comment field.
- Stored Procedure Injection: Attacks targeting stored procedures, attempting to manipulate their parameters to execute unintended code.
Blind SQL Injection Detection Scenario
Imagine a web application with a user search functionality. A malicious actor attempts a blind SQL injection attack to determine if a specific user exists in the database. They craft a request that subtly modifies the search query, observing the application’s response time. If a specific user exists, the response time might be slightly longer due to the database performing additional work. Art4sqli monitors these response times. When it detects unusually long response times correlated with specific input patterns, it flags a potential blind SQL injection attempt. The tool’s analysis identifies the pattern of manipulated input that causes the delay, thus confirming the attack.
False Positives and Limitations
Source: medium.com
Art4sqli, while a powerful tool in the fight against SQL injection vulnerabilities, isn’t a silver bullet. Like any automated security scanner, it’s susceptible to false positives and has limitations when dealing with sophisticated attack vectors. Understanding these shortcomings is crucial for effective use and interpretation of its results. Ignoring these limitations can lead to wasted time investigating benign code and a false sense of security.
Art4sqli’s reliance on pattern matching and heuristic analysis means it can sometimes flag legitimate code as potentially malicious. This happens because the patterns used to identify SQL injection attempts might overlap with legitimate database interactions. For instance, dynamically generated SQL queries, even if perfectly safe, might trigger a false positive if they contain string concatenation similar to those used in malicious SQL injections.
Scenarios Leading to False Positives
Several scenarios can lead to Art4sqli generating false positives. One common culprit is the use of parameterized queries, a standard security practice that prevents SQL injection. However, if the tool doesn’t properly identify parameterized queries, it might incorrectly flag them as vulnerable. Another scenario involves applications that use complex string manipulation for non-malicious purposes; the resulting strings might resemble SQL injection attempts, leading to false alarms. Finally, the use of specific database functions or s within legitimate code might inadvertently trigger Art4sqli’s detection mechanisms.
Limitations in Detecting Sophisticated Attacks
Art4sqli, like many static analysis tools, struggles with highly obfuscated SQL injection attempts. Techniques such as encoding, using multiple layers of encryption, or employing uncommon SQL syntax can easily bypass simple pattern matching. Furthermore, attacks that leverage vulnerabilities outside the direct SQL query, such as exploiting stored procedures or manipulating server-side configurations, are unlikely to be detected by Art4sqli. Advanced attacks might use techniques that modify the application’s behavior at runtime, making static analysis less effective.
Comparison of False Positive Rates
A comparative analysis of false positive rates across different SQL injection detection tools is difficult due to the lack of standardized benchmarks and the varying complexity of the tested applications. However, a hypothetical bar chart could illustrate this. The chart would have the x-axis representing different tools (e.g., Art4sqli, SQLmap, another commercial tool), and the y-axis showing the percentage of false positives observed in a controlled test environment. We might see Art4sqli positioned somewhere in the middle, with some tools showing a significantly higher rate of false positives due to overly aggressive detection strategies, and others having a lower rate but potentially missing more subtle attacks. The precise numbers would depend on the testing methodology and the specific datasets used.
Mitigating False Positives
Minimizing false positives with Art4sqli requires a multi-pronged approach. Firstly, carefully review all flagged instances. Understand the context of the flagged code within the application’s logic. Secondly, leverage Art4sqli’s configuration options to fine-tune its sensitivity. Adjusting parameters related to pattern matching and heuristic analysis can help reduce the number of false positives. Thirdly, consider using Art4sqli in conjunction with dynamic analysis tools that test the application’s runtime behavior. This combined approach provides a more comprehensive security assessment. Finally, staying updated with the latest version of Art4sqli is crucial as improvements and bug fixes often address false positive issues.
Practical Application and Integration: Art4sqli Sqli Detection Method
Source: cloudfront.net
Integrating Art4sqli into your security testing workflow isn’t rocket science, but it does require a methodical approach. Think of it as adding a powerful new tool to your cybersecurity arsenal – one that specifically targets the ever-present threat of SQL injection vulnerabilities. Proper implementation ensures you’re leveraging its capabilities to their fullest, maximizing the protection of your web applications.
Art4sqli’s strength lies in its ability to automate the detection of SQL injection vulnerabilities. This saves significant time and resources compared to manual testing methods, allowing security professionals to focus on other critical aspects of application security. Its integration should be a seamless part of your regular security audits, acting as a first line of defense against this common attack vector.
Art4sqli Integration into a Web Application Security Testing Pipeline
Integrating Art4sqli involves adding it as a step within your existing security testing pipeline. This could be part of a Continuous Integration/Continuous Delivery (CI/CD) process, or incorporated into a regular penetration testing schedule. The specific implementation will vary depending on your existing infrastructure and tools, but the general principle remains consistent: Art4sqli should be executed after the application is built and deployed, but before it’s released to production. A common approach would be to run Art4sqli as part of automated tests, alongside other security scans and vulnerability assessments. Failing these tests should trigger alerts and prevent deployment until the identified vulnerabilities are addressed. This ensures a robust security posture and minimizes the risk of exposing your application to SQL injection attacks.
Configuring and Using Art4sqli with Django
Let’s consider a practical example using the popular Django web framework. Assume you’ve already set up your Django project and have a functional application. To integrate Art4sqli, you’ll need to incorporate it into your testing suite. This might involve writing custom scripts that interact with Art4sqli’s command-line interface or API (if available). For instance, you could create a Django management command that runs Art4sqli against your application’s URLs. The command would then parse Art4sqli’s output, identifying any reported vulnerabilities. This output could then be integrated into your CI/CD pipeline, causing the build process to fail if vulnerabilities are detected. Detailed documentation on Art4sqli’s usage and API would be essential for successful integration. Remember to thoroughly test this integration process to ensure accurate and reliable results.
Interpreting Art4sqli Results, Art4sqli sqli detection method
Art4sqli’s output typically includes a list of potentially vulnerable URLs or endpoints, along with details about the identified vulnerabilities. It’s crucial to understand that Art4sqli’s findings represent potential vulnerabilities, not confirmed exploits. Each flagged instance needs careful manual review to determine its validity. False positives are possible, so don’t immediately panic if Art4sqli reports a vulnerability. Investigate each finding meticulously, verifying its legitimacy through manual testing and code review. Consider the context of the reported vulnerability; a seemingly vulnerable endpoint might be safe due to other security measures in place. Prioritize the findings based on their severity and the potential impact on your application.
Auditing a Database Application with Art4sqli: A Step-by-Step Procedure
- Preparation: Set up your testing environment, ensuring you have a copy of the database application and necessary dependencies. Access credentials for the database should be available but treated with extreme caution.
- Configuration: Configure Art4sqli according to your application’s specifics. This might include specifying the database type, connection details, and the URLs to be tested.
- Execution: Run Art4sqli against your application. This involves executing the Art4sqli command-line tool or interacting with its API, providing the necessary configuration parameters.
- Analysis: Carefully review Art4sqli’s output. Identify potentially vulnerable endpoints and prioritize them based on their severity.
- Verification: Manually verify each potential vulnerability reported by Art4sqli. This involves manual testing and code review to confirm the vulnerability’s existence and assess its impact.
- Remediation: Address identified vulnerabilities by implementing appropriate security measures, such as parameterized queries or input sanitization. Retest after each remediation step.
- Documentation: Document the entire process, including the identified vulnerabilities, the remediation steps taken, and the results of the retesting. This documentation serves as a valuable record for future audits and security assessments.
Advanced Techniques and Future Directions
Art4sqli, while a powerful tool, operates within the current landscape of SQL injection detection. Looking ahead, significant improvements are possible through the integration of advanced techniques and a focus on evolving threat vectors. The future of effective SQLi detection lies in leveraging the power of machine learning and adapting to the complexities of modern web application architectures.
The application of machine learning (ML) and artificial intelligence (AI) promises a paradigm shift in Art4sqli’s capabilities. By training ML models on vast datasets of both benign and malicious SQL queries, Art4sqli could significantly improve its accuracy and reduce false positives. This would involve developing algorithms capable of identifying subtle patterns and anomalies indicative of SQL injection attempts that might evade traditional rule-based systems. For example, an ML model could learn to distinguish between legitimate database queries containing s like `SELECT` and `WHERE` and malicious queries that manipulate these s for nefarious purposes. The continuous learning aspect of ML would enable Art4sqli to adapt to new and emerging SQL injection techniques, ensuring its effectiveness remains robust over time.
Machine Learning Integration for Enhanced Detection
Integrating machine learning into Art4sqli would involve several key steps. First, a substantial dataset of SQL queries, categorized as either benign or malicious, would need to be compiled. This dataset would serve as the training data for the ML model. Next, a suitable ML algorithm would be selected and trained on this dataset. Recurrent Neural Networks (RNNs) or Long Short-Term Memory (LSTM) networks, known for their ability to process sequential data like SQL queries, would be particularly well-suited for this task. Finally, the trained model would be integrated into Art4sqli, enhancing its ability to detect even the most sophisticated SQL injection attempts. The model could be retrained periodically with updated datasets to maintain its accuracy and adapt to new attack vectors.
Future Enhancements and Features
Beyond machine learning, several other enhancements could significantly improve Art4sqli’s functionality. These include: improved context analysis to better differentiate between legitimate and malicious database interactions, support for a wider range of database systems and frameworks, and enhanced reporting and visualization capabilities to provide security professionals with clearer insights into detected threats. The integration of a vulnerability scoring system could also prioritize alerts based on the severity of the detected SQL injection vulnerability. For example, a high-severity alert might be triggered for a vulnerability that allows an attacker to execute arbitrary commands on the database server, while a low-severity alert might be triggered for a vulnerability that only allows an attacker to view sensitive data.
Challenges of Detecting SQL Injection in Modern Web Applications
Modern web applications often employ complex architectures, utilizing multiple layers of frameworks, microservices, and third-party libraries. This complexity presents significant challenges for SQL injection detection tools. The dynamic nature of these applications, with frequent updates and code changes, further complicates the detection process. Moreover, the use of ORM (Object-Relational Mapping) frameworks can obscure the underlying SQL queries, making it difficult to identify malicious patterns. Additionally, the increasing use of parameterized queries and prepared statements, while mitigating SQL injection risks, can also create challenges for detection tools, as they may not always accurately identify potential vulnerabilities. These complexities necessitate the development of more sophisticated detection techniques that can effectively analyze and interpret the behavior of modern web applications.
Conceptual Design: Contextual Threat Scoring Feature
A new feature, “Contextual Threat Scoring,” could be added to Art4sqli to provide a more nuanced assessment of SQL injection risks. This feature would go beyond simply identifying potentially vulnerable code segments and would incorporate contextual information, such as the application’s architecture, the sensitivity of the data being accessed, and the authentication mechanisms in place. The system would analyze various factors, assigning weights to each based on their impact on the overall risk. For instance, a query accessing highly sensitive personal data would receive a higher threat score than a query accessing less sensitive information. Similarly, a vulnerability in an application with weak authentication would receive a higher score than a vulnerability in an application with strong authentication. This contextual threat scoring would allow security teams to prioritize their remediation efforts, focusing on the most critical vulnerabilities first. The resulting score would be displayed alongside the vulnerability report, providing a clear indication of the potential impact of the SQL injection vulnerability.
Final Review
So, there you have it – a comprehensive look at the Art4sqli SQLi detection method. From understanding its core functionality to exploring its limitations and future possibilities, we’ve covered the essential aspects of this powerful security tool. By integrating Art4sqli into your security pipeline and understanding its nuances, you can significantly enhance your web application’s resilience against the ever-evolving threat of SQL injection attacks. Remember, staying ahead of the curve in cybersecurity is crucial, and Art4sqli is a key player in that fight.