Ako Ransomware Abusing Windows API Calls: Think you’re safe behind your Windows firewall? Think again. This insidious ransomware isn’t just encrypting your files; it’s exploiting the very operating system you rely on. We’re diving deep into the dark art of how Ako ransomware leverages Windows API calls to wreak havoc, from its sneaky infiltration tactics to its devastating encryption methods. Prepare for a thrilling exposé of digital crime.
We’ll unravel the mystery behind Ako’s evolution, detailing its distribution methods and favorite targets. Get ready for a technical deep dive into the specific Windows API calls it abuses, how it uses them to encrypt your data, and the shockingly simple ways it exfiltrates your precious information. We’ll even show you how to fight back, offering practical remediation strategies and preventative measures to keep Ako—and other malicious actors—at bay.
Ako Ransomware Overview
Ako ransomware, a relatively newer player in the malicious software landscape, has quickly gained notoriety for its aggressive encryption techniques and sophisticated evasion tactics. Unlike some ransomware families that have a long and complex history, Ako’s evolution is less documented, making it a challenging threat to analyze and counter. However, its impact is undeniable, showcasing the ever-evolving nature of cybercrime.
Ako’s development and distribution methods remain somewhat shrouded in mystery, but available information suggests a continuous refinement of its capabilities. Initial versions likely employed simpler encryption algorithms and less sophisticated distribution vectors. However, recent variants demonstrate improvements in both areas, highlighting the adaptive nature of the malware creators. This constant evolution underscores the need for robust cybersecurity measures to stay ahead of such threats.
Ako Ransomware Distribution Methods
The primary distribution methods employed by Ako ransomware are consistent with other ransomware families, often leveraging well-known attack vectors. This includes phishing emails containing malicious attachments or links leading to compromised websites hosting the malware. Exploiting vulnerabilities in outdated software is another common method, allowing attackers to silently deploy the ransomware onto vulnerable systems without user interaction. Furthermore, compromised remote desktop protocol (RDP) servers, often left unsecured, provide an easy entry point for Ako’s deployment. The attackers may also use software cracks or keygens found on less reputable websites, bundling the ransomware within these seemingly legitimate files. These distribution methods emphasize the importance of practicing safe computing habits and maintaining updated software.
Primary Targets of Ako Ransomware Attacks
While Ako ransomware doesn’t appear to specifically target particular industries or organizations, its impact is felt across a wide spectrum. Its indiscriminate nature makes it a threat to both individuals and businesses alike. Small and medium-sized enterprises (SMEs) often lack the robust cybersecurity infrastructure of larger corporations, making them particularly vulnerable. Home users are also at risk, especially those who are less tech-savvy and less likely to practice good online security hygiene. The lack of specific targeting highlights the broad reach of this ransomware and the importance of universal cybersecurity best practices regardless of size or industry.
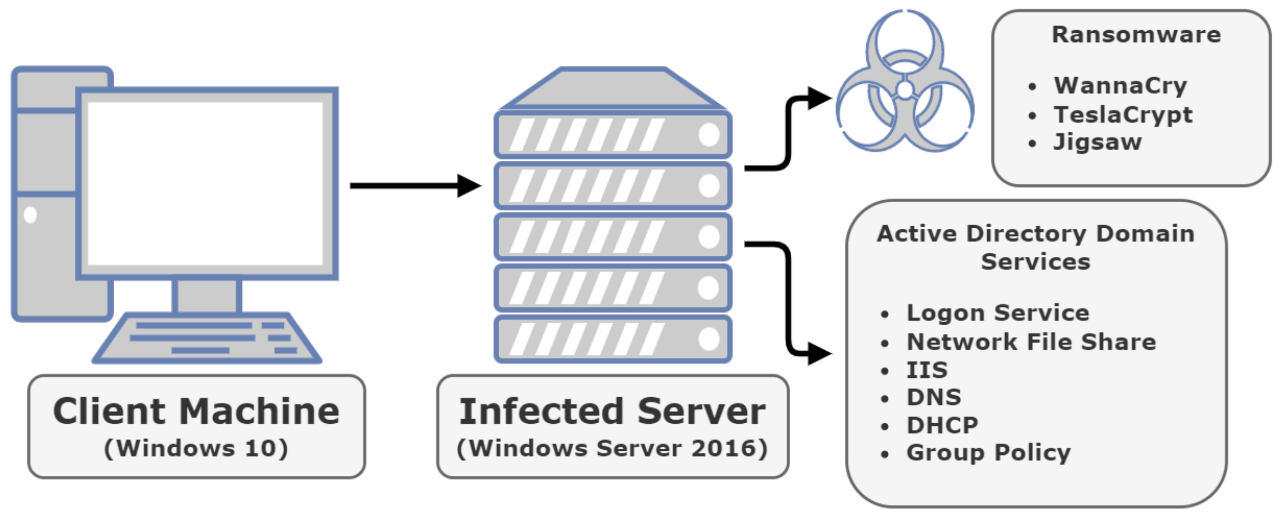
Windows API Calls Abused by Ako
Source: mdpi-res.com
Ako ransomware, like other malicious software, relies heavily on the Windows API to perform its nefarious tasks. Understanding which specific API calls it leverages is crucial for both detecting and mitigating its impact. This section delves into the specific Windows API functions exploited by Ako, examining their roles in the ransomware’s lifecycle and exploring potential defensive strategies.
Specific Windows API Calls Exploited by Ako
The following table Artikels key Windows API calls commonly abused by Ako ransomware. The exact calls may vary slightly depending on the specific Ako variant, but these represent the core functionalities consistently observed. Note that this is not an exhaustive list, and new techniques are constantly emerging.
| API Call | Function | Purpose in the Attack | Mitigation Strategy |
|---|---|---|---|
CreateFileA |
Creates or opens a file. | Used to access and encrypt victim files. Ako uses this to open target files for encryption. | Implement robust file access control lists (ACLs) and monitor for unauthorized file access attempts. Regularly back up critical data. |
ReadFile |
Reads data from an open file. | Reads the contents of files before encryption. | Similar to CreateFileA mitigation. Employing application whitelisting can help prevent unauthorized reads. |
WriteFile |
Writes data to an open file. | Writes the encrypted data back to the files. | Similar to CreateFileA mitigation. Regularly monitor file system changes for suspicious activity. |
FindFirstFileA/FindNextFileA |
Finds files matching a specified pattern. | Used to locate target files for encryption, often recursively searching directories. | Monitor for suspicious file scanning activity. Implement strong access controls to restrict access to sensitive data. |
GetVolumeInformationA |
Retrieves information about a volume. | Gathers information about the drives, potentially excluding system drives from encryption. | Regularly monitor system logs for unusual volume access attempts. |
CryptEncrypt/CryptDecrypt |
Performs cryptographic operations. | Used for the actual encryption and decryption of files (though decryption is usually only performed by the attacker with the decryption key). | Implement strong encryption for sensitive data. Regularly update antivirus software. |
RegCreateKeyExA/RegSetValueExA |
Creates and sets registry keys. | May be used to create persistence mechanisms, ensuring the ransomware restarts after a reboot. | Regularly scan and monitor the registry for unauthorized changes. Employ strong anti-malware solutions. |
DeleteFileA |
Deletes a file. | May be used to delete shadow copies to prevent file recovery. | Enable and regularly check the integrity of Volume Shadow Copy Service (VSS). |
Comparison with Other Ransomware Families
While the specific API calls used by Ako might vary slightly from other ransomware families like Ryuk, Conti, or LockBit, the underlying functionalities remain remarkably similar. All these families exploit similar core Windows API functions for file access, encryption, and persistence. The key difference often lies in the sophistication of their techniques, the types of encryption used, and the overall complexity of their code. For example, some ransomware families might utilize more advanced techniques to evade detection or employ more robust encryption algorithms. However, the fundamental reliance on core Windows API functions for file manipulation and system interaction remains a constant across many ransomware variants.
Encryption Techniques and Data Exfiltration
Ako ransomware employs sophisticated techniques to encrypt victim files and, in some cases, exfiltrate sensitive data. Understanding these methods is crucial for developing effective countermeasures and mitigating the impact of an attack. The specific encryption algorithm and data exfiltration methods used can vary slightly depending on the Ako variant, but the general principles remain consistent.
The encryption process itself relies heavily on abused Windows API calls to achieve broad access to files and system resources. These calls enable Ako to traverse directories, identify target files, and perform the encryption operation without significant user interaction. This stealthy approach is a key component of the ransomware’s effectiveness.
Encryption Algorithm
Ako ransomware typically utilizes a robust symmetric encryption algorithm, often AES (Advanced Encryption Standard) with a strong key size (e.g., 256-bit). This algorithm is widely considered secure when implemented correctly, making decryption difficult without the decryption key. The ransomware generates a unique encryption key for each victim, enhancing the difficulty of a mass decryption effort. The selection of AES is not surprising; it’s a common choice for ransomware developers due to its balance of speed and security. The key itself is then often encrypted with an asymmetric algorithm (like RSA) and stored alongside the encrypted files, but this asymmetric key is often protected with a password or further obfuscation techniques.
File Encryption Process
The file encryption process begins with the ransomware identifying target files based on their extensions (e.g., .doc, .pdf, .jpg). Abusing Windows API calls like `FindFirstFile` and `FindNextFile`, Ako iterates through directories, identifying files that meet predefined criteria. Once a target file is located, the ransomware reads its contents into memory. Then, using the chosen symmetric encryption algorithm (typically AES), it encrypts the data in memory. The encrypted data is then written back to the original file, overwriting the original content. This process repeats for each identified target file. The abuse of Windows API calls like `CreateFile`, `ReadFile`, and `WriteFile` are essential for this file manipulation. Finally, the ransomware appends a specific file extension (e.g., .ako) to the encrypted files, indicating their compromised status.
Data Exfiltration Methods
While not all Ako variants include data exfiltration, some versions employ this tactic to further pressure victims into paying the ransom. These versions utilize Windows API calls to establish network connections and transfer stolen data to a remote server controlled by the attackers. The data exfiltration process typically involves several steps.
Data Exfiltration Process Flowchart, Ako ransomware abusing windows api calls
Imagine a flowchart. The first box would be “Identify Sensitive Files.” This leads to a second box, “Read Files using Windows API calls (e.g., ReadFile)”. This connects to a third box, “Compress Data (optional)”. From there, an arrow points to “Establish Network Connection using Windows API calls (e.g., Winsock)”. This leads to the final box, “Transfer Data to C&C Server.” This represents a simplified version, as more complex steps (like encryption of exfiltrated data) might be involved. The exact API calls used might vary based on the ransomware variant and the attacker’s sophistication. For example, the `InternetOpen` and `InternetWriteFile` API calls might be used to communicate with a Command and Control (C&C) server. The data might be exfiltrated in batches or as a single large transfer, depending on the bandwidth and network conditions.
Impact and Remediation Strategies
Source: malwareguide112.com
A successful Ako ransomware attack can cripple an organization, leading to significant financial losses and reputational damage. The impact extends far beyond the immediate cost of decryption; it encompasses business disruption, legal ramifications, and the long-term erosion of customer trust. Understanding the potential consequences is crucial for developing effective prevention and recovery strategies.
The severity of the impact depends on several factors, including the size of the organization, the criticality of the encrypted data, and the ransomware’s capabilities. For example, a small business might face closure after an attack, while a larger enterprise might experience significant downtime and financial losses due to halted operations and the cost of remediation. The loss of sensitive customer data could trigger hefty fines and legal battles, further compounding the damage.
Data Recovery Procedures
Recovering data encrypted by Ako ransomware is a complex process that requires careful planning and execution. Attempting to decrypt the files without professional assistance is risky and may lead to further data loss or system compromise. The first step is to isolate the affected systems from the network to prevent further spread of the ransomware. Next, a thorough assessment of the damage needs to be conducted to identify the extent of the encryption and the types of files affected. This involves analyzing system logs and identifying the affected files and folders. If backups are available, restoring data from a clean backup is the safest and most efficient method. If backups are unavailable or corrupted, specialized decryption tools might be necessary, though their effectiveness depends on the specific variant of Ako ransomware and the availability of a decryption key. Professional data recovery services should be considered in such cases, as they possess the expertise and tools to handle complex recovery scenarios. Remember, attempting to manually decrypt files without the proper knowledge and tools could irreparably damage your data.
Prevention Best Practices
Proactive measures are paramount in preventing Ako ransomware infections. A multi-layered security approach is essential, combining technical safeguards with employee training and awareness programs.
- Regular Software Updates: Keeping operating systems, applications, and antivirus software up-to-date patches vulnerabilities that ransomware exploits.
- Robust Backup Strategy: Implement a comprehensive backup strategy that includes regular backups to an offline or cloud-based storage location. This ensures data recovery even if the ransomware encrypts all local files. Consider using the 3-2-1 backup rule: 3 copies of your data, on 2 different media, with 1 copy offsite.
- Strong Passwords and Multi-Factor Authentication (MFA): Enforce strong, unique passwords for all accounts and implement MFA wherever possible to add an extra layer of security.
- Employee Security Awareness Training: Educate employees about phishing scams, malicious attachments, and other social engineering tactics used to distribute ransomware. Regular training reinforces best practices and helps employees identify and avoid threats.
- Network Security Measures: Implement robust network security measures, including firewalls, intrusion detection/prevention systems, and regular security audits to identify and mitigate vulnerabilities.
- Principle of Least Privilege: Grant users only the necessary access rights to prevent lateral movement of ransomware within the network. This limits the damage if a system is compromised.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify and address potential vulnerabilities before they can be exploited by ransomware.
- Antivirus and Endpoint Detection and Response (EDR): Deploy robust antivirus and EDR solutions to detect and prevent ransomware infections. EDR solutions provide advanced threat detection and response capabilities.
Malware Analysis Techniques: Ako Ransomware Abusing Windows Api Calls
Unmasking the secrets of Ako ransomware requires a multi-pronged approach leveraging both static and dynamic analysis techniques. These methods allow security researchers to understand how the malware operates, identify its malicious components, and ultimately develop effective countermeasures. By carefully examining the ransomware’s code and observing its runtime behavior, we can paint a comprehensive picture of its capabilities and attack methods.
Static analysis involves examining the ransomware without executing it. This allows researchers to identify potential malicious code segments, embedded commands, and overall structure before triggering any harmful actions. Dynamic analysis, on the other hand, involves running the ransomware in a controlled environment (like a sandbox) to observe its behavior in real-time. This provides insights into its network activity, file system interactions, and encryption processes. Combining these techniques provides a robust understanding of Ako’s behavior.
Static Analysis of Ako Ransomware
Static analysis starts with examining the ransomware’s file structure and code. This includes analyzing the file’s metadata, identifying strings and embedded resources, and disassembling the code to understand its logic. Tools like IDA Pro and Ghidra are invaluable for this process, allowing researchers to visually inspect the code, identify functions, and trace the flow of execution. By analyzing the code, researchers can identify the algorithms used for encryption, the methods for file selection, and the communication channels used for command and control (C2). For instance, analyzing the code might reveal hardcoded API calls to encryption libraries or specific network addresses used for exfiltration. The presence of obfuscation techniques, such as packing or code virtualization, adds complexity, requiring advanced deobfuscation tools and techniques.
Dynamic Analysis of Ako Ransomware
Dynamic analysis complements static analysis by observing the ransomware’s behavior during execution. This is typically done in a virtualized environment, such as a sandbox, to isolate the malware and prevent it from affecting a real system. Tools like Cuckoo Sandbox and Hybrid Analysis automate this process, providing detailed reports on the malware’s activities. During dynamic analysis, researchers monitor system calls, network traffic, and file system changes. They look for indicators like unusual network connections, attempts to encrypt specific file types, or the creation of ransom notes. Analyzing the network traffic can reveal the C2 server used by the ransomware, allowing for the identification of other infected systems and the potential disruption of the attacker’s infrastructure.
Identifying Indicators of Compromise (IOCs)
Identifying IOCs is crucial for detecting and responding to Ako ransomware infections. IOCs are artifacts left behind by the malware, such as specific file names, registry keys, network addresses, or process IDs. These indicators can be identified through both static and dynamic analysis. Examples of IOCs associated with Ako ransomware might include specific file extensions targeted for encryption (.doc, .pdf, .jpg, etc.), unique strings embedded within the malware’s code, or specific registry keys used for persistence. Network IOCs could include the IP addresses or domains of C2 servers used by the ransomware operators. Gathering and sharing these IOCs with security communities is vital for proactive threat detection and response.
Tools and Techniques for Reverse Engineering Ako Ransomware
Understanding Ako’s inner workings requires advanced reverse engineering techniques. Several tools and techniques can assist in this process:
- Disassemblers (IDA Pro, Ghidra): These tools convert machine code into assembly language, making it easier to understand the ransomware’s logic.
- Debuggers (x64dbg, WinDbg): Debuggers allow step-by-step execution of the code, enabling researchers to observe the ransomware’s behavior in real-time and identify critical functions.
- Sandbox Environments (Cuckoo Sandbox, Hybrid Analysis): Sandboxes provide a controlled environment for executing the malware without risking damage to a real system.
- Network Monitoring Tools (Wireshark, tcpdump): These tools capture and analyze network traffic, revealing communication with C2 servers and data exfiltration attempts.
- Memory Forensics Tools (Volatility): These tools analyze memory dumps to extract information about running processes and malware behavior, even after the malware has been terminated.
- Deobfuscation Tools: Many ransomware samples employ obfuscation techniques to hide their malicious code. Specialized tools and techniques are necessary to unravel this obfuscation.
Security Implications and Future Threats

Source: lepuchin.com
Ako ransomware, with its sophisticated exploitation of Windows API calls, presents a significant threat to individual users and organizations alike. Its ability to bypass traditional security measures and encrypt critical data highlights vulnerabilities in current security practices and the need for proactive, multi-layered defense strategies. The implications extend beyond immediate data loss, impacting business continuity, financial stability, and potentially even national security depending on the targeted victims.
The successful deployment of Ako underscores the persistent arms race between malware developers and security professionals. Ako’s reliance on legitimate Windows functions makes detection more challenging, requiring a deeper understanding of system behavior and advanced threat hunting techniques. This necessitates a shift towards more proactive security measures that focus on behavior analysis rather than solely relying on signature-based detection.
Potential Future Variations of Ako Ransomware
Ako’s design suggests several potential avenues for future development. We might see Ako variants incorporating advanced evasion techniques, such as process injection or rootkit capabilities, to further hinder detection and removal. Increased use of polymorphism or metamorphic techniques could also make signature-based detection even more difficult. Furthermore, future iterations could integrate features like self-propagation or the ability to target specific network services, expanding the scope of the attack and increasing the potential for widespread damage. For instance, a future variant could exploit vulnerabilities in cloud storage services, extending its reach beyond local machines. Imagine a version of Ako that not only encrypts local files but also automatically uploads encrypted copies to cloud storage, making recovery even more challenging. This represents a logical evolution in ransomware design, leveraging cloud services to further complicate recovery and increase the pressure on victims to pay the ransom.
Windows Vulnerabilities Exploited by Ako
While the specific vulnerabilities exploited by Ako might not be publicly known (to prevent further exploitation), the ransomware’s reliance on Windows API calls points towards potential weaknesses in the operating system’s security model. These could include vulnerabilities in access control mechanisms, allowing Ako to gain elevated privileges, or flaws in the handling of system processes that enable code injection or other malicious actions. The potential for exploitation of less-known or unpatched vulnerabilities in specific Windows services or drivers is also a concern. For example, a weakness in a network driver could allow Ako to spread laterally across a network, infecting multiple machines. Similarly, a vulnerability in a specific Windows service could provide Ako with a privileged position to execute its malicious code and evade detection. The continuous release of security patches by Microsoft highlights the ongoing effort to address such vulnerabilities, emphasizing the importance of keeping systems updated.
Broader Security Implications
The widespread adoption of ransomware like Ako highlights the increasing sophistication of cyberattacks and the inadequacy of traditional security measures in certain contexts. The reliance on legitimate system calls for malicious purposes underscores the need for more advanced security solutions that go beyond simple signature-based detection. This necessitates a shift towards proactive threat hunting, behavior analysis, and the adoption of robust security architectures that include advanced threat detection and response capabilities. Furthermore, user education and training play a crucial role in mitigating the risk of ransomware attacks, as many infections occur due to phishing or social engineering. The overall impact extends beyond the immediate financial loss to victims, affecting trust in digital infrastructure and potentially hindering economic growth and innovation.
Ultimate Conclusion
So, there you have it: Ako ransomware isn’t just another digital thug; it’s a master manipulator, exploiting the very system designed to protect you. Understanding its tactics is the first step in building a robust defense. By recognizing the telltale signs of infection and implementing proactive security measures, you can significantly reduce your risk of becoming another victim. Remember, knowledge is power—and in the world of cybersecurity, it’s the ultimate weapon.


