3 3m POP3 IMAP services unencrypted? Yeah, we’re diving headfirst into the murky waters of unsecured email. Think of it like leaving your front door unlocked – anyone can waltz in and grab whatever they want. We’re talking data breaches, identity theft, the whole shebang. This isn’t just a techy problem; it’s a real-world threat that can seriously impact your life. Let’s explore the vulnerabilities, the best practices for staying safe, and the alternatives to these outdated, insecure methods.
This deep dive will cover the security risks associated with unencrypted POP3 and IMAP protocols, highlighting real-world examples of attacks. We’ll then navigate the path to secure email communication, providing actionable steps for securing your accounts and choosing safer email clients and providers. Finally, we’ll examine the legal implications of using unencrypted email for sensitive data, ensuring you’re not just protected, but also compliant.
Security Risks of Unencrypted 3, 3M, POP3, and IMAP Services
In today’s hyper-connected world, email remains a cornerstone of communication, both personal and professional. However, relying on unencrypted email protocols like POP3 and IMAP exposes you to significant security risks. Understanding these vulnerabilities is crucial to protecting your sensitive information. This section will delve into the dangers of sending and receiving emails without encryption.
Unencrypted POP3 and IMAP expose your email communication to eavesdropping and manipulation. When you use these protocols without encryption (like using POP3 or IMAP over plain HTTP), your email messages travel across the internet in plain text. This means anyone with access to the network – including hackers, malicious actors, or even your internet service provider – can potentially intercept and read your emails. They could access your passwords, financial information, personal details, and confidential business communications.
Data Breaches and Identity Theft Resulting from Unencrypted Email
The consequences of using unencrypted email services can be severe. Data breaches are a common outcome, leading to the exposure of sensitive personal and financial information. This compromised data can then be used by criminals for identity theft, resulting in fraudulent activities such as opening bank accounts, applying for loans, or making purchases in your name. The financial and emotional toll of such events can be devastating. Imagine your banking details falling into the wrong hands simply because you’re using an unencrypted email service.
Real-World Examples of Attacks Exploiting Unencrypted Email Communication
Numerous real-world examples demonstrate the vulnerability of unencrypted email. For instance, man-in-the-middle attacks can intercept email traffic, allowing attackers to read messages, modify their content, or even inject malicious code. These attacks are particularly effective against unencrypted connections because they don’t require sophisticated techniques to break encryption. Another example is the use of sniffing tools to passively capture unencrypted email data as it transits across a network. This can reveal sensitive data without requiring active intervention by the attacker. In some cases, poorly secured email servers themselves can be compromised, exposing all unencrypted email stored on the server.
Comparison of Encrypted and Unencrypted Email Protocols
The table below compares the security features, speed, and common use cases of POP3, IMAP, and SMTP protocols, both with and without encryption. Encryption (typically using SSL/TLS) significantly enhances security, but can sometimes slightly reduce speed.
| Protocol | Encryption | Security | Speed | Common Use Cases |
|---|---|---|---|---|
| POP3 | Unencrypted | Low – vulnerable to eavesdropping and data interception | Fast | Downloading emails to a single device |
| POP3 | Encrypted (POP3S) | Medium – protected from eavesdropping, but server security remains a factor | Moderately fast | Downloading emails to a single device securely |
| IMAP | Unencrypted | Low – vulnerable to eavesdropping and data interception | Fast | Accessing emails from multiple devices |
| IMAP | Encrypted (IMAPS) | Medium – protected from eavesdropping, but server security remains a factor | Moderately fast | Accessing emails from multiple devices securely |
| SMTP | Unencrypted | Low – vulnerable to eavesdropping and email manipulation | Fast | Sending emails |
| SMTP | Encrypted (SMTPS/STARTTLS) | Medium – protected from eavesdropping and email manipulation during transmission | Moderately fast | Sending emails securely |
Best Practices for Secure Email Communication
Source: websavers.ca
In today’s digital landscape, email remains a cornerstone of communication, both personal and professional. However, the convenience of email comes with inherent security risks. Protecting your inbox isn’t just about avoiding spam; it’s about safeguarding sensitive information and maintaining your online privacy. Implementing robust security measures is crucial to mitigate these risks and ensure your email communications remain confidential and trustworthy.
Securing your email involves a multi-faceted approach, encompassing password management, authentication protocols, and the choice of email clients. By adopting these best practices, you can significantly reduce your vulnerability to phishing scams, data breaches, and other cyber threats.
Strong Passwords and Two-Factor Authentication
Strong passwords are the first line of defense against unauthorized access. A strong password is long, complex, and unique to each of your accounts. Avoid using easily guessable information like birthdays or pet names. Instead, opt for a combination of uppercase and lowercase letters, numbers, and symbols. Password managers can help you generate and securely store complex passwords. Beyond strong passwords, two-factor authentication (2FA) adds an extra layer of security. 2FA requires a second form of verification, such as a code sent to your phone or email, in addition to your password, making it significantly harder for attackers to gain access even if they obtain your password. Consider enabling 2FA on all your email accounts for enhanced protection.
Encrypted Email Protocols: POP3 over SSL/TLS and IMAP over SSL/TLS
Using encrypted email protocols is essential for protecting your email content during transmission. POP3 (Post Office Protocol) and IMAP (Internet Message Access Protocol) are common protocols used to retrieve emails from a server. However, using these protocols without encryption leaves your emails vulnerable to interception. POP3 over SSL/TLS and IMAP over SSL/TLS encrypt the connection between your email client and the server, ensuring that your emails are protected from prying eyes. Always choose the SSL/TLS versions of these protocols when configuring your email settings. This ensures that your emails are encrypted both when sending and receiving.
Benefits of Using Encrypted Email Clients
Many email clients offer built-in support for encryption, providing an additional layer of security. These clients often incorporate features like end-to-end encryption, which ensures that only the sender and recipient can read the email content. Furthermore, secure email clients often include features that help you identify and avoid phishing attempts and malicious links. Choosing an email client with strong security features is a proactive step towards protecting your email communications.
Configuring Secure Email Settings in Outlook, 3 3m pop3 imap services unencrypted
Properly configuring your email client is crucial for securing your email communications. Here’s a step-by-step guide for setting up secure email in Microsoft Outlook:
- Open Outlook and go to File > Account Settings > Account Settings.
- Select your email account and click Change.
- Under Server Settings, ensure that “Use Secure Password Authentication (SPA)” is checked. This option helps protect your password during transmission.
- For incoming mail server (IMAP), ensure that the “Use SSL/TLS” option is selected, and the correct port (typically 993) is specified.
- For outgoing mail server (SMTP), ensure that the “Use SSL/TLS” option is selected, and the correct port (typically 465 or 587) is specified. The exact port may depend on your email provider.
- Click Next and then Finish to save your changes.
Alternatives to Unencrypted Email Services
Switching to a secure email provider is a crucial step in protecting your digital privacy and sensitive information. Unencrypted POP3 and IMAP services leave your emails vulnerable to interception and snooping, putting your personal data at risk. Thankfully, there are plenty of robust alternatives available that prioritize security and privacy. Let’s explore some of the best options and how to make the switch.
Choosing a secure email provider involves considering various security features. The strength of encryption, the provider’s privacy policy, and their overall security infrastructure all play a vital role. Understanding these aspects will empower you to make an informed decision and protect your communications effectively.
Secure Email Provider Comparison
Several factors differentiate secure email providers. Some providers offer end-to-end encryption, ensuring only you and the recipient can read your messages. Others may offer two-factor authentication (2FA), adding an extra layer of security to prevent unauthorized access. Some providers are more transparent about their data handling practices, while others may have less stringent privacy policies. A comprehensive comparison should consider these aspects to determine the best fit for individual needs. For example, ProtonMail is known for its strong encryption and commitment to user privacy, while Tutanota emphasizes its open-source nature and strong security protocols. The level of security offered varies depending on the provider’s design and implementation of these features.
Migrating Email Accounts
Migrating your email account from an unencrypted service to a secure alternative is generally a straightforward process. Most secure email providers offer detailed instructions on their websites, guiding users through the process of importing their existing emails and contacts. This typically involves using the provider’s import tools, which often support various formats like POP3 and IMAP. Remember to back up your data before initiating the migration, just in case anything goes wrong. For instance, if you’re moving from Gmail to ProtonMail, you’d configure your ProtonMail client to import emails from your Gmail account using the appropriate settings. The process might involve setting up an IMAP connection to download your old emails. After verification, your emails will be transferred to your new secure email account.
Privacy-Focused Email Providers
Choosing an email provider that prioritizes user privacy and security is paramount in today’s digital landscape. Consider these factors when making your selection: strong encryption (ideally end-to-end), transparent privacy policies, open-source code (allowing for independent security audits), and robust security features like two-factor authentication.
- ProtonMail: Known for its strong end-to-end encryption and Swiss privacy laws.
- Tutanota: An open-source email provider with a focus on security and privacy.
- Posteo: A German provider emphasizing user privacy and data protection.
- Mailfence: Offers end-to-end encryption and a variety of security features.
The Role of Email Providers in Security
Email providers are the gatekeepers of our digital correspondence, and their role in ensuring the security of our emails is paramount. Their responsibility extends beyond simply providing an inbox; they are tasked with protecting user data from breaches, unauthorized access, and malicious actors. The level of security offered directly impacts the privacy and trust users place in their chosen email service.
Email providers can implement numerous measures to safeguard against unencrypted email access. These measures are crucial because unencrypted emails are essentially postcards traveling across the internet, visible to anyone who intercepts them. Stronger security practices are needed to protect user data and maintain user trust.
Measures to Protect Against Unencrypted Email Access
Robust security measures implemented by email providers significantly reduce the risk of unencrypted email access. These include employing robust encryption protocols like TLS/SSL for all email traffic, implementing strong authentication methods like two-factor authentication (2FA) to prevent unauthorized logins, regularly updating their systems and software to patch vulnerabilities, and investing in advanced security technologies such as intrusion detection and prevention systems to monitor for suspicious activity. Furthermore, proactive measures such as educating users about email security best practices and providing tools to help users identify and report phishing attempts are crucial for a comprehensive security strategy. Providers should also have clear and accessible policies on data retention and user privacy.
Examples of Email Providers Promoting Encrypted Email
Several email providers actively promote and support the use of encrypted email protocols. ProtonMail, for example, is built from the ground up with end-to-end encryption, meaning only the sender and recipient can read the email content. Tutanota is another provider that emphasizes privacy and security by default, utilizing encryption to protect user data. While services like Gmail and Outlook don’t automatically encrypt all email traffic by default, they support and encourage the use of TLS/SSL, and offer features like two-factor authentication to enhance security. These providers demonstrate a commitment to user privacy and security by actively promoting the use of secure protocols and features.
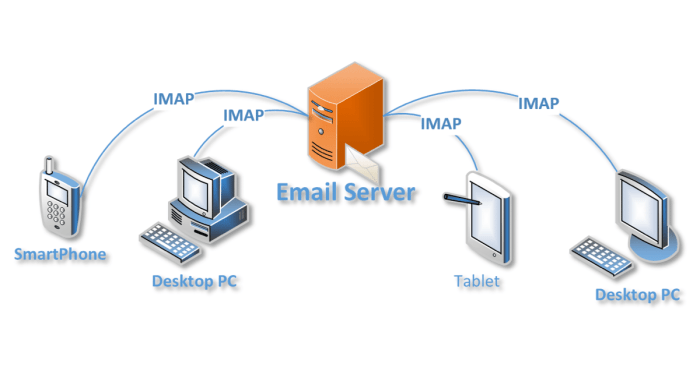
Illustrative Example of Email Transmission and Vulnerabilities
Imagine sending an email from your device to a recipient. First, your email client (like Outlook or Thunderbird) connects to your email provider’s server using either POP3 or IMAP. In an unencrypted connection, this initial connection is vulnerable. Any eavesdropper on the network could potentially see your login credentials. Once connected, your email is sent to your provider’s server. If the connection between your client and the server is not encrypted (lack of TLS/SSL), the email content itself is visible to anyone monitoring network traffic. Your provider’s server then routes the email to the recipient’s provider’s server. This process repeats in reverse for the recipient to access the email. Each step, if unencrypted, presents a potential vulnerability. The use of encryption at each stage of this process drastically reduces the likelihood of unauthorized access to the email’s contents.
Legal and Regulatory Implications of Unencrypted Email: 3 3m Pop3 Imap Services Unencrypted
Source: co.uk
Using unencrypted email to transmit sensitive data exposes individuals and organizations to significant legal and regulatory risks. Data protection laws worldwide mandate secure handling of personal and confidential information, and failing to meet these standards can result in hefty fines and reputational damage. This section explores the legal landscape surrounding unencrypted email communication and the potential consequences of non-compliance.
Data Protection Laws and Regulations
Numerous laws and regulations globally address data protection and privacy, many of which implicitly or explicitly require secure email practices. The General Data Protection Regulation (GDPR) in the European Union, the California Consumer Privacy Act (CCPA) in California, and the Health Insurance Portability and Accountability Act (HIPAA) in the United States are prime examples. These regulations establish strict rules regarding the collection, processing, storage, and transmission of personal data, including email communication. Failure to protect data transmitted via unencrypted email channels can be a direct violation of these regulations.
Legal Implications of Unencrypted Email for Sensitive Data
The use of unencrypted email for sensitive data, such as financial information, medical records, or personally identifiable information (PII), carries substantial legal risks. Data breaches resulting from unencrypted email can lead to lawsuits from affected individuals, regulatory investigations, and significant financial penalties. The legal implications extend beyond direct financial losses; reputational damage and loss of customer trust can also severely impact an organization’s long-term viability. For instance, a healthcare provider sending unencrypted emails containing patient medical records could face HIPAA violations, leading to substantial fines and potential legal action from affected patients.
Penalties for Non-Compliance with Data Protection Regulations
Penalties for non-compliance with data protection regulations vary significantly depending on the jurisdiction and the severity of the violation. GDPR, for example, imposes fines of up to €20 million or 4% of annual global turnover, whichever is higher. CCPA violations can result in civil penalties of up to $7,500 per violation. HIPAA violations can lead to significant fines, ranging from several thousand dollars to millions of dollars, depending on the nature and extent of the violation. Beyond financial penalties, organizations might face legal action from individuals whose data has been compromised, further increasing their liability.
Key Legal Aspects of Unencrypted Email
| Legislation | Jurisdiction | Data Protection Requirements | Penalties for Non-Compliance |
|---|---|---|---|
| GDPR | European Union | Requires appropriate technical and organizational measures to ensure a level of security appropriate to the risk. | Up to €20 million or 4% of annual global turnover |
| CCPA | California, USA | Requires businesses to implement reasonable security measures to protect consumer personal information. | Up to $7,500 per violation |
| HIPAA | United States | Mandates the implementation of safeguards to protect the privacy and security of protected health information (PHI). | Varies significantly, potentially reaching millions of dollars. |
Conclusive Thoughts
Source: secybr.com
In a world where our digital lives are increasingly intertwined with our real ones, securing our email communication is paramount. Ignoring the risks of unencrypted POP3 and IMAP services is like playing Russian roulette with your personal information. By understanding the vulnerabilities, adopting best practices, and choosing secure alternatives, you can significantly reduce your risk of becoming the next victim of a data breach. Remember, your digital security is your responsibility. Take control and protect yourself.


