Adobe ColdFusion vulnerability: It’s a phrase that sends shivers down the spines of developers everywhere. For years, ColdFusion has powered countless websites and applications, but its age and complexity have also made it a tempting target for cybercriminals. This isn’t just about technical jargon; we’re talking about potential data breaches, financial losses, and reputational damage. Let’s unpack the vulnerabilities, explore the risks, and discover how to safeguard your ColdFusion applications.
From SQL injection nightmares to the terrifying prospect of remote code execution, the potential threats are real and varied. Understanding the common attack vectors, like cross-site scripting (XSS) and other exploits, is the first step towards building a robust defense. We’ll dissect real-world examples, showcasing how these vulnerabilities have been exploited and the devastating consequences that followed. This isn’t just a theoretical exercise; it’s a survival guide for the digital age.
Introduction to Adobe ColdFusion Vulnerabilities
Adobe ColdFusion, a rapid web application development platform, has a history spanning decades. While offering powerful features for building dynamic websites and applications, its security landscape has been a recurring concern. Early versions lacked robust security features, leading to vulnerabilities that were frequently exploited. Over time, Adobe has released numerous updates and security patches, but the legacy of older, unpatched systems continues to pose a significant risk. Understanding the common vulnerabilities and their potential impact is crucial for securing ColdFusion applications.
ColdFusion’s vulnerabilities stem from various sources, including outdated components, insecure coding practices, and insufficient configuration. Common issues include SQL injection flaws, cross-site scripting (XSS) vulnerabilities, remote file inclusion (RFI) attacks, and insecure session management. These vulnerabilities can allow attackers to gain unauthorized access to sensitive data, execute malicious code, or even take complete control of the server hosting the ColdFusion application. The severity of these vulnerabilities varies depending on the specific flaw and the application’s architecture.
Common ColdFusion Vulnerabilities
Many ColdFusion vulnerabilities arise from improper handling of user inputs. SQL injection, for instance, occurs when an attacker manipulates user input to inject malicious SQL code into database queries. This allows them to bypass security measures, access, modify, or delete data. Similarly, Cross-Site Scripting (XSS) vulnerabilities occur when an application fails to properly sanitize user input before displaying it on a web page. This can allow attackers to inject malicious JavaScript code, potentially stealing user cookies or redirecting users to phishing sites. Remote File Inclusion (RFI) attacks exploit vulnerabilities that allow an attacker to include and execute arbitrary files from a remote server. This often results in code execution and server compromise. Insecure session management can allow attackers to hijack user sessions, gaining unauthorized access to their accounts and data.
Examples of Real-World ColdFusion Exploits
While specific details of many exploits are kept confidential for security reasons, public reports and security advisories illustrate the real-world impact of ColdFusion vulnerabilities. For example, in 2010, a critical vulnerability in ColdFusion allowed attackers to execute arbitrary code remotely. This vulnerability, if left unpatched, could have resulted in widespread server compromises and data breaches. Another example involves the exploitation of SQL injection vulnerabilities to steal sensitive customer data from e-commerce applications built using ColdFusion. These examples underscore the importance of regularly updating ColdFusion installations, employing secure coding practices, and implementing robust security measures to mitigate these risks. The consequences of neglecting these precautions can be severe, leading to financial losses, reputational damage, and legal liabilities.
Common Vulnerability Types
Source: teratech.com
Adobe ColdFusion, while a powerful platform, is susceptible to various vulnerabilities if not properly secured. Understanding these vulnerabilities is crucial for developers and administrators to implement effective mitigation strategies and protect their applications. This section details some of the most prevalent vulnerability types found in ColdFusion applications.
SQL Injection
SQL injection attacks exploit vulnerabilities in database interactions. Malicious actors can inject SQL code into input fields, manipulating database queries to gain unauthorized access to data, modify or delete records, or even execute arbitrary commands on the database server. This occurs when user-supplied data is directly incorporated into SQL queries without proper sanitization or parameterization.
| Vulnerability Type | Description | Example Code (Vulnerable) | Mitigation Strategy |
|---|---|---|---|
| SQL Injection | Improper handling of user input in database queries allows attackers to inject malicious SQL code. | |
Use parameterized queries or prepared statements. Avoid directly concatenating user input into SQL queries. Example: |
Cross-Site Scripting (XSS)
Cross-site scripting vulnerabilities allow attackers to inject malicious scripts into web pages viewed by other users. These scripts can steal session cookies, redirect users to phishing sites, or deface web pages. XSS attacks typically occur when user-supplied data is displayed on a web page without proper encoding or escaping.
| Vulnerability Type | Description | Example Code (Vulnerable) | Mitigation Strategy |
|---|---|---|---|
| Cross-Site Scripting (XSS) | Improperly sanitized user input is reflected back to the user’s browser, allowing the injection of malicious JavaScript. | |
Encode user input using HTMLEditFormat or equivalent functions before displaying it on a web page. Sanitize all user input before using it in any context. |
Remote Code Execution (RCE)
Remote code execution vulnerabilities allow attackers to execute arbitrary code on the ColdFusion server. This is often the most severe type of vulnerability, granting attackers complete control over the server. RCE vulnerabilities can arise from various sources, including improper file handling, insecure configuration, and vulnerabilities in ColdFusion components or custom code.
| Vulnerability Type | Description | Example Code (Vulnerable – Hypothetical) | Mitigation Strategy |
|---|---|---|---|
| Remote Code Execution (RCE) | Allows attackers to execute arbitrary code on the server, potentially leading to complete compromise. | |
Strictly validate and sanitize all file uploads. Never execute code from untrusted sources. Implement robust input validation and filtering. Regularly update ColdFusion and its components. |
Session Hijacking
Session hijacking involves an attacker stealing a user’s session ID to gain unauthorized access to their account. This can be achieved through various methods, including exploiting XSS vulnerabilities, sniffing network traffic, or exploiting vulnerabilities in session management. Weak or predictable session IDs increase the risk of session hijacking.
| Vulnerability Type | Description | Example (Vulnerable – Conceptual) | Mitigation Strategy |
|---|---|---|---|
| Session Hijacking | Attackers steal a user’s session ID to impersonate them. | Using easily guessable session IDs or failing to properly secure cookies. | Use strong, unpredictable session IDs. Implement HTTPS to encrypt communication. Use secure cookie settings (HttpOnly, Secure). Regularly rotate session IDs. |
Impact and Consequences of Exploits

Source: itlandmark.com
A successful exploit of a ColdFusion vulnerability can have devastating consequences for both individual applications and entire businesses. The severity depends on the type of vulnerability exploited and the sensitivity of the data involved. From minor inconveniences to catastrophic financial losses and reputational damage, the potential impact is wide-ranging and should be taken very seriously.
The consequences stem primarily from unauthorized access to sensitive information and disruption of services. Data breaches expose confidential customer information, intellectual property, and financial records, leading to significant legal and financial repercussions. System compromises can lead to service outages, operational disruptions, and the potential for further malicious activities such as ransomware attacks.
Data Breaches and Their Fallout
Data breaches resulting from ColdFusion vulnerabilities can expose a wide array of sensitive data, including personally identifiable information (PII), financial data, and intellectual property. The immediate consequences often include regulatory fines under laws like GDPR and CCPA, legal actions from affected individuals and businesses, and significant damage to brand reputation. Long-term impacts can include loss of customer trust, decreased market share, and increased insurance premiums. The cost of remediation, including forensic investigations, notification efforts, and credit monitoring services for affected individuals, can also be substantial. For example, the 2017 Equifax breach, while not directly related to ColdFusion, highlights the immense financial and reputational costs associated with large-scale data breaches; the company faced billions of dollars in fines and legal settlements.
System Compromise and Operational Disruption
Beyond data breaches, successful exploits can compromise the entire ColdFusion application and the underlying server infrastructure. This can lead to complete service outages, rendering the application unusable for extended periods. The disruption can significantly impact business operations, leading to lost revenue, decreased productivity, and potentially even the inability to fulfill contracts. Furthermore, compromised systems can be used as launching points for further attacks against other systems within the organization’s network, expanding the scope and severity of the incident. A scenario where a ColdFusion application is compromised and used to launch a Distributed Denial of Service (DDoS) attack against a company’s website, leading to significant downtime and lost sales, illustrates the potential for cascading consequences.
Real-World Examples and Their Effects
While specific details of ColdFusion exploits are often kept confidential due to security reasons, numerous reported incidents involving similar vulnerabilities in other web applications highlight the potential for significant damage. For example, attacks exploiting SQL injection vulnerabilities in web applications have resulted in massive data breaches and financial losses for various organizations. These incidents underscore the importance of proactive security measures, including regular patching, vulnerability scanning, and robust security audits, to mitigate the risks associated with ColdFusion vulnerabilities. The impact of these breaches isn’t limited to financial losses; the reputational damage can be long-lasting, affecting customer loyalty and investor confidence.
Vulnerability Detection and Prevention
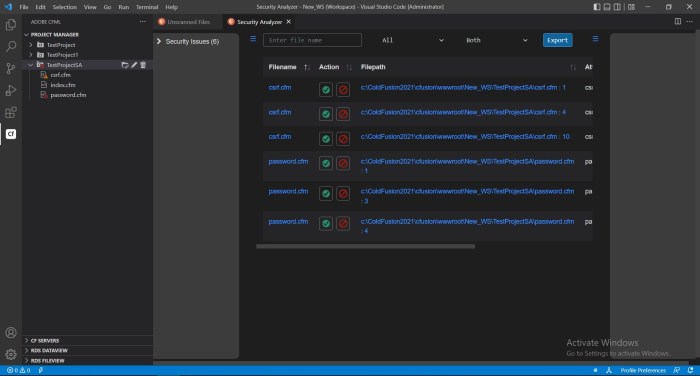
Source: adobe.com
So, you’ve learned about the nasty vulnerabilities lurking in your ColdFusion applications. Now, let’s talk about how to find and stop them before they cause serious trouble. Proactive security is key, folks, and it’s not as daunting as it sounds.
Identifying and preventing ColdFusion vulnerabilities requires a multi-pronged approach combining automated tools with skilled human expertise. Think of it like a comprehensive health checkup for your application – regular check-ups are crucial for long-term health.
Static and Dynamic Analysis Techniques
Static analysis examines your ColdFusion code without actually running it. Think of it as a thorough code review, but on steroids. Automated tools scan for common coding flaws, like SQL injection vulnerabilities or cross-site scripting (XSS) weaknesses, flagging potential problems before they become real-world exploits. Dynamic analysis, on the other hand, involves running the application and observing its behavior under various conditions. This helps identify vulnerabilities that only appear during runtime. Penetration testing, a form of dynamic analysis, simulates real-world attacks to uncover exploitable weaknesses. A skilled penetration tester can identify vulnerabilities that automated tools might miss, offering a comprehensive security assessment. The combination of both methods provides the most thorough security evaluation.
Secure Development Lifecycle (SDLC) for ColdFusion Applications
Implementing a robust SDLC is paramount. This isn’t just about coding; it’s about a structured process encompassing every stage of application development, from initial design to deployment and maintenance. A secure SDLC integrates security considerations into each phase, preventing vulnerabilities from taking root in the first place. This includes secure coding practices, regular security testing, and a well-defined incident response plan. For example, integrating security scanning tools into the build process ensures that code is checked for vulnerabilities before deployment. Failing to implement such a system can lead to significant security breaches, resulting in financial losses, reputational damage, and legal consequences. A well-defined SDLC acts as a safeguard against such issues.
Best Practices for Preventing ColdFusion Vulnerabilities
Following these best practices significantly reduces your application’s vulnerability surface. Think of them as your application’s security armor.
- Regularly update ColdFusion and related software: Patches often address known vulnerabilities. Neglecting updates is a major security risk.
- Use parameterized queries to prevent SQL injection: This prevents attackers from injecting malicious SQL code into your database queries.
- Validate and sanitize all user inputs: Never trust user input. Always validate and sanitize it before using it in your application. This helps prevent XSS and other injection attacks.
- Implement robust authentication and authorization mechanisms: Protect your application with strong passwords, multi-factor authentication, and role-based access control.
- Encode output to prevent cross-site scripting (XSS): Properly encoding output prevents attackers from injecting malicious JavaScript code into your application.
- Use a web application firewall (WAF): A WAF acts as a shield, protecting your application from common web attacks.
- Regularly perform security audits and penetration testing: Proactive security assessments identify vulnerabilities before attackers do.
- Follow the principle of least privilege: Grant users only the necessary permissions to perform their tasks.
- Employ robust error handling: Avoid revealing sensitive information in error messages.
- Keep your ColdFusion server and related components up-to-date: This ensures that you benefit from the latest security patches and improvements.
Remediation Strategies and Patching
Addressing Adobe ColdFusion vulnerabilities requires a proactive and multi-layered approach. Ignoring these vulnerabilities can leave your system exposed to significant risks, including data breaches and system compromise. Effective remediation involves prompt patching, robust security practices, and a commitment to ongoing maintenance.
The cornerstone of any effective ColdFusion security strategy is timely patching. Adobe regularly releases security updates addressing known vulnerabilities. These patches are crucial because they directly address the flaws exploited by attackers. Delaying patching significantly increases your exposure to attacks, potentially leading to severe consequences. A robust patching schedule, coupled with rigorous testing in a non-production environment before deploying to production, minimizes the risk of unintended disruptions while maximizing security.
Patch Management Process
Implementing a structured patch management process is essential. This involves regularly checking for updates from Adobe, downloading and testing the patches in a controlled environment, and then deploying them to your production systems. A well-defined rollout plan, including thorough testing and rollback procedures, mitigates the risk of downtime or unforeseen complications. Automated patching systems can streamline this process, ensuring patches are applied consistently and efficiently. Consider using a change management system to track patch deployments and maintain a comprehensive audit trail.
Security Hardening Techniques
Beyond patching, proactive security measures significantly strengthen your ColdFusion application’s defenses. These measures go beyond simply addressing known vulnerabilities and focus on building a more resilient system overall. Regular security audits, penetration testing, and vulnerability scanning can help identify and address potential weaknesses before they can be exploited. Implementing strong access controls, including multi-factor authentication, limits unauthorized access to your ColdFusion server and applications. Regularly reviewing and updating user permissions helps ensure only authorized individuals have access to sensitive data and functionalities. Input validation and sanitization are critical to prevent injection attacks, such as SQL injection and cross-site scripting (XSS). Properly configured web application firewalls (WAFs) can also help protect against various web-based attacks.
Importance of Regular Security Updates
Regular security updates aren’t just a good idea; they’re a necessity in today’s threat landscape. Cybercriminals are constantly developing new attack vectors, and relying solely on previously applied patches leaves you vulnerable to emerging threats. By staying current with the latest patches and security best practices, you significantly reduce the attack surface of your ColdFusion applications and minimize the risk of exploitation. Regular updates often include not only bug fixes but also performance improvements and new features that enhance the overall security posture of your system. This proactive approach is far more efficient and cost-effective than reacting to a security breach after it has occurred.
Secure Coding Practices
Writing secure ColdFusion code isn’t about adding a few extra lines; it’s about building security into the very foundation of your application. By proactively addressing potential vulnerabilities, you significantly reduce the risk of exploitation and protect your users’ data. This involves a multifaceted approach encompassing careful planning, robust coding techniques, and regular security audits.
Secure coding practices in ColdFusion demand a shift in mindset, moving from a “fix-it-later” approach to a proactive, preventative strategy. Ignoring security best practices can lead to costly breaches, reputational damage, and legal ramifications. Prioritizing security from the outset saves time, resources, and potential headaches down the line.
Input Validation and Sanitization
Input validation and sanitization are fundamental to secure ColdFusion development. They act as the first line of defense against many common vulnerabilities, such as SQL injection and cross-site scripting (XSS). Failing to properly validate and sanitize user inputs leaves your application vulnerable to malicious attacks.
Effective input validation involves checking that data conforms to expected formats, types, and lengths. Sanitization, on the other hand, involves removing or escaping potentially harmful characters from user input before it’s used in your application. This ensures that even if an attacker tries to inject malicious code, it’s rendered harmless.
- Secure Example: Using CFML’s built-in functions like
PreserveSingleQuotes()andREReplace()to sanitize user input before using it in a database query or displaying it on a web page. For example, - Insecure Example: Directly embedding user input into a database query without any validation or sanitization. This leaves your application wide open to SQL injection attacks. For example,
SELECT * FROM users WHERE username='#form.username#'
Parameterization of Database Queries
Using parameterized queries is crucial to prevent SQL injection attacks. Instead of directly embedding user input into SQL queries, parameterized queries treat user input as data, not as part of the SQL command itself. This prevents attackers from manipulating the query’s logic.
Parameterized queries significantly reduce the risk of SQL injection by separating the data from the SQL code. This approach ensures that even malicious input is treated as plain data and cannot be interpreted as executable code.
- Secure Example: Using ColdFusion’s
cfqueryparamtag to pass user input as parameters to a database query. For instance:SELECT * FROM users WHERE username = - Insecure Example: Concatenating user input directly into the SQL query string. This is extremely vulnerable to SQL injection.
Session Management
Proper session management is critical for protecting user data and preventing session hijacking. This includes using secure session IDs, implementing appropriate session timeouts, and employing HTTPS to encrypt session data.
Robust session management practices are essential to maintaining the confidentiality and integrity of user sessions. Failure to secure sessions can lead to unauthorized access and data breaches.
- Secure Example: Utilizing ColdFusion’s built-in session management features, ensuring HTTPS is enabled, and regularly rotating session IDs. Setting appropriate session timeouts based on risk assessment also strengthens security.
- Insecure Example: Storing sensitive information directly in session variables without encryption and failing to implement proper session timeouts.
Output Encoding
Output encoding is essential to prevent cross-site scripting (XSS) attacks. This involves encoding special characters in user-supplied data before it’s displayed on a web page. This prevents malicious scripts from being executed in the user’s browser.
Output encoding ensures that data displayed to the user is rendered as plain text, neutralizing any potential malicious code. This is a critical step in protecting users from XSS attacks.
- Secure Example: Using ColdFusion’s
HTMLEditFormat()function to encode HTML entities before displaying user input. For example:#HTMLEditFormat(form.userInput)# - Insecure Example: Directly displaying user input on a web page without any encoding. This is highly vulnerable to XSS attacks.
Third-Party Component Vulnerabilities
Third-party components, while offering significant time and resource savings in ColdFusion development, introduce a considerable security risk. These pre-built modules, often downloaded from repositories or purchased from vendors, can contain vulnerabilities unknown to the developer until exploited. Ignoring this risk can expose your application to severe security breaches, data loss, and reputational damage. Understanding and mitigating these risks is crucial for maintaining a secure ColdFusion application.
The reliance on external code introduces a level of trust that needs careful consideration. A vulnerability in a seemingly innocuous component can create a significant weakness in your application’s overall security posture. This is especially true given the potential for vulnerabilities to remain undiscovered for extended periods. Proactive measures are essential to minimize the impact of these risks.
Assessing the Security of Third-Party Components
Thorough vetting of third-party components is paramount. This involves more than just checking for positive reviews; it necessitates a deep dive into the component’s source code, security audits, and the vendor’s reputation. A simple check for recent updates can also reveal potential security fixes implemented by the component’s maintainers. Understanding the component’s dependencies and their security implications is equally important. Failing to do so could leave your application vulnerable through transitive dependencies.
Managing and Mitigating Third-Party Component Vulnerabilities, Adobe coldfusion vulnerability
Effective management of third-party component vulnerabilities requires a multi-faceted approach. Regular security audits are essential to identify potential weaknesses. This should include both automated vulnerability scanners and manual code reviews, especially focusing on the interactions between the third-party component and your application’s core functionality. Maintaining a detailed inventory of all third-party components and their versions is critical for tracking updates and patching vulnerabilities. When a vulnerability is discovered, rapid patching and deployment of the updated component are crucial to minimize the window of exposure.
Implementing a robust change management process is also vital. This ensures that updates are properly tested in a staging environment before being deployed to production, minimizing the risk of unintended consequences. Finally, consider the use of a software composition analysis (SCA) tool. These tools automatically scan your application’s codebase to identify the components used and check them against known vulnerability databases, offering early warnings of potential security risks. Using a well-defined process for evaluating and integrating third-party components reduces the likelihood of incorporating insecure code into your ColdFusion application.
Security Auditing and Monitoring: Adobe Coldfusion Vulnerability
Regular security audits and monitoring are crucial for maintaining the integrity and confidentiality of your ColdFusion applications. Ignoring these practices leaves your systems vulnerable to exploitation, potentially leading to data breaches, financial losses, and reputational damage. A proactive approach, incorporating regular checks and robust monitoring systems, is vital for identifying and mitigating threats before they escalate.
Proactive security measures, rather than reactive responses, are the key to successful ColdFusion application security. Think of it like regular health checkups – it’s much better to catch potential problems early rather than waiting for a major crisis. Consistent monitoring allows for early detection of suspicious activity, giving you valuable time to respond effectively.
Implementing Security Monitoring and Alerting Systems
A comprehensive security monitoring system for ColdFusion applications should encompass several key components. First, you need a centralized logging system that captures all relevant events, including user logins, application errors, and database interactions. This data forms the foundation for identifying anomalies and potential security breaches. Second, integrate intrusion detection and prevention systems (IDPS) to actively monitor network traffic for malicious activities targeting your ColdFusion infrastructure. These systems can detect and block suspicious patterns, preventing attacks before they reach your applications. Finally, implement a robust alerting system that notifies your security team immediately when critical events occur. This system should be configurable to prioritize alerts based on severity and potential impact. For example, an unauthorized login attempt should trigger an immediate alert, while a minor application error might only require logging. Consider using tools like Splunk, ELK stack, or dedicated security information and event management (SIEM) systems to manage and analyze this data effectively.
Responding to Security Incidents
A well-defined incident response plan is paramount. This plan should Artikel clear steps for handling security incidents, including the identification, containment, eradication, recovery, and post-incident analysis phases. The plan should designate roles and responsibilities for different team members, ensuring a coordinated response. For example, a dedicated security team member should be responsible for isolating the affected system, while another might focus on analyzing logs to identify the root cause. Regular drills and simulations will help the team familiarize themselves with the plan and refine their response capabilities. A real-world example might involve a SQL injection attempt. The incident response plan would dictate the steps to block the malicious traffic, investigate the vulnerability, patch the affected application, and restore affected data. Post-incident analysis would then identify the weaknesses that allowed the attack and implement measures to prevent similar incidents in the future. Detailed documentation of each incident, including the root cause, remediation steps, and lessons learned, is crucial for continuous improvement.
Future Trends and Emerging Threats
The world of ColdFusion application security is constantly evolving, with new threats emerging alongside advancements in technology. Understanding these future trends is crucial for developers and security professionals to proactively protect ColdFusion applications from increasingly sophisticated attacks. The convergence of several technological advancements and evolving attacker tactics presents a unique challenge for ColdFusion’s future security landscape.
The increasing sophistication of automated attacks, coupled with the potential for vulnerabilities in third-party libraries and integrations, poses a significant threat. Furthermore, the expanding attack surface due to the integration of ColdFusion with cloud services and mobile technologies necessitates a proactive and adaptive security strategy. We’ll explore these trends and their implications for ColdFusion security in the following sections.
Emerging Threats and Vulnerabilities
The rise of serverless architectures and the increasing adoption of microservices present new challenges for securing ColdFusion applications. Attackers may exploit vulnerabilities in individual microservices to gain access to the entire system. Similarly, serverless functions, while offering scalability, can introduce security complexities if not properly configured and monitored. Another emerging threat is the use of AI-powered tools by attackers to automate vulnerability scanning and exploit discovery. These tools can identify and exploit weaknesses in ColdFusion applications more efficiently than traditional methods. For instance, an AI-powered tool could identify a specific pattern in ColdFusion code that indicates a vulnerability to SQL injection, then automatically generate and execute an exploit.
Predictions on Future Security Challenges
Predicting the future is always challenging, but based on current trends, we can anticipate several key security challenges for ColdFusion applications. First, the growing reliance on third-party libraries and APIs will continue to increase the attack surface, as vulnerabilities in these components can directly impact ColdFusion applications. Second, the increasing complexity of ColdFusion applications, especially those built using microservices and serverless architectures, will make it more difficult to identify and address security vulnerabilities. Third, the increasing sophistication of attackers and the use of AI-powered tools will make it harder to defend against attacks. For example, we might see a rise in targeted attacks exploiting zero-day vulnerabilities in less frequently updated ColdFusion installations. This mirrors the trend seen with other software where outdated versions become prime targets for malicious actors.
The Role of AI and Machine Learning in ColdFusion Security
AI and machine learning are not just threats; they can also be powerful tools for enhancing ColdFusion security. AI-powered security tools can be used for automated vulnerability scanning, threat detection, and incident response. Machine learning algorithms can analyze large datasets of security logs to identify patterns and anomalies indicative of malicious activity. For example, an AI system could be trained to recognize the characteristics of a successful SQL injection attack, enabling it to detect similar attacks in real-time. Furthermore, AI can assist in the development of more secure ColdFusion applications by automatically identifying potential vulnerabilities in code during the development process. This proactive approach helps prevent vulnerabilities from ever reaching production environments. However, it’s important to note that AI security tools are not a silver bullet; human expertise is still essential for interpreting results and developing effective security strategies.
Closing Summary
Securing your ColdFusion applications isn’t a one-time fix; it’s an ongoing process. Regular security audits, proactive patching, and a commitment to secure coding practices are essential. By understanding the vulnerabilities, implementing effective mitigation strategies, and staying ahead of emerging threats, you can significantly reduce your risk and protect your valuable data. Ignoring these vulnerabilities is simply not an option in today’s interconnected world. Let’s build a more secure digital future, one ColdFusion application at a time.